Spam Campaign with .PUB Attachment Delivers RAT, Targets Food and Retail Brands
We have been following a spam campaign with attached malicious Publisher files used as malicious macro-downloaders. The cybercriminals behind it may be taking advantage of using .PUB files as the macro-downloader during the busiest quarter of the year for businesses as it is not associated with possible infections, unlike other document files such as .DOC (Word) and .XLS (Excel).
[Read: Same old yet brand-new: New file types emerge in malware spam attachments]
Behavior
These manipulated .PUB files download a malicious MSI file, installing a Remote Access Trojan (RAT) on the user’s computer after accessing the command and control (C&C) server. The choice of using an .MSI file can be a means for evasion as these are associated with legitimate Microsoft Installer files. When executed, the .PUB file displays the following:
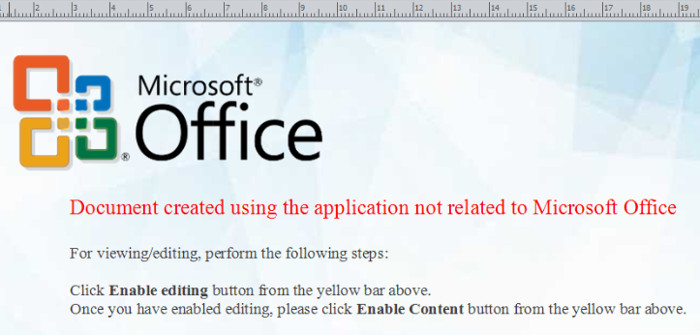
Figure 1. .PUB file when executed
Data from our telemetry tells us that majority of the targets are in the food and retail industries, as well as a few government agencies. We have identified more than 50 companies belonging under these sectors repeatedly targeted via blocked spam messages between November 20 to 27, including the US Department of Agriculture and the Taiwanese Food and Drug Administration, Starbucks and Taco Del Mar in the food sector, and Harris Teeter and Save Mart Supermarkets in the retail industry.
The cybercriminals use social engineering techniques, likely targeting specific offices from these companies as the email addresses are disguised to appear as the “Operations Department,” while the attached file is named “invoice.pub”.
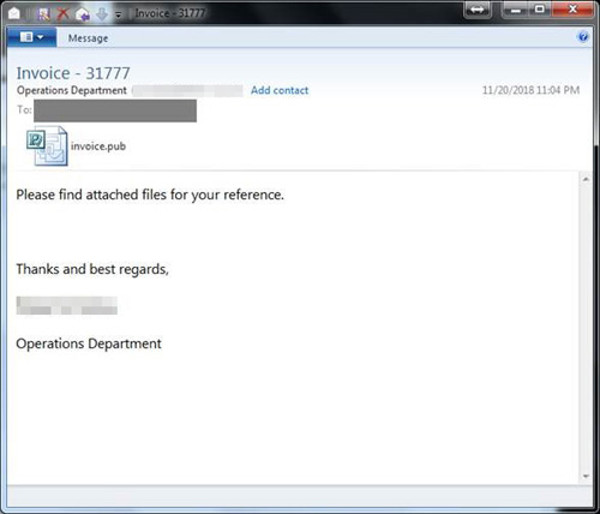
Figure 2. Sample email using the “Operations Department” signature
[Read: Spam campaign delivers malware via .WIZ, targets banks]
Further, as we scanned through the wave of emails received from detection feedback, we found emails targeting the financial sector in the first two weeks of November. This may imply that the cybercriminals were initially targeting financial institutions, some of which include La Banque Postale France, Kotak Mahindra Bank, China Construction Bank, and Natixis.
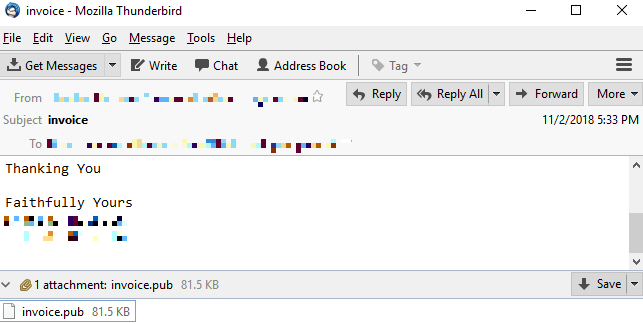
Figure 3. Sample email sent to a financial institution
The usual infection chain for these types of attacks uses a malicious Word document or Excel file as macro-downloader and uses a PowerShell function to deliver the .EXE payload. However, this malware uses the infected .PUB as the malicious macro-downloader but schedules the task of downloading and executing the .MSI file instead of doing so immediately or directly. The additional layer of detection evasion allows the msiexec process to fall under the scheduler instead of the publisher executing the macro. Once scheduled, the task now falls under the usual parameter for msiexec ,/q /I {url}, installing the file automatically and without the need for additional user interaction.
The techniques used by the cybercriminals are not new. However, the detection evasion maneuver added to the usual infection chain and payload delivery behavior makes it unique.
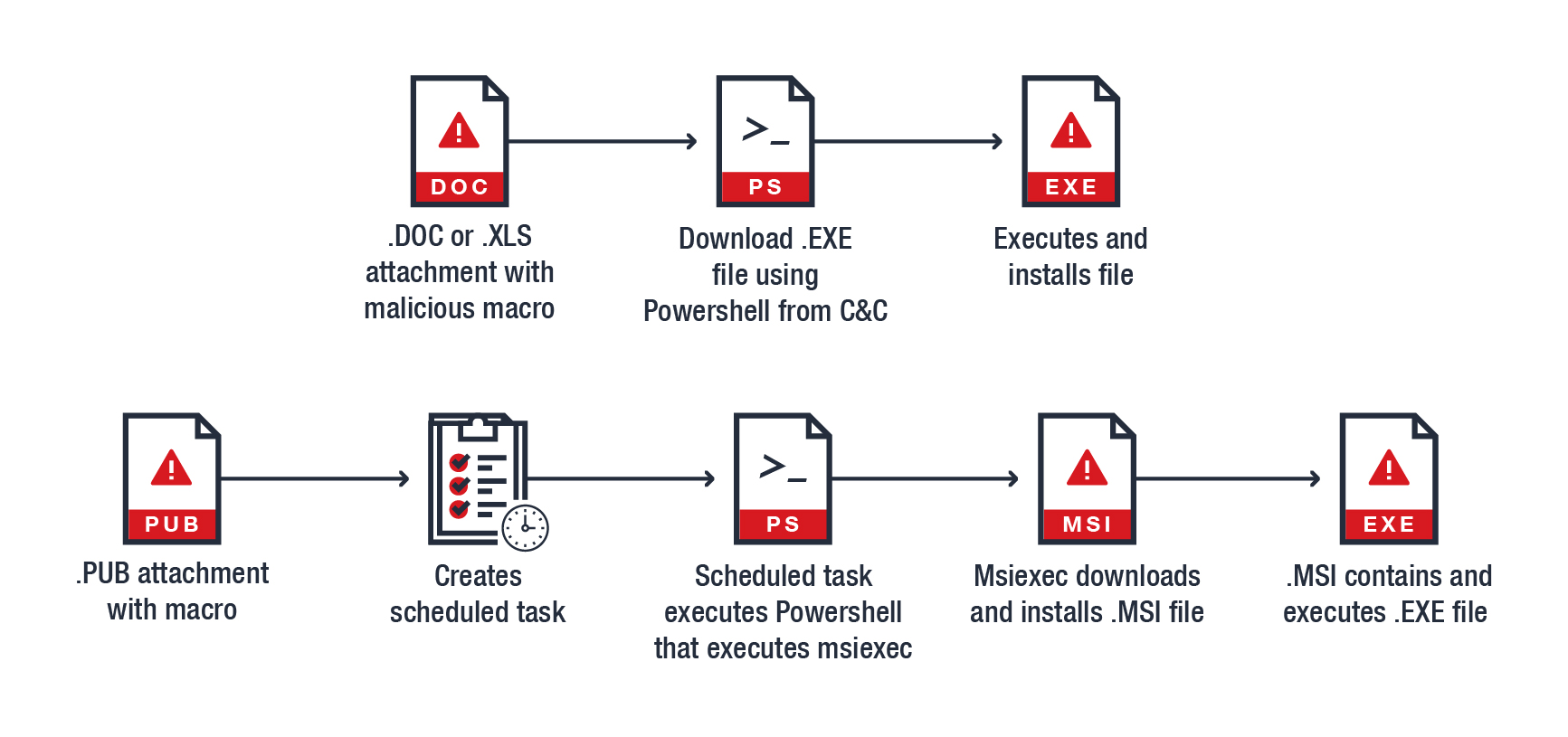
Figure 4. Comparing the usual macro virus routine vs. the malicious .PUB’s infection chain
[Read: Spam campaign targets Japan, uses steganography to deliver the BEBLOH banking Trojan]
We are currently following and investigating this campaign. Our most recent detections have shown that the cybercriminals have reverted to the conventional routine of using a .DOC file and delivering a different malware payload, but with a similar coding style, spam layout, and target companies. Cybercriminals will continue combining old techniques with new ones, as well as using legitimate applications and tools to infiltrate businesses for malicious activities. Make sure you stay ahead of these threats:
- Update your systems and software to prevent cybercriminals from taking advantage of possible outdated entry points.
- Be aware of urgent-looking emails with attachments. Compare and verify with previous communication and transactions if the email addresses and documents are legitimate.
- Use a multi-layered security solution that can scan and block emails with malicious attachments and URLs.
Trend Micro Solutions
Trend Micro™ InterScan™ Messaging Security stops email threats with global threat intelligence, protects your data with data loss prevention and encryption, and identifies targeted email attacks, ransomware, and APTs as part of the Trend Micro Network Defense Solution. Its enhanced web reputation is powered by the Trend Micro™ Smart Protection Network™, and blocks emails with malicious URLs in the message body or in attachments.
Trend Micro Deep Discovery™ has an email inspection layer that protects enterprises by detecting malicious attachments and URLs. Deep Discovery detects remote scripts even if it is not being downloaded in the physical endpoint. Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. Additionally, Trend Micro Anti-Spam Engine detects and blocks malicious files without using signatures. Hosted Email Security protects Microsoft Exchange, Microsoft Office 365, Google Apps, and other hosted and on-premises email solutions.
Trend Micro™ Email Reputation Services™ detects the spam mail used by this threat upon arrival. Trend Micro™ OfficeScan™ with XGen™ endpoint security infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against advanced malware.
Indicators of Compromise
Hashes:
SHA1 | SHA256 | Description | Detection |
2346056432b47fae7b96b75599e1772da0f7209e | 874cd2ec55b9ac69a9594ff9338adbed95226a8a736c6e8638060684abd3d110 | Malicious .PUB file | |
ce2412ece9fbf34e11229d07aa7c2a20b7fa9621 | 8493b0150d5fd56e527dd4cd0e16813826981ccbb296fb9eac972b720bba9bc5 | Malicious MSI file | |
3042d91d1f31e8ee5ee8627bf69327a01516ff60 | e187fa57475bae6187ba7a1aad04f29673dcf0b126507779fa08f2ffc48eec18 | password-protected Self-extracting archive | |
651b8d1377910e4728e85dcd231e269313ab9e1d | 609b0a416f9b16a6df9b967dc32cd739402af31566e019a8fb8abdf3cb573e30 | .EXE RAT file |
Malicious domains/URLs:
- hxxp://homeofficepage[.]com/TabSvc (Source of MSI file)
- 89.144.25.16/backnet (C&C)
With additional insights from Junestherry Salvador and Byron Gelera
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks