Ransomware Recap: Nov. 7- 18, 2016
 The reign of Cerber as one of the most visible ransomware families to have emerged of late continues with the consistent release of updated versions with evolved tactics. Just last October, three malvertising campaigns and a compromised site campaign was seen using version 4.0 (detected by Trend Micro as RANSOM_CERBER.DLGE), a version that was released just a month after version 3.0.
The reign of Cerber as one of the most visible ransomware families to have emerged of late continues with the consistent release of updated versions with evolved tactics. Just last October, three malvertising campaigns and a compromised site campaign was seen using version 4.0 (detected by Trend Micro as RANSOM_CERBER.DLGE), a version that was released just a month after version 3.0.
Over the past two weeks, Cerber demonstrated new tricks it added in its updated versions. The evolved routines and techniques spotted early in its lifecycle include the addition of a DDoS component in its attack, the use of double-zipped Windows Script Files and cloud productivity platform, and acting as a secondary payload for an information-stealing malware. This time, Cerber, which earned almost US$200,000 in July, 2016 alone, attempts to ramp up its money-making schemes as it adds encrypting database files to its routines, possibly meant to go after bigger enterprise targets.
While other existing ransomware families have been known to encrypt database files, this routine was likely adopted by Cerber developers to target enterprises and businesses that are more likely to pay the ransom given the crucial nature of these files. This routine was spotted in versions as early as 4.0 but has since been integrated into the succeeding versions of Cerber released within the past couple of weeks.
Cerber 4.1.5 (detected by Trend Micro as RANSOM_CERBER.F116K8), in fact, surfaced within a day after its previous version’s release. One of the samples studied by Trend Micro researchers involves a spam email spoofing an online payment service provider. Notifications of an exceeded credit line are used as a hook to coerce would-be victims into authenticating their accounts. This action leads to the download and installation of the ransomware into the system. Other spam emails uncovered involve messages masquerading as an invoice, with attached Word documents embedded with malicious macro aiding in the download and execution of the ransomware.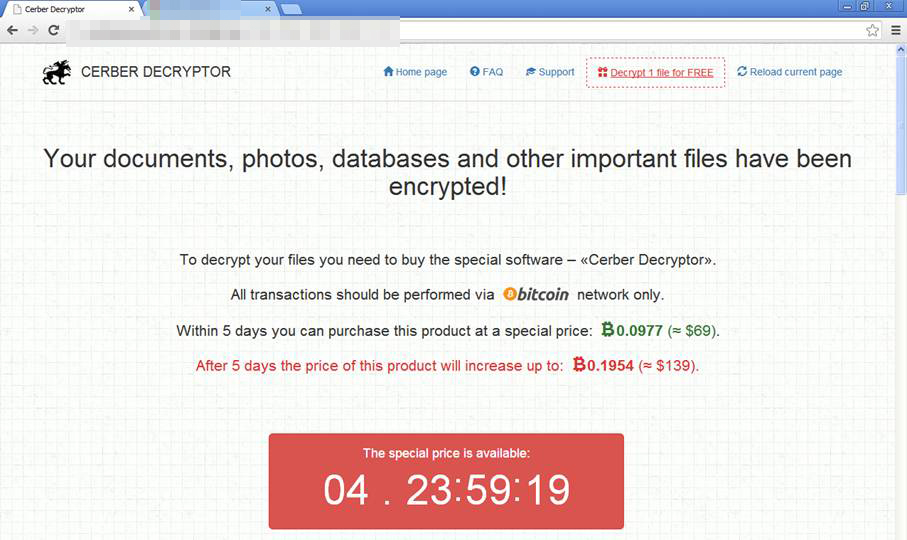
Interestingly, it demands a cheaper ransom compared to its earlier variants. A “special” price of 0.0977 bitcoins is asked from the victim, or an amount equivalent to $69 on a five-day grace period. Failure to settle the ransom will increase the ransom to 0.1954 bitcoins (around $139).
With the success of Cerber, the emergence of copycats attempting to reap the same kind of notoriety and monetary rewards is no longer surprising. In the past couple of weeks, CerberTear (detected by Trend Micro as RANSOM_HIDDENTEARCERBER.A), a ransomware variant based on the open-source ransomware Hidden Tear surfaced. Following its file encryption routine, the ransomware appends the extension, .cerber to its locked files. A ransom note, resembling that of the ransomware it impersonates, then appears directing all transactions to a Bitcoin network.
Here are other notable ransomware stories that surfaced in the past two weeks:
Shortly after the release of master decryption keys and decryptor for Crysis, a ransomware family that emerged in June 2016, reports of activity of a new variant patterned after the former surfaced. Dharma (detected by Trend Micro as RANSOM_CRYSIS.F116KI) uses asymmetric cryptography before appending the .[bitcoin143@india.com].dharma extension to the filename of each locked file while other variants use the extension .[worm01@india.com].dharma. This means that an encrypted file named “photo.jpg” becomes photo.jpg.[bitcoin143@india.com].dharma.
The ransom note is then saved as a text file in each of the folders containing infected files. The ransom note does not disclose any particular ransom amount but simply asks the victim to contact the developers via the email address on the appended extension names.
CITOXE and SHELL LOCKER
Not long after the US elections drew to a close, cybercriminals are once again jumping in on the notable characters and incidents involved during the event. Developers quickly took the feud between President-elect Donald Trump and German Chancellor Angela Merkel and turned it into ransomware variants that are said to be patterned after Exotic (detected by Trend Micro as RANSOM_EXOTIC.A).
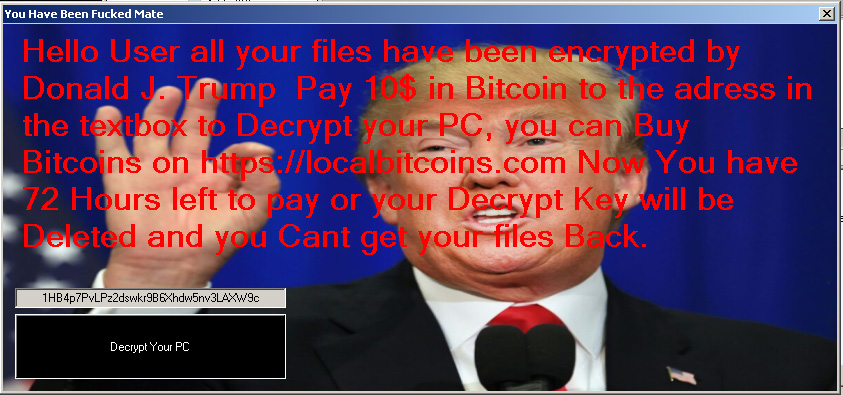
One variant (detected as RANSOM_CITOXE.A) disables Task Manager and uses AES encryption to lock its targeted files. Once encrypted, the file names of the locked files are then appended with the extension name .TRUMP. The ransom note with a Donald Trump image then asks for a $10 payment in bitcoin within a 72-hour deadline. Once the deadline passes, the developers threaten to delete the decryption key, making it impossible to get the files back.
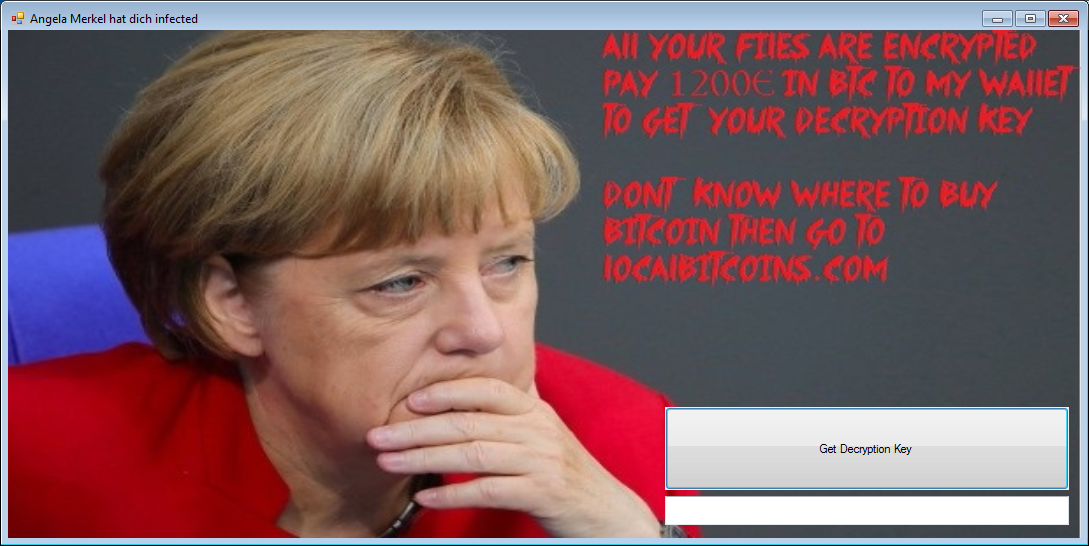
The other variant (detected by Trend Micro as RANSOM_CITOXE.B) masquerades as a Google Chrome updater, deliberately tricking the would-be victim by spoofing the Google Chrome icon. Similar to the previous variant, it disables the Task Manager and carries out its encryption routines using the AES algorithm. Once its encryption routine is done, it encodes filenames and adds the .angelamerkel extension to the encrypted files. This then leads to the display of a ransom note with the image of Angela Merkel, asking for a rather hefty ransom of 1200 euro in bitcoins, amounting to more than US$1,280. Within the same period, another ransomware variant that resembles Exotic surfaced. Shell Locker (detected by Trend Micro as RANSOM_EXOSHELL.A) drops a copy of itself in the targeted system’s Startup folder, enabling it to automatically execute upon reboot. After its encryption routine, it appends the extension .L0cked to the filename of its infected files. A ransom note then notifies the victim that all photo, video, and audio files are encrypted and can only recovered when the ransom of $100 ransom in bitcoins is paid within 48 hours. As with other variants that uses this similar ploy, it threatens to delete the encrypted files when the ransom is ignored.
TELECRYPT
Researchers uncovered traces of a new ransomware variant, which is the first to use the Telegram channels as its command-and-control (C&C) server. Because of this, Telecrypt (detected by Trend Micro as RANSOM_TELECRYPT.A) needs to establish a connection to its operators by creating a Telegram bot through the public Telegram API. Each newly-created bot is then provided a unique token ID hardcoded in the ransomware’s body.
After communicating with the C&C servers, encryption of specific file types targeted in the system begins. Telecrypt also keeps a log of all files that are successfully encrypted. Researchers note that certain variants of this ransomware append the extension .Xcri to the filenames of its encrypted files, while other variants leave the filenames as it is.
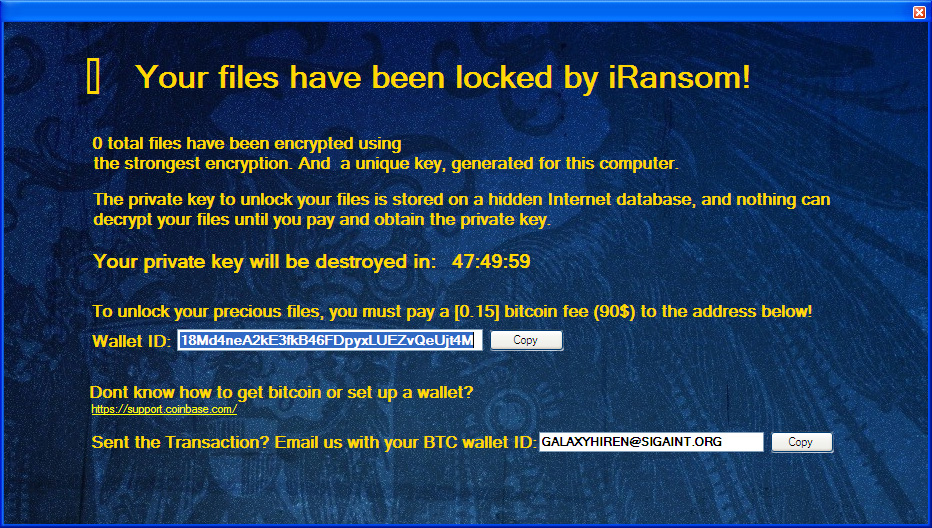
iRansom (detected by Trend Micro as RANSOM_ILOCKED.A) is one of the few ransomware variants that threatens to delete the decryption key instead of the hostaged files commonly seen in other families. Upon successful encryption, this variant appends the extension .Locked to the file names of each locked file. This then leads to the display of a pop-up screen that contains the ransom note, which demands a ransom of 0.15 bitcoins ($110) on a 48-hour deadline.
FSociety
In August 2016, ransomware developers gave a nod to the popular US television show, Mr. Robot by using imagery based on the show on their ransomware. When it was first spotted, FSociety ransomware (then detected by Trend Micro as RANSOM_CRYPTEAR.SMILA) showed signs of ongoing development, including incomplete payment details in its ransom note.

Recently, developers took a liking to the popular Hollywood TV series again, spawning another ransomware variant with a name that matches the earlier ransomware variant. This time, FSociety (detected by Trend Micro as RANSOM_REMINDMEFSOCIETY.A) made its presence felt with a working sample that is based on the Hidden Tear-based variant, Remind Me. This version of FSociety appends the extension name .dll to the filenames of its locked files. An undisclosed ransom payment is demanded from the victims on a five-day deadline. Failure to settle the ransom will then lead to the deletion of the encrypted files.
RANSOC
A unique ransomware variant ramps up its extortion scheme not by encrypting system files but by collecting malicious content coming from victim’s computer and using it as leverage for extortion. Ransoc (detected by Trend Micro as RANSOM_RANSOC.A) goes through an elaborate routine that involves scanning its targeted victim’s machine for local media containing strings that are associated with child pornography.
This particular variant is distributed by malvertising campaigns on adult websites. Ransoc does not necessarily encrypt files in exchange for a ransom payment. Instead, this variant locks the computer screen and displays a customized note warning the victim of a looming lawsuit, either for violation of intellectual property rights if the target system contains media illegally downloaded from torrent clients or from the serious offense of accessing sites that are, or can be, related to child pornography.
Such lawsuit can only be prevented by paying a particular ransom. Interestingly, unlike ransomware variants seen of late, Ransoc does not do payment transactions through Bitcoins. The ransom is settled via direct credit card payments.
CryptoLuck
Researchers uncovered a new ransomware family that is distributed by the RIG-E exploit kit via malvertising. CryptoLuck (detected by Trend Micro as RANSOM_CRYPTOLUCK.A) makes use of an interesting infection routine that involves the abuse of the legitimate GoogleUpdate.exe executable as well as DLL hijacking to install the malware onto the targeted machine.
This variant also does a series of checks to see if it's being run on a virtual machine. When it does, it is capable of terminating itself. If not, it scans all known drives and even unmapped network shares to look for files to encrypt. Upon successful infiltration, filenames of the locked files will be appended with the .[victim_id]_luck. This means that a unique alphanumeric ID given to a victim will be incorporated in the new filenames of the encrypted files. For instance, an image named photo.jpg encrypted in the system of a victim with an ID of 0012A345 will have new file name photo.jpg. 0012A345_luck. It then asks for a steep ransom of 2.1 bitcoins, which amounts to more than $1,500 to be settled in a 72-hour window.
The continuing rise of new and updated variants and families shows that cybercriminals are still raking in profits. A multi-layered approach is vital to defend against ransomware. That way, all possible gateways of compromise remains intact and secure. A solid back-up of valuable files, on the other hand, mitigates the damage brought by a ransomware infection.
Ransomware solutions:
Trend Micro offers different solutions to protect enterprises, small businesses, and home users to help minimize the risk of getting infected by ransomware:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks