Ransomware Recap: Still in Development, Found in the Wild
 As the threat of ransomware becomes more pervasive, bad guys are more than willing to rustle up more of these file-encrypting malware, some in a bid to make a cash cow out of more victims, and others possibly for cybercriminal fame (notoriety). Last week, we took a look at the evolution of Cerber, a well-established ransomware as a service, and the reemergence of another notorious family, Locky. Their common denominators? A continually diversified set of capabilities and attack vectors focused on stealth, despite relying on common points of entry—spam and exploit kits.
As the threat of ransomware becomes more pervasive, bad guys are more than willing to rustle up more of these file-encrypting malware, some in a bid to make a cash cow out of more victims, and others possibly for cybercriminal fame (notoriety). Last week, we took a look at the evolution of Cerber, a well-established ransomware as a service, and the reemergence of another notorious family, Locky. Their common denominators? A continually diversified set of capabilities and attack vectors focused on stealth, despite relying on common points of entry—spam and exploit kits.
This week, however, was highlighted by ransomware found in early stages of development. While these work-in-progress malware sound underwhelming, they are still credible threats that can adversely impact end users and organizations. Their emergence in the wild also provides the baseline of capabilities these threats will take down the line as they resurface as full-fledged ransomware. Also of note are ransomware refashioned from—or possibly mimicked—previous families, likely for the convenience of mounting a campaign using older families with public or open-source code.
Here are some of the notable ransomware we uncovered last week:
Stupid Ransomware
Detected by Trend Micro as RANSOM_STUPFTS, this ransomware has two known versions: one that appends infected files with a .haters extension, and another with .xncrypt. Initial analysis indicates it is still in development. Written in .NET, these variants encrypt files in the following directories:
- My Documents, My Music, My Pictures
- %userprofile%\Downloads, and %userprofile%\Desktop
- C:\\Windows (top-level only)
- C:\\Program Files\\ (top-level only)
- All drives
The ransomware demands a ransom of 0.25 Bitcoin (US$43 as of May 5, 2017). It targets 61 file types, although it doesn’t encrypt files or folders that ends with the following strings: “Bin”, “indows”, “tings”, “System Volume Information”, “cache”, “very”, “rogram Files (x86)”, “rogram Files”, “boot”, “efi”, “.old”, and “All Users”.
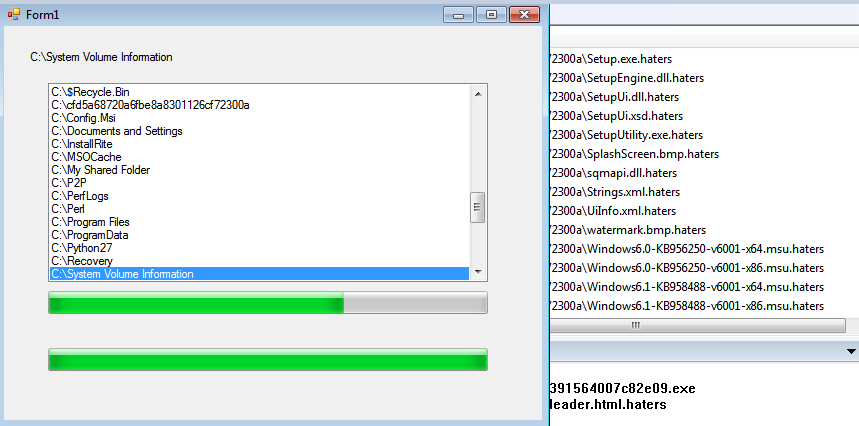
Figure 1: Encryption routine of Stupid ransomware that appends a .haters extension
DeadSec Crypto v2.1
Another ransomware-in-progress is a rehashed version of DeadSec Crypto ransomware. This v2.1 variant (RANSOM_DEADSEC.A) appears to currently have no encryption routine yet, but only displays a ransom note and deletes some test files. A closer look at its code reveals it will append a .crypto extension to targeted files, which are ZIP (.zip) and image files (.img), executables (.exe), Portable Document Format files (.pdf), Rich Text Format files (.rtf), shortcut files (.lnk and .url), Hypertext Preprocessor files (.php), and spreadsheets (.xlsx).
Hidden Tear Mordor
This variant (RANSOM_HIDDENTEARMORDOR.A), which is based on the source code of Karmen ransomware as a service (RANSOM_HIDDENTEARKARMEN.A), which is in turn derived from open-source Hidden Tear ransomware. Hidden Tear Mordor is capable of encrypting 265 file types with AES-256 encryption algorithm, then appends the infected file with .mordor extension. It changes the wallpaper to an image depicting Sauron, a character from the Lord of the Rings novels.
Interestingly, it doesn’t execute its encryption routine if the infected system is located in Germany. It uses English and Russian languages in its command and control (C&C) and payment instruction sites.
CryptoMix: Wallet / SHIELDO-WALLET
Another ransomware variant sighted last week was CryptoMix: Wallet / SHIELDO-WALLET (RANSOM_CRYPAURA.WLT). It appends the .wallet extension to the files it encrypts. It is the same extension that an established ransomware, Crysis/Dharma ransomware (RANSOM_CRYSIS), uses.
In its ransom note, it promises to guarantee decryption after payment by offering to decrypt five files for free, on the condition that the files are not archived and less than 10MB.
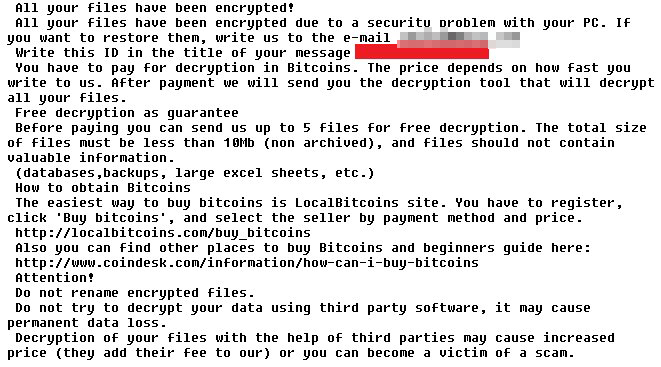
Figure 2: Ransom note of CryptoMix: Wallet
Amnesia Ransomware
This ransomware (RANSOM_AMNESIA.A) is written in Delphi, something it shares from other families like LeChiffre (RANSOM_LECTOOL) and CryptXXX (RANSOM_WALTRIX). It’s notable for being capable of encrypting a whopping 7,000 file types. To successfully execute its encryption routine, it drops a copy of itself to the directory %APPDATA% and asks the user for admin permission. Once the malware is run, %APPDATA%\guide.exe, it proceeds to encrypt its targeted files.
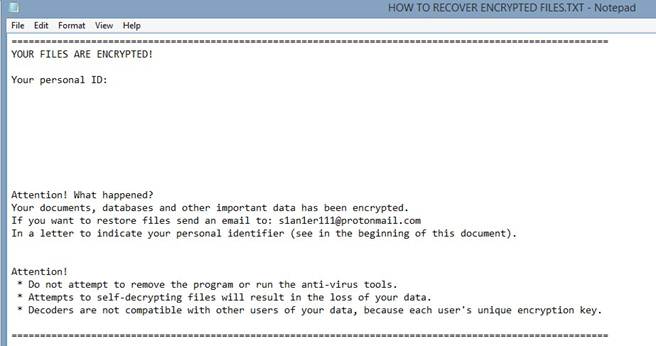
Figure 3: Ransom note of Amnesia ransomware
ShellLocker
ShellLocker (RANSOM_CUTESHELOCKER.A) appears to be derived from old ransomware cuteRansomware family (RANSOM_CRYPCUTE), whose source code is based on a Github-hosted project my-Little-Ransomware. It adds 128 bytes to the files it encrypts, and renames them with a random string. ShellLocker encrypts files found in these directories: Desktop, Personal, My Pictures, My Music, My Videos, Common Documents, Application Data, Common Application Data, Templates, System, Cookies, Desktop Directory, Favorites, History, Internet Cache, Local Application Data, and My Computer.
In its ransom note, ShellLocker threatens victims with a 48-hour time limit, after which the files and the decryption key needed to unlock the file will be deleted. It asks victims to pay 50$ in Bitcoin or paysafecard or Amazon gift cards.
Defending against Ransomware
Indeed, these threats highlight how ransomware operators are deploying their malware as quickly as they can, possibly to accrue a larger pool of victims. Another that we’ve seen was the inclination to rework existing threats—given their public availability—instead of creating a completely different family.
While they may no longer be novel in principle, they still pose risks to end users and businesses and thus call for a proactive approach to security. Backing up important files, being wary of unsolicited and unverified emails, websites, and suspicious applications, and regularly updating the system and its software with the latest patches, are just some of the best practices defending against ransomware.
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Postagens recentes
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks