Ransomware Recap: Ransomware Taking Advantage of Older, Popular Variants
The activity of Hidden Tear variants have been on the rise since March this year and there seems to be no signs of it stopping. The popularity of the open-source ransomware continues to encourage the development of more dangerous versions of the original, which cybercriminals are using in attacks that are growing more sophisticated.
The two newcomers are tagged with the names CryMore (detected by Trend Micro as Ransom_HIDDENTEARCRYMORE.A) and R4bb0l0ck (Ransom_HIDDENTEARRABLOCK.A).
CryMore targets a range of common file types except for .jar, .exe, .vbs, .dll,.lnk, and .encrypt, and encrypts these files using the AES encryption algorithm.The variant arrives as a Win32 EXE file, and is written in Microsoft Intermediate Language (MSIL). The ransom note demands Bitcoin payment in exchange for a decrypt key, but doesn’t specify the amount.
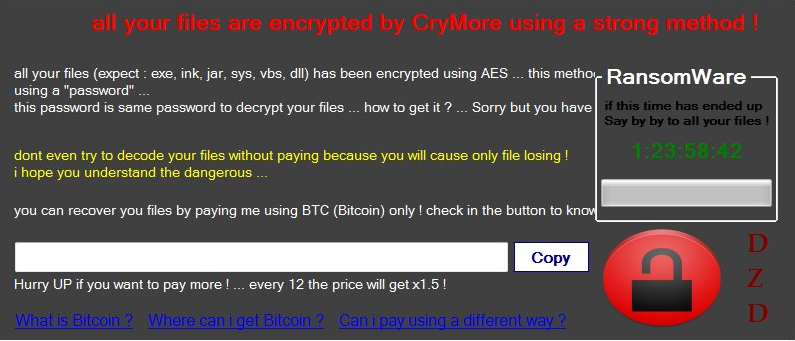
Figure 1. CryMore ransom note
R4bb0l0ck features a ransom note written in Dutch language. Translated to English, the note warns the victim that “it will be too late” if the victim doesn’t send an email to the provided address within an hour after encryption. The Hidden Tear variant, which arrives as a PDF document, also demands that the victim meets other conditions, such as having privileges on an account indicated in an email, and being given “5,000 crowns” and “5,000 diamonds” using the same account.
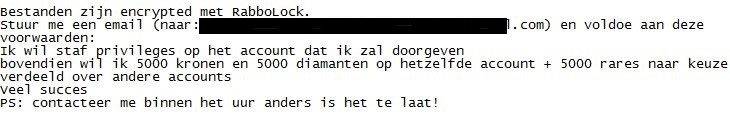
Figure 2. R4bb0lock ransom note
Hidden Tear isn’t the only ransomware to inspire cybercriminals to launch new attacks based on the original code of other ransomware. Last week, a new member of the JIGSAW crypto-ransomware family emerged in the form of The Dark Encryptor (detected by Trend Micro as Ransom_DARKENCRYPTOR.A). The variant was found in the wild with a typical image of Jigsaw plastered across its ransom note. Encrypting targeted files with a so-called military grade algorithm, the ransomware asks victims to pay US$100 in exchange for a decrypt key. The note also threatens to raise the ransom to $350 if payment is not made within five days.
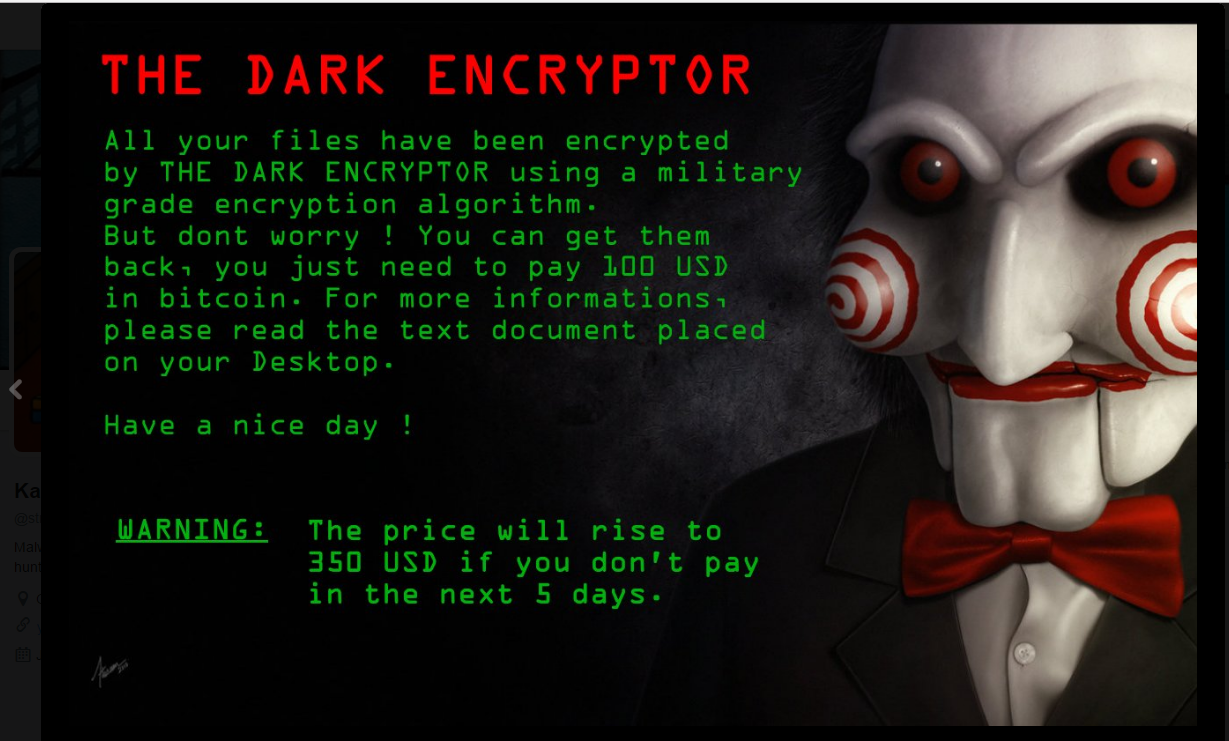
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers—whether physical, virtual, or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks