Despite being more than five decades old, email still prevails as the communication tool of choice for most organizations and groups. In fact, email was hailed as the most popular internet activity in 2023. And because of its vast userbase — with approximately 4.37 billion users worldwide last year — it remains a favored attack vector for cybercrime. One report regarded it as the “most vulnerable communication and collaboration tool in the enterprise environment.”
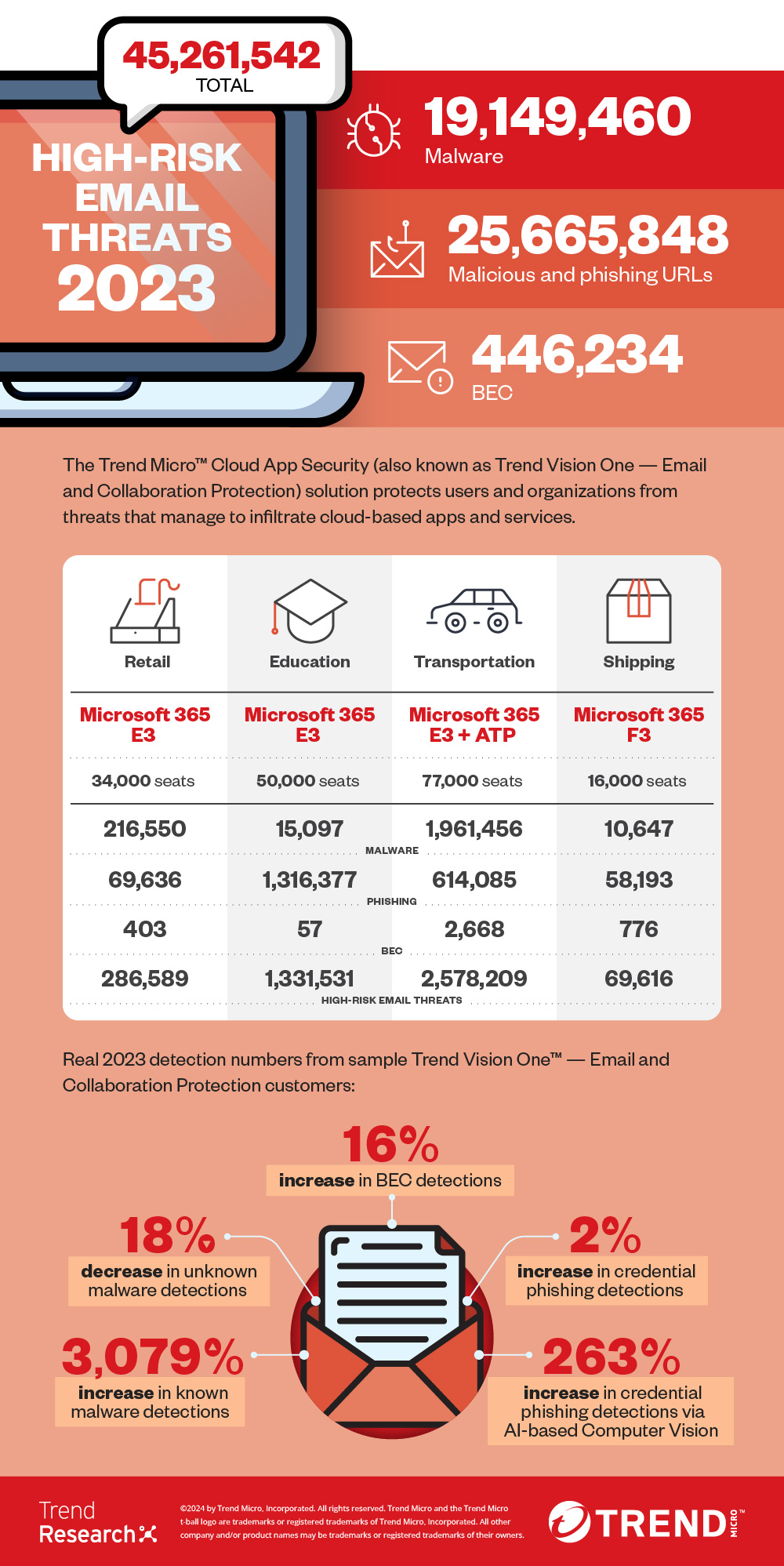
This report looks into the notable email threats of 2023, including the 45,261,542 high-risk email threats we detected and blocked using the Trend Micro™ Cloud App Security solution, also referred to as Trend Vision One™ — Email and Collaboration Protection solution, which is part of the Trend Vision One Email and Collaboration Security suite.
Overall malware, known malware detections saw mammoth growth in 2023
We detected and blocked a total of 19.1 million malware files in 2023, which account for a substantial 349% jump from 2022’s detections. Known malware files also dramatically surged last year, with 16 million detections for a massive 3,079% increase. This substantial increase in file detection is due to the heightened use of phishing links within email attachments. We detect these as malicious files and note that the number of detected files has increased accordingly.
This trend shows that malicious actors are using attacks with more sophisticated arrival techniques, and as a result, businesses of all sizes will go up against a slew of increasingly complex attacks that could put their operations at risk.
Aside from detecting known malware, our security solution can catch, analyze, and block new and unknown malicious content used by threat actors. In 2023, we detected 3 million unknown malware files, a slight decrease of 18% from 2022’s numbers.
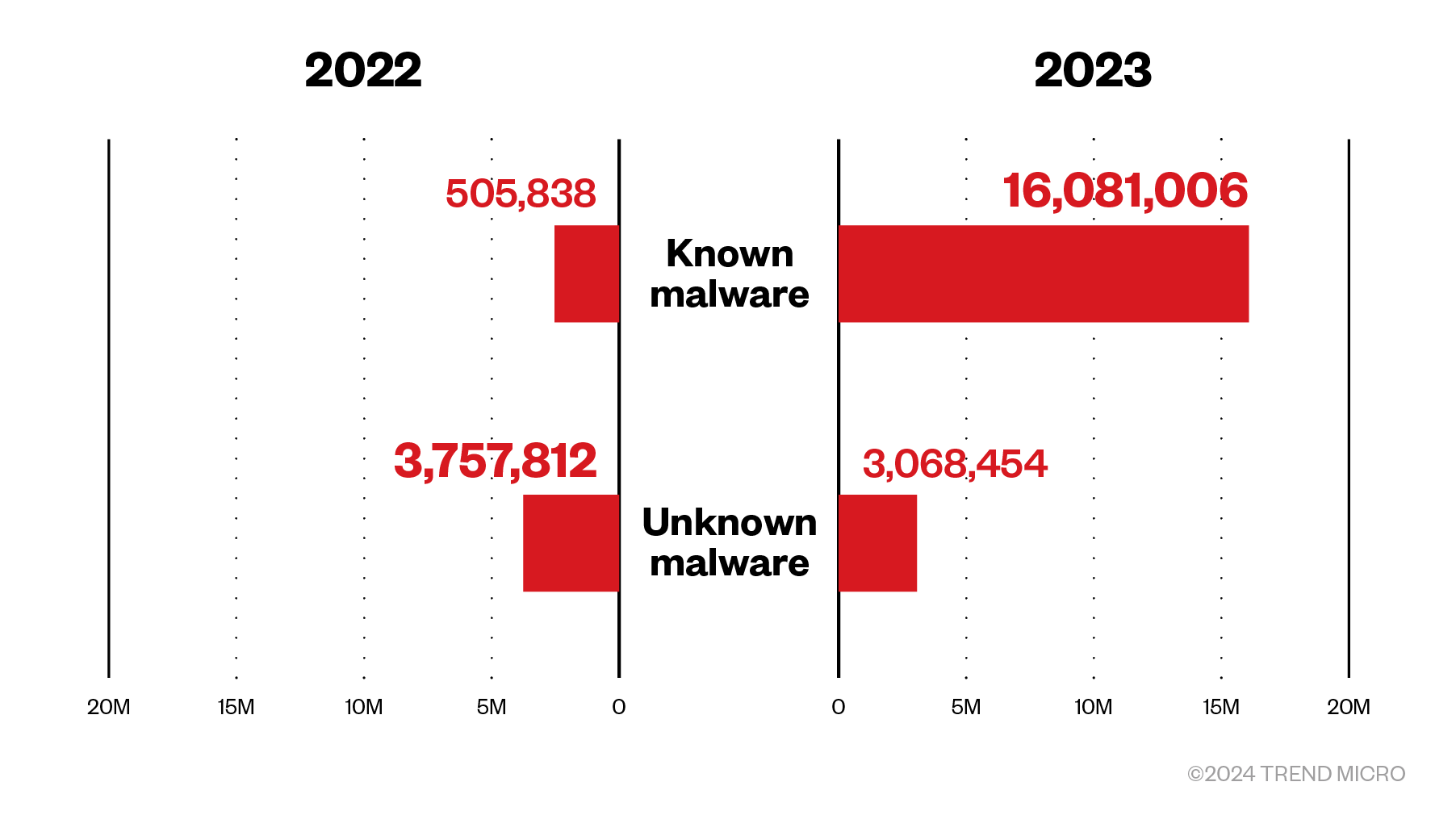
Figure 1. Known and unknown malware detections in 2022 and 2023
Notable malware attacks of 2023:
DarkGate actors abused instant messaging platforms Microsoft Teams and Skype to spread malware to victim machines.
APT34 launched a phishing campaign to drop a new malware type we dubbed “Menorah,” which was specifically designed for cyberespionage.
Lumma Stealer operators abused the Discord platform to host and spread a piece of information-stealing malware and create bots to remotely control this piece of malware.
Bandit Stealer, an example of information-stealing malware, has been seen to target multiple browsers and cryptocurrency wallets while evading detection.
We’ve also recently noticed an uptick in malicious QR codes that are being distributed via email for phishing purposes, an attack that is also known as “quishing” (a portmanteau of “QR code” and “phishing”) that has been seen to evade inboxes’ built-in spam filters.
From Oct. 25, 2023, to April 22, 2024, we detected 154,945 malicious QR codes in email bodies. Quishing attacks are being used to target company executives; one report shares that in the fourth quarter of 2023, C-suite executives were targeted 42 times more than regular employees.
Meanwhile, ransomware detections in 2023 increased by 9%.
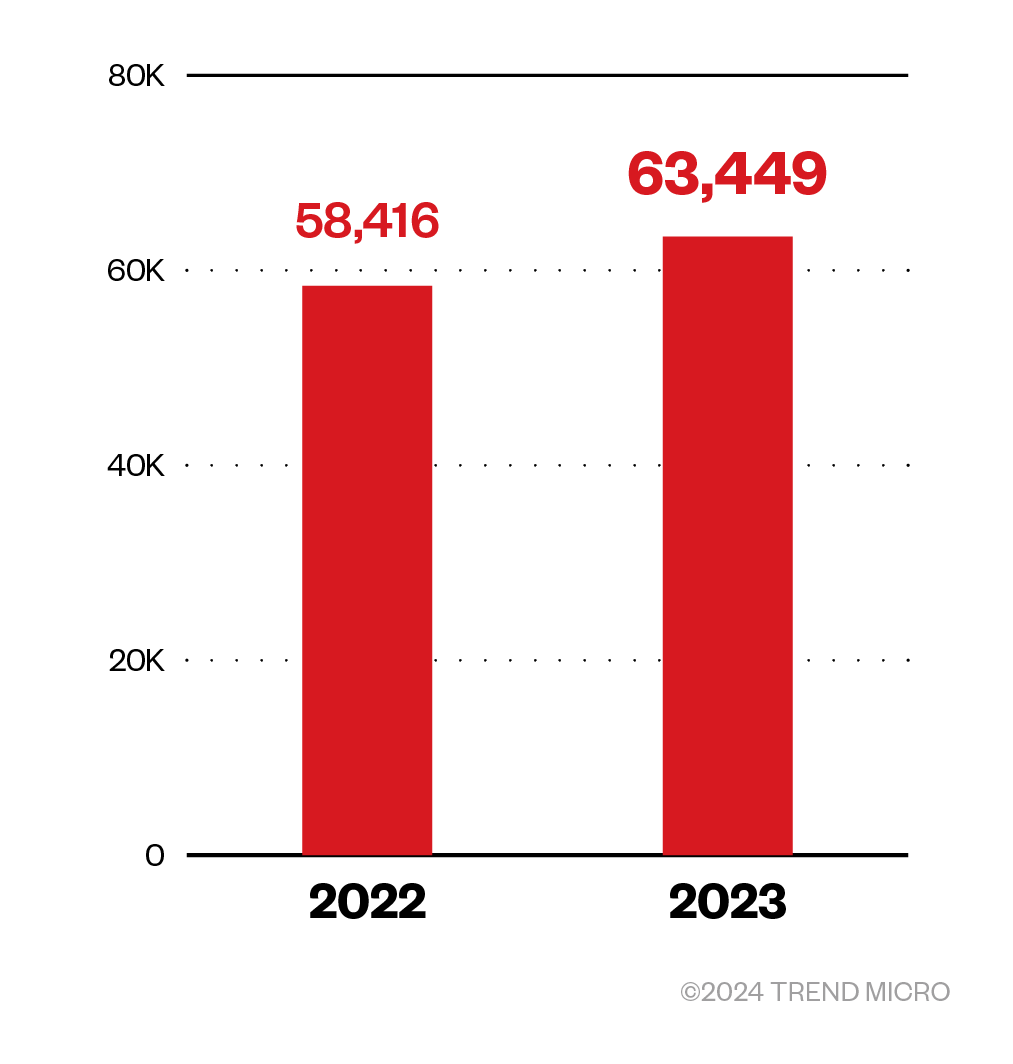
Figure 2. Ransomware detections in 2022 and 2023
Notable ransomware attacks of 2023:
Vice Society ransomware operators started targeting the manufacturing sector in Brazil, Argentina, Switzerland, and Israel.
Ransomware operators used a new ransomware type called Rhysida to target the healthcare sector, including healthcare systems company Prospect Medical Holdings.
Cerber ransomware actors were observed exploiting the Atlassian Confluence vulnerability CVE-2023-22518 in their operations.
Overall and known credential phishing attacks show small growth, Computer Vision detections jump 263%
In 2023, our telemetry showed that there was minimal growth in the total number of credential phishing attacks, which was at 6.7 million. The number of known credential phishing detections grew 5%, while unknown credential phishing detections decreased 29%.
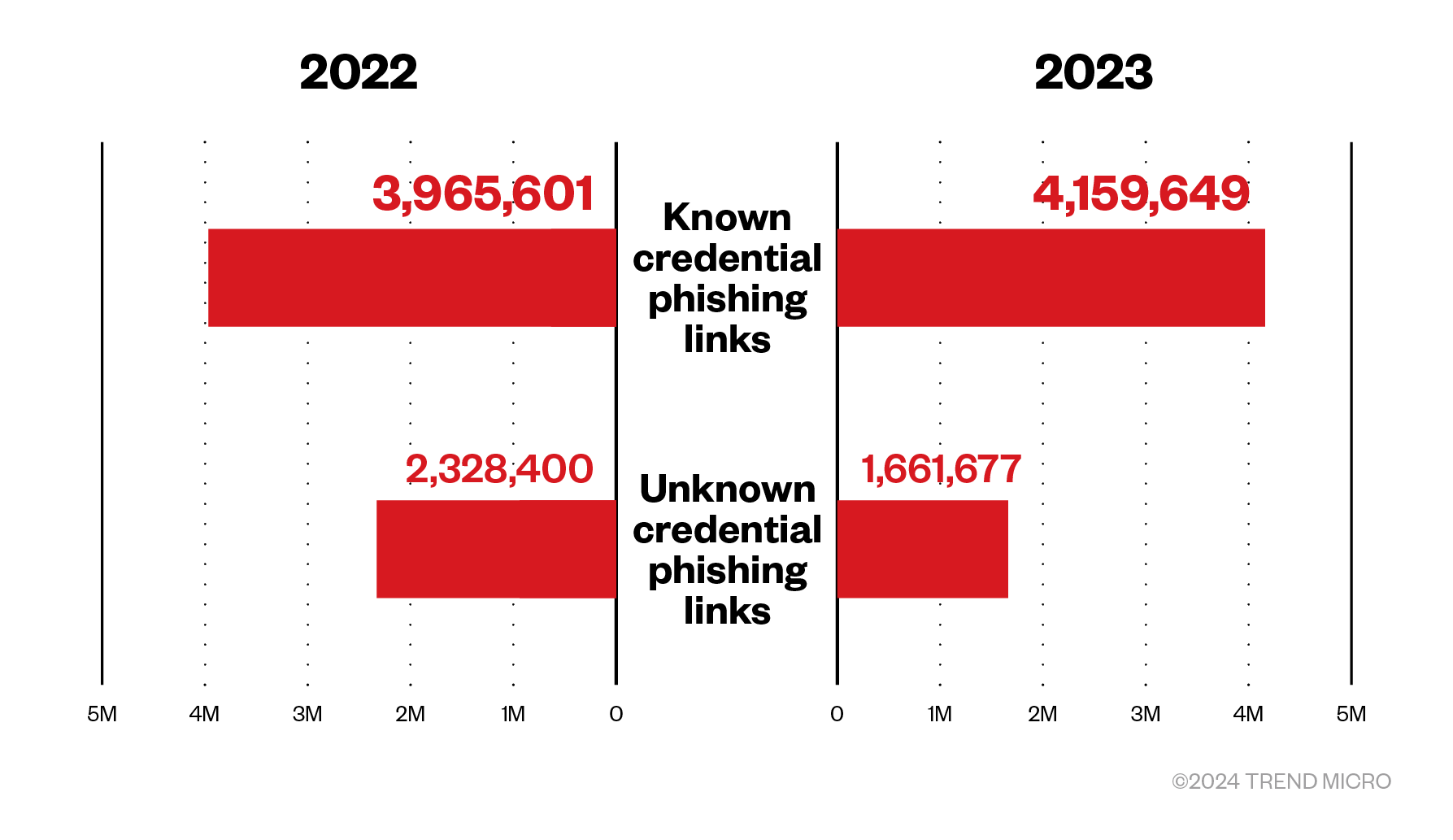
Figure 3. Known and unknown credential phishing detections in 2022 and 2023
As for Computer Vision detections — a technology that combines image analysis and machine learning (ML) to check branded elements, login forms, and other site content to detect credential phishing URLs — we saw 870,555 detections, a substantial 263% increase from the previous year’s numbers.
Notable credential phishing attacks of 2023:
The Android banking trojan TgToxic was used to steal cryptocurrency from digital wallets and banking credentials in Thailand and Indonesia.
Malicious actors started using large language models (LLMs) to abuse paid Facebook promotions and spread malicious code that installs a credential-stealing browser add-on.
Cybercriminals launched a credential phishing campaign that used socially engineered emails with a link to DRACOON.team, which leads victims to a fraudulent Microsoft 365 login portal that steals victims’ login information.
BEC detections via antispam and Writing Style DNA spike
We observed a 16% growth in the total number of business email compromise (BEC) detections last year. BEC attacks detected via Writing Style DNA — an authorship analysis technology that detects impersonations of high-profile users (CEOs, vice presidents, and general managers) by analyzing the writing style of suspicious emails and comparing it with an AI model of the user’s writing — grew to 166,043, a 23% increase. Meanwhile, BEC detections via the antispam engine rose to 280,191, representing a 13% growth.
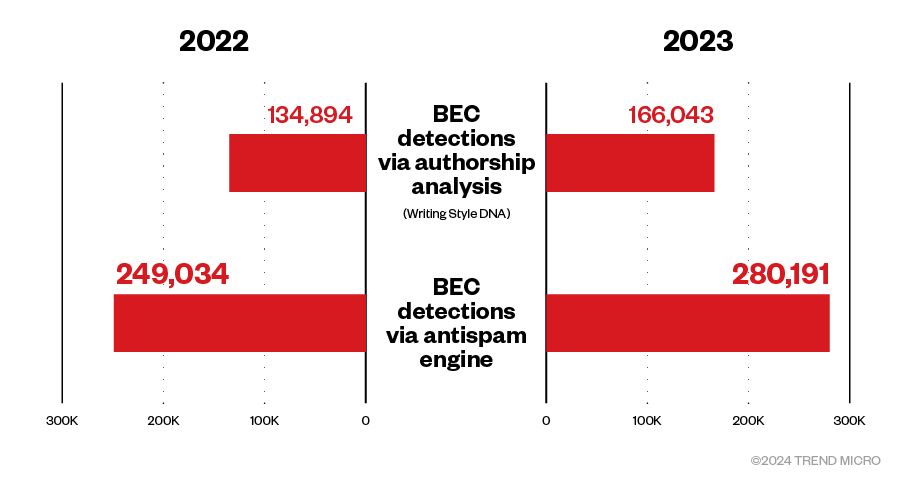
Figure 4. BEC detections via Writing Style DNA and antispam engine in 2022 and 2023
Notable BEC attacks of 2023:
Microsoft reported on a complex multistage adversary-in-the-middle (AiTM) phishing and BEC attack on banking and financial services companies.
Europol thwarted a notorious CEO fraud group that stole US$40.3 million from one victim by using BEC attacks to siphon payments from victim organizations to cybercriminals’ bank accounts.
Phishing numbers dropped in 2023
Last year, we detected and blocked 14.7 million phishing attacks that represent a 31% decrease. There was also a 45% decrease in phishing attacks detected via spam count, with 8 million detections.
As previously mentioned, our detection efforts count phishing links within attachments as potential malware, which explains the rise in malware and the drop in phishing detections. In the past, we’ve seen cybercriminals send phishing links directly in the email body and lure victims into providing credentials or critical information. However, in more recent times, we’ve observed a different trend, with cybercriminals opting to incorporate phishing links inside email attachments for obfuscation purposes.
It’s safe to attribute this substantial decrease to malicious actors’ focus on better infiltration and preliminary detection evasion tactics, as we shared in our 2023 year-end roundup report.
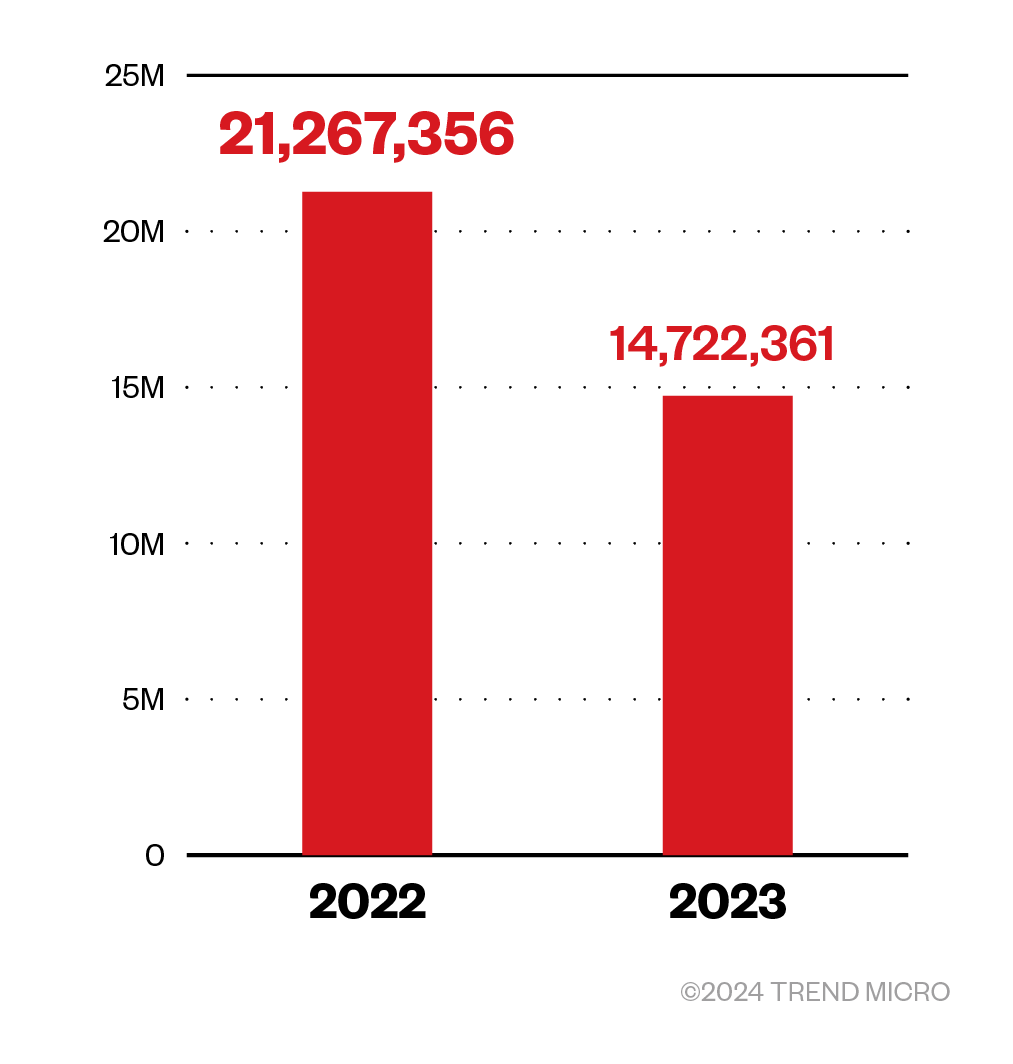
Figure 5. Phishing detections in 2022 and 2023
Notable BEC attacks of 2023:
We uncovered a RedLine Stealer campaign that used spear-phishing emails to target organizations in the hospitality industry.
The Hershey Company reported that a limited number of company emails were hit with a phishing campaign that led to a data breach.
Approval phishing scams were used to steal at least US$374 million worth of cryptocurrency in 2023.
Software company Retool was targeted by an SMS-based phishing attack that led to 27 of its cloud customers being compromised.
Protect your organization’s emails, endpoints, and cloud-based services and apps with Trend Vision One — Email and Collaboration Protection
Organizations should consider a comprehensive multilayered security solution such as Trend Vision One — Email and Collaboration Protection, which takes the following actions:
- Supplements pre-existing security features in email and collaboration platforms such as Microsoft 365 and Google Workspace by using ML to analyze and detect any suspicious content in the message body and attachments
- Acts as a second layer of defense that can catch highly evasive and complex threats
- Uses sandbox malware analysis, document exploit detection, data loss prevention (DLP) and advanced malware protection for Box, Dropbox, Google Drive, SharePoint online, and OneDrive for Business, and file, email, and web reputation technologies
- Uses layers of artificial intelligence (AI) to detect advanced threats such as lateral phishing, advanced phishing, and domain/brand impersonation attacks for cross-module detection. Our AI features, which include user preferences, email sentiment analysis, and intention analysis, learn users’ habits in sending and receiving emails to identify abnormal emails
- Includes the RiskAI user visibility feature that detects malicious activity that customers can use to trigger further investigation; for example, the solution detects a user that continuously sends out phishing or malicious emails, which indicates that the user’s account is compromised or a victim of an account takeover attack
- Offers seamless integration with an organization’s existing cloud setup, preserving full user and administrator functionality, providing direct cloud-to-cloud integration through vendor APIs
- Minimizes the need for additional resources by assessing threat risks before sandbox malware analysis
- Provides users the option to rescan historical URLs in users' email metadata and performs continued remediation (automatically taking configured actions or restoring quarantined messages) using newer patterns updated by Trend Micro™ Web Reputation Services
Trend Vision One — Email and Collaboration Protection stands on the cutting edge of email and software-as-a-service (SaaS) security, offering ML-powered features that combat two of the primary email-based threats (BEC and credential phishing):
- Writing Style DNA helps determine if an email is legitimate by using ML to check a user’s writing style based on past emails and then comparing suspicious emails against it.
- Computer Vision combines image analysis and ML to check branded elements, login forms, and other site content. It then pools this information with site reputation elements and optical character recognition (OCR) to check for fake and malicious sites — all while reducing instances of false positives to detect credential phishing emails.
Trend Vision One — Email and Collaboration Protection also comes with the advanced and extended security capabilities of Trend Micro™ Managed XDR, providing investigation, detection, and response across your endpoints, email, and servers. Trend Vision One — Email and Collaboration Protection is part of Trend Vision One™, a security platform that enhances and consolidates detection, investigation, and response capabilities across email, endpoints, servers, cloud workloads, and networks. Customers of both the standalone Cloud App Security solution and Trend Vision One — Email and Collaboration Protection under Trend Vision One are covered by Trend Micro’s robust threat intelligence and risk protection services.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks