Superfish Adware in Lenovo Consumer Laptops Violates SSL, Affects Companies via BYOD
 There is a nasty new fish in town.
There is a nasty new fish in town.
Certain consumer-grade Lenovo laptop models shipped out between September and December 2014 came pre-installed with Superfish, a visual search technology that not only exhibits adware behaviors, but also allows cybercriminals to snoop in secure communications via man-in-the-middle (MitM) attacks.
To deal with adware or “advertising-related software” is harrowing enough for many consumers. For them to be actually exposed to the threat of data theft, however, is another story. Unfortunately, this is the case in Superfish adware in Lenovo laptops.
According to Lenovo, desktops, servers, and enterprise laptops never had this adware installed. However, given that the consumerization trend allows employees to bring their own devices in the office. Should one or more of these include affected Lenovo models, company systems may also be open to the consequences of this flaw.
The pre-installed Superfish root certificate allows the software to still function even in SSL-secured (HTTPS) transactions—such as when you log into your online banking account, sign into your favorite social networking site, or log in your email or IM accounts.
The Superfish adware, in effect, replaces all certificates the system receives with its own certificates created on the fly, signed with the installed root certificate. This is exactly how a man-in-the-middle attack is performed.
The problem with this is that attackers can use this knowledge to create their own certificates that the system would consider valid. For example, a phishing site could have what appears to be valid certificate and a typical user would have a very hard time telling the difference. An attacker could also sign a malicious file to make it look like from a reputable developer, and the user would be none the wiser.
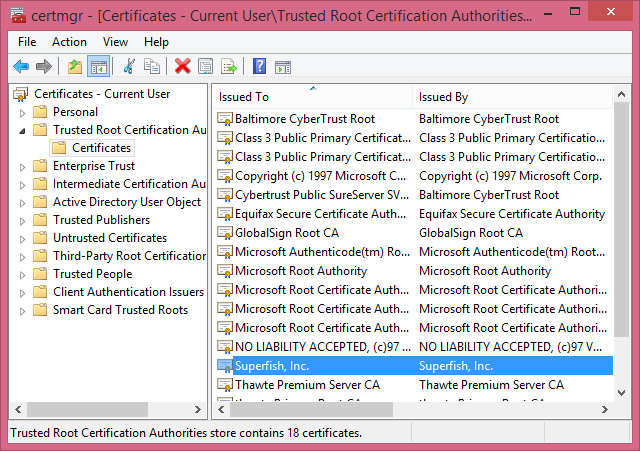
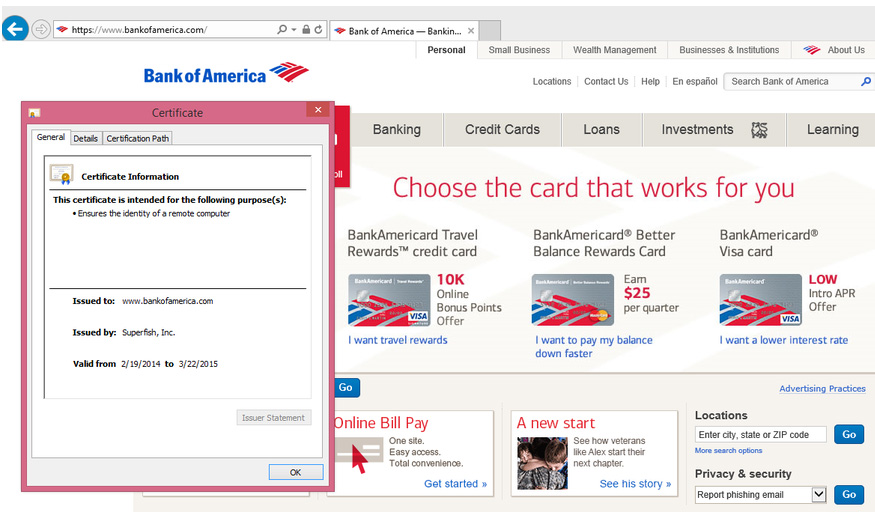
Photo source: Rob Graham Twitter account
A Rotten Case of Adware Gone Bad
For many of those who owned one of Lenovo consumer laptop models with Superfish adware, using search engines can be a bit irritating.
When you search something in your browser with Superfish installed, you get visual search results, which Lenovo said in a statement , was placed there “to help customers potentially discover interesting products while shopping.”
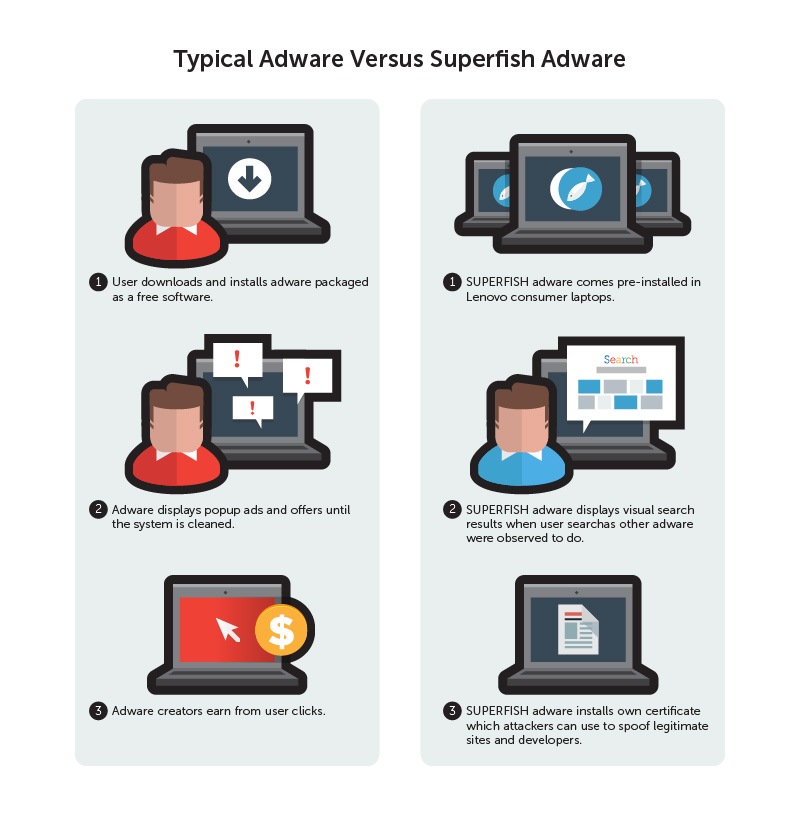
“Lenovo why are you adding adware…that hijacks search results on any browser? Is it not enough that customers buy a laptop from you?” asked a Lenovo community forum commenter known as “iknorr” on September last year. This is only one in over a hundred comments from customers displeased with the pre-installed Superfish adware.
In response, Lenovo has since stopped preloading the software and disabled server-side transactions on Lenovo products. They have also published instructions on how to uninstall the Superfish applications, which can be found on this link: http://support.lenovo.com/us/en/product_security/superfish_uninstall.
“Longer term, I believe manufacturers should be obliged to offer the option of buying all PCs as a bare-metal option i.e. with no operating system pre-installed. Not only would this reduce cost to the user, it would also increase freedom of choice of Operating System and hand full control back to the owner of the device,” says Rik Ferguson, Global VP Security Research at Trend Micro.
[Read: Superfish (and chips) or Super Phish? ]
In the past, we have also noted of how the InstallBrain adware had led to the installation of the MEVADE/ SEFNIT malware.
[Read: Adware Gone Bad: The Adware and MEVADE/SEFNIT Connection ]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Postagens recentes
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks