From Bounty to Exploit: Cybercriminals Use Crowdsourcing for New Attacks
By David Sancho
Cybercriminals today have access to any resources they need to exploit and extort victims, and their resources continue to grow. While they do not have regular research and development departments as we know them, they have developed a way of coming up with new attacks by crowdsourcing their offensive research and development processes. In this entry, we attempt to explain criminal research and development in the form of public contests.
Modern cybercrime is a global dynamic community made up of separate groups interconnected by the so-called criminal underground. These criminal communities allow each gang to outsource criminal services, as well as to buy and sell software and development services, vulnerabilities, and any other useful resource, from stolen credit cards to network credentials. These groups also use this thriving interconnected network to recruit new members.
Cybersecurity defenders constantly develop ways to counteract each cybercriminal attack, similar to a massive cat-and-mouse game where each side tries to one-up the other with new ways of attacking and defending.
In the last two years, we have observed an increasing number of malware actors holding public contests in the criminal underground to come up with creative new attack methods.
In this article, we describe the different contests we have been witnessing and why we believe that these contests are a dangerous innovation in an already well-developed cybercriminal market.
What are these contests?
These contests are public calls for articles asking for technical content featuring offensive methods. They can be limited to a particular domain or be more generic in nature. Any forum member can submit a technical text proposing a new attack, technique, vulnerability, or offensive method. The organizer of the contest offers a prize (sometimes prizes) that will be awarded to the best or more innovative of those articles.
In this way, criminal actors could reliably get an edge in the cat-and-mouse competition against network defenders. If they keep running these contests frequently, eventually they could find a paradigm shift that would significantly alter the offensive status quo. It is therefore important to know what they are doing to prevent a new way of attack that will catch us unaware in the future. Indeed, it is possible that these contests would breed an innovation significantly challenging for cybersecurity.
In the next sections, we summarize the kinds of context we have been seeing and why they are relevant.
Contests seeking talent
This is the malware group equivalent of a singing or talent competition such as “American Idol” or “America’s Got Talent.” Although these talent-seeking contests are not the most frequent kind, we have spotted them in the past and believe that their relevance lies in possibly hiring the best candidates to develop their newer malware strains.
Take for instance the following post from a criminal actor in an “exploit” forum posted on Nov. 16, 2020. The translation is as follows:
Loader development contest. Prize fund: BTC 2
Friends! Our big and tight-knit team is ready to reward your talents.
We value your work and time, and we are ready to pay the best of you!
At the moment, we need coders who can develop simple and easy-to-use loaders more than ever. Not just develop them, but do it beautifully, and in a nonconventional way. Show us something new, not used and abused source code from GitHub.
So, we are starting a small, but a very interesting contest!
We are ready to offer a financial reward and further cooperation to two to three developers, whose projects will contain fresh solutions for available tasks.
You can get the software requirements specification via PM by mentioning that you're contacting us regarding the contest. We aren't forcing you to participate, but those two to three developers who will surprise us with their approach to our tasks can count on a mutually beneficial relationship with our team.
The prize fund (deposit) will be split between two to three frontrunners of the contest in equal parts. The criteria that will be used to evaluate your work are listed in the software requirements specification.
We are a large and well-working team with lots of experience. We have a decent resource base for your growth in the future.
We have a ton of work to do and lots of plans for the future. We are fully autonomous and have a full array of tools to work with.
What seems fantastic to you is ordinary to us.
The goal of this contest is to hire several developers for our team. We aren't interested in purchasing a loader in a one-off deal. We are interested in constant, pipelined development, creativity in solving problems as well as stability and decency on your end.
The prize fund of 2 bitcoins (US$38,061.60) is sizeable. This would be the equivalent of around 40 months’ worth of salary for an average software developer in Moscow, and even divided among the top three winners, it would still amount to over a year’s worth of salary for each of them.
Contests seeking knowledge
The second type of contest is knowledge-driven, where cybercriminals seek articles that bring forward the knowledge level of the offensive technology field. The following is an example of a translated post for one such contest:
TOPICS PARTICIPATING IN THE CONTEST:
Unorthodox ways for procuring private keys and wallets.
Staking, farming, and landing, unusual proprietary techniques for passive income.
Mining in 2021. Mining types, equipment (apart from the standard Bitmain), unusual mining software.
A big encyclopedia. Describe in layman's terms the most unorthodox and non-standard nuances of the cryptocurrency protocols.
Smart-contracts and everything to do with them, how to work with them.
NFT - where to begin? From understanding the fundamentals to making your first profits.
Custom software for working with cryptocurrencies (private keys, parsing tools, brute forcing tools, and so on).
A review of hardware wallets and the specifics of working with them.
Tokens, creating and promoting (all possible networks).
Analysis (technical and financial) of cryptocurrencies.
Security for working with cryptocurrencies, apart from the trivial stuff.
DeFi-segment, exclusive articles on the subject in general.
Setting up your own blockchain server for the major cryptocurrencies.
Automating payments when working with cryptocurrencies, managing payments, processing data.
REQUIREMENTS FOR THE ARTICLES:
This must be the first time your article is published, and the article must be unique (exclusive).
The article must be informative, covering all the aspects of the suggested topic, describe mechanisms, applied practices and tools.
Technical details must be provided (algorithms, implementation code snippets, graphs).
The article must be at least 5,000 characters long (without spaces).
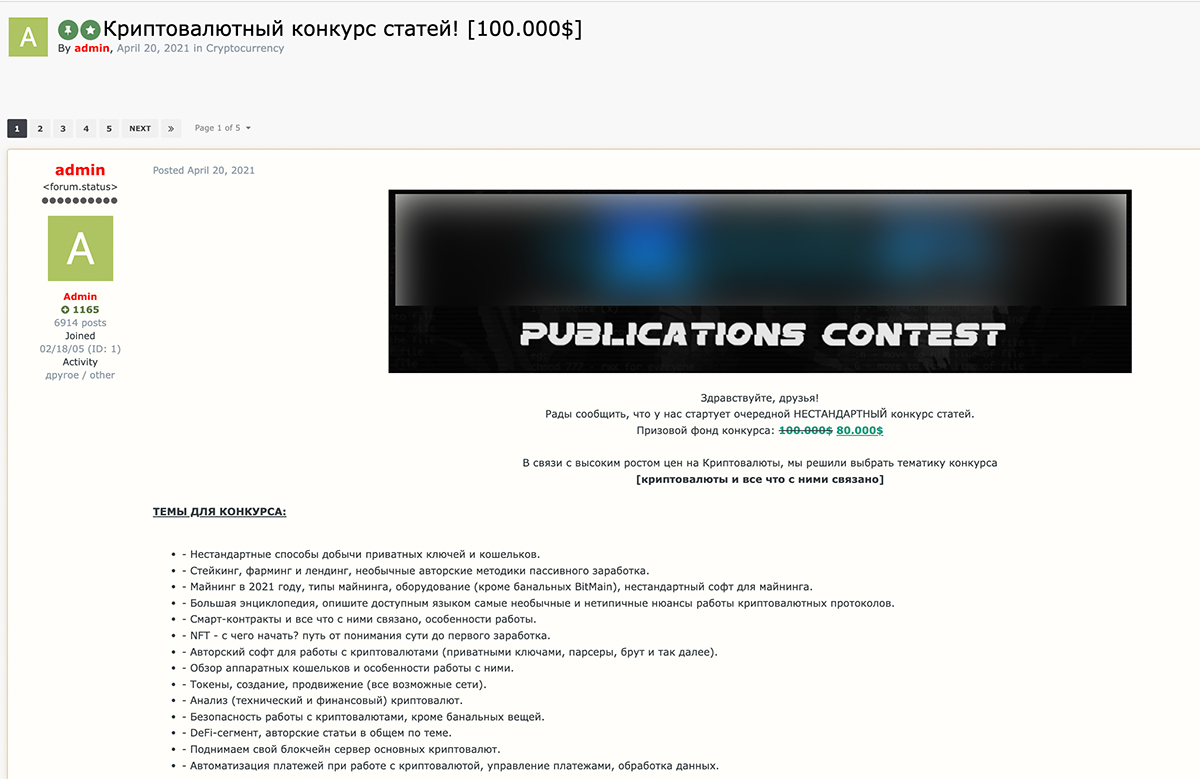
In this context, the organizers are looking to increase knowledge in the cryptocurrency field. Paradoxically, the prize is set in US dollars and not in cryptocurrency, as one might expect. These contexts are geared toward experts on the field and, though they favor technique-based knowledge as well, including articles that explain protocols and dig up unusual software.
Figure 1. Forum contest regarding cryptocurrency exploitation
Often, we observe more generic calls for articles that don’t limit the topic to a single domain. In fact, there is one cybercriminal forum that runs a series of contest that is currently in its seventh iteration, with the cybercriminals running the contest every few months. Both the participation and interest in this contest have been steadily increasing alongside the increase in prize offerings:
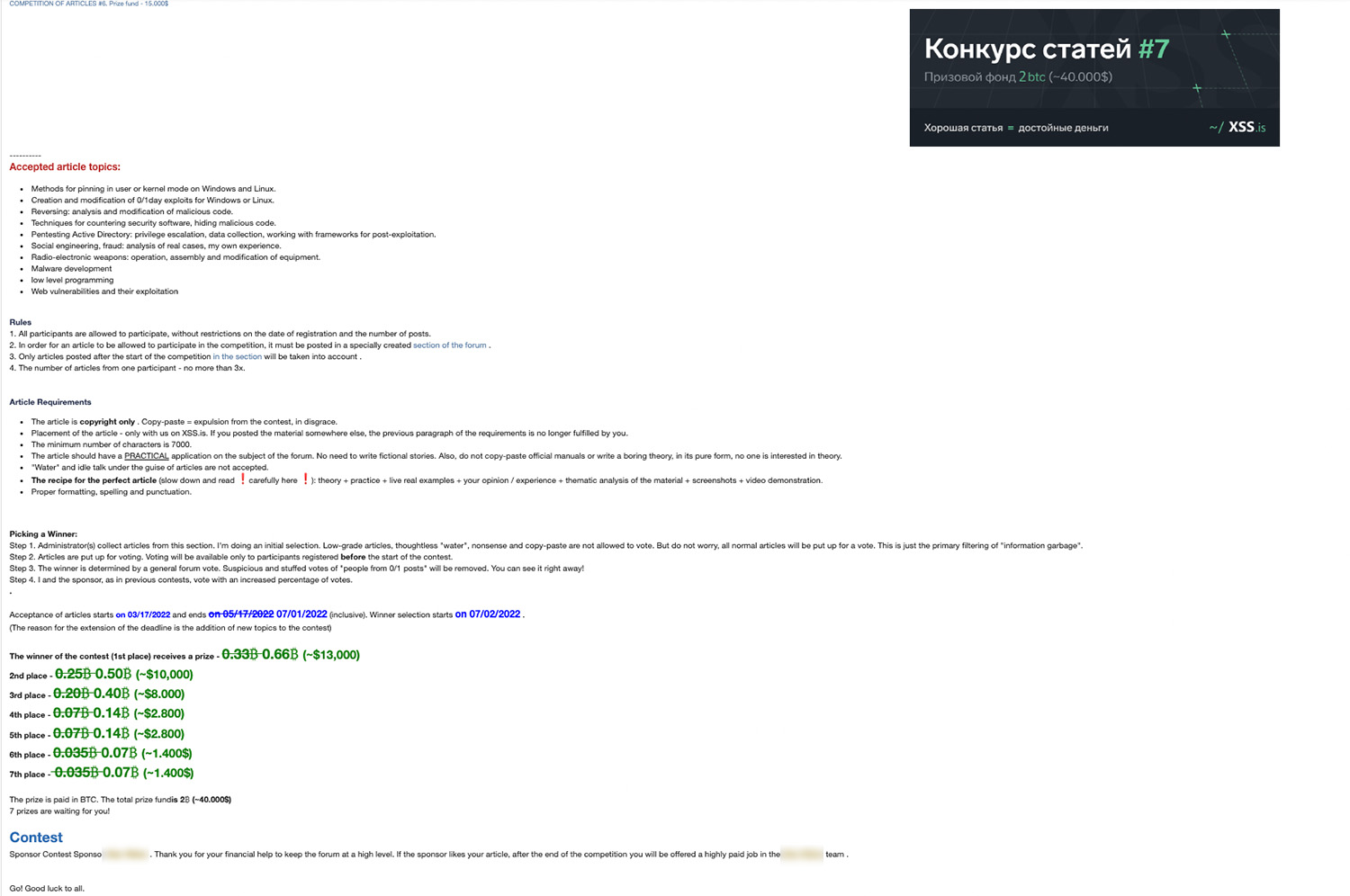
We are launching our ARTICLE CONTEST #7. The prize fund is BTC 1 (~USD 40,000).
We accept articles on the following topics:
Methods for gaining persistence in the user or kernel mode in Windows and Linux.
Creating and modifying 0/1-day exploits targeting Windows or Linux.
Reverse engineering: analyzing and modifying malicious code.
Methods for counteracting protection software, hiding malicious code.
Active Directory penetration testing: escalating privileges, collecting data, working with frameworks for post-exploitation.
Social engineering, fraud: studying real cases, sharing personal experience.
Radio and electronic equipment: using, assembling, and modifying the hardware.
Rules
All forum members can participate, regardless of their registration date or post count.
To submit your article for the contest, you must post it in the dedicated forum section
We will consider only the articles posted in the appropriate section after the contest start date.
One participant can submit no more than three articles.
Requirements for articles
Only original articles are accepted. If you copy paste anything, you will be kicked out of the contest.
The articles must be posted on [this forum] only. If you post your text anywhere else, you are already violating the previous rule.
The minimum character count is 7,000.
The article must be of PRACTICAL value related to the forum activities. Don't write about imaginary cases. Don't copy paste official guides or write about boring theory either. Theory in its pure form is of no interest to anyone.
We do not accept waffling or empty rhetoric in articles
It is interesting to note the range of topics in this contest, as the topics are broader in scope than the previous cryptocurrency-focused contest. Their applications are also eminently practical: The organizers only want offensive techniques that can be put to use immediately. The topics they cover are the main stages of an intrusion, namely social engineering, vulnerability exploitation, privilege escalation, counteracting defense software, gaining persistence, and generic malware technology. This could mean that the criminal underground is also interested in the internet of things (IoT) as a topic in any of its dimensions, such as entering an IoT network or using an IoT device an attack target, either for the device’s capabilities or perhaps for the data it can hold.
Figure 2. XSS7 Contest
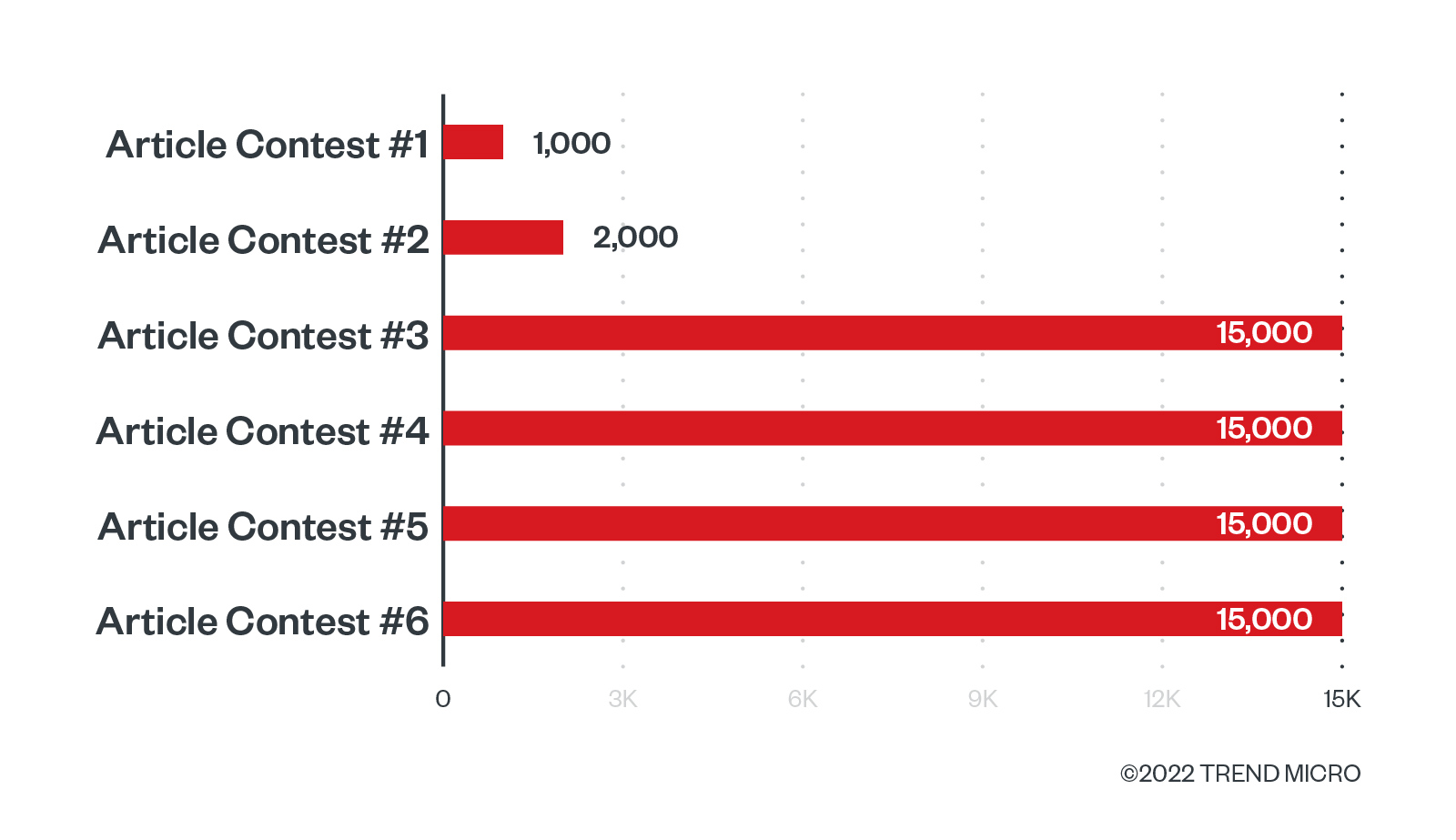
Again, the prize is quite high: 1 bitcoin (US$19,030.80). These criminals are investing quite a large sum of money in order to produce new offensive capabilities. It is also important to bear in mind that this is the last one in a series, in which these same organizers are running the same kind of contest every few months. The prizes offered in this contest series have been going up as well:
Figure 3. The growth of contest prizes
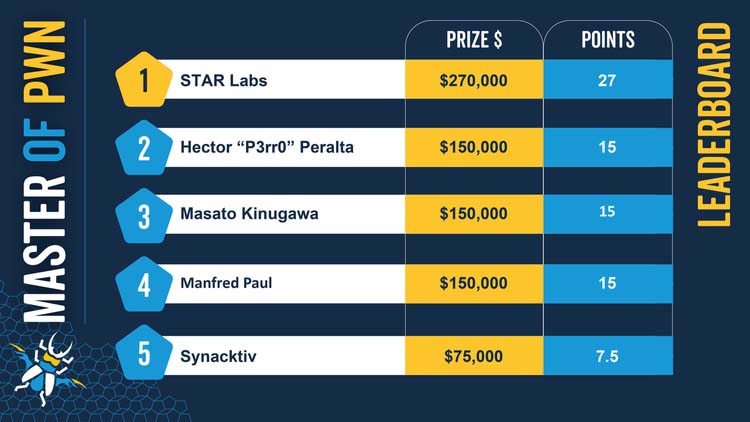
As a point of comparison, the white hat vulnerability-seeking contest was paying participants US$270,000 for the most valuable bug found in their most recent edition in Vancouver.
Figure 4. Pwn2Own leaderboard
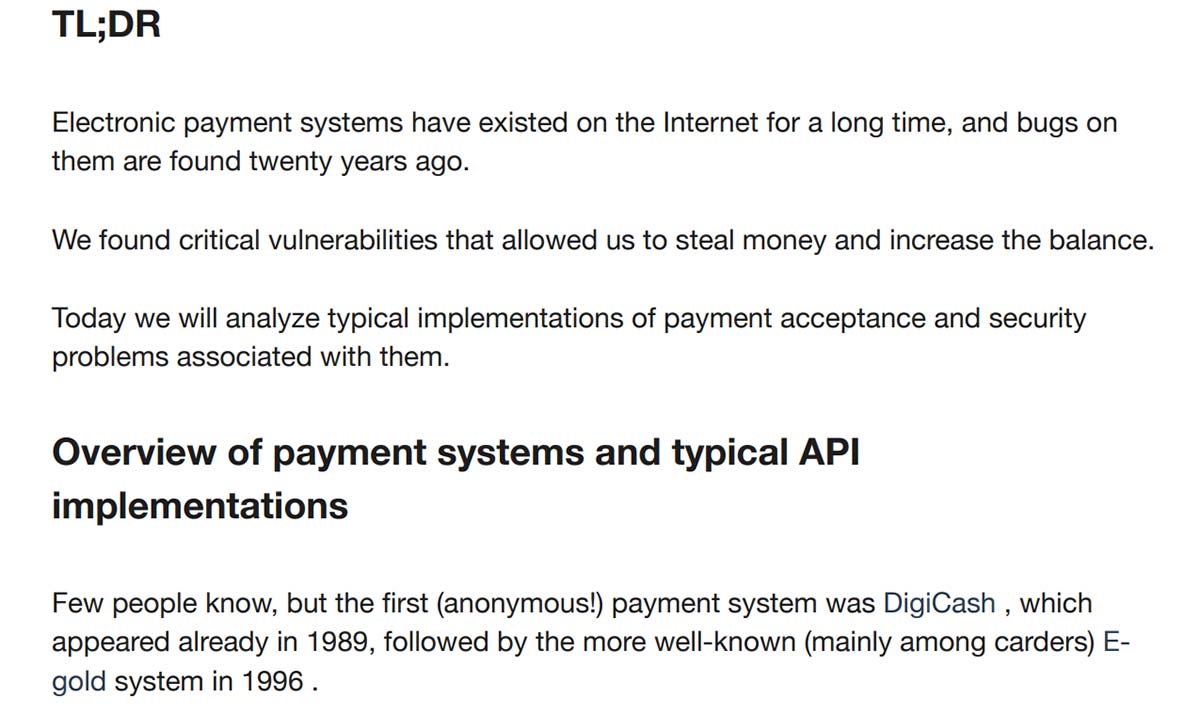
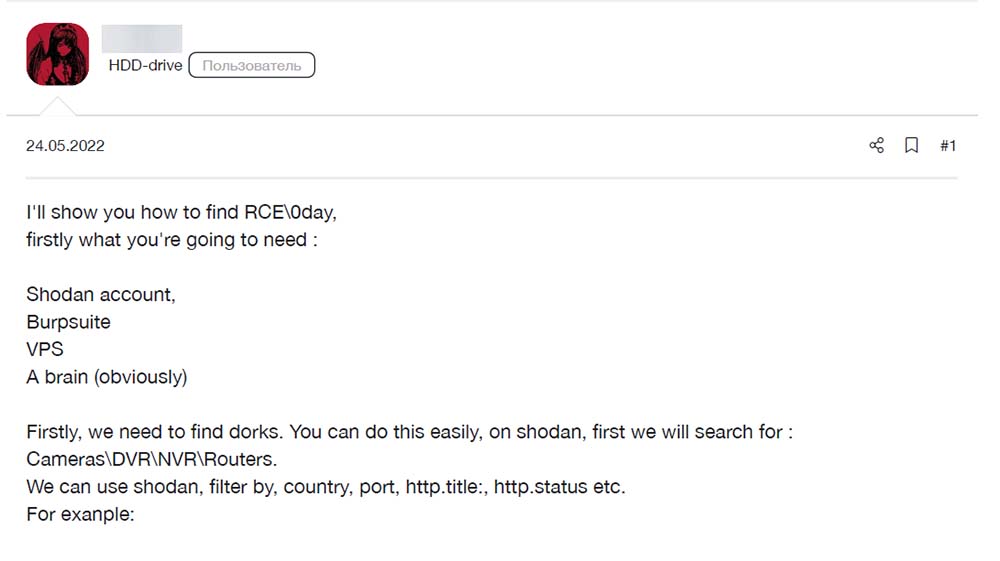
The winning articles, however, are the most interesting part of these past contests, although they can be quite disappointing based on the content we have managed to access. In particular, they tend to feature hacking tutorials or summaries of well-known subjects. While it is probably a good thing for the criminal community to have ready access to these attack methodologies, we have not seen anything close to groundbreaking just yet.
Figure 5. Summary of the winning article titled “20 years of payment acceptance problems”
Figure 6. Introduction to a contest’s winning article, “Finding RCE 0-days in IoT”
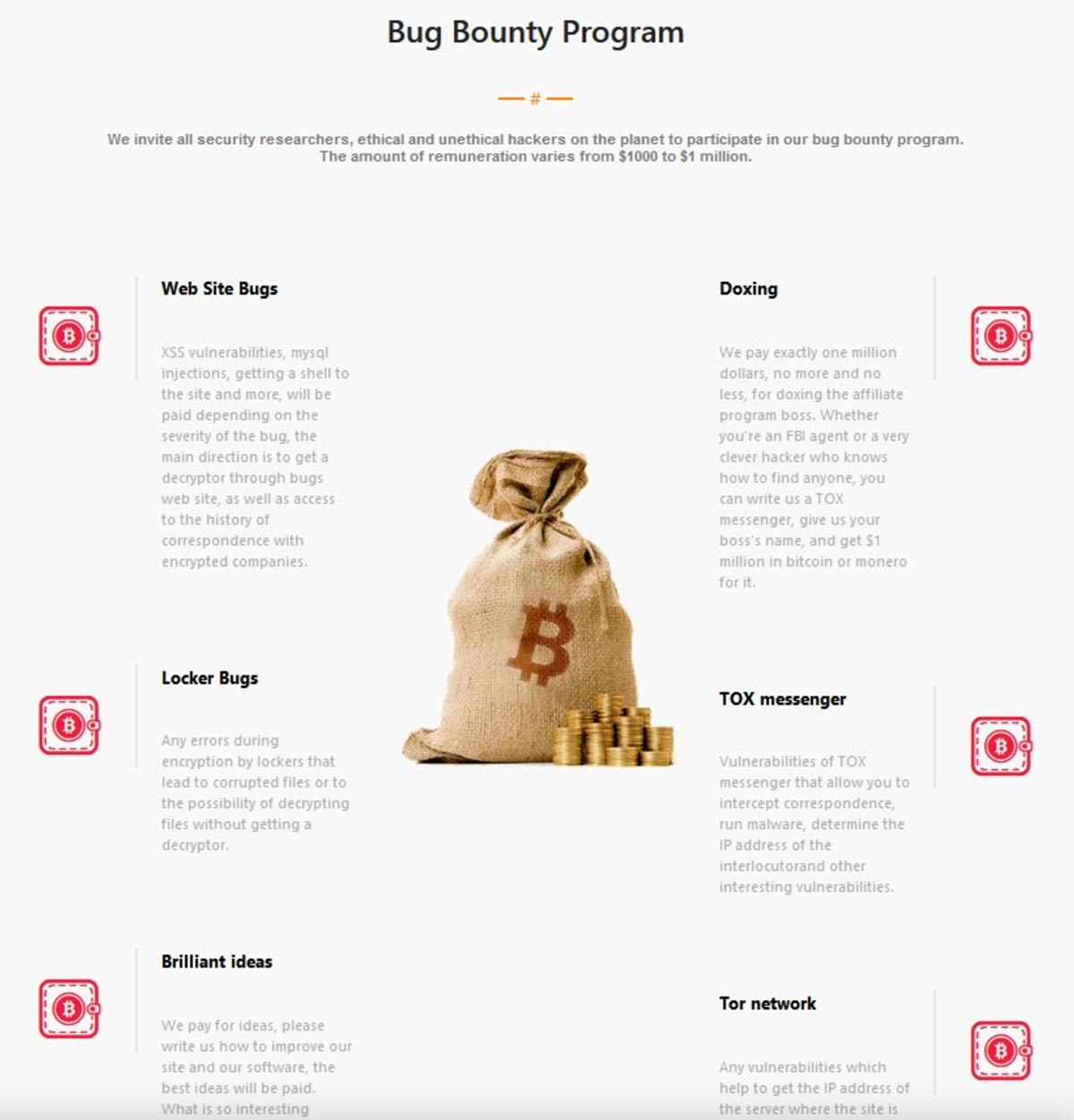
In a recent twist on the contest format, LockBit, a well-known ransomware group, just released version 3.0 of their malware. Alongside this, cybercriminals also introduced a bounty program that works very much like one of these contests. The idea of the bug reward program involves offering money to anybody who can help improve the software by attacking it (or any of the server infrastructure behind it) and disclosing how it could have been avoided. Cybercriminals also accept any attack that could affect the malware group in a negative way, such as abusing the Tor network, the TOX messenger they use to communicate, or any web bugs. They also offer US$1 million to anybody who can identify or “dox” the LockBit affiliate program’s manager, an individual who operates under the moniker “LockBitSupp.”
Figure 7. LockBit’s bug bounty program
Even though this is not a traditional contest as explained previously, the bug bounty program is essentially run the same way and accomplishes the same objective: to pool creative ideas from the community’s hive mind and thereby improve how cybercriminals stay operational under the radar of the law. This is, in a sense, therefore also a contest for criminal defenders as they continue to work to stay ahead of cybercriminals.
Other contests
The previous kinds of contests are the most concerning ones if we take into account that they might place completely new attacks in the hands of the criminals. However, they are not the only kinds of contests in existence. Criminal forums have been using this contest format for quite some time now, and we have seen them sparking creativity in all sorts of fields, even non-technical ones.
For instance, we have seen contests looking for the best poem, suggesting that perhaps internet criminal poetry might go down in history as a new genre in Russian literature. We have also observed contests looking for creative content to promote the criminal forum where the contest will take place. Such content might include videos, logos or images, and other promotion strategies to increase website viewership. Some of these websites regularly run logo creation contests and other artistic projects.
In general, these other contests are far less interesting for our purposes, and we mention them here only to highlight that this format is popular in the criminal underground and goes beyond the offensive technology field. Indeed, forum criminals have just adapted it to benefit from its great power of bringing about innovation.
Conclusion and future outlook
While the current trend is modest, we expect to see increasingly more of these competitions and a steady increase in prizes until these truly do become “X-Prizes” and game changers. These contests also have the effect of speeding criminal innovation since few criminal groups can afford to have a proper research and development department. However, by using this crowdsourcing model, the whole criminal community effectively becomes a research and development team, which is very powerful.
The evolutions spurred by this trend do not need to be major changes to be successful. Given the way crime works, they do not need big strategic wins; instead, there is much to be said for smaller tactical wins. This might mean a new procedure to carry out tactics, techniques, and procedures (TTPs) that are already known. Such a development is very valuable — at least in the short term — if it allows criminals to bypass current defenses. And this remains true even if an attack is not newsworthy from the point of view of innovation.
In addition to small tactical wins, if these exercises in creativity are regularly run, chances are that the criminals would eventually hit the jackpot and discover a completely new attack. This could be a game changer, similar to that time when the Maze ransomware started implementing leak sites to better extort target companies. With this new extortion method, the ransomware group succeeded in placing its victims under more duress, lest anyone else see the whole pile of stolen information on the leak site. This small change in attack behavior was instrumental in bringing about the current new wave of ransomware that focuses not only on encrypting data but also on stealing it and threatening to make it public. Ultimately, this paradigm shift can start from something relatively small, only to later alter the threat landscape significantly.
These contests therefore have the potential to perform the same function and give criminals the next big attack that IT security cannot see coming. The chance of one of these contests hitting the jackpot might be slim, but if criminals keep organizing them, one can expect a kind of “black swan” or unforeseen attack that could come about at some point.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks