Ransomware Recap: Ransomware Development Kit for Mobile Peddled Underground
 The Internal Revenue Service (IRS) has issued a message warning the public about a ransomware campaign that uses a bogus email to impersonate the IRS and the Federal Bureau of Investigation (FBI). This is not the first scheme to ever use the tactic, it's been proven to have been effective before. The ransomware business has been profitable enough to assume that the "industry" will only continue to expand. A ransomware development kit is already making rounds on underground forums. This one, however, will not require users with coding skills to use. It's been designed to allow users to build their own file-locking malware with an Android phone.
The Internal Revenue Service (IRS) has issued a message warning the public about a ransomware campaign that uses a bogus email to impersonate the IRS and the Federal Bureau of Investigation (FBI). This is not the first scheme to ever use the tactic, it's been proven to have been effective before. The ransomware business has been profitable enough to assume that the "industry" will only continue to expand. A ransomware development kit is already making rounds on underground forums. This one, however, will not require users with coding skills to use. It's been designed to allow users to build their own file-locking malware with an Android phone.
The Trojan Development Kit (TDK) app, which is downloadable from hacking discussion boards for free, comes with an interface that allows users to easily create their own variants. After filling out forms, the user only needs to press the 'create' button to initiate a conversation with the app developer for payment. It was discovered that the TDK samples were directed at Chinese-speaking users.
Like the ransomware-as-a-service (RaaS) business model, ransomware development kits for mobile devices could contribute to the increasing cases of ransomware infections. For instance, the emergence of a new SLocker variant was created using the Android integrated development environment (AIDE), a program used to develop Android apps directly on an Android device. This particular variant even redirects victims to a QQ forum where users are invited to create their own custom ransomware for a fee.
Here are other notable ransomware stories:
Defray
Defray is a new ransomware variant discovered targeting healthcare, education, manufacturing, and technology organizations using sophisticated phishing emails. The attackers used a Word document with an embedded OLE packager object that installs the ransomware when clicked.
Its ransom note demands US$5,000 in Bitcoin (BTC) in exchange for a decrypt key, and encourages victims to negotiate the payment via email. In addition, its note provides an alternative communication channel—BitMessage—in case email takes too long.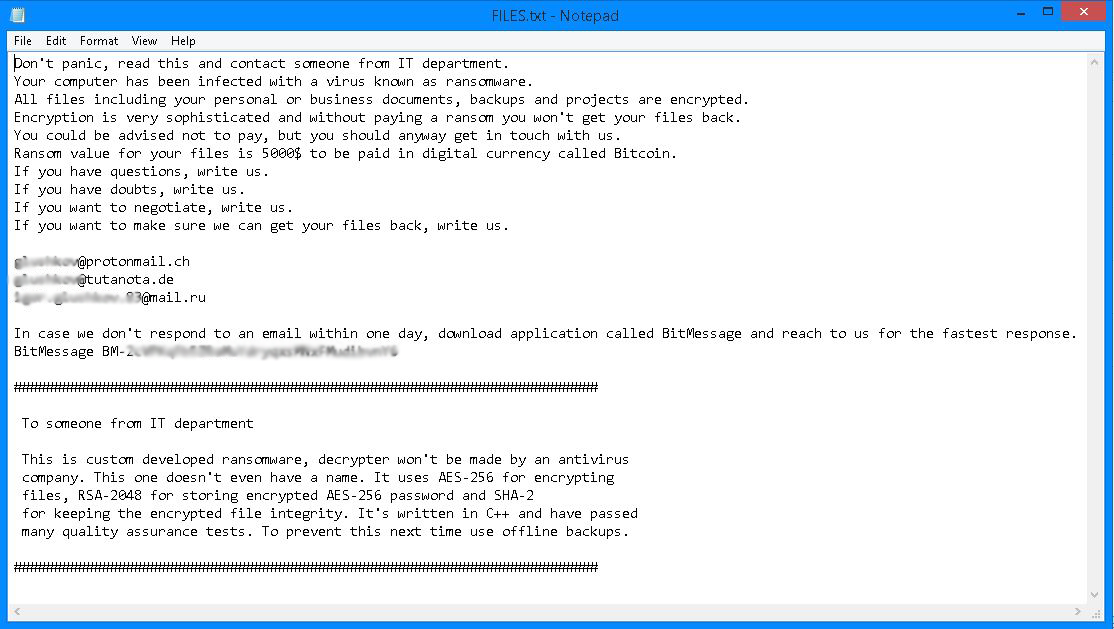 Figure 1. Defray ransom note
Figure 1. Defray ransom noteFlatChestWare
FlatChestWare is a Hidden Tear-based variant that arrives as a Win32 executable file. The ransomware variant also prompts a bogus 'Windows Update' dialog box, which is intended to trick users into restarting their endpoints.
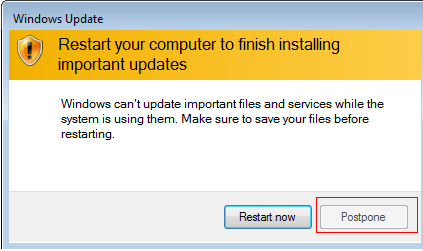
Figure 2. FlatChestWare’s fake dialog box
When the 'Restart now' button is clicked, the machine will reboot and subsequently display a ransom note. The lock screen has an animated image of an umbrella-carrying girl on the left, and a note on the right. FlatChestWare encrypts files that include Microsoft Office documents, as well as audio and video file formats.
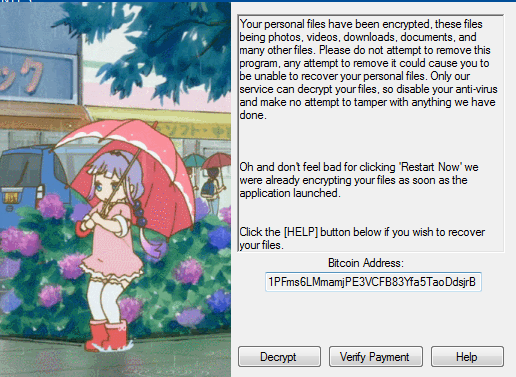
Figure 3. FlatChestWare ransom note
Users and enterprises can adopt these best practices to lower or eliminate the risk of ransomware infection.
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
End users and enterprises can also benefit from multilayered mobile security solutions such as Trend Micro™ Mobile Security for Android™ (available on Google Play), and Trend Micro™ Mobile Security for Apple devices (available on the App Store). Trend Micro™ Mobile Security for Enterprise provide device, compliance and application management, data protection, and configuration provisioning, as well as protect devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Postagens recentes
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks