The Targeted Attack Trends in APAC in 1H 2014
 View the full report on Targeted Attack Trends in Asia-Pacific: 1H 2014
View the full report on Targeted Attack Trends in Asia-Pacific: 1H 2014
If there’s one area attackers continued to focus on this year, it is in evading detection. Rounding up tactics we saw against Asia-Pacific countries during the first half of 2014, a number of notable techniques stood out to portray attackers’ apparent effort to keep their heads low for maximum destruction.
In an under-the-radar tactic never seen before, attackers used the cloud-based file storage platform Dropbox as a download site for a backdoor’s command-and-control (C&C) settings. It was also recently that attackers abused the interactive scripting tool Windows® PowerShell in a previously unheard of technique. Meanwhile, the Siesta campaign used a built-in sleep timer feature in the OS to stay dormant and avoid being detected easily.
Through all these, attackers remain bent on stealing as much confidential company data as they can. Seeing as four in five attacks (80%) seen in the region used spear-phishing emails as the infection vector, the employees who yield to the attacks themselves can be considered fatal flaws in the organization’s security.
Data gathered from these phishing mails show that majority, 57%, of the attachments used by threat actors are Microsoft Office files. This can be attributable to attackers being aware that these file types are typically passed around for company communications. Many organizations also fail to regularly patch or upgrade their versions of Microsoft Office, leaving them vulnerable to exploit attacks. Apart from Microsoft Office files, .RAR (18%) and .7Z (8%) files are also commonly used by threat actors.
Globally, nearly half (46%) of the victims of targeted attacks were located in Taiwan (46%), while other victims are in Japan (20%) and the US (12%).
Notably, threat actor servers attacking organizations in Asia-Pacific were tracked to come from the United States (48%), Taiwan (13%), and China (12%).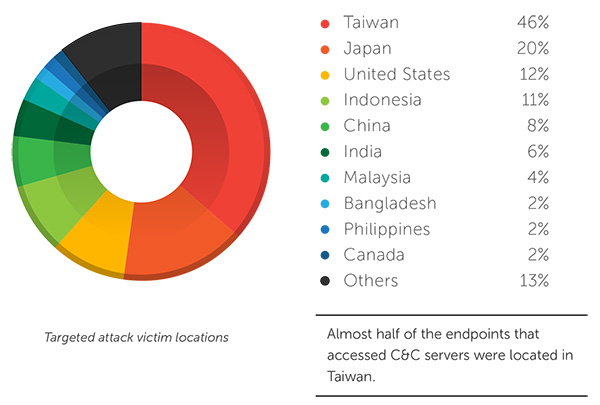
Organizations need to be wary of the effects of targeted attacks, the top of which are potential brand damage, damage to professional reputation, and potential loss of intellectual property, according to a recent Harvard Business Review study.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
HttpContext.GetGlobalResourceObject("ES","RecentPosts")%>
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One