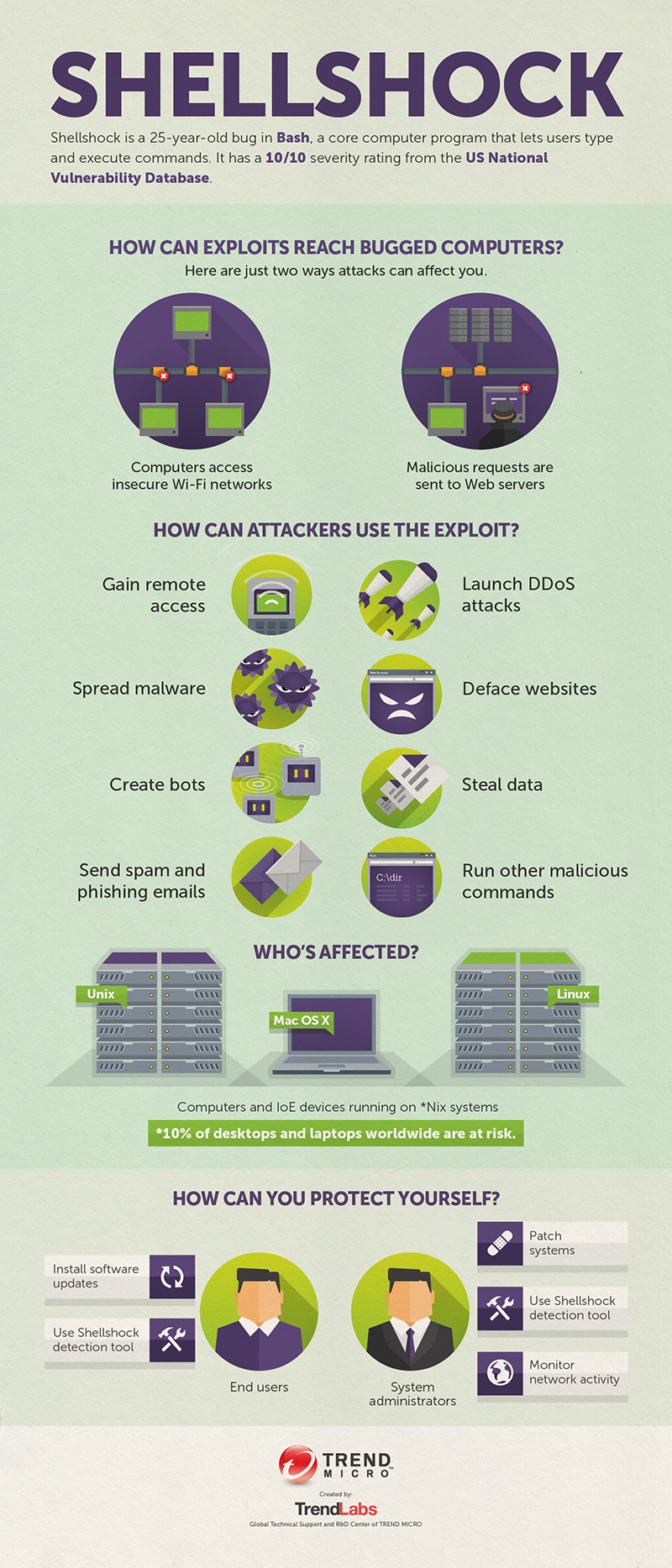
About the Shellshock Vulnerability: The Basics of the “Bash Bug”
Just after a few months after Heartbleed stormed the Internet, another existing widespread vulnerability known as Shellshock has been found, threatening to compromise millions of systems, servers and users. The Bash bug poses a serious threat as it is very easy to execute an attack, and requires little technical expertise to do so.
More: Bash Vulnerability Leads To Shellshock: What It Is, How It Affects You
What is it?
Shellshock is a vulnerability in the Bash shell, a user interface that uses a command-line interface to access an operating system’s services. The current command Bash interpreter lets users execute commands on a computer. The vulnerability allows attackers to run malicious scripts in systems and servers, which compromises everything in it. It has the potential to do significant widespread damage, since it affects Linux, BSD, and Mac OS X. Linux alone powers a majority of the servers on the Internet and IoT (Internet of Things) devices.
What is the threat extent and who are affected?
Shellshock creates a weak spot that serves as a backdoor for a hacker to carry out commands, take over a machine, dig into servers, steal data and deface websites. Most computers and Internet-enabled home devices such as routers, Wi-Fi radios, and even smart light bulbs running on Linux OS are most likely affected. Webcams for example, are often Linux-based and these devices can also be hacked and used as infection vectors. This problem extends to smart devices connected to the Internet of Everything, located anywhere and everywhere, including hospitals, energy sectors, and schools. This means even with a minimal vulnerability in a device could open doors for a potential attack.
More: Shellshock Exploit Leads to BASHLITE Malware
What can you do?
Be alert and recognize the scope and scale of Shellshock. Whether it’s as notorious as they say or not, having a healthy paranoia can make you more cautious and proactive about interconnected devices that could be vulnerable to possible attacks. Update all firmware and operating systems, and install security updates. Use Shellshock detection tools or plug-ins to scan likely vulnerabilities and exploits. For system admins, patch your systems immediately and closely track your network activity.
Learn more about the Bash Bug on the attached infographic: Shellshock.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
HttpContext.GetGlobalResourceObject("ES","RecentPosts")%>
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One