Ransomware Recap: Old Ransomware, New Features
 The ransomware CERBER, which has gained notoriety as a constantly evolving malware over its lifespan, has been spotted with new variants (Detected by Trend Micro as VBS_CERBER.DLCYG, RANSOM_CERBER.ENC, RANSOM_CERBER.VSAGD and TROJ_CERBER.AL) utilizing a loader that allows the malware to avoid machine learning detection.
The ransomware CERBER, which has gained notoriety as a constantly evolving malware over its lifespan, has been spotted with new variants (Detected by Trend Micro as VBS_CERBER.DLCYG, RANSOM_CERBER.ENC, RANSOM_CERBER.VSAGD and TROJ_CERBER.AL) utilizing a loader that allows the malware to avoid machine learning detection.
The CERBER variants arrive on a user’s system via an email with links to a Dropbox account containing a self-extracting archive. Once clicked and executed, the archive then infects the target system with the payload. The payload includes multiple files—notably, a loader that checks if the system is running in a virtual machine or in a sandbox. In addition, it will also check if the system contains certain analysis tools or anti-virus software. If these conditions are met, then the malware will stop running, else it will proceed with the main ransomware payload.
CERBER manages to evade machine learning approaches by using a multistep loading mechanism that is injected into a running process. This poses a problem for solutions with static machine learning features that only analyze the contents of a file for matching malicious behavior without taking into account how these files are executed. However, these ransomware types can still be detected by multilayer anti-malware solutions that don’t primarily rely on machine learning for detection.
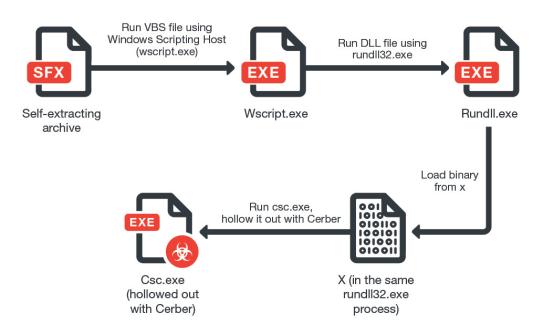
Figure 1: CERBER Infection Routine
SPORA v2
Another familiar ransomware made the rounds this week, with a new variant of SPORA (Detected by Trend Micro as RANSOM_SPORA.F117C2) that adds worm capabilities to the already dangerous malware.
SPORA v2 infects a user’s system when they click a Google Chrome popup advertisement, allegedly to update the “Chrome Font Pack” to properly display the “HoeflerText” font. If the user clicks on the ad, it will lead to a URL that contains a malicious program disguised as a legitimate one. Once the malware is run, it will then proceed to infect the user’s computer.
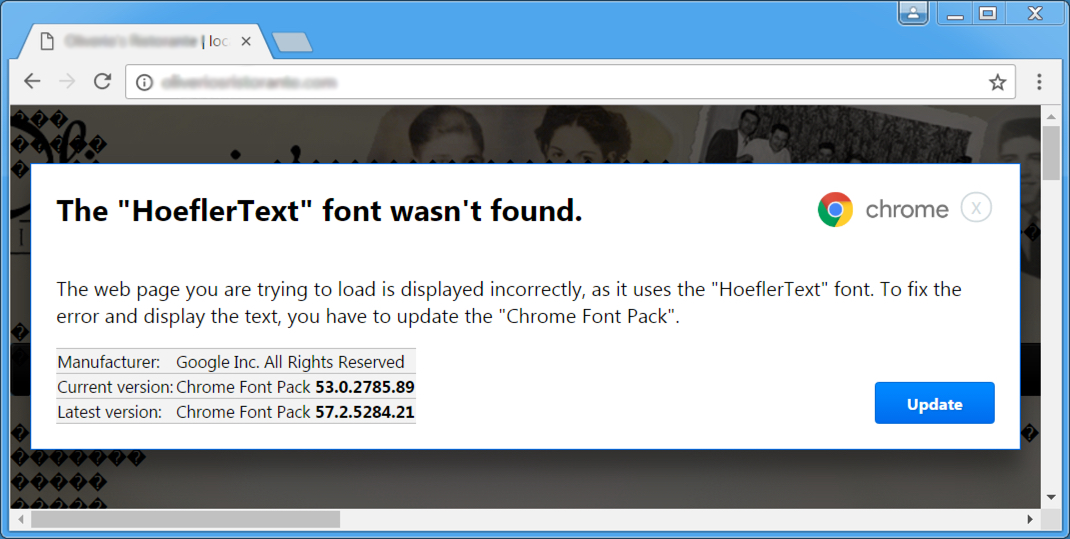
Figure 2: Fake popup for a “Chrome Font Pack”
This new SPORA variant will now drop copies of itself in fixed and removable drives as well as in network shares. In addition, it will enumerate the first level directories of every drive and network share it finds. Like the first version of SPORA, v2 deletes the registry value “"HKLM\Software\Classes\lnkfile IsShortcut", tricking users into thinking that the shortcut file is a normal folder without the small arrow that is typically found on shortcut links. Another change found in SPORA v2 is the generated RSA Key, RSAPrivKey2, which is now integrated into the ransom note instead of being a separate file. After execution, SPORA v2 will encrypt files such as images and Microsoft Office documents using the RSA-1024 algorithm. However, the malware will retain the extension names of the files it encrypts.
After encryption, SPORA v2 will display the ransom note, which comes with a unique machine-specific file name using the following format: XXOOO-AAAAA-BBBBB-CCCCC-DDDDD.html, with the first two letters (XX) being the2-digit country code. The rest of the letters are randomized and specific for each victim.
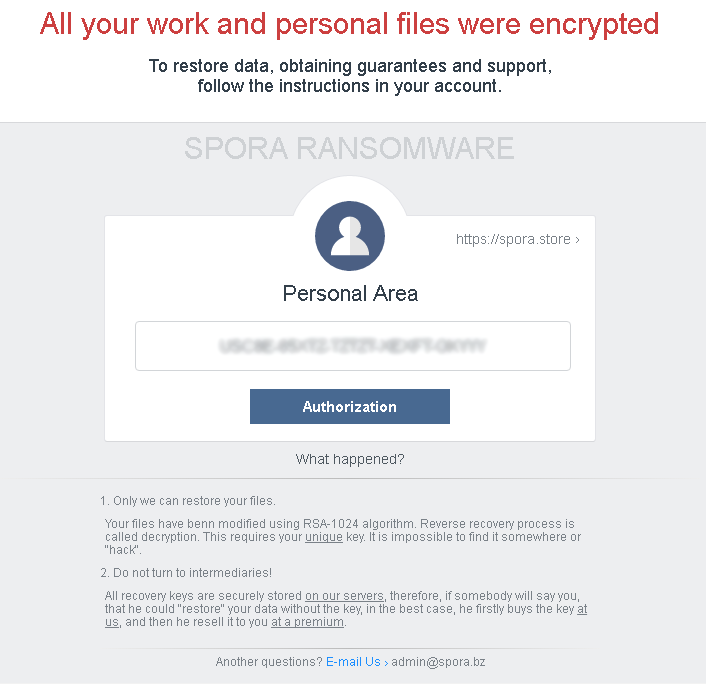
Figure 3: SPORA V2 ransom note
HiddenTear
During the last two ransomware recaps, we highlighted new HiddenTear variants such as Enjey Crypter (detected by Trend Micro as RANSOM_HiddenTearEnjey.A), which was based off the EDA2-ransomware. Developed alongside HiddenTear, EDA2 is also an open source educational ransomware that was later found being abused by cybercriminals for malicious purposes. This week, a further slew of variants were discovered, each with minor variations to the HiddenTear ransomware.
AngleWare (Ransom_HiddenTearAngleWare.A)
This HiddenTear-based ransomware drops a ransom note asking for the expensive amount of 3 bitcoins (roughly $3000). Encrypted files are appended with the .AngleWare extension.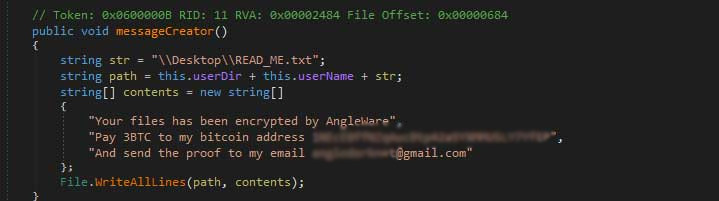
Figure 4: AngleWare code (Image via Bleeping Computer)
GC47 (Ransom_HiddenTearGCFS.A)
This variant tricks users into downloading malware by displaying a fake Windows “upgrade” box. Once the user clicks the “ok” button, its encryption routine begins. The affected files, which include documents, media files, and images, are appended with the .Fxck_You extension. The ransom note asks for $50, or roughly 0.04 bitcoin for decryption.
Zorro (Ransom_HiddenTearZorro.A)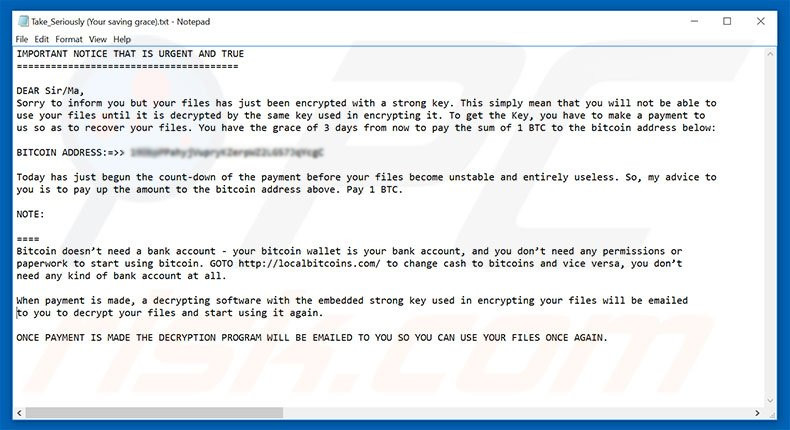
Figure 6: Zorro ransom note
The dangers of open-source ransomware
Both HiddenTear and EDA2 were initially developed as open-source ransomware for educational purposes. However, cybercriminals were able to take the source code of both ransomware and use them to develop malicious variants. Given the tendency of cybercriminals to adopt and modify malware for their own purposes, the development and distribution of open-source ransomware will always be a risky endeavor. As such, researchers must take steps to ensure that any source code they distribute – whether for educational purposes or otherwise—are not easily accessible. One example of how to mitigate the risks posed by open-source ransomware is by distributing it to targeted recipients via secure channels.
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks