WordPress GDPR Plugin Vulnerable to Cross-Site Scripting Attacks
 GDPR Cookie Consent, a WordPress plugin, inadvertently exposed websites to cross-site scripting (XSS) attacks through a vulnerability that affects versions 1.8.2 and below of the plugin. As disclosed in a report by NinTechNet, the vulnerability allowed privilege escalation. The plugin had over 700,000 active installations at the time of the exploit.
GDPR Cookie Consent, a WordPress plugin, inadvertently exposed websites to cross-site scripting (XSS) attacks through a vulnerability that affects versions 1.8.2 and below of the plugin. As disclosed in a report by NinTechNet, the vulnerability allowed privilege escalation. The plugin had over 700,000 active installations at the time of the exploit.No CVE number has been assigned to the vulnerability yet. The plugin has been patched in version 1.8.3 and subsequent versions.
How the vulnerability works
The exploit is a result of improper access controls, specifically the __construct method used for initializing objects. This AJAX endpoint, originally only intended for administrators, failed to implement checks to verify the user’s identity.
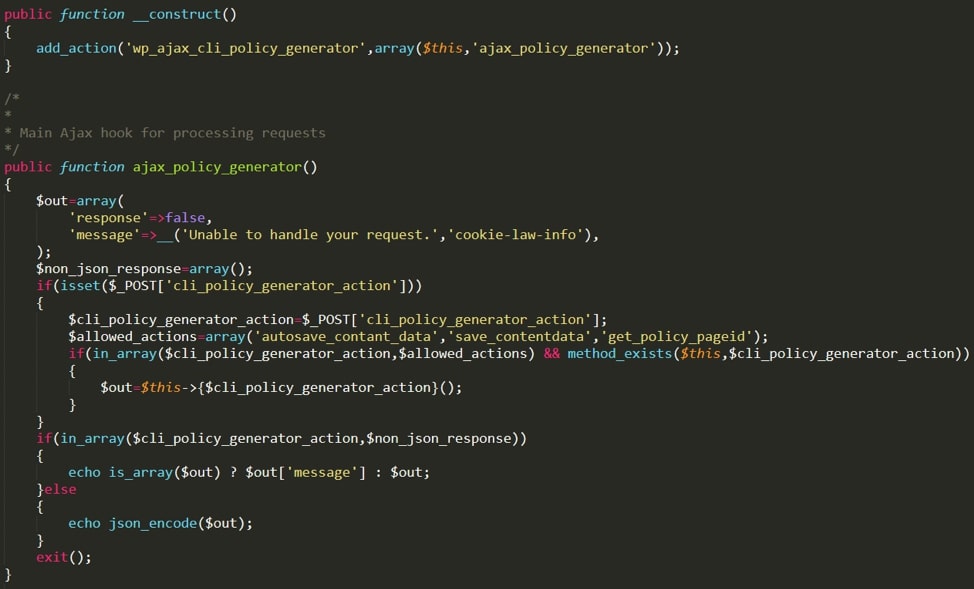
Figure 1. Vulnerable code in admin/modules/cli-policy-generator/classes/class-policy-generator-ajax.php
- autosave_contant_data (sic) – defines the default content that appears in the cookie preview page
- save_contentdata – sends a POST request to the database in order to store cookie information
- get_policy_pageid – returns the post ID of the cookie configuration page
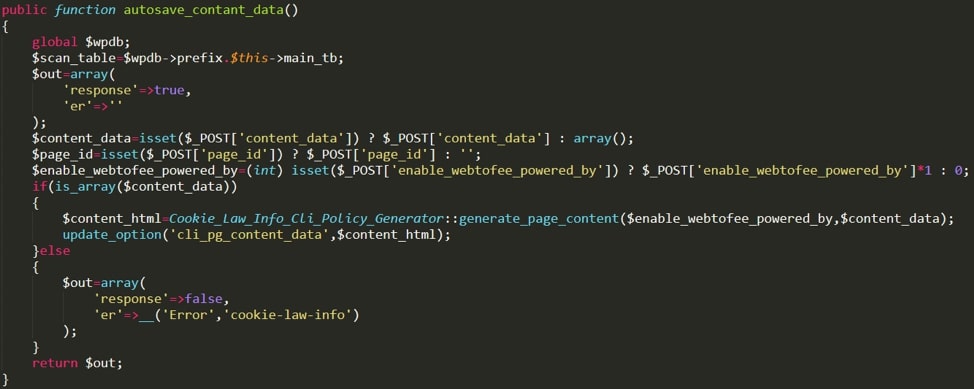
Figure 2. The autosave_contant_data function, which can be used to perform an XSS attack
The second of the two functions, save_contentdata, allows the attacker to send information to the backend database and modify page content. In addition, by setting the status of the page to draft instead of published, an attacker can use the function to make parts of the website invisible to the public and leverage this for a Denial of Service (DoS) attack.
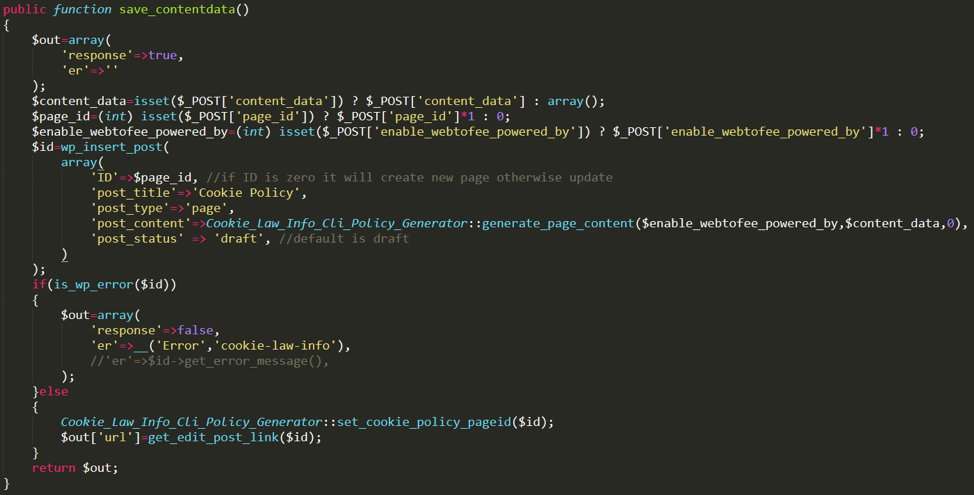
Figure 3. The save_contentdata function, which can be used to modify page structure and potentially cause DoS
Patch details
The improper access control vulnerability was patched in version 1.8.3. The patch adds an additional check to the ajax_policy_generator function called by __construct to verify that the user’s nonce value is valid and that it has the correct permissions to modify the plugin content. With the patched constructor function, users without correct permissions will no longer be able to use autosave_contant_data or save_contentdatato inject code.
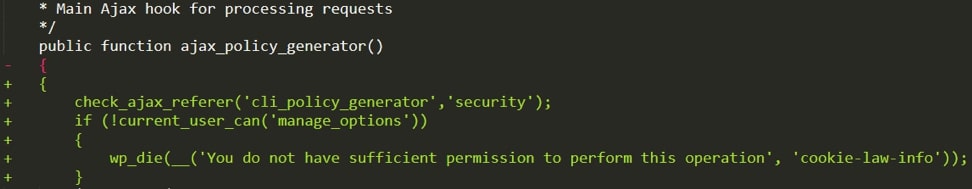
Figure 4: Check added to the ajax_policy_generator function to patch the access control vulnerability
Everyone using this plugin should update to the latest version (>= 1.8.3) as soon as possible to mitigate the risk.
Protecting systems against compromise
- 37304: HTTP: WordPress GDPR Cookie Consent Plugin Stored Cross-Site Scripting Vulnerability
-
1010194 - WordPress 'GDPR Cookie Consent Plugin' Stored Cross-Site Scripting Vulnerability
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
HttpContext.GetGlobalResourceObject("ES","RecentPosts")%>
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime
- Threat Attribution Framework: How TrendAI™ Applies Structure Over Speculation
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One