Ransomware Recap: TorrentLocker's New Tactics
 The ransomware known as TorrentLocker has been spotted perpetrating an attack against European nations such as Germany and Norway. While the ransomware’s behavior isn’t too different from the earlier variants, its new method of propagation makes it a dangerous threat for end users who lack awareness of the various phishing techniques used by cyber criminals.
The ransomware known as TorrentLocker has been spotted perpetrating an attack against European nations such as Germany and Norway. While the ransomware’s behavior isn’t too different from the earlier variants, its new method of propagation makes it a dangerous threat for end users who lack awareness of the various phishing techniques used by cyber criminals.
These variants (Detected by Trend Micro as RANSOM_CRYPTLOCK.DLFLVV, RANSOM_CRYPTLOCK.DLFLVW, RANSOM_CRYPTLOCK.DLFLVS and RANSOM _CRYPTLOCK.DLFLVU), use social engineering to trick its victims—primarily company employees—into clicking a Dropbox URL embedded in a phishing email. This URL leads to a fake “invoice document" which is actually the ransomware’s file. TorrentLocker’s use of Dropbox makes for an additional detection hurdle, as the site itself is a legitimate one.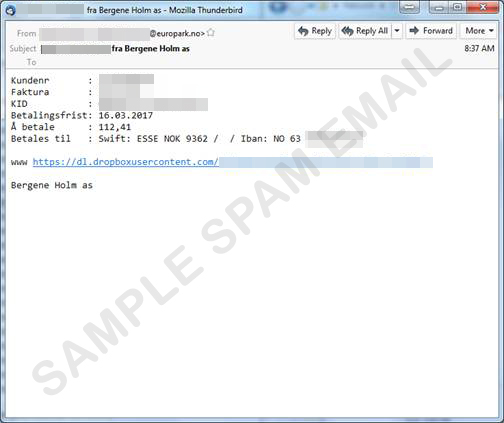
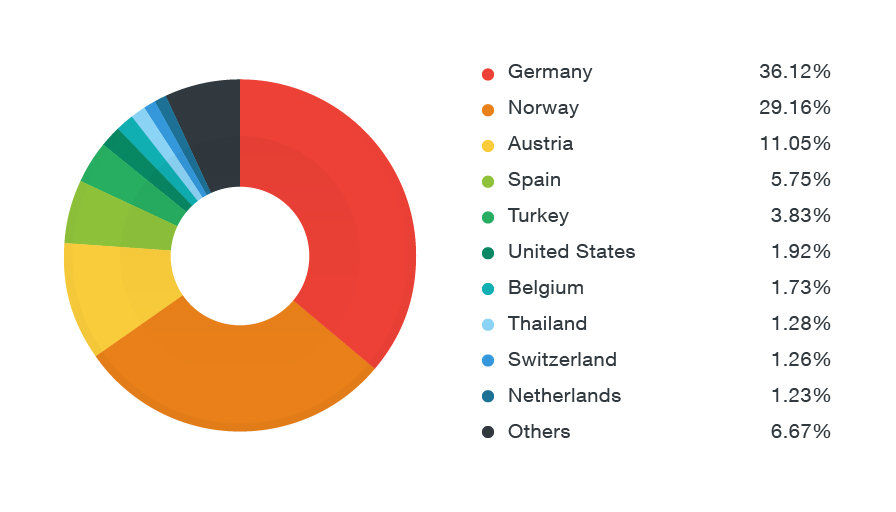
The ransomware’s distribution of targets based on Trend Micro’s Smart Protection Network (SPN) data can be seen in the chart below:
Python-based ransomware make an appearance
A couple of notable Python-based ransomware dubbed PyL33t (Detected by Trend Micro as Ransom_PYLEET.A) and Pickles (Detected by Trend Micro as Ransom_CRYPPYT.A) made the rounds during the end of February.![]()
Internet culture bears a heavy influence on the PyL33t ransomware, as seen in its Comic Sans ransom note, its use of the 1337 port, and its use of the .d4nk extension, which it adds to files it encrypts. Once PyL33t is downloaded and executed in the victim’s computer, it will encrypt various files that use extensions such as .docx, .jpg and .xlxs.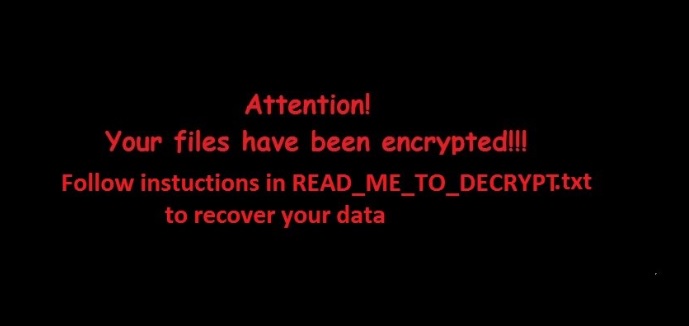
Pickles is a harmless-sounding name for another dangerous Python-based ransomware. Once Pickles infects the victim’s computer, it encrypts files and renames them with the .EnCrYpTeD extension, changes the wallpaper to the message seen above, and drops a ransom note called READ_ME_TO_DECRYPT.TXT which contains the expensive ransom demand of 1 bitcoin, which roughly amounts to $1200. The decryptor is also dropped along with the ransomware; however, decrypting the affected files requires a password.
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks