Securing Smart Homes and Buildings: Threats and Risks to Complex IoT Environments
 View Cybersecurity Risks in Complex IoT Environments
View Cybersecurity Risks in Complex IoT Environments
The evolution of smart homes and smart buildings into complex IoT environments reflects the continuing developments in home and industrial automation. Security should not be left behind as increased complexity also means new threats and risks.
One of the most enticing images of the future has been that of technology that allows ordinary objects to seemingly come to life to cater to our personal needs. A certain version of that future has already materialized in present time. The internet-of-things (IoT) has made possible a new kind of space where that future exists — complex IoT environments (CIE).
A CIE consists of at least 10 IoT devices that are functionally chained together and integrated into an environment using an IoT automation platform. CIEs are more commonly exemplified by smart homes, but are not restricted to them. IoT automation platforms can be scaled up to control devices in larger structures like smart buildings.
For a better understanding of CIEs, we can look at the most familiar implementation: the smart home. Integral to a smart home is internet connection throughout the entire CIE, which requires Ethernet or fiber wiring and modems and Wi-Fi routers. Devices integrated into the environment can include a gateway, smart bulbs, smart locks, speakers, TVs, and many others. Even traditional appliances like toasters can take on more complicated functions through smart plugs. The number and the types of devices in a CIE dictate the possible commands, interactions, and functionalities. The number should be significant enough to create dynamic interactions.
As mentioned previously, what enables these individual devices to work together are software products called IoT automation platforms (also called automation servers). An IoT automation platform serves as a brain of sorts for the CIE and allows the creation of smart applications by functionally chaining the devices through custom rules, thus allowing devices to interact and affect each other’s actions. The complexity afforded by automation platforms expands the possibilities in smart homes and buildings and other setups in various settings. But the increasing complexity with each additional device and automation rule also means an expanding attack surface. Therefore, we must look at the challenges CIEs pose, specifically cybersecurity risks.
To look into the security of CIEs and automation servers, we set up smart home labs and tested possible threat scenarios on actual CIEs. A comprehensive discussion on what we learned can be found in our research, Cybersecurity Risks in Complex IoT Environments. We highlight some of our findings here.
Intrusions
A CIE integrates various devices and systems. For smart homes, it ranges from lighting and entertainment to security. This means the automation platform also has control over functions that are essential to the safety and privacy of the home’s residents, like keeping entryways secured or setting up security alarms.
In our research, we explored scenarios wherein attackers can seize control of a CIE. One scenario that we tested involves compromising the CIE’s automation server. As mentioned earlier, the automation server is where all the automation rules that govern the function and interaction of devices in the CIE are stored. We had full read-write control to modify/update those rules. Several possible risks arise when this server is exposed online and the rule set is compromised.
If smart locks are installed and connected to the CIE, then attackers could modify automation rules that would allow them entry into the home. These rule modifications could make the sensors either recognize the attacker as one of the homeowners or leave the doors unlocked. Such rules could also be controlling any alarm systems set up in the CIE, making it easy for any attacker to disarm them.
Another scenario involves the attackers using internet-connected speakers to issue commands to virtual assistants like Alexa and Siri. Attackers can analyze and clone the owner’s voice and play the resulting sound file to bypass any voice recognition checks by connected devices in the CIE. This area of the threat landscape is expanding further as some smart cars can now be controlled through voice services like Alexa and Google Assistant and connected to home Wi-Fi networks. Voice threats have the potential of becoming a bigger issue should voice commands one day control more critical functions like starting the car engine.
Surveillance and information theft
Once an automation server is compromised, other attack scenarios are possible, depending on the types and number of devices connected to a CIE. Attackers can opt to take a less physically intrusive method, one that is nonetheless a breach of the privacy of a structure’s inhabitants. By configuring rules in the automation server, an attacker can monitor activity within the home or building through sensors, cameras, and any other device capable of collecting information from its surroundings. The automation system can be set up to send the attacker snapshots and information about activity inside the home via a supported messaging application such as Slack channels.
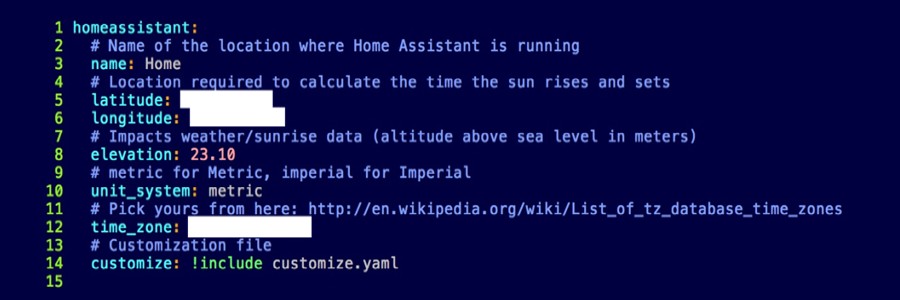
It is also possible for attackers to gather useful information without having to tamper with the automation rules. In some cases, personally identifiable information (PII) like the geolocation of the home or credentials can be gathered from the configuration file of the automation server if it is unwittingly exposed online.
 Screengrab of an exposed automation server showing a home’s location
Screengrab of an exposed automation server showing a home’s location
Secure complex IoT environments
As evidenced by the described scenarios, a common thread in cybersecurity risks to CIEs was tampering with the logic or rules in the automation server. Access to the logic provides attackers full control over the CIE. Exacerbating this risk is the lack of notification to users about changes made to the CIE’s logic. Rules can be changed by an attacker and left as is without the owner ever realizing anything’s amiss.
In many ways, CIEs bring new considerations in securing one’s home. Although CIEs have created a new kind of space for innovation, they also come with expanded attack surfaces. It is important for adopters of such an environment to take true ownership of their CIEs by being aware of the risks and preparing for them.
Homeowners can gain a better control over CIEs through security practices such as the following:
- Check automation rule files and make backups. Regularly checking automation rules and tracking changes to them will help users see if something has been modified, thus defending against many of the threat scenarios. Use a file integrity monitor to check for any unauthorized changes made to the configuration files.
- Practice good password hygiene for every component of the CIE. Important for many IoT-related devices is the immediate changing of default passwords. Good password hygiene also involves using strong passwords or enabling two-factor authentication if applicable.
- Be knowledgeable about the settings of each component of the CIE. Make sure that device and server settings are secure by turning off unnecessary services and minimizing the amount of information being gathered by a device if possible.
In CIEs, we find that the future we previously only imagined is here — the challenges CIEs pose drive home the point further. From recognizing CIEs, the next important step is to be familiar with the requirements of CIE maintenance and security. As CIEs become greater in scale and adoption, anticipating new forms of attack on the IoT becomes more crucial. Read more about CIEs and potential threats against them in our research paper, Cybersecurity Risks in Complex IoT Environments.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks