Ransomware Spotlight: INC
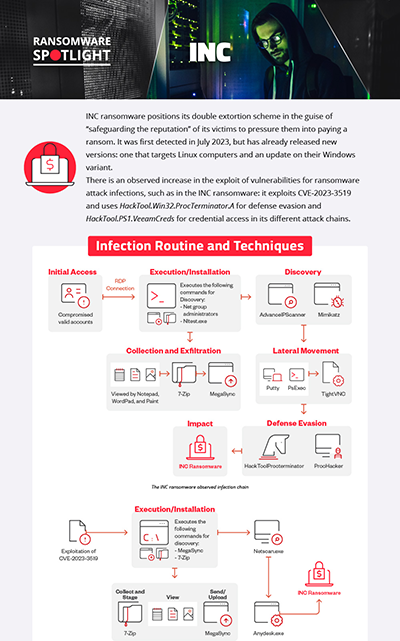
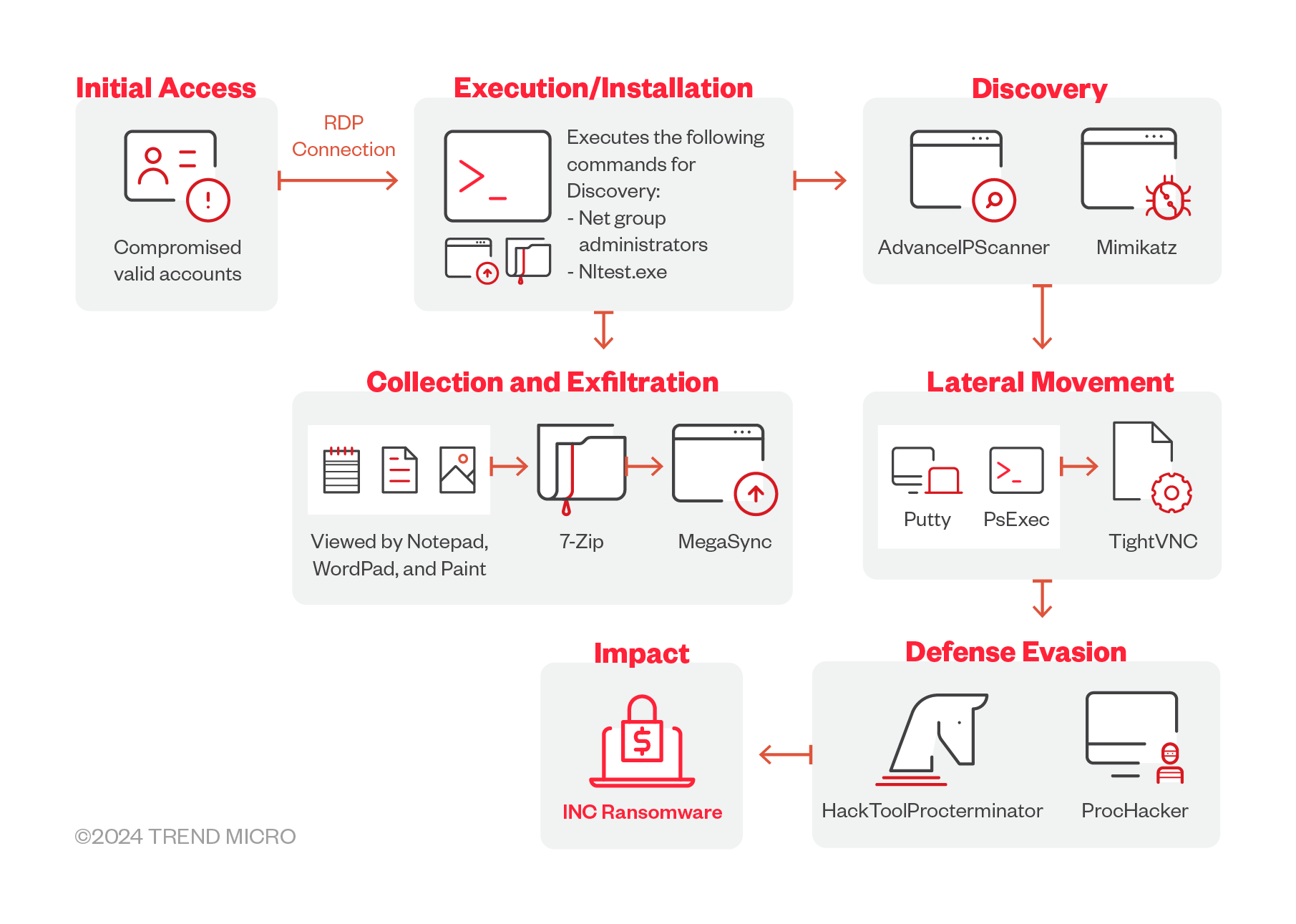
Infection chain and techniques
Initial Access
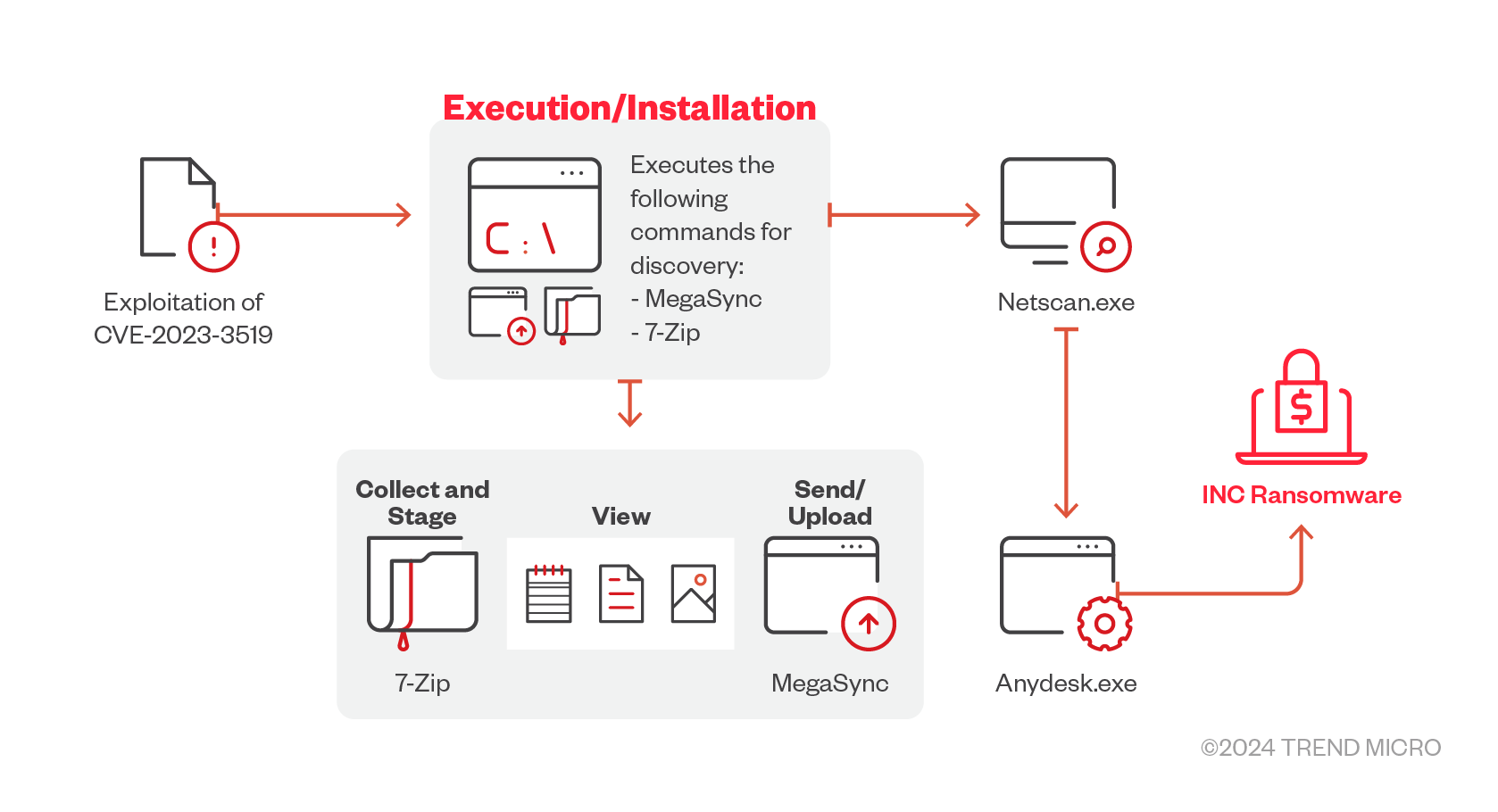
- INC ransomware uses purchased valid account credentials typically acquired through Initial Access Brokers. The group also targets victims via phishing in its early attacks. In November 2023, they have been observed to exploit the Citrix NetScaler vulnerability CVE-2023-3519 in an attack to gain initial access onto the victim’s network device.
Defense Evasion
- The INC ransomware uses HackTool.ProcTerminator and ProcessHacker to evade detection.
- New samples from the group reveal that the gang is employing a new tool to terminate processes running in their victim's system; among those tasks observed notably is specifically terminating TrendMicro-related processes and services.
Credential Access
- Recent samples of INC ransomware also reveal new tools used to dump credentials from Veeam Backup and Replications Managers.
Discovery
- The INC ransomware uses NetScan and Advance IP scanner to collect network information that later could be used in lateral movement.
- It has also been observed to use legitimate tools such as Notepad, Wordpad, and Paint to view files.
- It also downloads from an open directory tools for lateral movement such as Mimikatz and AdvanceIPScanner.
Lateral Movement
- The INC Ransomware uses PSexec, AnyDesk, and TightVNC to move through its victim’s system.
Impact
- The ransomware uses 7-Zip to archive data before exfiltration using MegaSync.
- INC ransomware also uses AES algorithm for its file encryption and has two encryption modes: its fast encryption encrypts at a fixed value of 1,000,000 bytes and skips larger bytes of data, while its medium encryption encrypts at a fixed value of 1,000,000 bytes and skips smaller bytes of information.
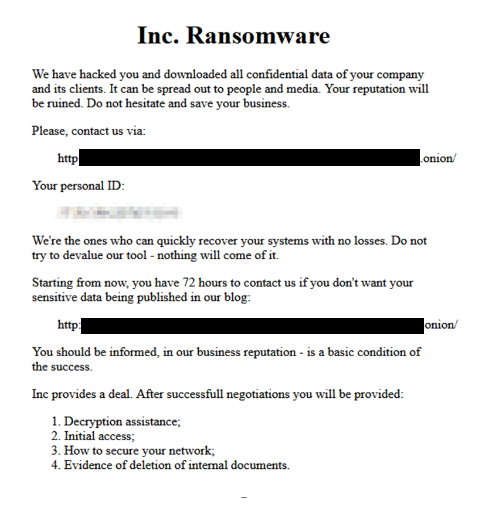
Figure 3. A sample ransom note dropped by INC ransomware after successful data encryption
Additional information
In December 2023, the INC ransomware dropped a Linux version while new versions of the first samples have been detected in March 2024. In the following table is a comparison of the command-line arguments across observed versions of INC ransomware.
| Early Windows version | Linux | Latest Windows version | Description |
|---|---|---|---|
| --debug | --debug | --debug | The print debugging logs of the sample to the terminal |
| --file | --file | --file | Specifies a file to be encrypted |
| --dir | --dir | --dir | The path to encrypt |
| Does not exis | --daemon | Does not exist | Daemonize the current sample |
| Does not exis | --motd | Does not exist | Modifies message of the day |
| Does not exis | --skip | Does not exist | Skips killing of VM's |
| --sup | Does not exist | --sup | Stops using processes |
| --ens | Does not exist | --ens | Encrypts network shares |
| --lhd | Does not exist | --lhd | Encrypts hidden boot and recovery volumes |
| Does not exist | Does not exist | --mode | Chooses mode for file encryption (fast, medium, slow) |
| Does not exist | Does not exist | --hide | Hides console window |
| Does not exist | Does not exist | --safe-mode | Kills process/services by mask |
| Does not exist | Does not exist | --help | Displays the arguments |
| Does not exist | Does not exist | --kill | Boots the victim’s machine into safemode |
MITRE tactics and techniques
| Persistence | Defense Evasion | Discovery | Impact |
|---|---|---|---|
T1543 - Create or Modify System Process | T1562.009 - Impair Defenses: Safe Mode Boot T1070 - Indicator Removal | T1057 - Process Discovery It terminates the following processes: | T1486 - Data Encrypted for Impact The INC ransomware avoids the following files for encryption with the following file extension: T1490 - Inhibit System Recovery T1491.001 - Internal Defacement |
Summary of malware, tools, and exploits used
Security teams can watch out for the presence of the following malware tools and exploits that are typically used in INC ransomware:
| Initial Access | Lateral movement | Discovery | Exfiltration | Defense Evasion | Credential dumping | Collection | Impact |
|---|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
Top affected countries and industries from Trend Micro threat intelligence
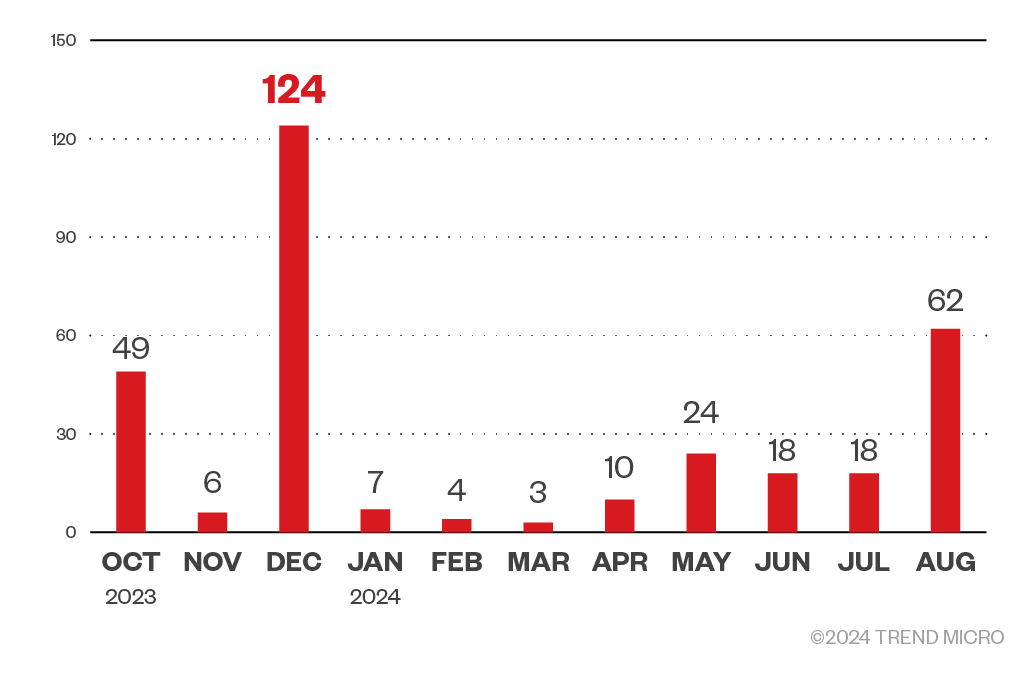
Based on Trend threat intelligence data, there were at least 325 attack attempts by the INC ransomware from October 2023 to August 2024. The INC ransomware group was most active in December 2023, with 124 attack attempts detected in Trend Micro environments. The gang took a breather for the first quarter of 2024, but is increasingly active as the year progresses.
Figure 4. A monthly breakdown of INC ransomware attack attempts based on Trend Micro threat intelligence
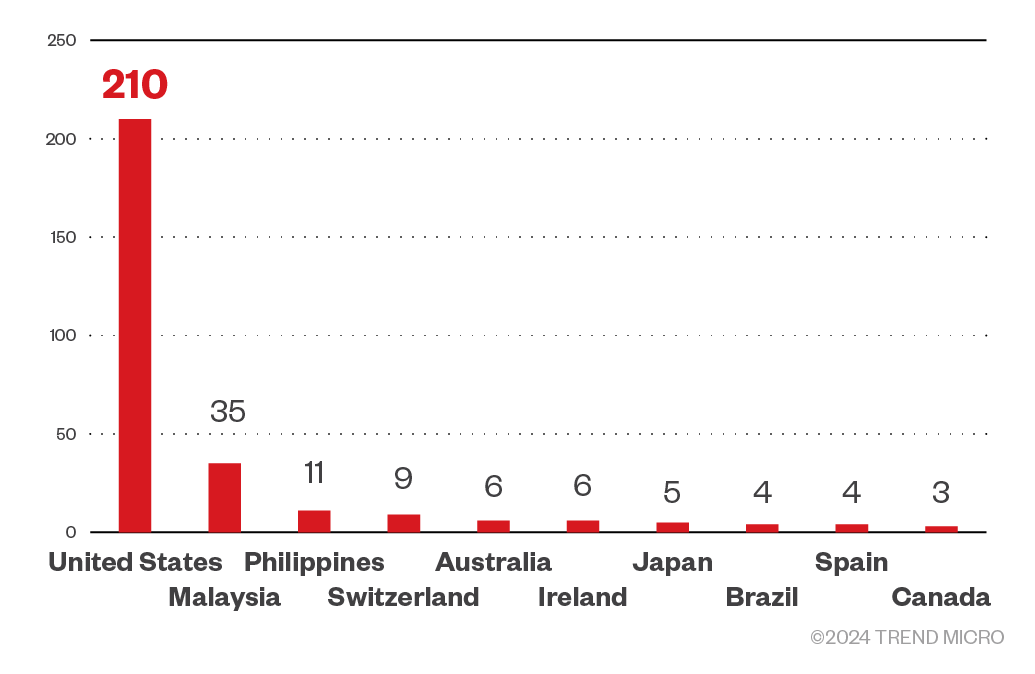
The INC ransomware group targeted enterprises in the United States the most, followed by Malaysia and the Philippines. It also targeted Switzerland, Australia, and Ireland. Countries that did not make into the top 10 targeted by the gang include Austria, Germany, Thailand, South Korea, and France.
Figure 6. The top 10 breakdown of countries targeted by the INC ransomware group based on Trend Micro threat intelligence
Targeted regions and industries according to INC ransomware’s leak site
This section looks at data based on attacks recorded on the leak site of the INC ransomware and a combination of our open-source intelligence (OSINT) research and an investigation from July 2023 to September 2024.
The gang has so far added at least 165 victims to its leak site, but as with double-extortion ransomware groups, the actual victim count is likely higher; the group only leaks data from victims who refused to pay ransom.
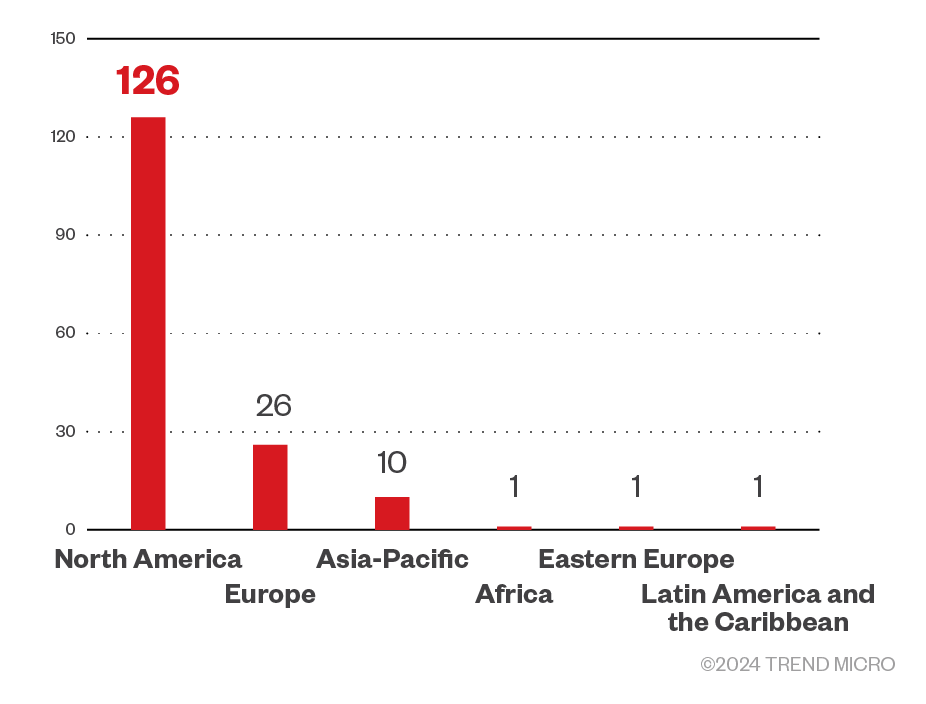
Of the total number of revealed victims, the INC ransomware targeted enterprises in the North American region the most.
Figure 7. The distribution by region of the INC ransomware’s victim organizations
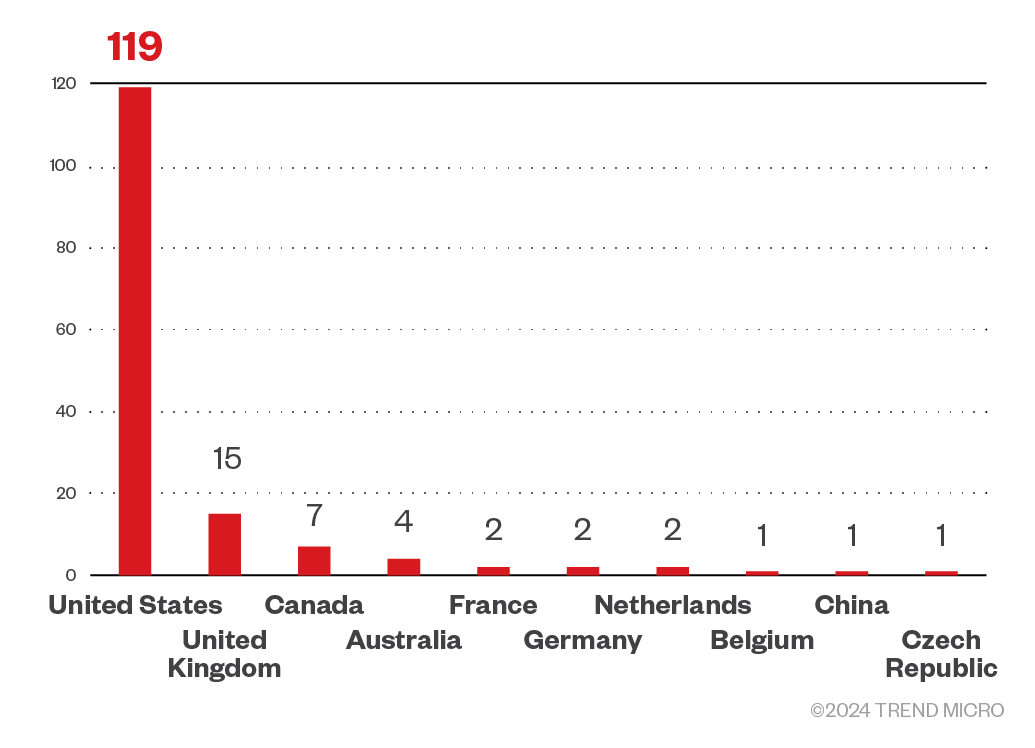
INC ransomware targeted enterprises in the United States the most. It also launched attacks on businesses from the United Kingdom, Canada, Austraia, and France.
Figure 8. The top 10 countries targeted by the INC ransomware
Sources: INC ransomware’s leak site and Trend Micro’s OSINT research (July 2023 - September 2024)
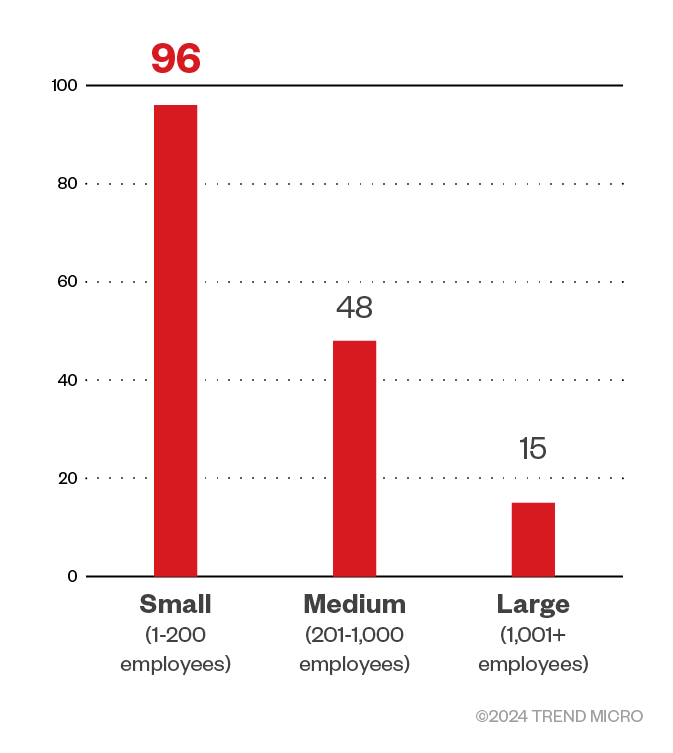
Majority of the INC ransomware’s victim organizations were small businesses followed by medium-sized businesses. The gang seldom targeted large enterprises.
Figure 9. The distribution by organization size of INC’s victim organizations
Sources: INC ransomware’s leak site and Trend Micro’s OSINT research (July 2023 - September 2024)
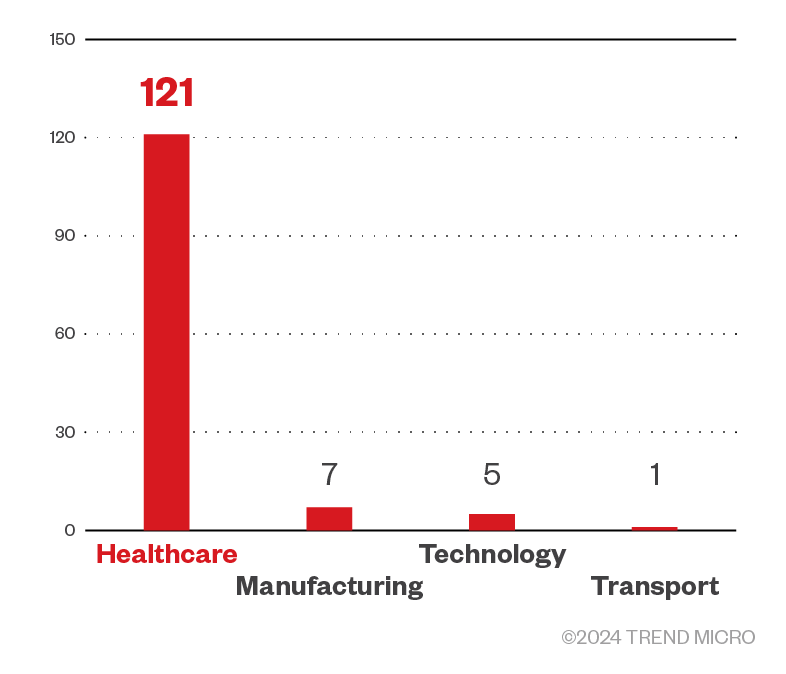
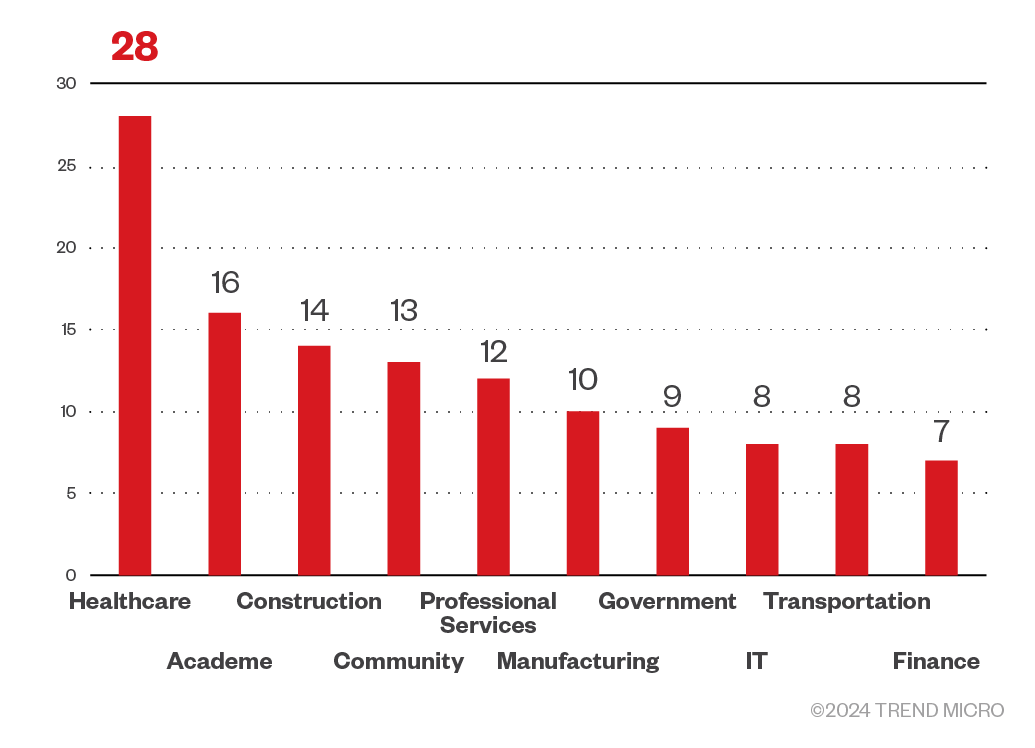
Cybercriminals behind INC ransomware mostly targeted healthcare organizations but also attacked organizations in the academe, as well as the community sector such as non-profit organizations and religious organizations. INC ransomware also targeted enterprises in the construction, professional services, and manufacturing industries.
Figure 10. A breakdown of the top 10 industries targeted by INC ransomware attacks
Sources: INC ransomware’s leak site and Trend Micro’s OSINT research (July 2023 - September 2024)
Trend Micro Vision One Threat Intelligence
To stay ahead of evolving threats such as INC ransomware, Trend Micro customers can access a range of intelligence reports and threat insights in Trend Vision One. Vision One threat insights help customers stay ahead of cyber threats before they happen and be better prepared for emerging threats by offering comprehensive information on threat actors, their malicious activities, and the techniques they use. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and respond effectively to threats.
Trend Vision One Intelligence Reports App [IOC Sweeping]
The following can be searched in the Trend Vision One Intelligence Reports dashboard for IOC sweeping:
- [Spot Report] Binary Metamorphosis: Inc. Ransomware Adapts, Sets Sights on Diverse ESXi Networks
- Lynx Ransomware
- [Spot Report] Analysis of Newly Discovered Variant of INC Ransomware and its Capabilities
- [Hot Threats]: New Indicators used by Water Lalawag Threat Actor - 2024/10/24
Trend Vision One Threat Insights App
Threat Actors
Emerging Threats
Trend Vision One Hunting Query
Trend Micro Vision Once Customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Trend Vision one customers can use the following hunting query to search for INC ransomware within their system:
fullPath:(*.INC* OR (*INC-README.txt* AND *INC-README.html)) AND ((processCmd:"(?:*\\psexec.exe OR ?:*\\cmd.exe)" AND objectFilePath:"*.exe*(--file OR --dir OR --ens OR --lhd OR --sup OR --debug)*")
More hunting queries are available for Vision One customers with Threat Insights Entitlement enabled
Recommendations
Ransomware groups continue to use tried and tested techniques such as spear-phishing to lure victims and gain access to enterprise systems. Despite only being over a year old, INC ransomware has already victimized many enterprises, proving the continued effectivity of these simple but hardy techniques.
There is also an increase in vulnerability exploits used for ransomware attack infection vectors, as observed in INC ransomware; SOCs should prioritize patching network devices to secure their respective enterprises and minimize chances of successful attacks.
To protect systems against INC ransomware and other similar threats, organizations can implement security frameworks that allocate resources systematically to establish a strong defense strategy.
The following are some best practices that organizations can consider to help protect themselves from ransomware infections:
Audit and inventory
- Take an inventory of assets and data
- Identify authorized and unauthorized devices and software
- Make an audit of event and incident logs
Configure and monitor
- Manage hardware and software configurations
- Grant admin privileges and access only when necessary to an employee’s role
- Monitor network ports, protocols, and services
- Activate security configurations on network infrastructure devices such as firewalls and routers
- Establish a software allow list that only executes legitimate applications
Patch and update
- Conduct regular vulnerability assessments
- Perform patching or virtual patching for operating systems and applications
- Update software and applications to their latest versions
Protect and recover
- Implement data protection, backup, and recovery measures
- Enable multifactor authentication (MFA)
Secure and defend
- Employ sandbox analysis to block malicious emails
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network
- Detect early signs of an attack such as the presence of suspicious tools in the system
- Use advanced detection technologies such as those powered by AI and machine learning
Train and test
- Regularly train and assess employees on security skills
- Conduct red-team exercises and penetration tests
A multilayered approach can help organizations guard the possible entry points into the system (endpoint, email, web, and network). Security solutions can detect malicious components and suspicious behavior could help protect enterprises.
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before the ransomware can do irreversible damage to the system.
- Trend Micro Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of Compromise (IOCs)
The IOCs for this article can be found here. Actual indicators might vary per attack.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.

 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks