Securing IoT Apps
 The internet of things (IoT) has changed the way businesses and industries operate, as well as the way people facilitate daily tasks. Today’s smart devices allow users to handle tasks and errands more conveniently. The apps that connect users, smart devices, and the internet have altered the way users integrate different systems and functions for work, play, education, and personal necessities with a touch or command.
The internet of things (IoT) has changed the way businesses and industries operate, as well as the way people facilitate daily tasks. Today’s smart devices allow users to handle tasks and errands more conveniently. The apps that connect users, smart devices, and the internet have altered the way users integrate different systems and functions for work, play, education, and personal necessities with a touch or command.
The abrupt shift to work-from-home arrangements has made users more dependent on the convenience that IoT technology brings, prompting a surge in IoT app development, deployment, and usage for “contactless” purposes. As people work from their homes, business equipment such as laptops and smartphones are connected within the same space and network as their IoT devices. Home networks and devices are unlikely to have the same layered security compared to offices, and these added entry points could compromise users’ and organizations’ security and expose their data to threats. Cybercriminals on the constant lookout for threat vectors to abuse are finding new openings, such as device and app vulnerabilities, storage misconfigurations, traffic exchange, and programming weaknesses, among other gaps.
[Read: Uncovering risks in ordinary places: A look at the IoT threat landscape]
Threats to IoT app security and management
All IoT devices have actuators that serve as sensors, enabling them to transmit and receive data, translating it to observable actions following users’ prompts, data, and programming. These devices also have operating system (OS)-based firmware with corresponding OS-based installation procedures of apps, and Wi-Fi enablement for data network transmission to the internet via the internet router. A final component involves an interface that allows the user to interact with the device in a way that the manufacturer or developer determined to be the most efficient. While this has been in the form of an app in recent years, previous instances also included notifications via emails or text messages.
These components have allowed users to control their respective devices remotely. Unfortunately, they have also been repeatedly identified as vulnerable to attacks and malware as each represents a path that can be used for cybercriminal intent.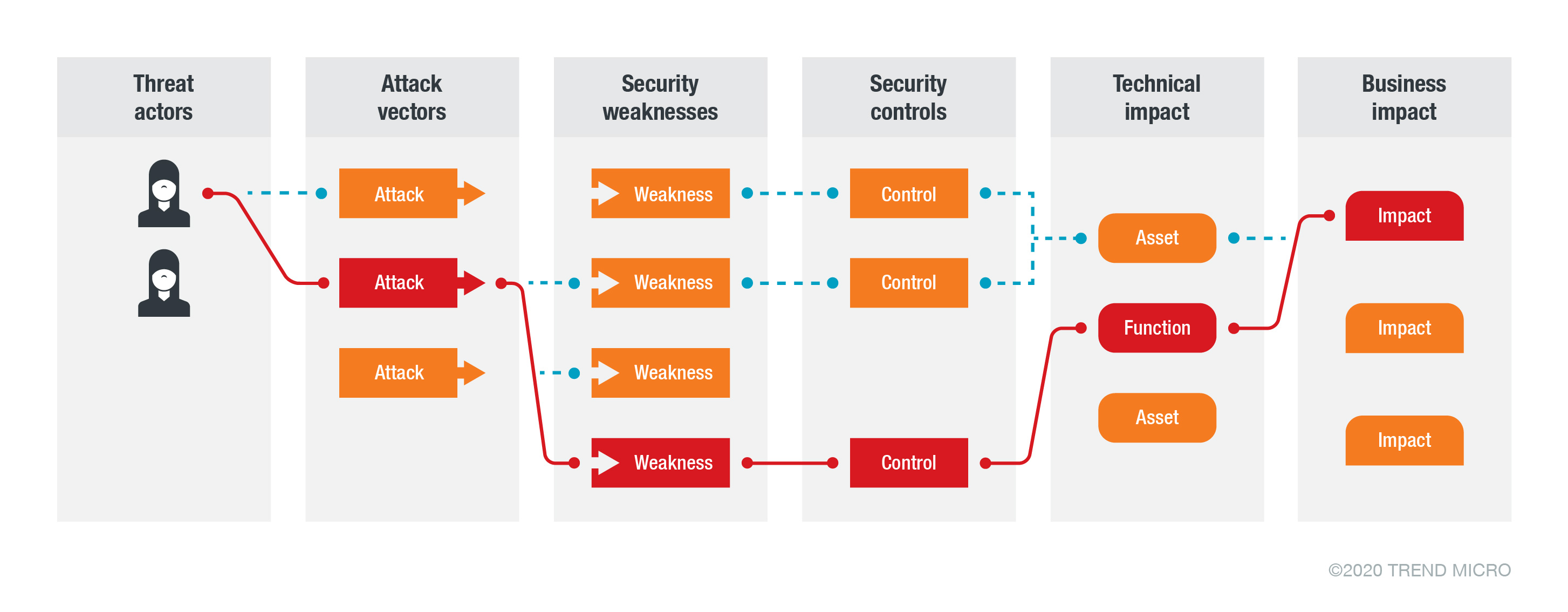
Figure 1. The widened attack surface of IoT devices, as identified by the Open Web Application Security Project (OWASP)
While the components pose varying degrees of difficulty for cybercriminal abuse or exploitation, an intrusion into the system can cause significant damage through any of the identified paths. Here are some of the attack vectors and risks to IoT applications:
- Vulnerabilities. Security gaps in apps can be overwhelmed so attackers and other malware can use them as entry points for distributed denial of service (DDoS) attacks, spoofing, and privilege escalation, among other possible routines. They can also be easier for cybercriminals to attack as these are constantly online and have multiple channels for entry.
- Unsecure communication channels. Communication channels that the devices use to transmit data need to be encrypted with one of the many available protocols available, such as transport layer security (TLS) or hypertext transfer protocol secure (HTTPS). Whether data is at rest or in transit, these channels enable traffic exchange and communication to and from the app. Left unencrypted, these channels can be abused to access supposedly confidential data that intruders can easily understand.
- Malicious application programming interface (API). Some developers depend on third-party API providers to integrate other known functions and libraries into their respective apps. Unfortunately, vulnerable and malicious third-party APIs and libraries have been previously reported to affect and infect legitimate apps, causing potentially irreversible damage to devices and users’ data. These malicious apps can also provide entry points for further attacks into the system, such as injection or man in the middle (MiTM) attacks.
- Misconfigured security settings. With more organizations and manufacturers moving workloads to the cloud for round-the-clock accessibility and efficiency, misconfigured settings for cloud-hosted apps can allow unauthorized actors to access data. Causes for these range from forgetting to customize default configurations, open storage, or error messages containing sensitive data, among others. Moreover, some organizations fail to remember that despite successful deployments of apps, all components (such as all operating systems, libraries, frameworks, and applications) involved in the development of apps, must be upgraded and patched regularly.
- Outdated operating systems and app versions. Outdated operating systems and app versions can also become entry points for intrusion. Some devices’ programming and accompanying apps may be based on the latest OS version available during manufacturing. In worst-case scenarios, these versions may already be outdated by the time it is sold to a user due to possible marketing, manufacturing, transit, or usage concerns. Some manufacturers also do not release updates as often as necessary, nor do they release updated versions. This can render users’ devices vulnerable and defenseless while in use and connected to the internet.
- Weak and recycled authentication passwords. Reusing the same credentials can also lead to intrusions to user accounts and IoT device platforms, potentially leading to an interconnected attack across different platforms. More often than not, device manufacturers also provide similar default account credentials to different devices, and users who leave the default settings on their respective devices become vulnerable to attacks.
These threat entry points affect all phases and parties involved, from the device manufacturers and their respective supply chain partners to the app developers and users. Aside from the technical reparations needed, threats could affect an organization’s reputation and finances significantly.
[Read: Into the battlefield: A security guide to IoT botnets]
Mitigating IoT app threats and attacks
Contrary to an old belief, individuals with IT backgrounds are no longer the only ones responsible for securing devices and connections. Every user is expected to manage their own devices and data, especially once connected and in use. But with the increased adoption of devices to accommodate our daily needs at home, work, and in transit, keeping these device and app threats at bay makes security a collective responsibility. Here are some measures that organizations and users can do to mitigate these risks:
- Download apps from legitimate platforms. Choose to download device apps from legitimate platforms instead of non-official third-party providers. Threat actors have been known to create fake or malicious versions of legitimate apps to steal sensitive information such as online account credentials and device details.
- Review and limit app permissions. Check the permissions that the apps request before downloading them to your phone, tablet, or computer. Be wary of apps that request excessive permissions as they may be trying to perform or access more than their published functions.
- Be more selective of the IoT devices to use. A growing number of manufacturers have been implementing “security by design” in their devices following an increased awareness among users and to comply with legal mandates in different countries. Organizations can also choose specific products and brands that prioritize security for their customers’ and partners’ data and supply chain safety.
- Update your applications and device OS regularly. Reputable developersand OS companies release updates periodically to enhance security and functionality. Download these updates as soon as they are available to patch potential security gaps that malicious actors can abuse.
- Map and identify the devices connected to the network. Identify and monitor the devices regularly connected to the home and office network. This allows administrators to track regular traffic and the accounts allowed to use the network, as well as recognize irregular traffic from malicious routines in the background. Since not all devices can be directly under the organization’s control, take additional precautions when needed (such as installing or enabling parental controls), and use recommended network filtering and site blocking whenever available.
- Secure communication protocols and channels. Devices need to communicate with each other to perform their respective online functions. These communication channels should be secured with cryptographic protocols such as transport layer security (TLS) and HTTPS, among others, to mitigate compromise.
- Change all devices’ default credentials. Device manufacturers and internet service providers (ISPs) provide default credentials for the devices they release. Remember to change their usernames and passwords, as well as customize the device settings.
- Practice password hygiene and enable available multi-factor authentication (MFA). Do not reuse the same passwords on multiple online accounts. Enable any MFA features on sites and platforms that allow it to add an extra layer of security for your data.
Securing your apps
The surge of IoT devices in the market, coupled with the increase in users and their demand for more connectivity and accessibility features, makes it difficult for standards to keep up. Personal and professional networks, appliances, and devices are now more intertwined and connected than ever, along with the amount of sensitive information being exchanged through the apps used to control and manage these devices. Everyone using a connected device becomes an “administrator of things,” emphasizing the collective responsibility for security. Organizations and consumers must take a closer look and ask more questions to learn how these devices and applications work for them, with inquiries focused on the functions and services beyond their primary use: where their data goes, how it’s used and protected, and where it’s stored.
Furthermore, apps and devices may be vulnerable from the time they are made available in the market, not because of negligence but for the lack of requirements and time for testing, encryption, and certification. Because of the fast pace of development, there are no standards by which programmers, manufacturers, or users can compare for verification. Though more countries have a long way to go, some are changing this by slowly integrating laws and frameworks to establish an improved cybersecurity response and resilience for IoT devices and other digital products. Regulation is still trying to catch up with IoT’s rate of advancement. In the meantime, organizations and users should maintain a “security first” and security-by-design mindset, from conceptualization, marketing, and adoption of devices and products to their respective offices and homes.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks