A Growing Goldmine: Your LinkedIn Data Abused for Cybercrime
A Growing Goldmine: Your LinkedIn Data Abused For Cybercrime
We looked into professional and business networking platform LinkedIn and how cybercriminals abuse the platform to victimize users and companies, and how they monetize posted personal, career, and organizational information.
As of November 2022, LinkedIn is considered the largest platform catering to professionals and companies’ information with approximately 875 million users in over 200 countries. This focus on work-related information is one reason why cybercriminals are attracted to the site. It is a big pool in which where they can find heaps of data on users and organizations as a reference, and build sophisticated attacks with carefully constructed fake profiles that are difficult to distinguish from real people. In some cases, cybercriminals use artificial intelligence tools to create real-looking, AI-generated headshots.
Advanced persistent threat (APT) group Lazarus has used LinkedIn for cybercriminal and espionage operations as recent as September 2022, targeting macOS users searching for jobs in the cryptocurrency industry. The group established initial contact with the victims via targeted private messages on the platform. In 2021, Nobelium APT threat actors targeted LinkedIn users with a Safari zero-day security gap. Through LinkedIn messaging, a spear-phishing campaign dubbed Ducktail targeted marketing and HR professionals to allow the group to take over Facebook Business accounts and abuse the ads function for malvertising deployments.
Once these accounts have been compromised, malicious actors share, sell, and package these credentials in the cybercriminal underground. LinkedIn started tackling fake profiles during the second half of 2021. The company removed 11.9 million fake accounts upon registration and another 4.4 million before they were ever reported by other users.
LinkedIn added new security features in October 2022 to combat fake profiles and threat actors. These new features include one that confirms whether a profile is authentic by showing it has a verified work email or phone number (similar to other social media platforms’ verified badges). Due to the platform’s scale and evolving mix of professional and social context, it is difficult to protect the user from every threat even with these features and the LinkedIn security team’s efforts as it enables personal, professional, social, and organizational damage once attacks occur via impersonation, for example.
Julia is a Marketing Director known for her unconventional campaigns. She has a large network of professional connections and is always looking for new challenges and opportunities to advance her career. Growing up wealthy in a big city, she has always had to prove she earned her spot in the industry with her skills.
Steven had always been attracted by the power of technology and the endless possibilities it offers. Growing up in a small town, he always felt like an outsider and was more interested in programming and computers rather than socializing. As he got older, Steven realized that his skills could be used to make good money; he has been a hacker for as long as he could remember. It was on LinkedIn, the professional networking site, that he seemingly found his mission as it was a goldmine of personal and business-related information.
He works from home, spends weeks studying the behavior and interests of specific individuals and companies to look for something he can exploit. He found Julia and her profile with posts about her job and aspirations. She seems unhappy with her current position, making her the perfect target and this situation the perfect opportunity.
Steven starts planning the attack. He builds a fake profile, brings in some fake connections, and posts motivational quotes to make the victim believe he is a recruiter from a big company. Then he crafts a phishing website to promote a high-level job in proposal and sends the message to Julie.
The next day, Julia was going through her LinkedIn feed over breakfast when she noticed a message that caught her attention. It’s from a recruiter reaching out to fill a high-level marketing position. He claims that it’s a high-paying job at a prestigious company and is considered a lifetime opportunity, so Julia quickly responds and begins chatting with the recruiter.
The recruiter sends Julia a link to apply for the job. Without hesitation, she clicks on the link and sees that the website looks professional and legitimate, so she starts filling out the application form with her personal information, resume, and other details, then submits.
Little did Julia know, the website was part of a phishing scam. The URL sent her to a fake LinkedIn login page that looked exactly like the real one, and now all her information was in the hands of the attacker.
Behind his computer, Steven felt this was the right hit. He changed the profile password to lock Julia out of her account. He started sending messages to Julia's connections and colleagues while pretending to be her, asking for sensitive information, sending phishing links, or asking them to open malicious documents. Some of her colleagues fell for the scam, which infected their computers with malware, giving Steven access to their files and the company's sensitive information.
Steven collected a lot of confidential and proprietary information from the company's computers and decided to sell the information on underground forums. He also gained unauthorized access to a lot of LinkedIn profiles and decided to monetize them. He posted the offer on the most famous underground marketplace, and raked in a lot of buyers willing to pay $50 to $100 per account after a few minutes.
Legitimate LinkedIn User Julia
Marketing Director, Unconventional Campaign Strategies and Implementations
Dallas/Fort Worth Area 10,000+ connections Contact info
How data is stolen and used against users
From a cybercriminal perspective, LinkedIn is an optimal platform to gather information on potential targets and for initial reconnaissance given its large user base and business orientation. As in many other social networks, sharing data is the principal activity done on the platform, and this opens people to threats targeting all kinds of users.
This section provides a brief rundown on some of the most common techniques cybercriminals and threat actors abuse to collect and steal users' personally identifiable information (PII) from LinkedIn and other websites such as social media and networking platforms.
Criminals can weaponize data in several ways. Having a thorough background knowledge of the target can easily lead to a sophisticated, tailored attack that will likely succeed.
LinkedIn end users are not the only targets of campaigns developed using data gathered on the platform; employers can also be victims.
How data is stolen
This section provides a brief rundown on some of the most common techniques cybercriminals and threat actors abuse to collect and steal users' personally identifiable information (PII) from LinkedIn and other websites such as social media and networking platforms. Three of the most popular methods include:
- A criminal can exploit all scraped data for ill-intended purposes. Having a large amount of information at their disposal can allow threat actors to craft sophisticated attacks. It is not easy for a user to defend against scraping, but being mindful of what you share to the public can reduce the risks of having personal details used against you.
- A data breach occurs when the platform gets compromised by criminals with the aim of stealing confidential data. This data is then sold or used to gain access to key profiles to continue with attacks.
- Phishing is the most common way to get access to account credentials. The victim is deceived or forced to click on a link, which will bring or redirect them to a fake login page of the service. LinkedIn, much like other social networks, can be a valuable target platform for abuse due to the ease in coming up with a fictitious story as a lure to gain victims’ legitimate account credentials, among other PII.
How data can be used against users
Criminals can weaponize data in several ways. Having a thorough background knowledge of the target can easily lead to a sophisticated, tailored attack that will likely succeed. For example, knowing that a user wants to change jobs, is unhappy with the current employer, or is looking for a particular job, could allow a fake recruiter profile to induce the user to send their curriculum vitae filled with personal information, open malicious files, or fill in some forms. Moreover, if the criminals have access to a LinkedIn profile, they can have access to privileged connections depending on the kind of professional targeted.
In general, the more information the criminals have, the more knowledge they can leverage against the target. In having valuable stolen accounts, these profiles can bring threat actors a step forward to gaining a victim’s trust.
How data can be used against the respective employers
LinkedIn end users are not the only targets of campaigns developed using data gathered on the platform; employers can also be victims. In most cases, the first step in an attack kill chain is reconnaissance and gaining as much information as possible. Details shared by employees can be accidental data disclosures on how the company operates. While posted and done without malicious intent, it is still a leak of information that can offer strategic advantages to criminals. Gaining extensive company information or access to compromised LinkedIn accounts can be abused to gain trust among other people in the target company. At this point, malicious actors can achieve almost anything by sending malicious files to the right employee, allowing them to spread malware, steal information, or — eventually — even hold the organization’s data for ransom.
How criminals monetize data
There are different kinds of markets that leverage LinkedIn, each of them targeting different cybercriminal needs. One can buy databases, new or aged accounts, or even LinkedIn Premium features, along with special requests for roles supporting cybercriminal routine needs such as LinkedIn Marketing Specialist. Moreover, a parallel market on how to increase connections fast, buy connections, or boost your profile exists in the underground.
Databases of LinkedIn data are often shared for free, though some forums require users to purchase credits to access download links.
As LinkedIn enforced stricter antifraud and account verification policies when registering a new profile, there is now a demand for new and aged compromised user accounts, or fake accounts created using fraudulent verification data, in the cybercriminal underground.
LinkedIn offers options for different premium plans to upgrade personal profiles and enable advanced features. A parallel market in the underground exists for upgraded plans, each aimed to access different kinds and ranks of professionals.
Several actors offered phishing LinkedIn users as a service ranging from $150 to 400, depending on the number of emails the user wanted to send, and for the period ranging between 10 to 31 days.
Databases of PII and credentials
Databases of LinkedIn data are often shared for free, though some forums require users to purchase credits to access download links. On average, these credits cost around US$10. In 2012, LinkedIn was breached, and the database from this intrusion is still offered for free in 2022. More specific databases, such as those divided by country or by year, can be found at a higher price of up to US$1,500.
Databases offered in the underground are often from breaches or scraping that occurred over the years. In April 2021, LinkedIn suffered a data leak that exposed personal information of over 700 million (92%) of its 756 million users.
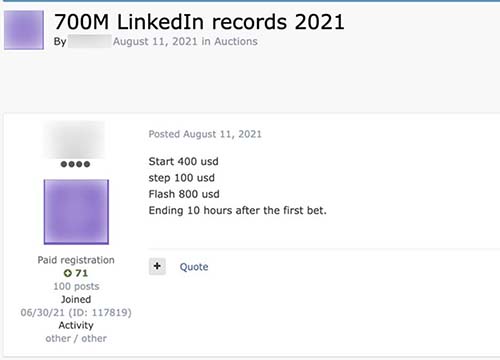
Figure 2. Auction advertisement for 700 million LinkedIn records
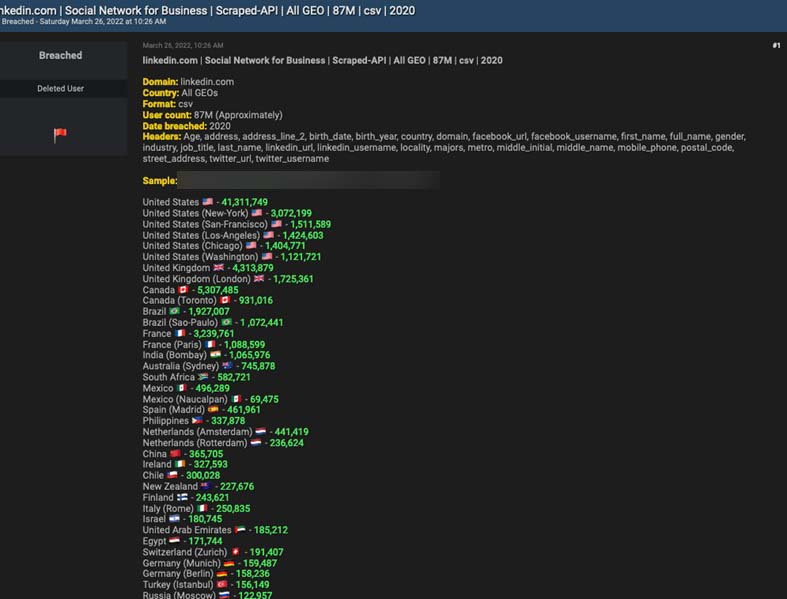
Figure 3. A database obtained by scraping the API, offered for “free.” Free users still need eight credits (equivalent to $10) to view the download link.
To summarize some offers we found in underground forums:
- February 2021: A threat actor advertised a database of over 500 million LinkedIn accounts for sale on the now defunct Raid Forums, filtered by country.
- July 2021: An actor offered a 2021 database of 530 million users for $1,500 on Exploit, a Russian-based forum.
- July 2021: A cybercriminal hacked into LinkedIn’s API of 700 million LinkedIn users in 2021 and listed it for $5,000.
- August 2021: A data broker auctioned off 700 million LinkedIn records starting at $400 on Exploit (Figure 1).
- November 2022: An actor was selling what was allegedly the full 2022 LinkedIn database for $1,500 in forum breached[.]to.
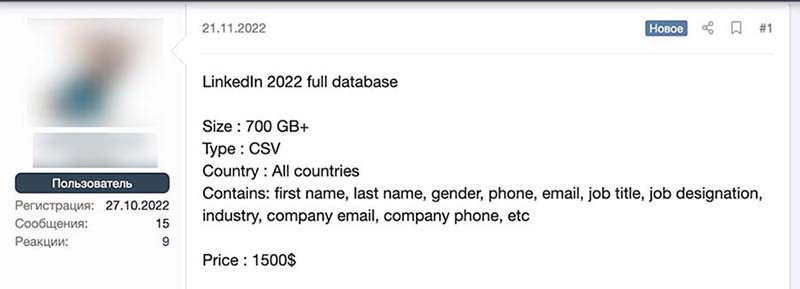
Figure 4. An advertisement for the complete 2022 LinkedIn user database
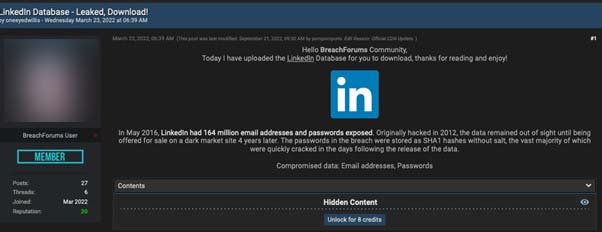
Figure 5. A database collected from the 2012 LinkedIn breach, offered for “free.” Free users still need eight credits to view the download link.
| Product | Prices |
|---|---|
| Leaked database | Free, while for some forums credits are needed. Credits average about $10. |
| Scraped databases | Ranging from $1,500 to $5,000 |
Table 1. Average prices of databases found in the underground
New and aged accounts
As LinkedIn enforced stricter antifraud and account verification policies when registering a new profile, there is now a demand for new and aged compromised user accounts, or fake accounts created using fraudulent verification data, in the cybercriminal underground. A new account is a recently created profile that can have some connections. These new accounts are also usually empty, with no (or limited) information but have all the verification data required to be considered real.
On the other hand, aged accounts are accounts that have been registered for months or are a few years old (the average aged account is around five years old). These aged accounts have connections, basic interactions, and a verified phone number. These profiles are considered more valuable because they are less likely to be banned. Aged accounts are from breached data, scraped, or accounts compromised through spear phishing, but can also be created and aged with the aim to sell later.
New and aged accounts can be sold individually for an average price of $15, or sold in bulk. We often see forum users posting a request for a specific country or job title. Accounts are also listed by gender, though this distinction does not appear to influence the price.
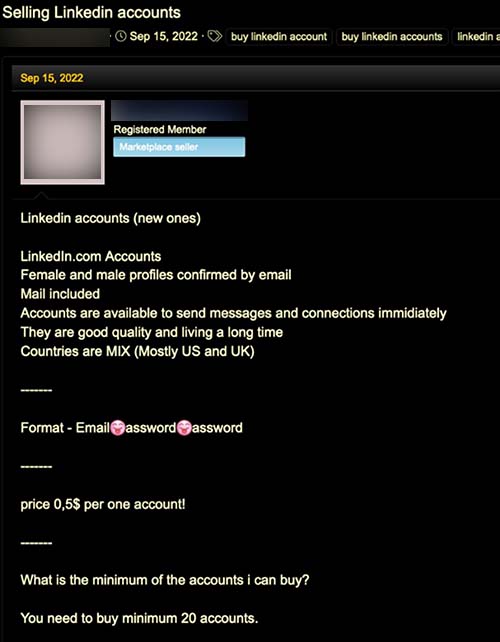
Figure 6. LinkedIn accounts sold by gender
Some forum posts include links to Storefront, a page dedicated to selling several social network accounts, including LinkedIn users’ accounts. The price ranges from $8 to $200, depending on the number of accounts needed.

Figure 7. New LinkedIn accounts sold on Storefront , a cybercriminal underground forum
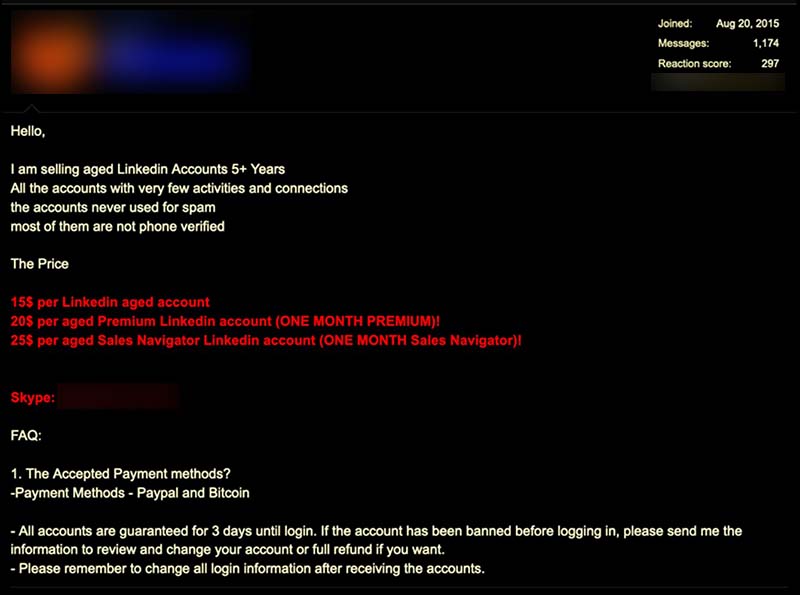
Figure 8. An advertisement for aged LinkedIn accounts
| Offering | Prices |
|---|---|
| New LinkedIn Accounts (the ones considered free) | From $5 |
| Aged Accounts | From $15 |
Table 2. Average prices of new and aged accounts in the underground
LinkedIn Premium accounts
LinkedIn offers options for different premium plans to upgrade personal profiles and enable advanced features. A parallel market in the underground exists for upgraded plans, each aimed to access different kinds and ranks of professionals.
These feature upgrades are offered for a ridiculously cheap price with respect to the real one. Malicious actors go for these upgrades because they allow users to send a vast number of messages, even to people outside the user’s network. InMail message is a premium feature, and it allows the user to directly message another LinkedIn member to whom a user profile is not connected. The profile is allotted a specific number of InMail message credits based on the subscription type, providing a large base for phishing attacks. Moreover, having a profile with these kinds of upgrades makes the account more flexible.
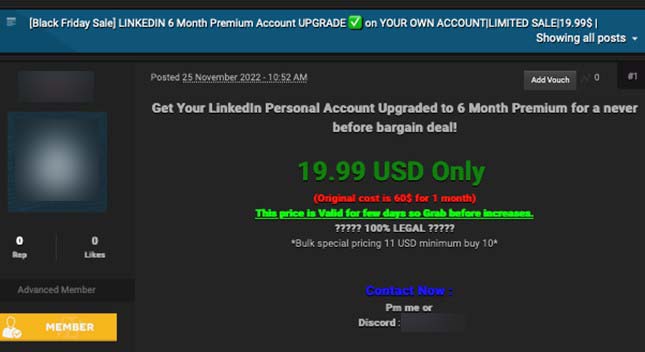
Figure 9. A Black Friday 2022 sale for a Personal Account upgrade
A Recruiter Lite account upgrade can be exploited in various ways. Since most of the conversations and exchanges a professional can have with a recruiter involve personal data, sending and receiving files, filling out online forms and so on, this can be a significant advantage for an attacker. Having a profile flagged as a recruiter can lead people to send their CVs without second-guessing the authenticity of the receiving account. On the other hand, it allows an attacker to search for precise requirements and details about the potential victim, opening users and organizations for a highly targeted attack. Users are more likely to follow a link or open a file sent to them through a recruiter’s account. We found a thread in an English-based forum where a malicious actor described how valuable it was to have a Recruiter account. The actor's inbox was flooded with resumes from people who blindly sent them just because it had a title of “Recruiter” on the profile.
Another advanced feature is the Sales Navigator, which allows users to conduct as many targeted audience searches as possible with all the available tools. Subscribers of the feature can narrow down search details by using filters, and will be informed of any changes in leadership, features, functions, or responsibilities. For illicit purposes, these features would also be good for a cybercriminal targeting a specific member of a company for deploying attacks with social engineering methods, such as fraud or ransomware. To offer these competitive prices, cybercriminal underground sellers use a discount code or stolen credit cards to offer lower prices than that of LinkedIn. Table 3 compares the prices advertised in the underground and the official prices.
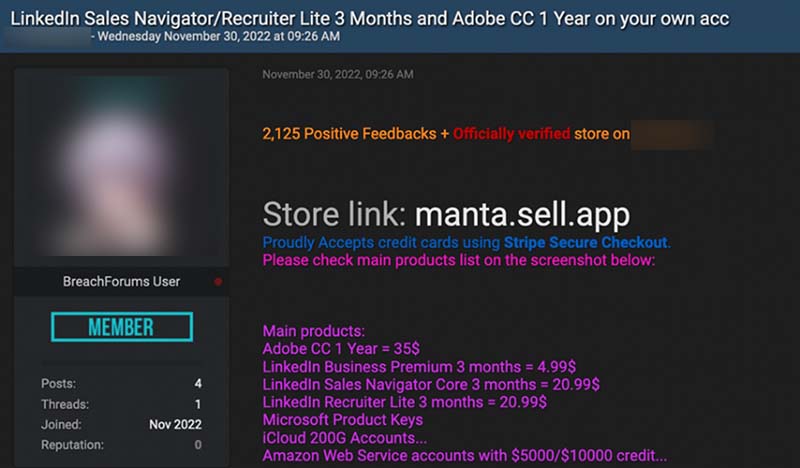
Figure 10. An advertisement for Sales Navigator and Recruiter LinkedIn upgrades
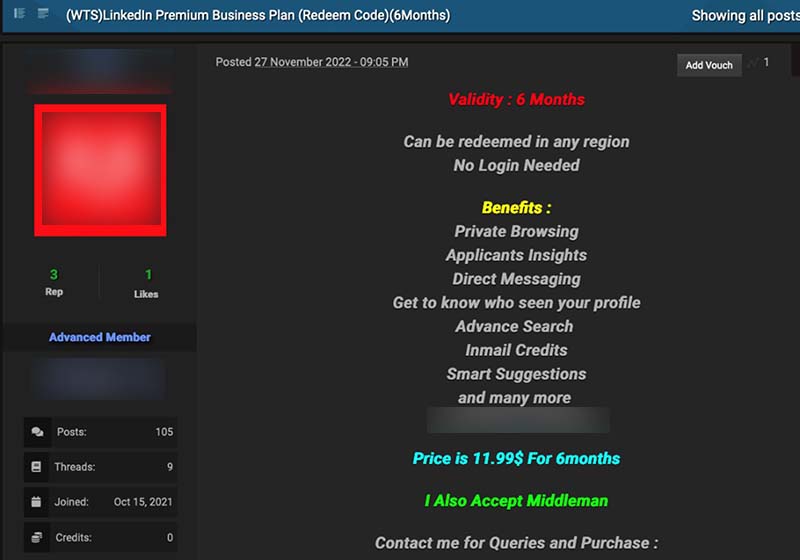
Figure 11. An advertisement for a LinkedIn Premium Business Plan upgrade that costs $11.99 for six months
| Product offer | Cybercriminal underground prices | Official prices on LinkedIn |
|---|---|---|
| New Premium accounts | $5 for three months | $39.99 per month, $99.99 per year when billed annually |
| Sales Navigator accounts | $20 for three months | Starts at $79.99 per user per month when billed annually |
| Aged Sales Navigator LinkedIn account | From $25 per month | |
| Recruiter Lite account | From $20 for three months | $139.99 per month when billed annually |
| Premium Business Plan account | From $11.99 and up | $44.99 per month when billed annually |
| Premium Career account | $39.99 USD per month |
Table 3. Average prices of LinkedIn Premium plans in the underground compared to official prices of LinkedIn Premium accounts.
How to monetize a considerable number of accounts
We found a post explaining in detail how to monetize many accounts by taking advantage of the accounts to create high engagement on posts and profiles of interest. The engagement rate is an important coefficient in social networks like LinkedIn or Instagram: the algorithm considers a profile more interesting (and more likely to promote it) if it has more interactions.
The method involves some fake accounts that, thanks to some scripts, will perform all the necessary actions to boost the target page. First, these fake users need to have a lot of connections so the threat actors can use automated tools to connect with as many profiles as they can. Then, the fake profile will spam their connections with messages to ask for likes, follows, and comments on specific pieces of content. These interactions make it possible to boost the page’s engagement rate. This service is sold in the underground for a subscription that costs around $100.
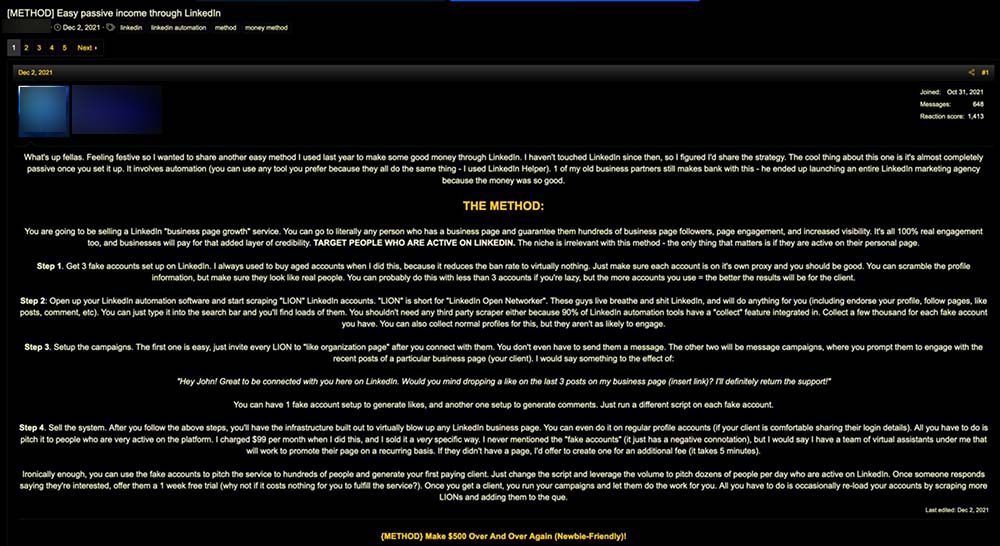
Figure 12. A post detailing a possible strategy on monetizing accounts through LinkedIn.
Cybercriminals take advantage of a group of LinkedIn users called LinkedIn Open Networkers (more popularly known as LION). These users connect with anyone regardless of their lack of familiarity or interest to the user, asking for the connection but are not necessarily malicious. In this manner, it is easy to rapidly increase the number of connections. We found an example of two of these accounts. LinkedIn does not consider LION accounts illegal; they are not new and have been around since 2011, and typically have “LION” or “L.I.O.N.” on their respective biographies. Underground forums often post links to LION accounts for others to use.
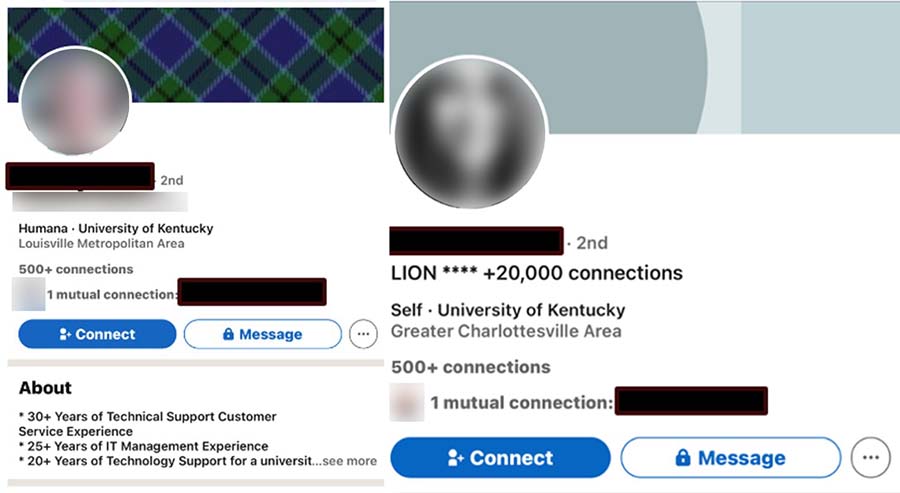
Figure 13. Legitimate LinkedIn accounts advertising LION connections
Additional LinkedIn services
In addition to LinkedIn accounts sold in the underground, we found other services that serve as tools for malicious activities that take advantage of the platform. Several actors offered phishing LinkedIn users as a service ranging from $150 to 400, depending on the number of emails the user wanted to send, and for the period ranging between 10 to 31 days.
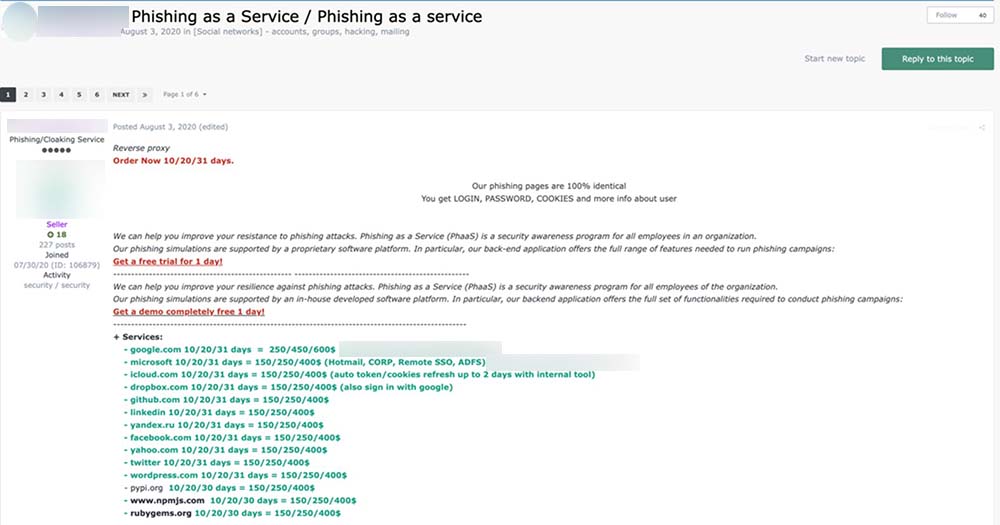
Figure 14. An advertisement posted on Exploit from a reputable underground seller for phishing on LinkedIn as a service, starting at $150 for 10 days.
We often see advertisements looking for LinkedIn experts, such as communications or marketers, to help in special projects. According to these ads, projects include filling out profiles, advertising on sites, and creating traffic to phishing sites. Pricing is not discussed in the advertisement and is negotiated via private messages.
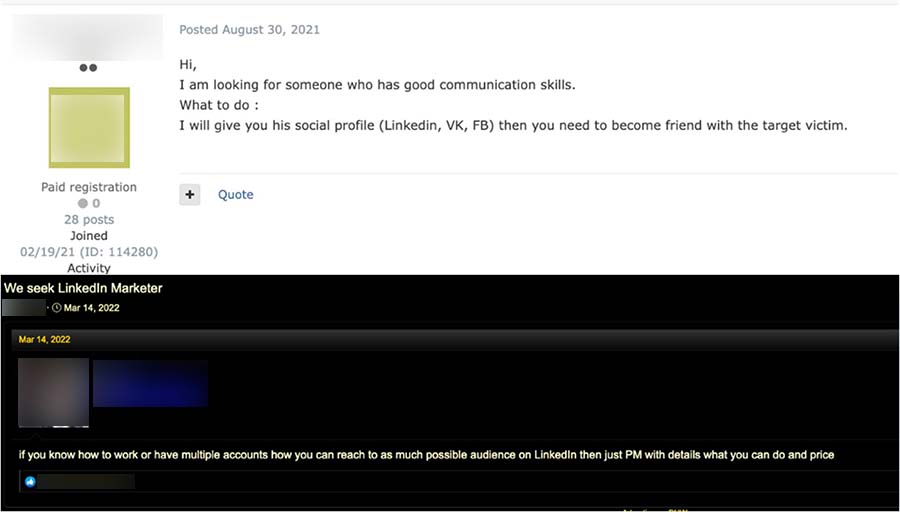
Figure 15. An advertisement looking for a LinkedIn Communications Specialist (top) and LinkedIn Marketer (bottom)
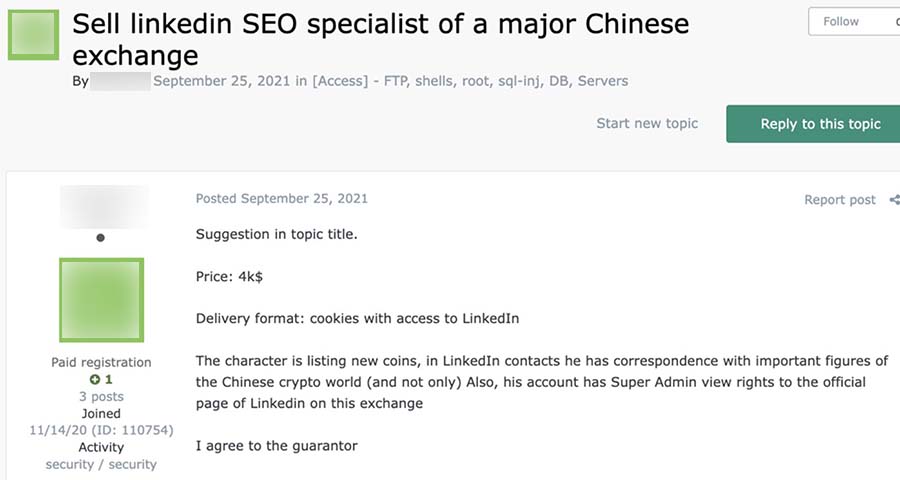
Figure 16. An advertisement selling the LinkedIn account of an SEO Specialist with connections to a Chinese cryptocurrency exchange
Conclusion and recommendations

Figure 17. Defense scenario against a LinkedIn compromise attempt
As Steven continued with his phishing activities targeting high-level executives, he found a new victim: a successful businesswoman named Alice. He spent weeks studying her online profile and posts, and what he found made him think he had the biggest target he’s ever had. Steven thought this single scam would be enough to set up his family for the rest of their lives, and promised his wife this would be his last attack.
However, Alice is an acute tech user who had security software installed on her device.
In his home office, Steven crafted the message with the phishing URL and sent it to Alice. He was happy and satisfied, having spent weeks researching for vulnerabilities in Alice and her company, and deployed the attack that he thought was the most sophisticated he’s crafted yet. Sure of his success, Steven turned off his computer and went to pick up his kids from school.
Unbeknownst to Steven, Alice’s security solution immediately blocked his message and flagged the link as a phishing email, effectively killing the attack.
For both companies and users, LinkedIn is a great platform for creating, raising awareness, and maintaining a professional brand. It sets itself apart from other social media platforms by promoting a professional and business-oriented atmosphere to network, share and highlight users’ works and organizations’ achievements, and — allegedly — open wider previously gatekept opportunities for those open to exploring career possibilities.
But like other social networking platforms, LinkedIn is not exempt from security concerns that target and compound all entry vectors: the platform, the companies, and the users. The flood of data and information is changing the deemed currencies for exchange and value, and LinkedIn is uniquely poised at the center as it accommodates and mixes personal and business purposes. The platform now has more posts and content related to the intersections of personal and professional lives, experience, and goals. However, the platform’s perceived professional-oriented angle also gives a false sense of security, making it easier for attackers to build a well-tailored attack and target the right victim.
LinkedIn has implemented some countermeasures. They have a blog that updates users on the latest events concerning the platform and explains common social network-related attacks. The ban ratio of fake or scam profiles is rising as both LinkedIn and cybercriminals recognize that more people trust the platform over other social network sites for its professional-oriented content and environment.
The majority of the threats and best security practices that can be applied on LinkedIn is similar to those of other social media platforms and online accounts.
What users can do to protect themselves:
- Avoid posting sensitive data or PII, such as emails, phone numbers, or addresses, on the user profile’s Summary section.
- Customize the visibility of drafts before sharing posts. Choose and identify specific posts that can be seen by followers, connections, and non-connections.
- Users should be aware of their respective company social media policies and the accompanying consequences of violating them. These also often include the legal compliance guidelines and security directives covered by the restrictions, as well as the privacy and incident management plans in effect.
- Users are advised to only share information they are comfortable with being posted publicly on the internet.
- Customize user profiles and privacy settings to limit the amount of information available to the public.
What organizations and users can do to mitigate the risks:
- Establish and implement clear social media policies to identify which corporate information and/or data are allowed for public posting. These can likely vary depending on the roles as employees handle information with differing hierarchical sensitivity and confidentiality. Higher roles likely require more restrictive guidelines due to information access, and the policies to be implemented have to clearly identify the employees, limits, data classifications, and legal requirements covered.
- Encourage account, profile, compliance, verification, and incident management scenarios with employees. Establish a point person for employees to approach when they find fake accounts impersonating legitimate personnel or company roles.
- Develop protocols on social media use during work hours or while using company-distributed assets such as laptops and mobile devices.
- Deploy multifactor authentication (MFA) on all business and personal accounts.
- Use password management software to store account passwords, and practice proper password hygiene by not using the same password on multiple websites and accounts.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks