Across the Span of the Spanish Cybercriminal Underground: Current Activities and Trends
By Mayra Rosario Fuentes, David Sancho
Key Takeaways
- The Spanish-speaking cybercriminal underground is teeming with cyber-enabled criminal offerings, such as various types of scams and unauthorized access to services.
- While less common, cyber-dependent criminal offerings also persist, notably involving high-profile Spanish-speaking threat actors.
- The typical venues for transactions are a messaging app (for cyber-enabled scams) and English or Russian web forums (for cyber-dependent offerings).
Over the years, underground forums and markets have been the go-to venue for cybercriminals raring to buy or sell illegal goods and services.
In the past, we have researched regional trends in the cybercriminal underground, probing Latin American and Caribbean, North American, East Asian, and Middle Eastern areas. We’ve also had studies specifically focusing on countries such as Brazil, France, Germany, Japan, and Russia.
This time, our research puts a particular focus on the Spanish cybercriminal underground. We have gathered findings from Argentina, Mexico, Peru, Puerto Rico, Spain, and other Spanish-speaking communities.
As with most underground markets, the following types of products and services are offered:
- Cyber-dependent, referring to cybercriminal offerings that are reliant on technology. Some examples are ransomware, malware, and hacking services.
- Cyber-enabled, referring to schemes that could be performed without technology, but could be performed and disseminated more efficiently through cyber channels. These include fraud, scams, and theft.
What are the current trends and activities in the Spanish cybercriminal underground? Read on and learn more.
Cyber-Dependent Offerings
Years ago, Spanish cybercriminal online communities such as Elhacker, Indetectables, and Undercode rose in popularity. Members which were mostly from Spain and Latin American countries had discussions on malicious files such as crypters, botnets, and ransomware.
While such forums still exist, there also has been an increasing trend of prominent Spanish-speaking threat actors participating in Russian and English-language-based cybercriminal forums to sell and advertise their cyber-dependent offerings. The Russian-speaking cybercriminal community in particular has been a pioneer in the field and remains a robust ecosystem for sellers of any background.
Some of the most popular Russian-language forums used by Spanish speakers are:
- “Exploit,” a long-running Russian cybercrime forum accessible with internet browsers on the clear web and also via the dark web by using the Tor browser. Here, cybercriminals buy and sell stolen credit card details, malware, access-as-a-service, and zero-day exploits. Ransomware affiliate recruitment and similar topics are also discussed. To join, there is a $100 fee to be paid in bitcoins, but this can be waived if the user has established a reputation on another forum.
- “XSS,” previously known as “DaMaGeLaB,” mainly features discussions and trades related to credential access, exploits, and valuable zero-day vulnerabilities. In the past, XSS was notorious for recruiting affiliates for ransomware-as-a-service gangs, but the admins banned ransomware topics in 2021.
- “Breach Forums” emerged in March 2022 to replace “RaidForums” when it was seized by the Federal Bureau of Investigation (FBI) the month before. Breach Forums has become one of the go-to forums for databases and access-as-a-service offerings. It has since been relaunched twice and was last seized by law enforcement in May 2024, only to emerge under new ownership a month later.
Below are some high-profile Spanish-speaking cybercriminals who dealt with business in Russian and/or English forums:
- Venezuelan cybercriminal Moisés Luis Zagala González, also known as “Nosophoros,” “Aesculapius,” and “Nebuchadnezzar.” Allegedly, this actor sold Thanos, Jigsaw ransomware, and Private Data Locker on “XSS.” The actor also participated in the Russian forums “Crdclub,” “Nulled,” “CryptBB,” and “Exploit,” and English forums “Hackforums” and “Kickass.” Zagala sold or rented out his ransomware software to hackers who used it to attack computer networks. He is on the FBI wanted list.
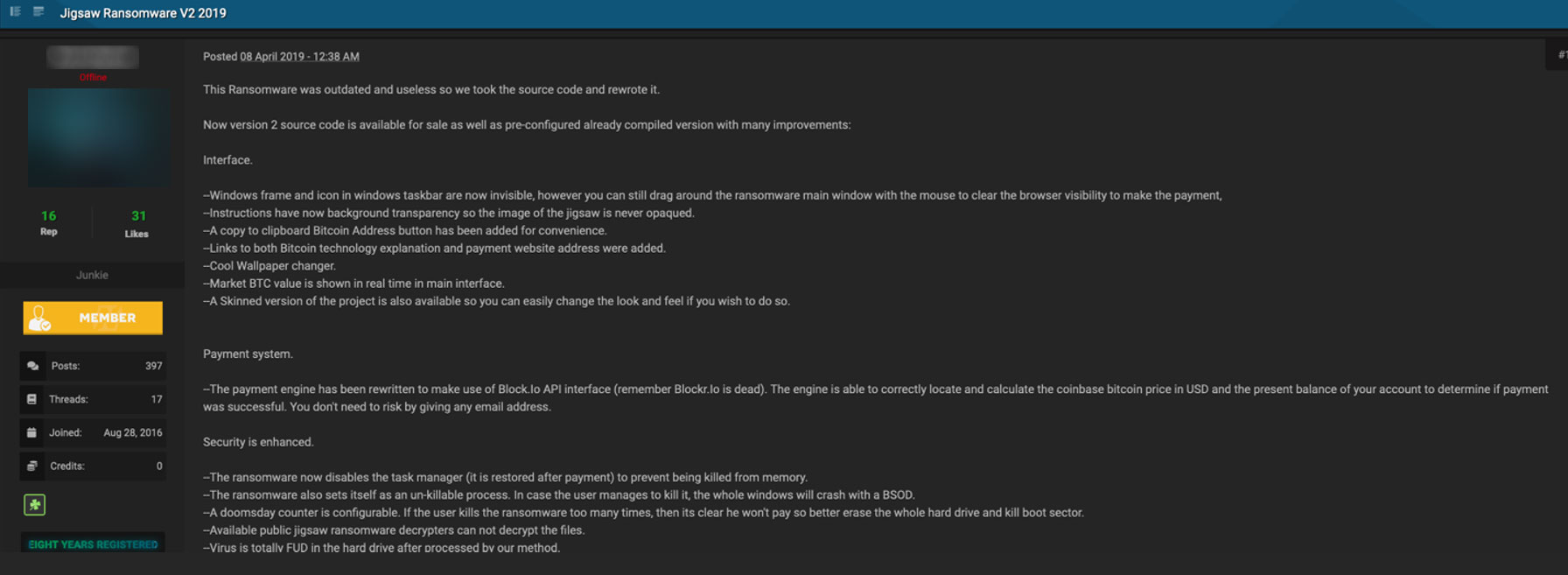
Figure 1. Aesculapius‘ Advertisement for Jigsaw Ransomware on Nulled
- José Luis Huertas (also known as "Alcaseca," "Mango," and “chimichuri”) created “Udyat,” a search engine dedicated to selling stolen sensitive information. He sold databases on the “Exploit” and also participated in “Cracked” and “Altenen.”
- The Kelvin Security hacking group leader, a Venezuelan national, was arrested in Spain in 2023. Kelvin Security has been active since 2013, leveraging vulnerabilities in public-facing systems to obtain valid user credentials and steal confidential data from breached systems. The group is believed to be responsible for 300 cyberattacks against organizations in 90 countries starting in 2020. Other group members are from Peru and Colombia.
- The user “USDoD,” also known as “EquationCorp,” was responsible for access-as-a-service offerings in the underground. His identity was later revealed as a 33-year-old man from Brazil. He was also previously known as “NetSec” on “Raidforums,” and later participated in “Breach Forums” in 2022.
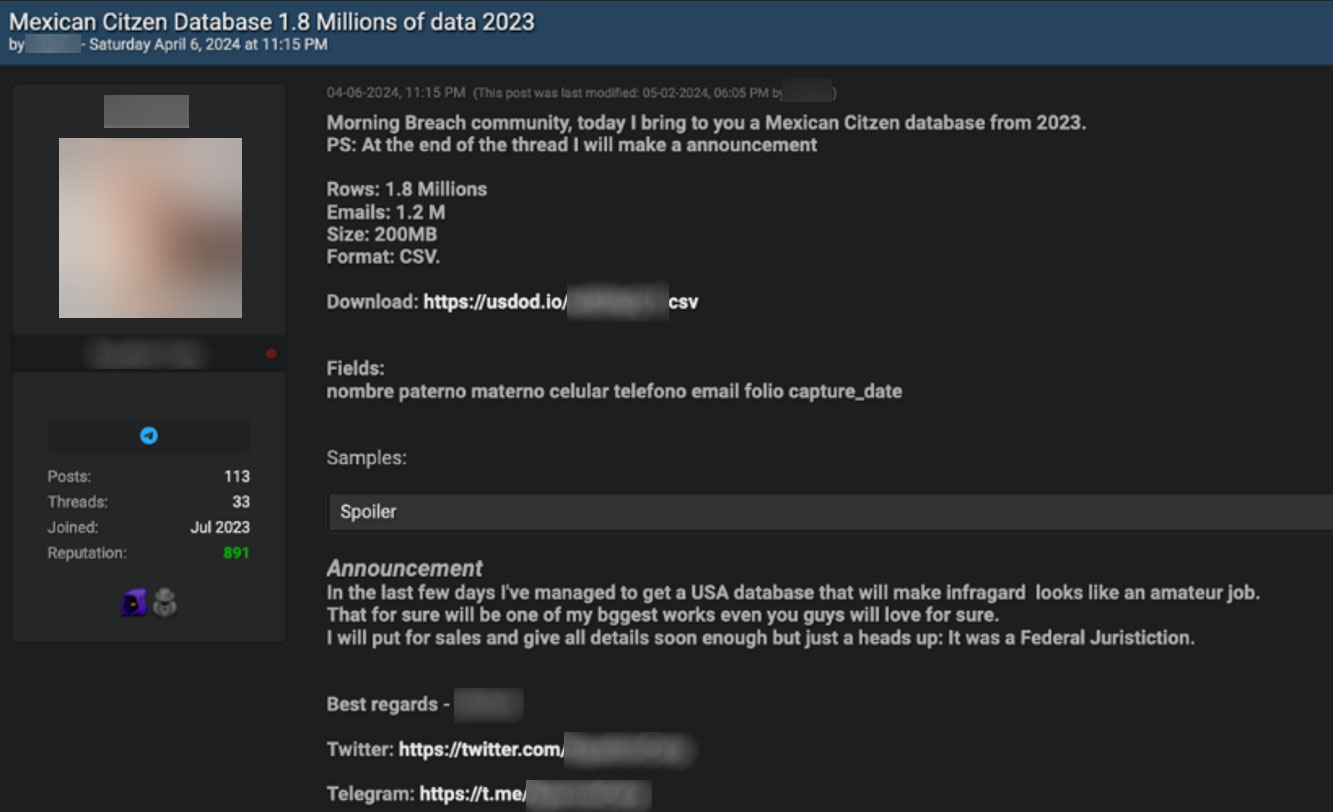
Figure 2. USDoD database advertisement on Breach Forums
Cyber-Enabled Offerings
The Telegram messaging app has become a popular channel for cyber-enabled offerings in the Spanish underground. While most channels require approval to join, some are accessible to all. Many of the channels are based in South America, Central America, Mexico, and Spain.
Pricing information is often omitted, making it challenging to identify a common currency and to compare similar products and services from different sellers. Unlike cybercriminal forums where digital currencies are the norm for payment, these Telegram channels use online payment sites like PayPal, Revolut, and Venmo to purchase goods.
The following are the common types of offerings:
- Bineros
- Phone and telecommunications company (telco) scams
- Stolen accounts for various services
- Check fraud scams
- Access as a service (AaaS)
- Selling social media followers and likes
- Travel discounts
- Fake medical documents
- Bill payment discount
- Doxing as a service
Bineros
In the Spanish-speaking community, cybercriminals that are associated with Bank Identification Number (BIN) attacks are called "bineros." A quick search for binero groups shows over 50 Telegram channels. Unlike carding where the credit card number is stolen, BIN attacks use automated bots and scripts to randomly generate countless payment card numbers. Bineros guess a combination of credit card numbers, expiration dates, and card verification values (CVVs). Once they find a working combination, they test the card by making minor purchases. The card’s credentials are then stored for further use.
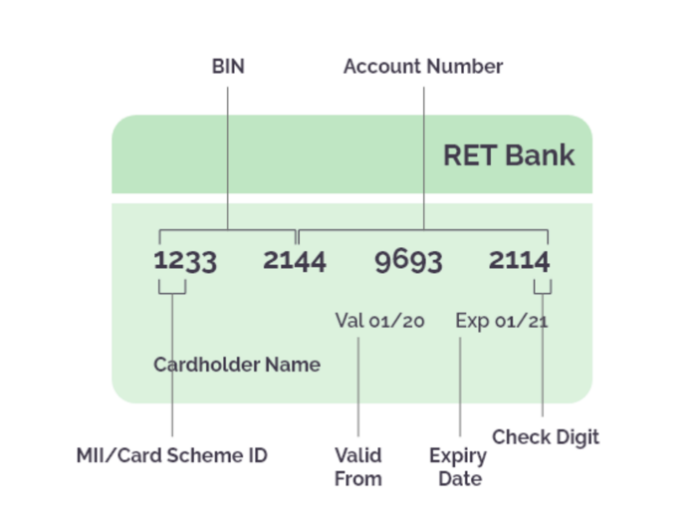
Figure 3. Credit card details that bineros try to guess (Image Credit: Arkose Labs)
Bot services that can facilitate this are advertised in the underground. While the skill level required to perform BIN attacks is relatively low, the bots help make the process faster, as this technology can cycle through hundreds of combinations in seconds.

Figure 4. Examples of binero Telegram channels
Credit card and bin checker bots are sold as a subscription. Prices start at $4 per month and can reach up to $25 per month.
For example, the “Rita Chk” bot’s price starts at $4. Each pricing tier comes with additional features such as free credit card giveaways and access to guides. The advertisement mentions a free credit card scraper. The sellers have also created a separate Telegram channel for reviewers to upload screenshots of successful purchases as proof of legitimacy.

Figure 5. “Rita Chk” bot services advertised on the ccsecretitos bins Telegram channel
Go to last slide Go to next slide- Go to previous slide Go to next slide
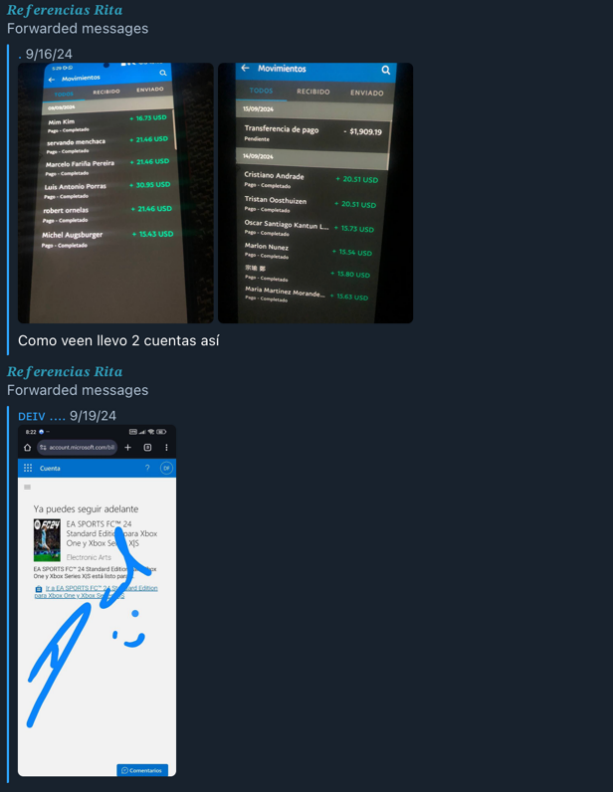
Figure 6. Screenshots showing “Rita Chk” positive feedback, taken from the ccsecretitos Telegram channel
Phone and Telco Scams
Another type of offering we encountered is unlocking services. Some channels offer this service specifically for iPhones. They are marketed for the supposed “recovery” of one’s own phone, but needless to say, those who avail of this service could have stolen the device. The example below is from “PERU FAKE.” The channel offers many services, including “iPhone unlocking,” “cellphone monitoring,” and “lost phone tracking.”
- Go to previous slide Go to next slide
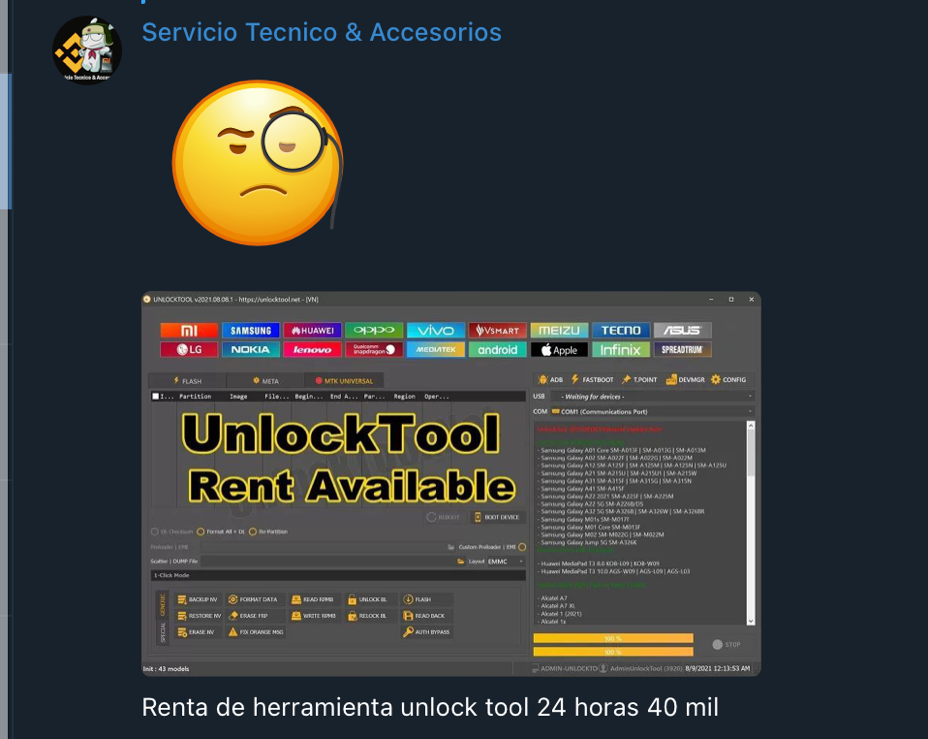
Figure 8. An ad from another seller on “Cronos CHK”
Sellers also offer eSIM (virtual SIM cards) from major Spanish telcos like Movistar, Vodafone, Orange, Yoigo, and O2. This can be used by cybercriminals to lend anonymity and credibility in targeted spamming or scamming attacks. Prices for eSIMs are often not explicitly mentioned, but they typically range from $10 to $50, with some sellers accepting crypto payments and escrow services (third-party verification services) to ensure secure transactions.
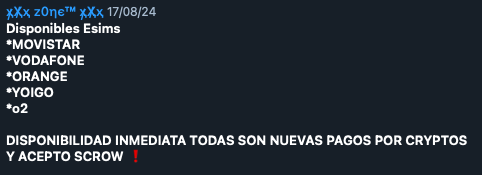
Figure 9. “Compras y Ventas ESP” group ad for eSIMs
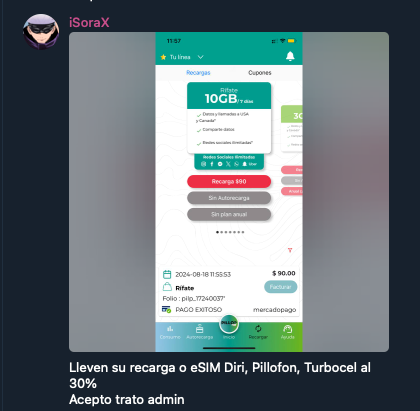
We have also seen ads for mobile phone balance top-ups. These tend to give the user a certain percentage of the balance more than what the buyer pays. In the example below from “Cronos CHK Chat”, the offer is 50%, so a 100 peso top-up would add 150 pesos to the user’s balance. In that same Telegram channel, another seller is offering a 30% top-up for Mexican mobile operators Diri, Pillofon, and Turbocel. For Pillofon and Turbocel we saw prices such as USD$3 (45 Mexican pesos) for 600 minutes.
- Go to previous slide Go to next slide
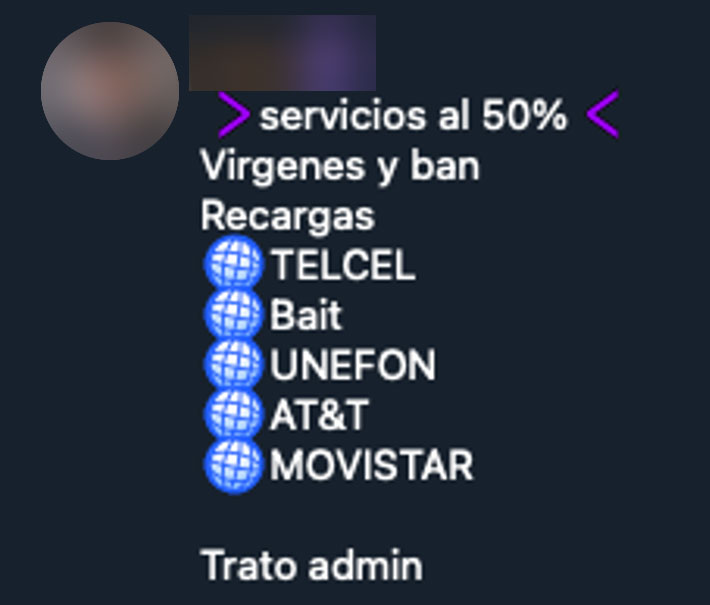
Figure 11. Ad for top-ups for different telcos
There were also offers for bulk SMS services on multiple Telegram channels. Prices start at $.01 and can be sent from many different countries. SMS verification codes for eating and streaming apps start at around $1 per SMS received. Other offerings include classes teaching how to use spamming bots, performing cash out services, investments, and more. Prices for these start at $150.
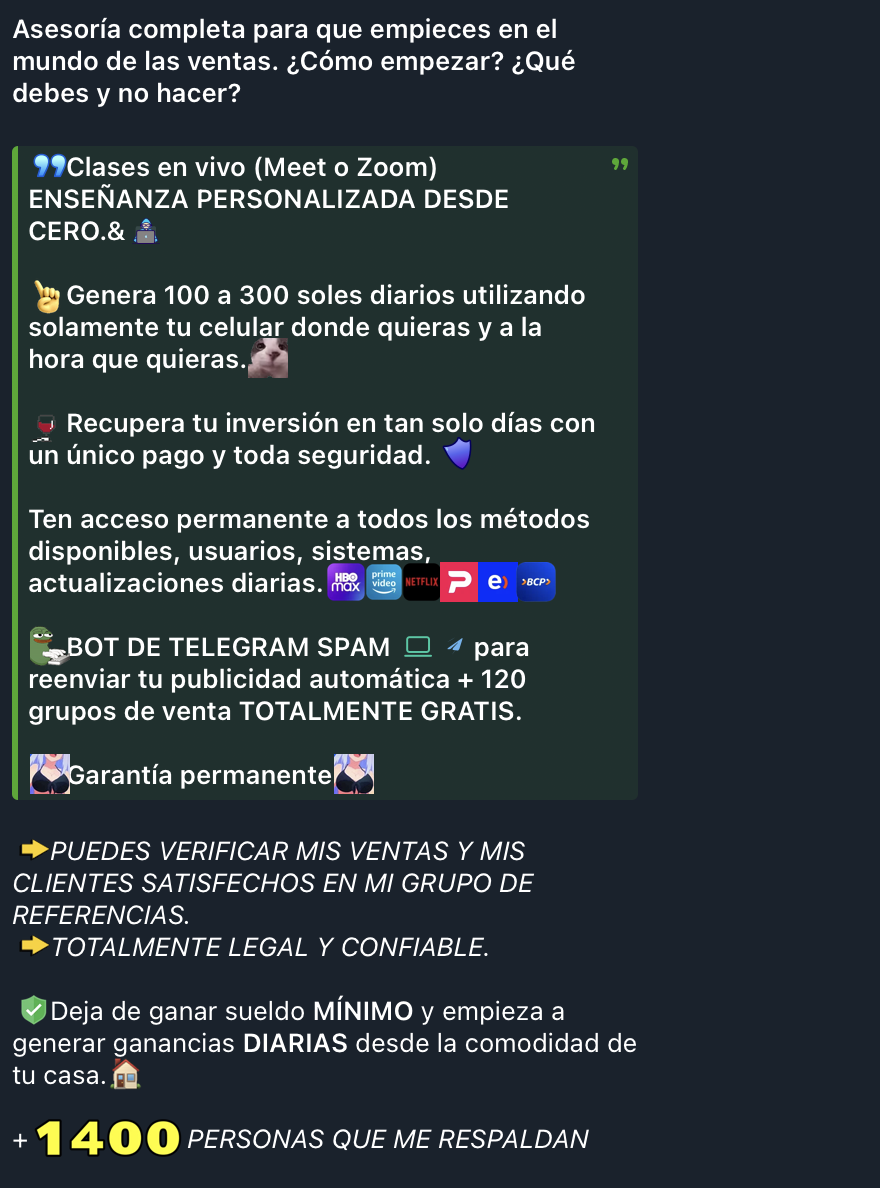
Figure 12. Investment classes offered on the “BINEROS DEL PERU” channel
Stolen Accounts for Various Services
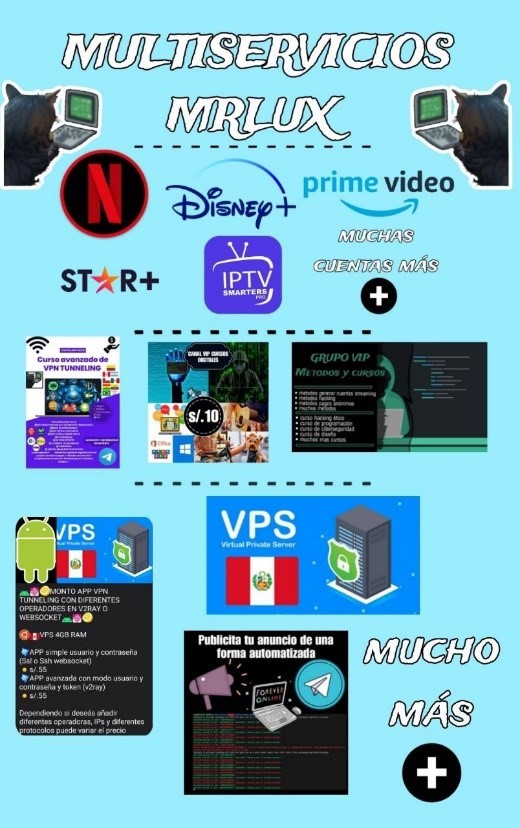
Many sellers also promote accounts for different services. These include streaming platforms such as Netflix, Disney+, Prime Video, Spotify, Star+, and IPTV shows.
The image in Figure 13, an ad from a certain MrLux in the Peru-based “BINEROS - Black Shop” channel, offers many streaming service accesses, as well as a Virtual Private Server (VPS). Another user from the same Peru-based channel offers access to the Euro Cup 2024 matches streams through IPTV.
Similarly, in a similar Peru-based group called “YAPE FAKE PERU,” (seen in Figure 15) a seller offers IPTV accounts for 8 pesos a month and Tinder+ and Canva Pro accounts for 15 and 5 pesos per month, respectively.
- Go to previous slide Go to next slide
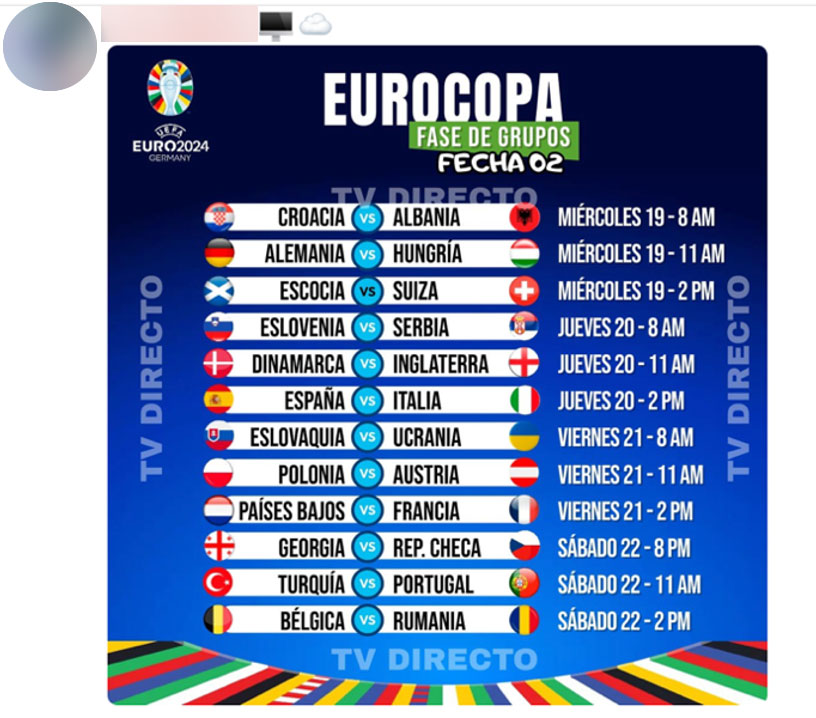
Figure 14. Advertisement from “BINEROS - Black Shop”
- Go to previous slide Go to next slide

Figure 15. “YAPE FAKE PERU” group offers premium accounts for a reduced price. Prices shown are in Peruvian soles.
In the “Vueltas Chipero” Telegram channel, a seller offers American PayPal accounts that supposedly have balance. These accounts are presumably stolen, perhaps from malware victims. The seller offers a $10k transaction and the buyer gets to keep $2k. This sounds very much like a money mule operation, but it’s unclear if the final product is selling the PayPal credentials or the money mule service.
In the “Compras y Ventas ESP” channel, seen in Figure 16, a seller is offering miscellaneous accounts, some local to Spain. Glovo is a food delivery service, so getting this account would presumably allow the buyer to get food delivered to them and charged to the account owner. Eroski is a supermarket, so perhaps such an account would allow the buyer to shop online and have groceries delivered to them but charged to the account owner. Other similar accounts on offer include loterias (the national lottery system in Spain), OnlyFans, and Burger King. The prices are not mentioned, but the seller provides a website.
The site displays a variety of accounts for sale. For example, Glovo food delivery accounts with a credit card configured in them are worth $3 each, but regular Glovo accounts are only $1 each. Burger King accounts are only worth $0.25 each, so the possibility of fraud is probably low.
In the “Cronos CHK Chat” channel, seen in Figure 17 and 18, a seller is offering Netflix, Spotify, ViX, and NordVPN accounts. For one seller, Spotify accounts go for 15 pesos (USD$0.75) each, or two accounts for 21 pesos (USD$1). Some also offer Spotify, Netflix, Disney, and HBO Max starting at $1 per month. This channel is related to cronos-chk[.]com, an online doxing service that reveals information about Mexican citizens.
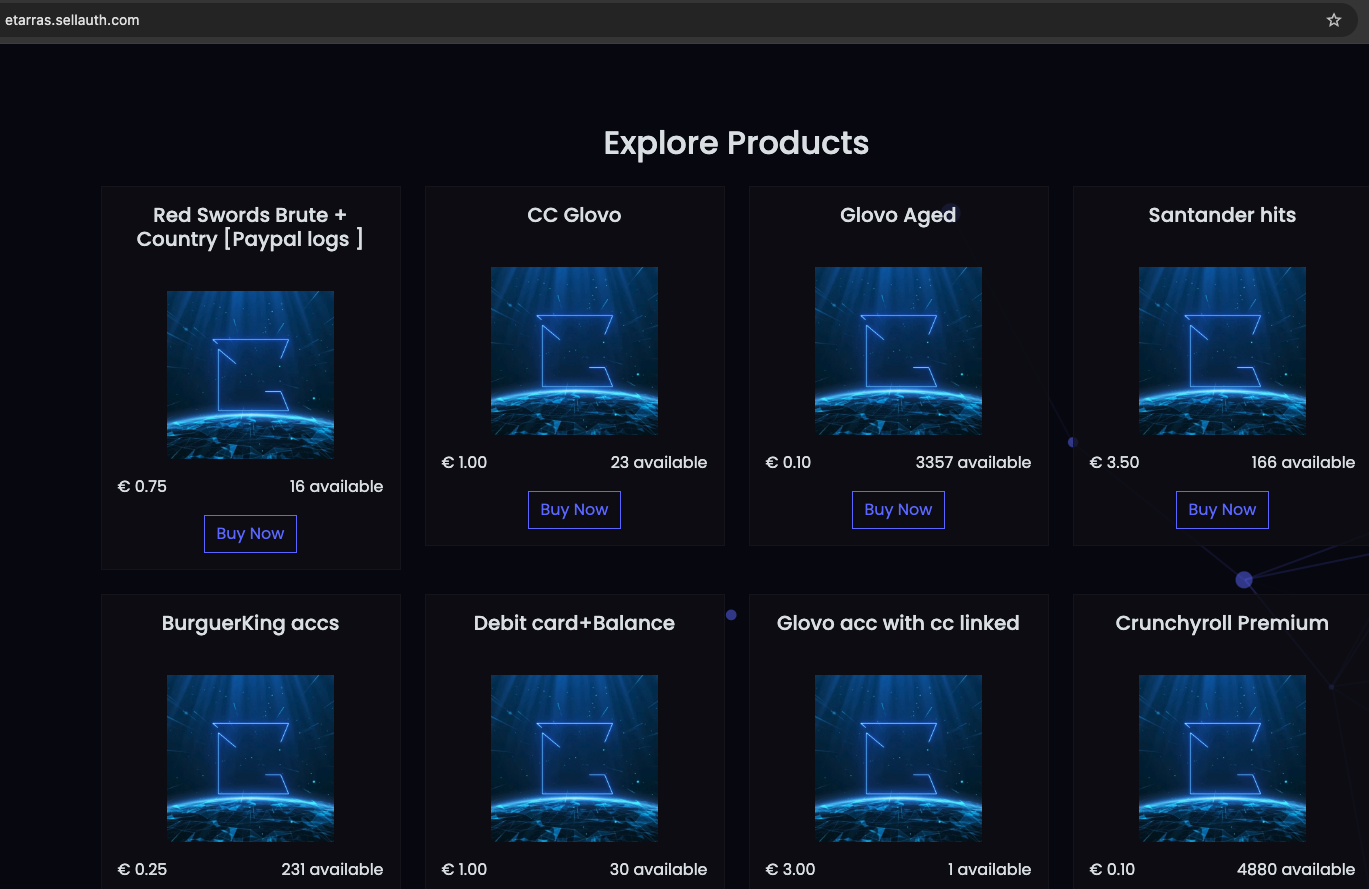
Figure 16. The seller from “Compras y Ventas ESP” redirects requests to a private site
Go to last slide Go to next slide- Go to previous slide Go to next slide
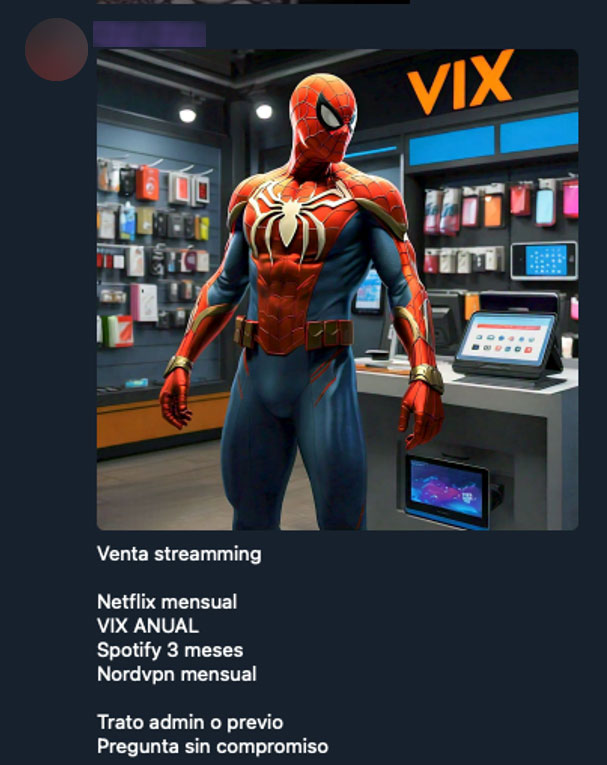
Figure 17. An ad for streaming service accounts from the “Cronos CHK Chat” group
- Go to previous slide Go to next slide
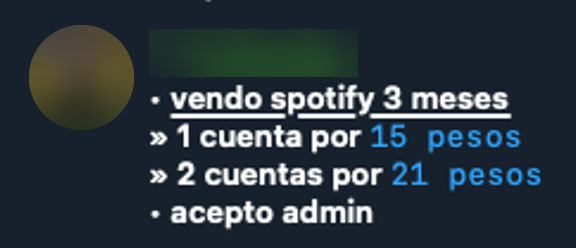
Figure 18. An ad for Spotify accounts from the “Cronos CHK Chat”
Cashout Services
Theoretically, these cashout services and methods allow the buyer to use an online service and then ask for a refund in a way that they receive both the goods purchased and the money back. In the banking industry, doing this is called “transaction reversal” and allows the fraudster to send money, and then revert the transaction, so that the money is never taken from the account, but arrives at the destination. However, we have not seen this before in the Spanish-speaking criminal underground.
Money mule recruitment services are often masked as “bank cashouts” or similar, which is deceitful, but not unheard of in these dark markets.
In the “CardHouse Latam” channel, a seller is offering cashout methods on TikTok and other apps.
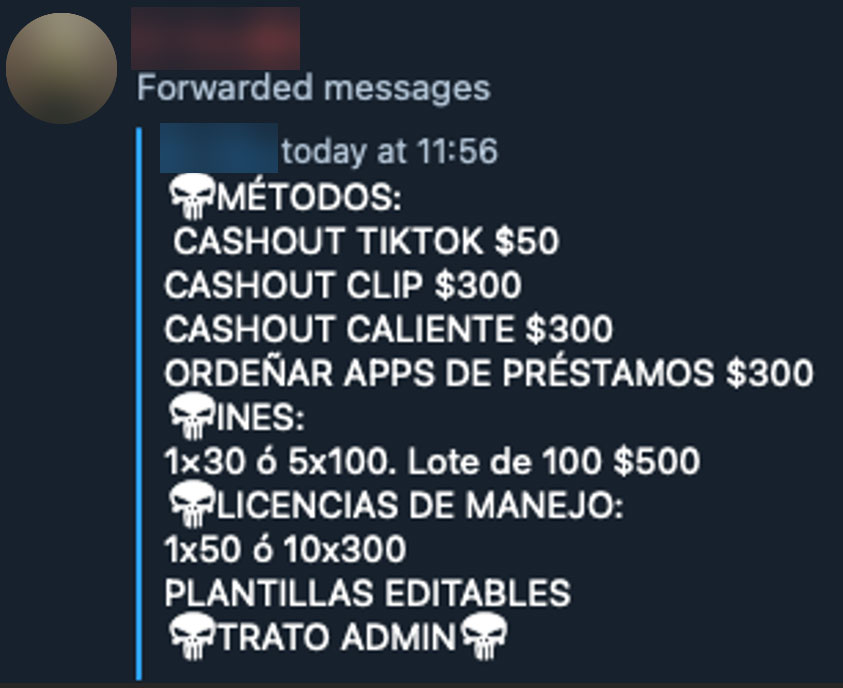
Figure 19. “CardHouse Latam” ad offering cashouts ”
In one of the Telegram channels we have been monitoring, somebody advertised a link to a related WhatsApp group. It turns out that this “Los Hijos de Kitah” channel belongs to an individual that sells cashout methods for popular retail websites like Walmart, Nike, Temu, and Shein. The same person also shows screenshots of successful reverted transactions on these platforms.
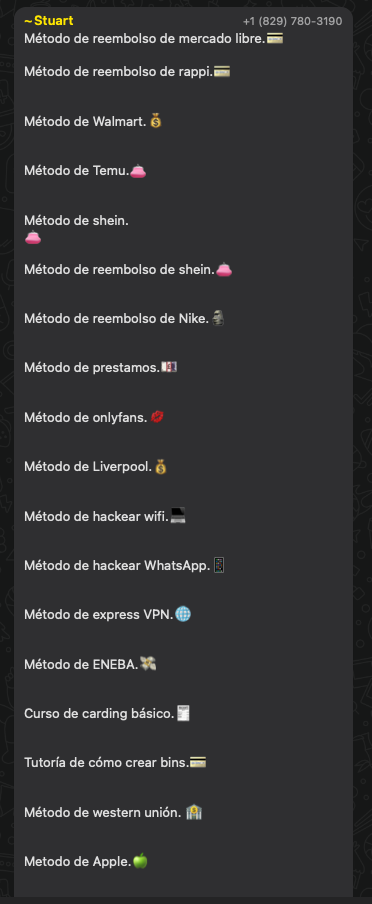
Figure 20. “Los Hijos de Kitah” WhatsApp group offering cashout methods and other related services ”
Check Fraud Scams
We also found many check fraud scams. They start with the seller opening a new bank account, and then depositing a large amount with a check. This check actually has no funds and will eventually bounce, but the bank already credited the check to the balance. This means that the criminal can spend that money before the bank realizes that it’s a bad check. The check deposits range from $5,000 to $15,000 with the money available immediately.
Another method is to use banking accounts that have been opened for a while, but owners who do not closely monitor this will not notice random deposits or withdrawals; some ads imply that the owner did not know about the fraud. Others charge an additional fee to use an established account with the alleged owner of the checking account. Some sample fees include $50, which would return $300; and $400, which would return $3500. Some other samples are in the screenshots below. The banks used most often are in the US, the Caribbean, South America, and Spain.
There is no US law requirement to make funds from a check immediately available for withdrawal, but legislation is different for each country. The number of days before funds are available varies depending on the bank or credit union. The sellers do offer a specific list of bank institutions that are available for this type of check fraud scheme. They can also take advantage of security glitches, like the one an American bank suffered from that allowed withdrawing money immediately after depositing fake checks into their accounts.
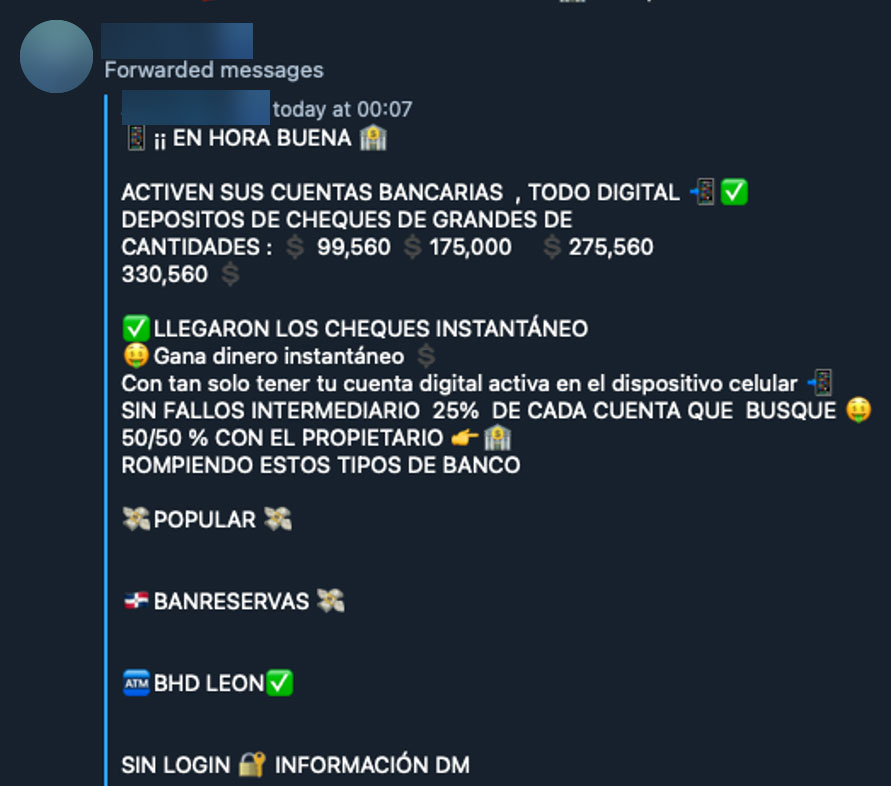
Figure 21. “Targeteros y Chiperos” channel offering to deposit large check amounts
Go to last slide Go to next slide- Go to previous slide Go to next slide
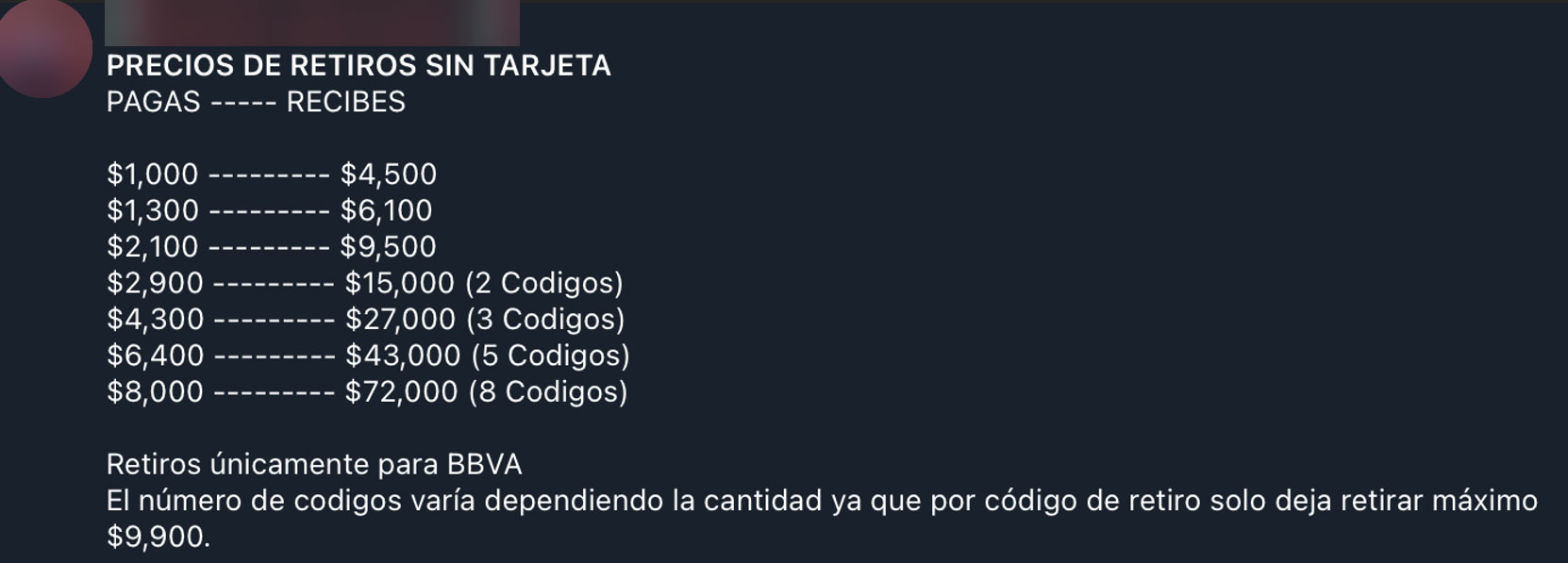
Figure 22. “Bineros Mexicanos” channel showing potential cashouts
- Go to previous slide Go to next slide
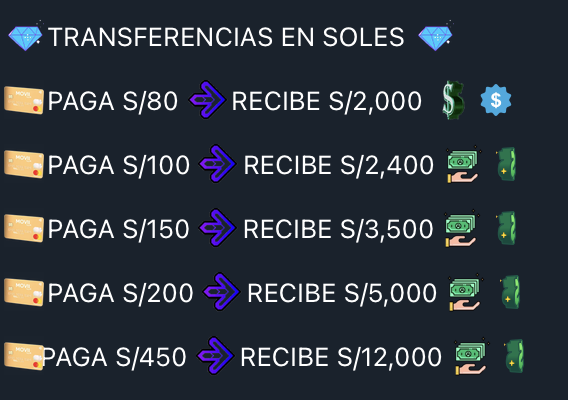
Figure 23. Sample Withdraw services from “Bineros Peru”
Access as a Service
Access-as-a-service (AaaS) offerings are also promoted in several Telegram channels. They offer logins to particular services, which are probably leaked credentials from data breaches.
We found one advertisement for logins into multiple types of health-related databases located in Argentina.
- An Argentinian pharmacy
- The Argentinian national system to ID taxpayers
- A hospital management system
- A leaked data searchable archive
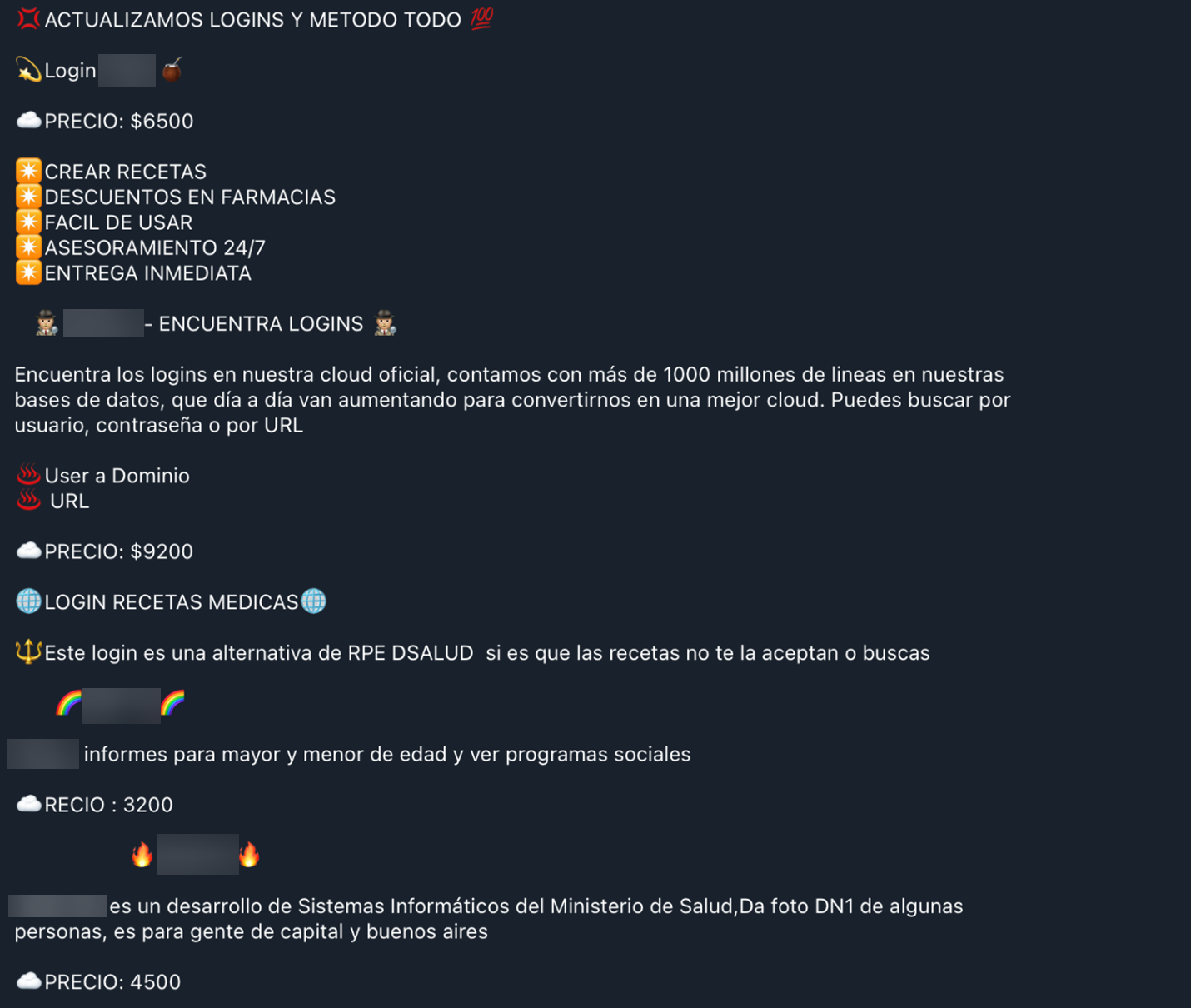
Figure 24. Ad for account logins on the Targeteros Calentones channel
Go to last slide Go to next slide- Go to previous slide Go to next slide
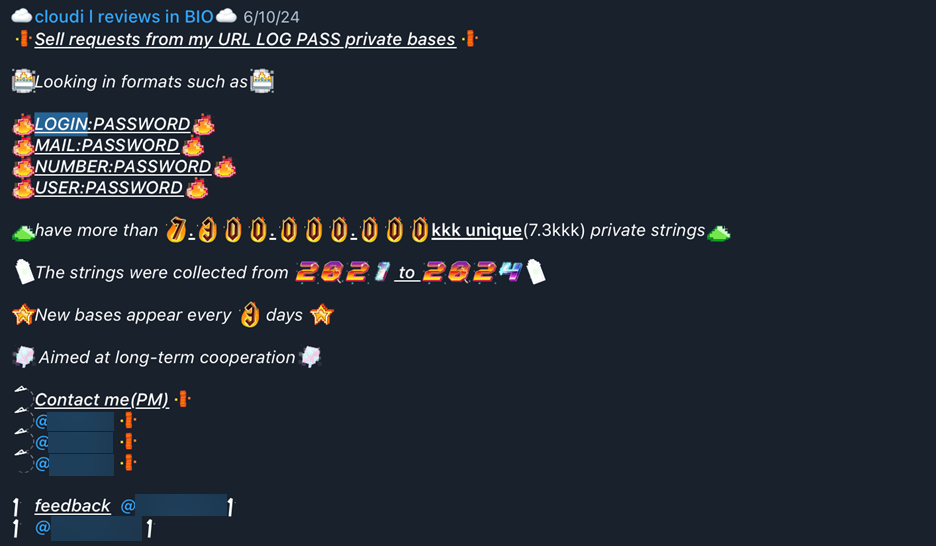
Figure 25. Advertisement for access to a database of 7,300,000,000 usernames/passwords dated from 2021-2022 from the Vueltas Chipero channel
Another popular offering is being able to do your own research for logins and passwords by buying an account for IntelX. This company advertises it as something similar to a search engine and data archive, where one can search Tor, I2P, data leaks, domain, IP, CIDR, Bitcoin addresses, and more. Currently, one researcher account costs around €2500 a year. These IntelX accounts were offered in multiple channels such as Bineros del Peru and Bineros Blackshop.
Selling Social Media Followers and Likes
Anyone looking to increase their number of followers, views, likes, and comments on social media accounts can purchase packages of 10-200,000 followers, and likes. 1000 Instagram followers or likes will cost around $2.50. Advertising a business to 1000 Telegram channels starts at $40 a week and can reach over $500 for 5000 Channels. A user from the Dominican Republic and Peru was offering 1000 Instagram and TikTok followers for $2. Users from Mexico also had similar pricing at $1.50 per 1000 followers.
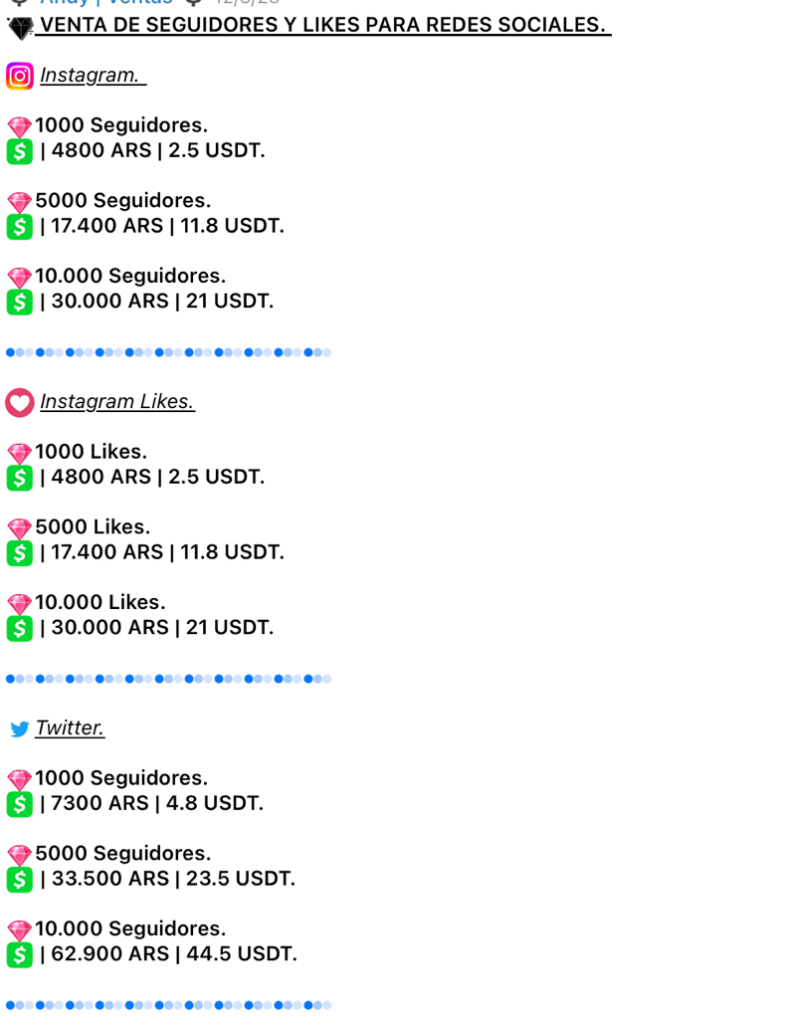
Figure 26. Likes and follower services from the “Bloody Ventas” channel
Go to last slide Go to next slide- Go to previous slide Go to next slide
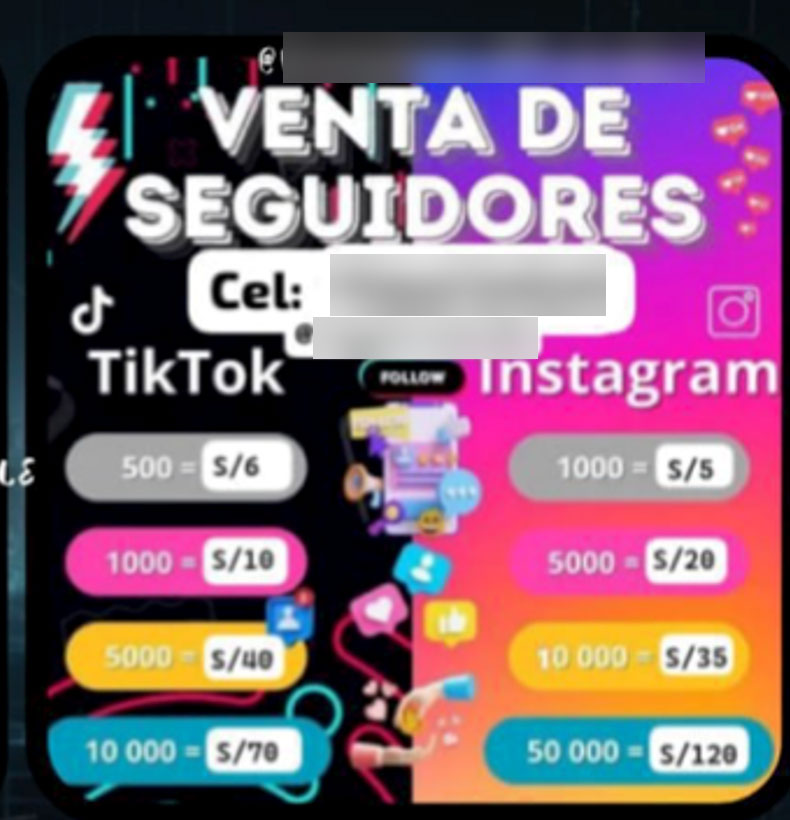
Figure 27. “PERU FAKE” ad offering social media followers
- Go to previous slide Go to next slide
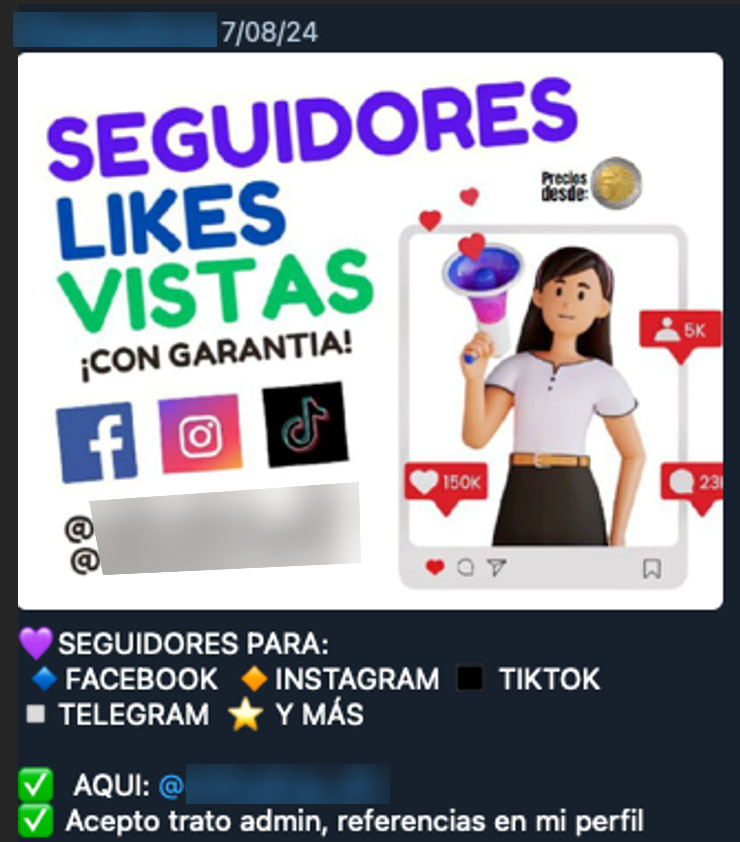
Figure 28. “YAPE FAKE PERU” group offers social media followers
Travel Discounts
Multiple channels also offered discounts for traveling. Cybercriminals are able to offer these either through services paid for using stolen credit cards or through leaked or hacked loyalty program accounts. Because of the cash value in these stolen travel points, cybercriminals will only have to pay 30-50% of the legitimate price of a plane ticket. Offerings include discounts on flights, resorts, and amusement parks. Other options we have seen involve adding miles or hotel points to accounts.
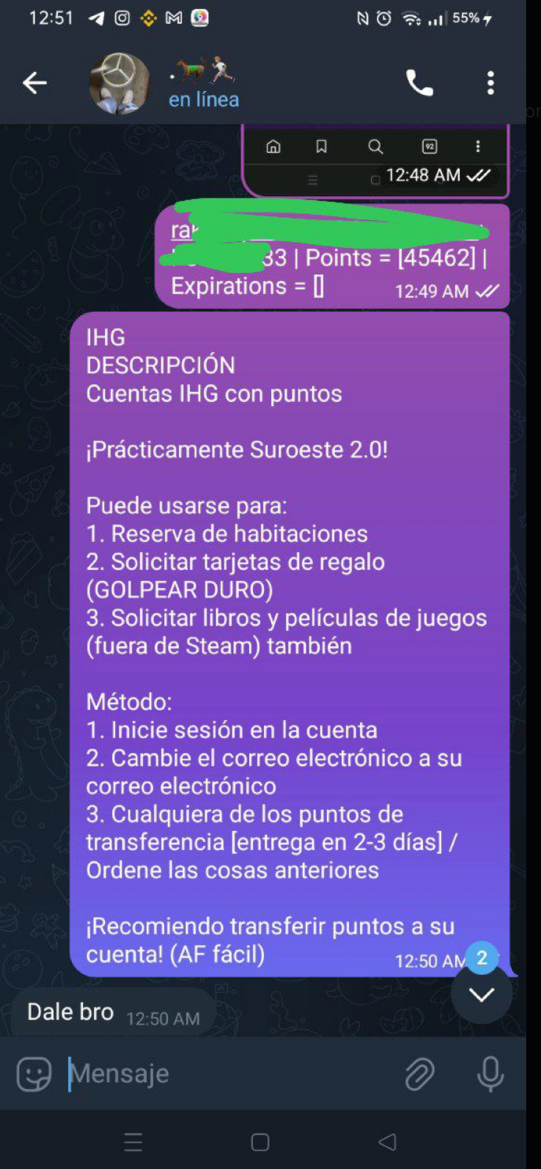
Figure 29. A message with instructions on how to move IHG Hotel points into another account from a Vueltas chipero member
Go to last slide Go to next slide- Go to previous slide Go to next slide

Figure 30. “Los hijos de Kitah” WhatsApp channel shows an advertisement for flights at 50% off
Fake Medical Documents
We also stumbled upon medical-related services provided specifically for Peru. Advertisements offered fake medical documents stating that one had an illness or disability, which could be used to take days off from work or to claim benefits. Some even come with an official doctor’s signature and seal. Turnaround for these services ranged from 24 to 72 hours and could be delivered as PDF files.
We looked into the social security programs of Peru to gain insight into why some would be particularly interested in faking their health status to obtain state or government benefits. Apparently, in 2018, permanent disability payments in Peru ranged from a minimum monthly disability pension of $150 to a maximum of $240 (500 - 893 soles).
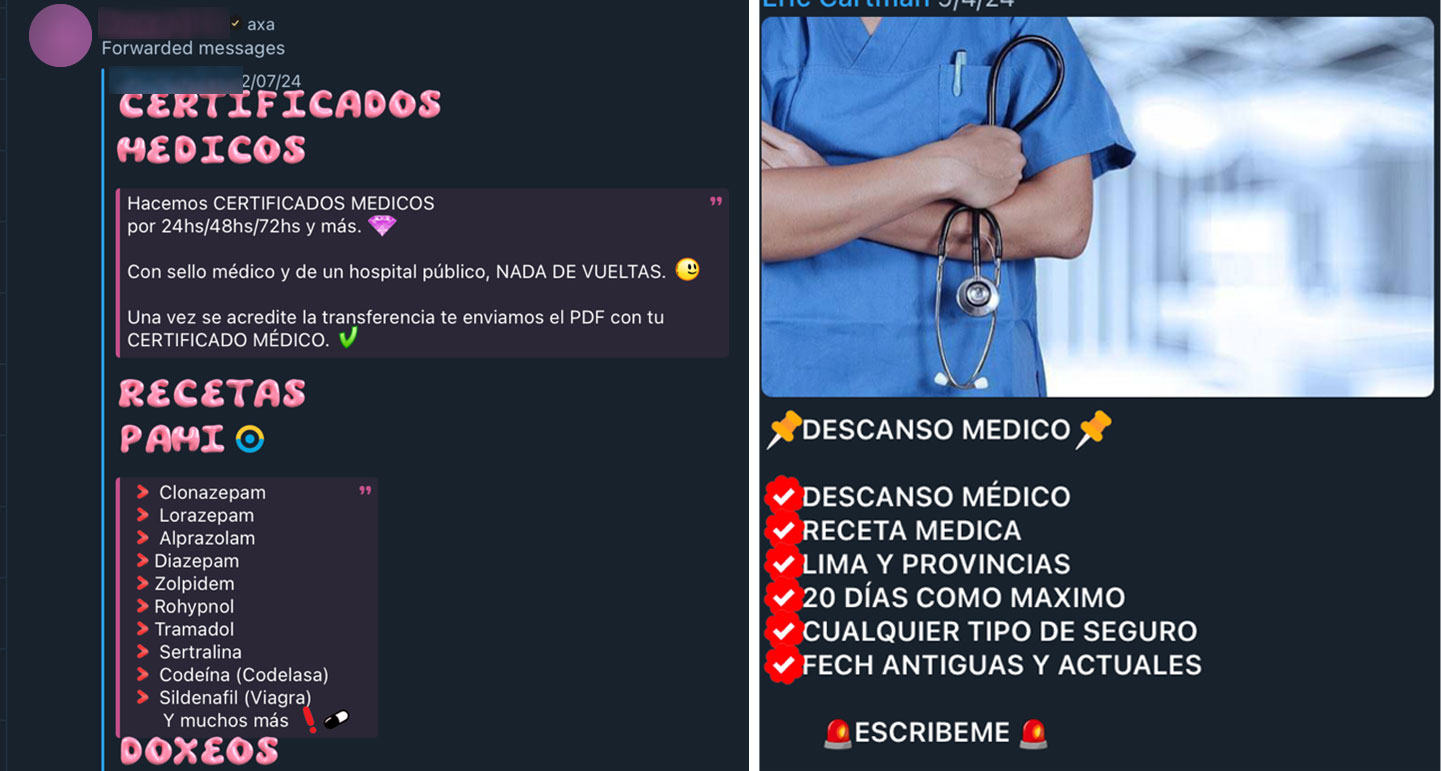
Figure 31. Advertisements for medical disability paperwork for people based in Peru from the Bineros del Peru channel
Bill Payment Discount
Some ads offer up to 50% discounts for bills such as rent, gas, water, electricity, phone, cable, hospital, traffic tickets, car insurance, loans, university tuition, and furniture purchases. The only requirement is that the buyer must provide the URL of where the bill needs to be paid.
This type of scam is not just specific to Spanish-speaking communities. We have also seen half-off bill offerings on TikTok, Facebook, and Instagram advertised in English. There is a strong possibility that some of these are outright scams. In many of these cases, we suspect that cybercriminals deposit fake checks or use stolen accounts and credit cards to pay these bills. We have also seen reviews of people saying their bills were never paid.
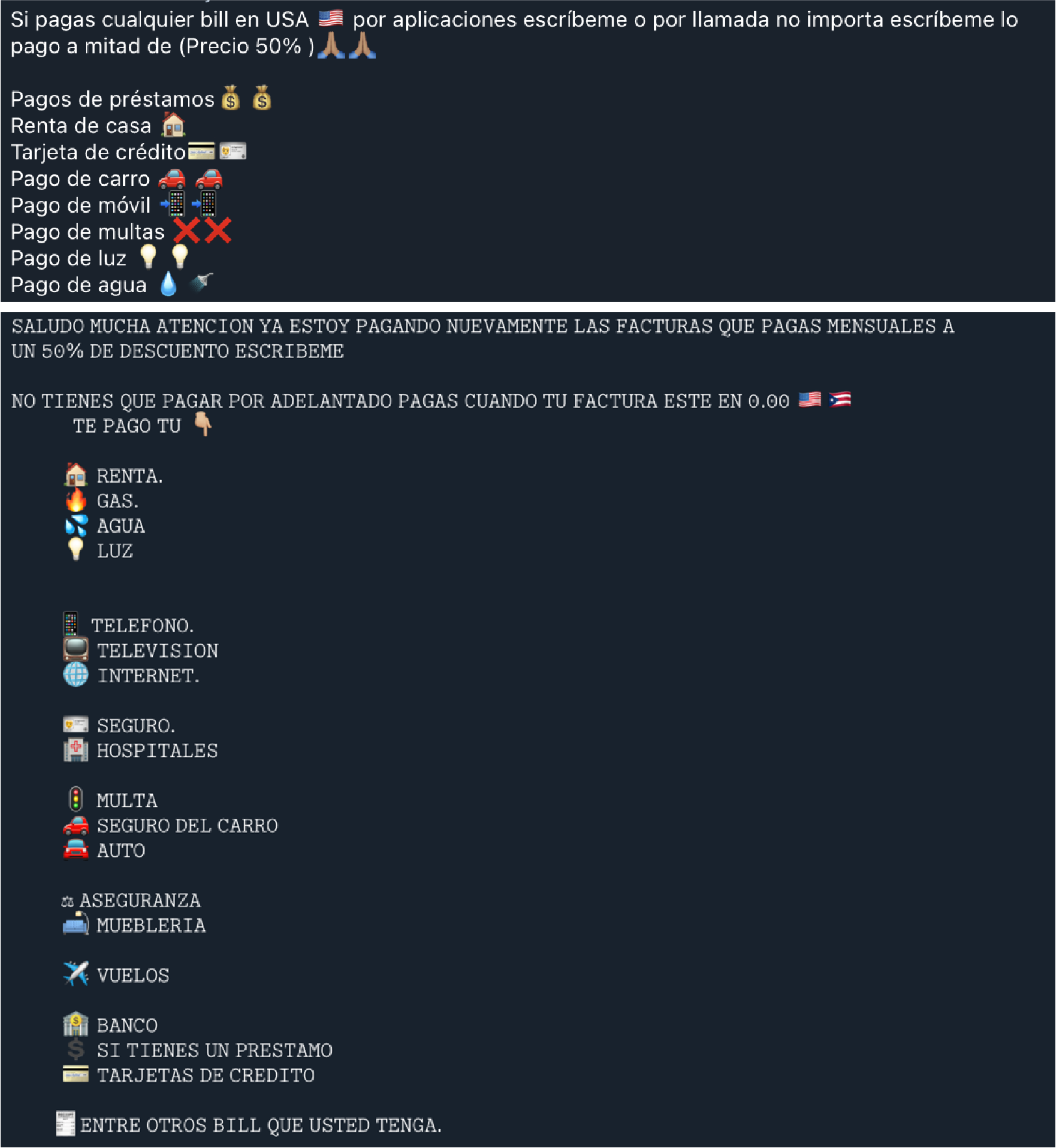
Figure 32. Ads for discounted bill payments on a Binero Telegram channel
Go to last slide Go to next slide- Go to previous slide Go to next slide

Figure 33. An advertisement posted in the “Los hijos de Kitah” WhatsApp group offering 50% off on bills in the USA
Doxing as a Service
Doxing-as-a-service offerings promise to disclose personal information from any specific target. Although doxing is not illegal per se, it is often used for harassment, stalking, intimidation, and identity theft.
The exposed information usually includes home address, photos, telephone numbers, work location, and more. Offerings for people in the US include social security numbers, tax forms, and driver’s licenses. They also include digital fingerprints for some countries. Additional services include genealogy records, criminal records, banking records, and prior work history. Sample pricing from an Argentinian seller included $4 for a name, address, phone number, and digital fingerprints for an additional $6. Offerings for Peru included additional items such as marriage certificates, driving records, birth certificates, and divorce certificates.
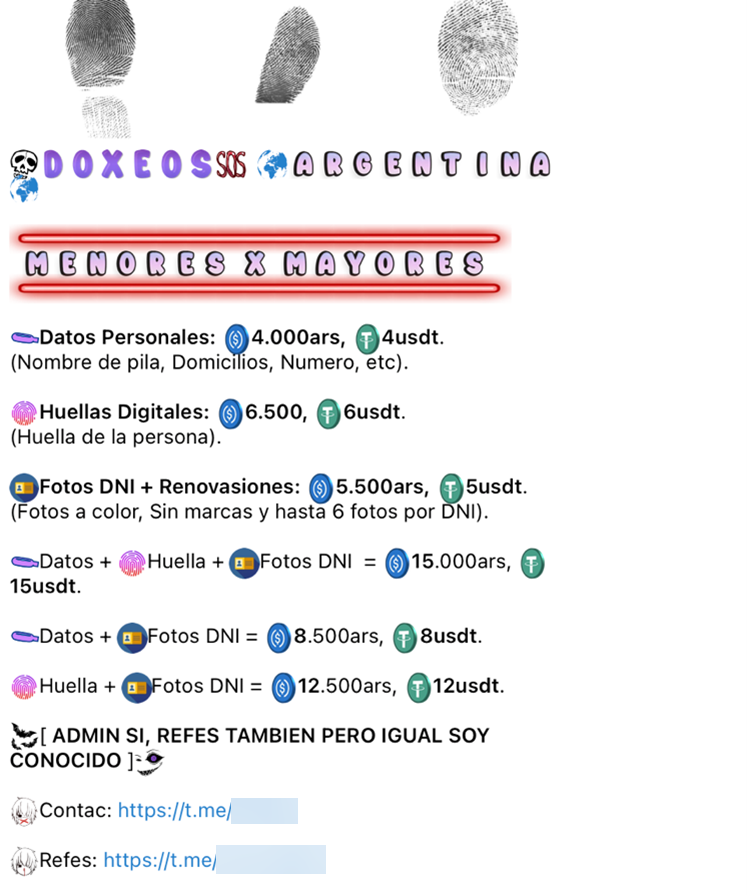
Figure 34. Ad for Doxing services in Argentina from the “Bloody Ventas” Telegram channel
Go to last slide Go to next slide- Go to previous slide Go to next slide

Figure 35. Ad for doxing services on the Bineros BlackShop channel
- Go to previous slide Go to next slide
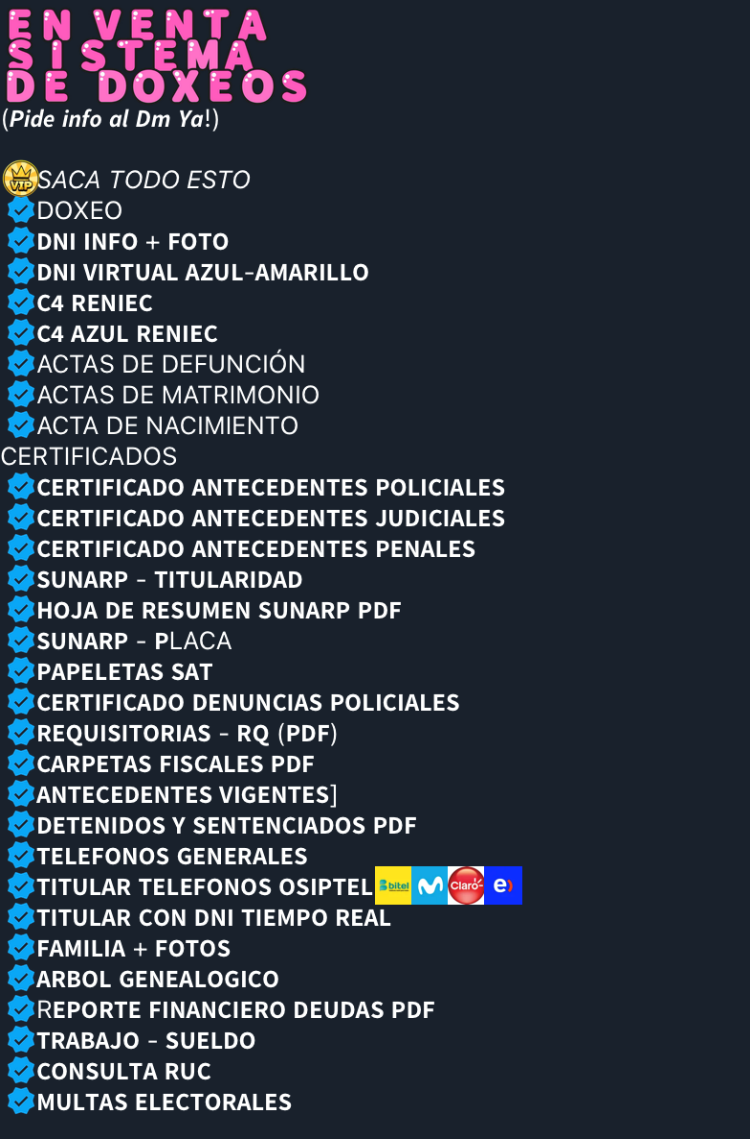
Figure 36. Doxing offerings in Bineros del Peru
Conclusion
In this research, we have described how the Spanish-speaking underground community is structured and what goods and services are being purchased and sold by cybercriminals. This community is mostly local and focused on monetizing the stolen goods that have been purloined from more complex attacks.
On the Russian and English-speaking dark marketplaces, we can see offerings for tools and services that enable cybercriminals to mount attacks. However, in the Spanish-speaking underground, we have not observed offers for tools that can launch assaults. The offers are focused on the byproducts of those attacks, such as account credentials, credit card numbers, and the like. The most likely reason for this is that Spanish speakers utilize other international criminal markets to obtain the tools for attacks, and once those are successful, they sell the spoils in the local underground.
Another interesting development in this criminal underground is the switch to Telegram as the tool of choice instead of web forums. The app is probably favored because it is known for not having strict moderation regulations. However, Telegram recently updated some policies, and we have yet to see whether this will diminish illegal transactions facilitated through the app.
We will keep monitoring new developments and report on new trends that will emerge in the cybercriminal underground. To learn more about the underground, read our past research.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Storie correlate
- Metaverse or Metaworse? How the Apple Vision Pro Stacks Up Against Predictions
- Bridging Divides, Transcending Borders: The Current State of the English Underground
- Generative AI in Elections: Beyond Political Disruption
- The Illusion of Choice: Uncovering Electoral Deceptions in the Age of AI
- Pushing the Outer Limits: Trend Micro 2024 Midyear Cybersecurity Threat Report
Ultime notizie
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks