Influential Facebook Brand Pages Stolen via Credential Phishing
By Alice Wu
 We observed an increase in the number of compromised Facebook pages of influential personalities since June. Through an analysis of the surge, we found fake Facebook accounts posting notification messages on pages allegedly hacked with an attached link. The fake accounts also steal the owner or admins’ credentials to sell the page, change the details and name, and/or disguise the page to make another phishing account. Observably, targeted pages appear to be based on the number of followers, and our latest observation shows that an average of three accounts are compromised per day. Our analysis showed these cybercriminals are targeting accounts and pages of personalities from Taiwan, India, Australia, Canada, and the Philippines. We have reported this to Facebook and they have stated that they have taken steps to secure the flagged accounts.
We observed an increase in the number of compromised Facebook pages of influential personalities since June. Through an analysis of the surge, we found fake Facebook accounts posting notification messages on pages allegedly hacked with an attached link. The fake accounts also steal the owner or admins’ credentials to sell the page, change the details and name, and/or disguise the page to make another phishing account. Observably, targeted pages appear to be based on the number of followers, and our latest observation shows that an average of three accounts are compromised per day. Our analysis showed these cybercriminals are targeting accounts and pages of personalities from Taiwan, India, Australia, Canada, and the Philippines. We have reported this to Facebook and they have stated that they have taken steps to secure the flagged accounts.
Stealing accounts, phishing for more
We found an estimated range of 120 to 180 fake Facebook accounts using the same names and official-looking profile photos. However, the names contained non-ASCII characters that translate as Roman letters online such as ə, ı, and ɾ:
- Prıvacy PoIicy
- Fecebook and PrIvacy
- Fəcebook System Corporation
- Fəcebook Term Of Services Register Center Team
- Fəcebook Sociəl Reconfirm Center Invitation
- Fəcebook Servıce Corporation 01
- Reconfirm Your Accounts
- Re-confiɾm Facəbook
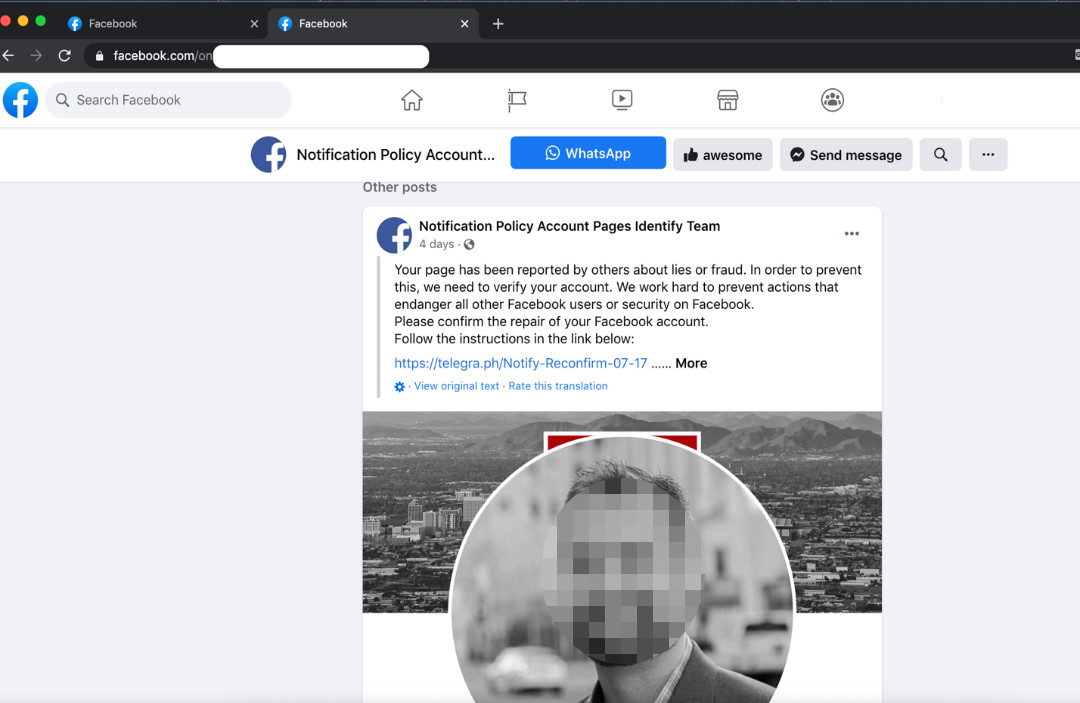 Figure 1. A notification to a user on a fake Facebook page
Figure 1. A notification to a user on a fake Facebook page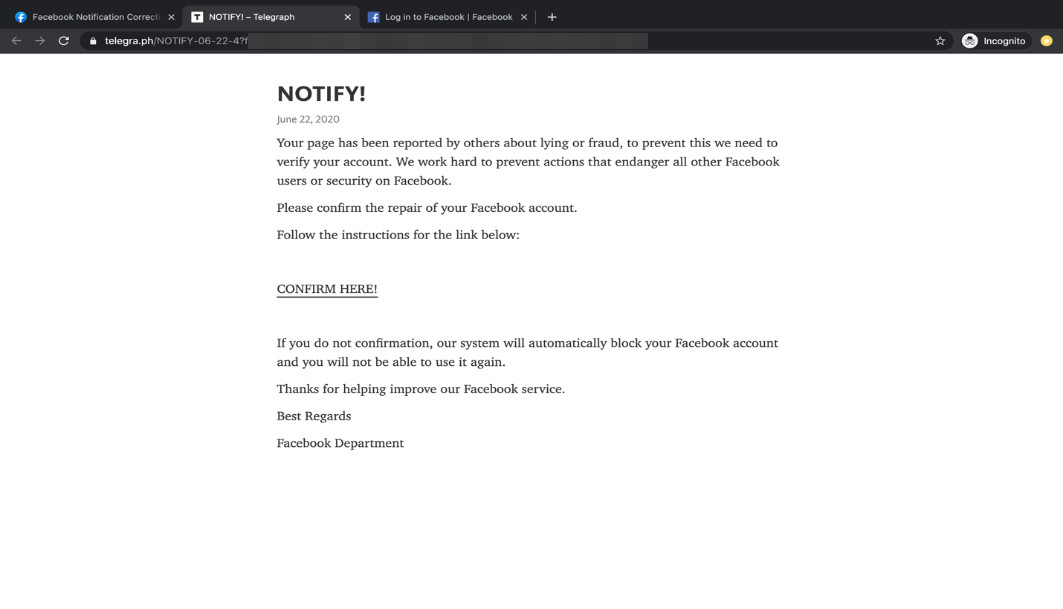
Figure 2. Instructions to “verify” a user account via an external link
Selecting the confirmation button redirects the user to a fake Facebook notice and to the phishing login page. Among the most evident red flags are the grammatical errors that consistently appear in all of the fake pages.
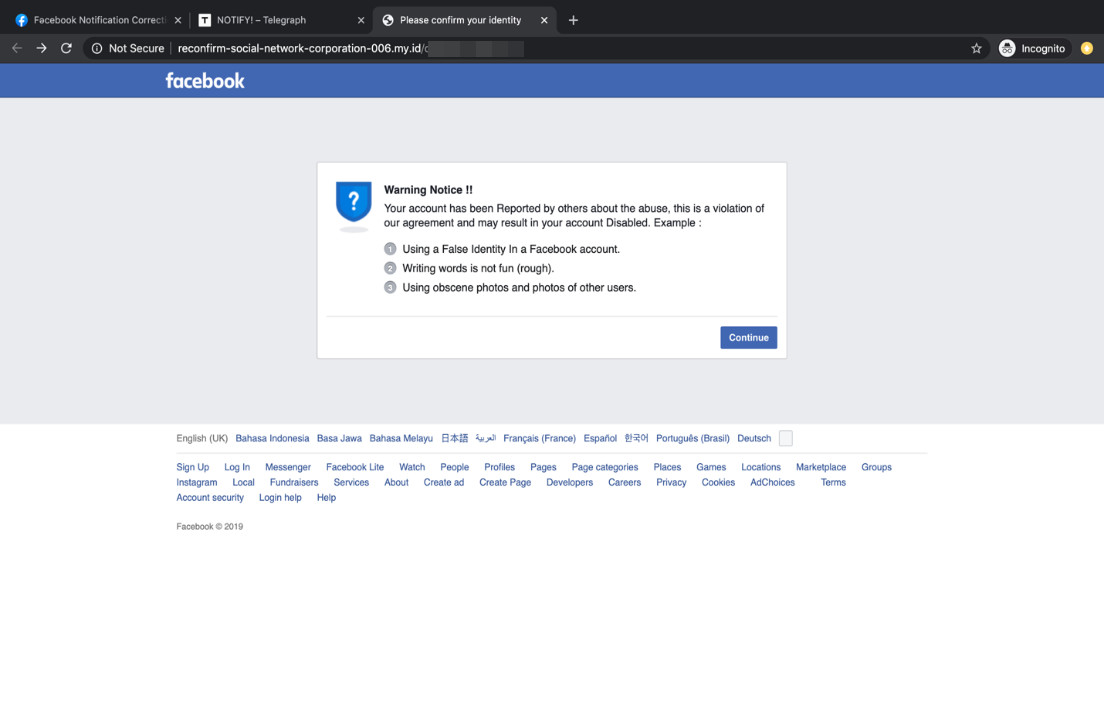
Figure 3. A fake Facebook warning
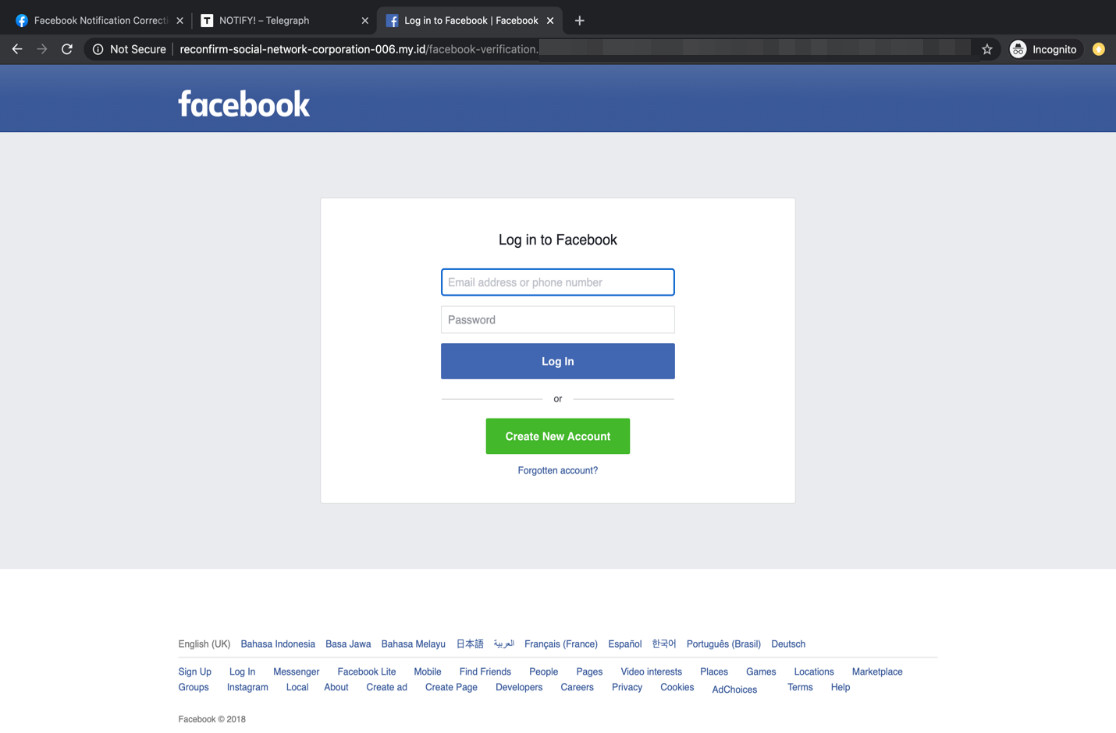
Figure 4. A phishing login page
Once the victim logs in with their username and password, the cybercriminal takes over the account and uses it as another Facebook “official” account. Aside from changing the profile picture and account name to make the account look more credible, cybercriminals also configure the vanity URL to the same name.
Following Facebook’s policy, usernames need to be unique even if account names are identical. As such, for the cybercriminals to make sure that the username and account name are exactly the same, they rearrange the words of the compromised accounts with similar keywords. However, it is possible that these cybercriminals face a growing problem: Since the number of compromised accounts are growing, there are, in effect, less username options to rearrange words with and to choose from. We also observed some compromised accounts using the format “account name-unique ID” as their username, where the unique ID is assigned by Facebook when the account is created. By following this format, the same account name can be reused in other compromised accounts.
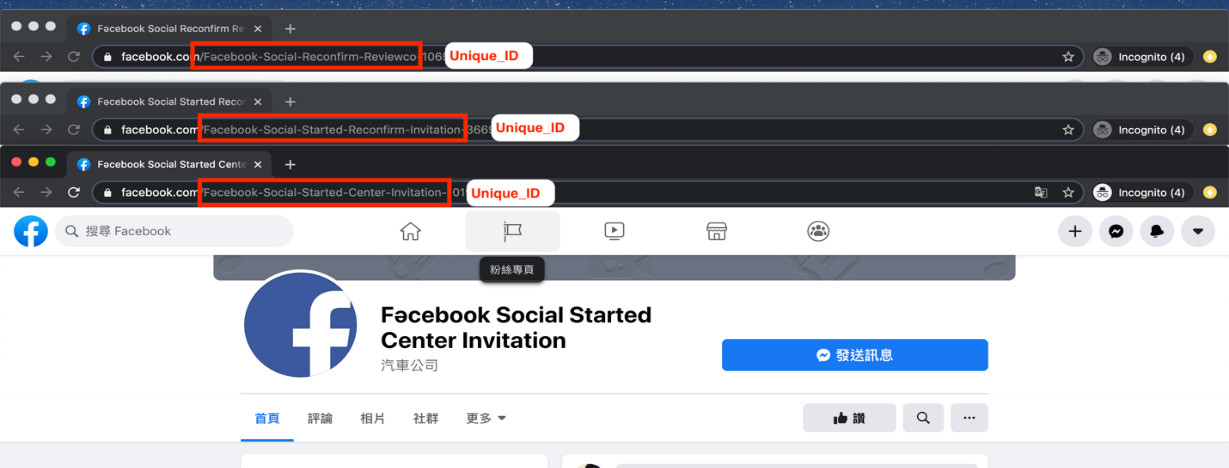
Figure 5. Same account names with different IDs
Legitimate owners discover that their accounts have been compromised within a day or two after seeing fake posts made by the hackers starting to spread. The owners can change their passwords to stop the continued unauthorized access to their accounts, remove the fake content, and change their profile pictures. However, the owners of accounts whose names have been changed find it difficult to revert to their original names because this process requires a manual review from Facebook and follows a specific set of criteria. The process takes quite a while, prompting more victims to simply create a new Facebook account instead of waiting for the review results.
As we continued monitoring this activity, we found it to be a growing concern considering that the pages and the fake content are regularly visited and viewed by their respective followers. Furthermore, a growing number of prominent personalities have been affected, as reported online in other countries. According to some of these reports, some celebrities have been targeted, failed to retrieve their respective accounts, or even worse, the cybercriminals appear to have sold the said pages.
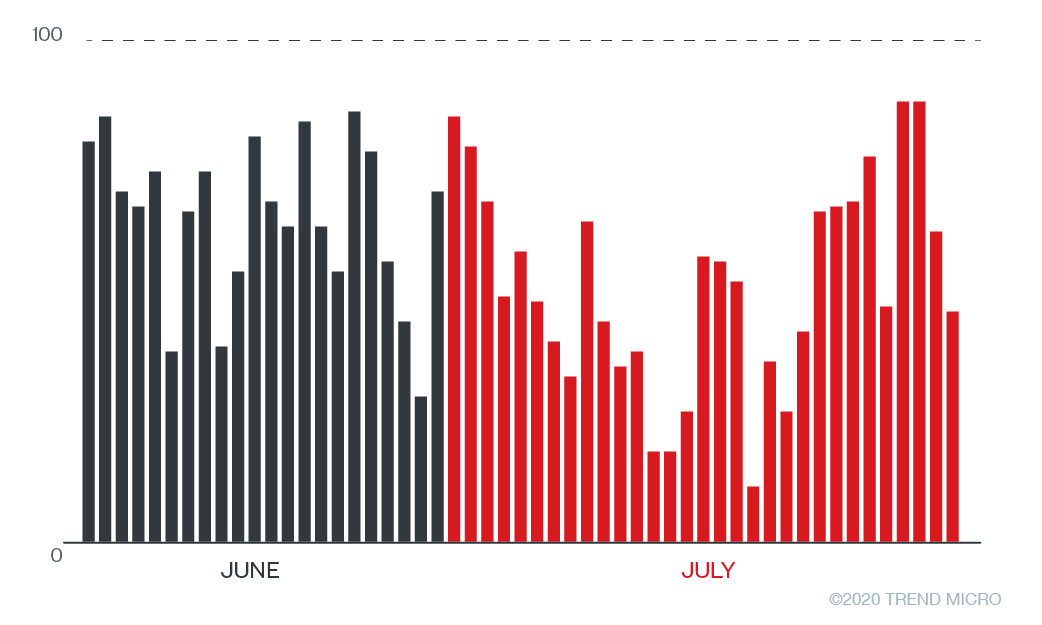
Figure 6. Accounts accessing the fake notification pages per day since June
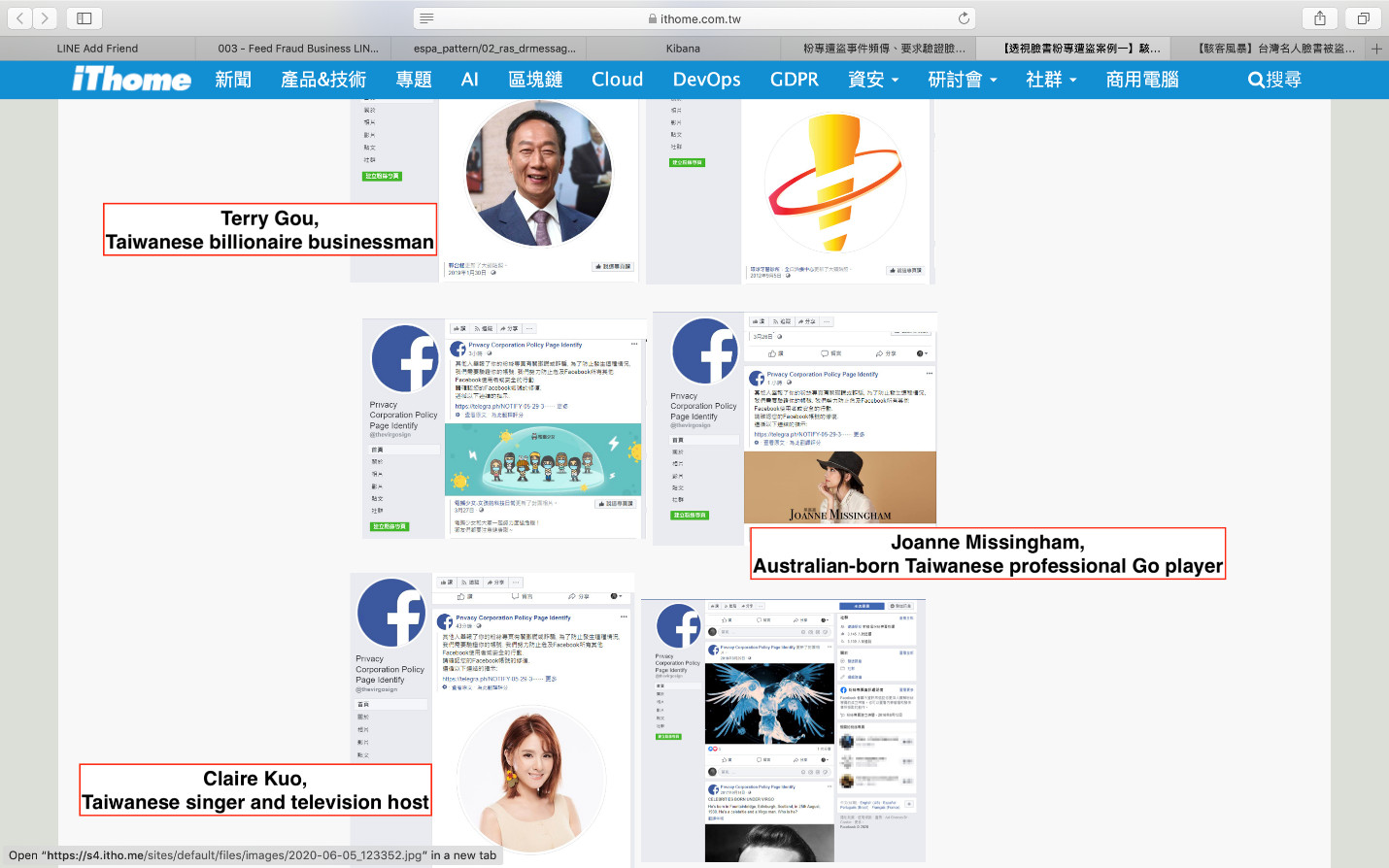
Figure 7. A screenshot from iThome News of popular figures whose Facebook pages have been targeted
Looking at the external links used for the phishing login pages, we used the search feature of the platform with the keywords telegra.ph/notify-07-22. telegra.ph/notify-. This is the phishing domain commonly used in the posts, while the rest of the URL indicate the date when the warning was posted. By choosing one of the posts from the search results, the post will show who posted the said notification.
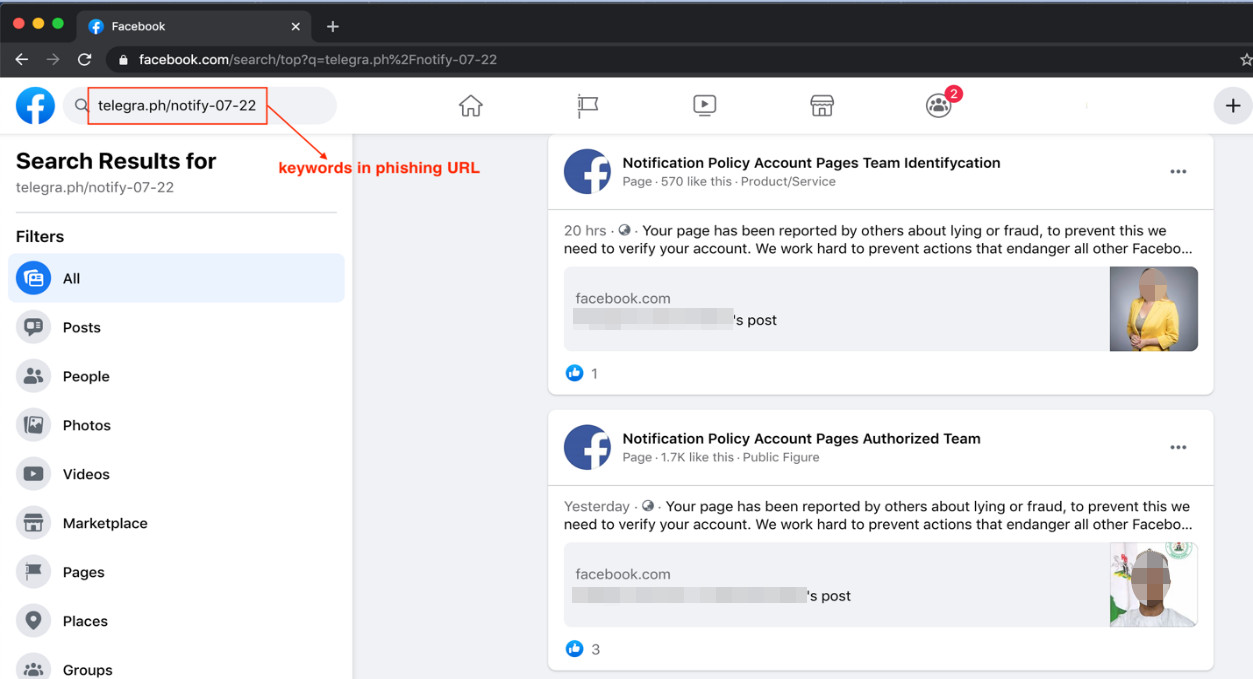
Figure 8. Search results showing compromised accounts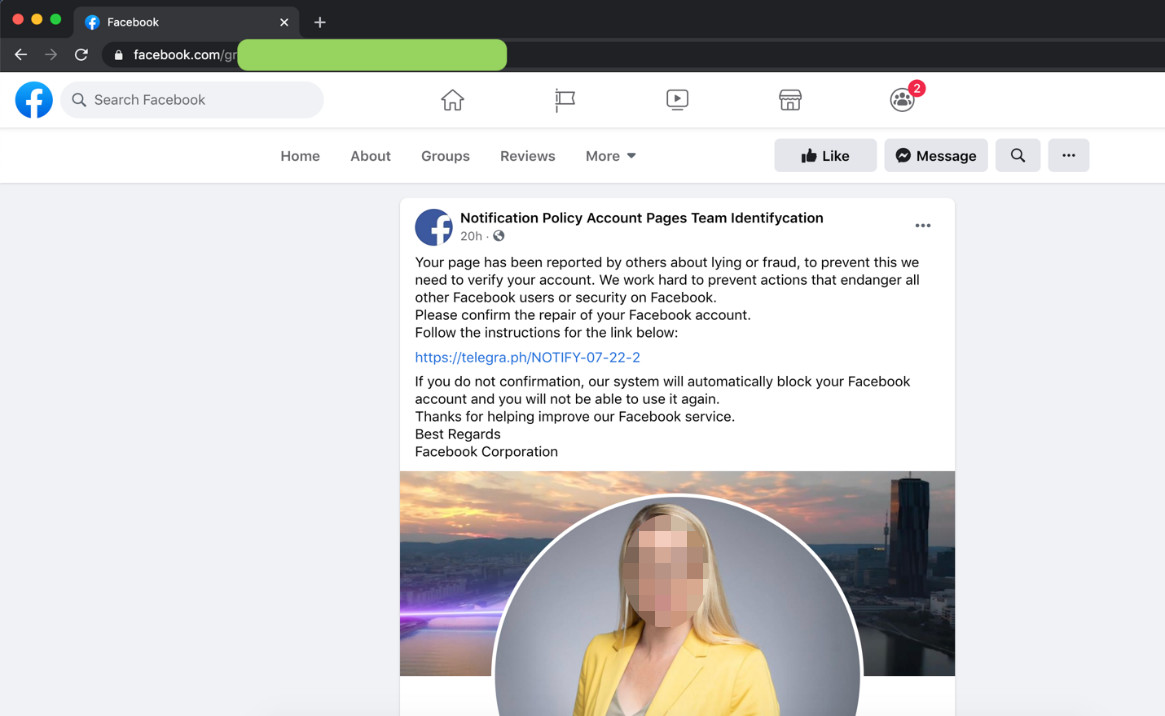
Figure 9. Fake post showing the user details
[Read: The rising tide of credential phishing]
Finding the suspicious accounts
For commercial, community, personality, brand, and product/service pages, there are four details that user and/or account owners can pay attention to in order to determine if the account is suspicious:
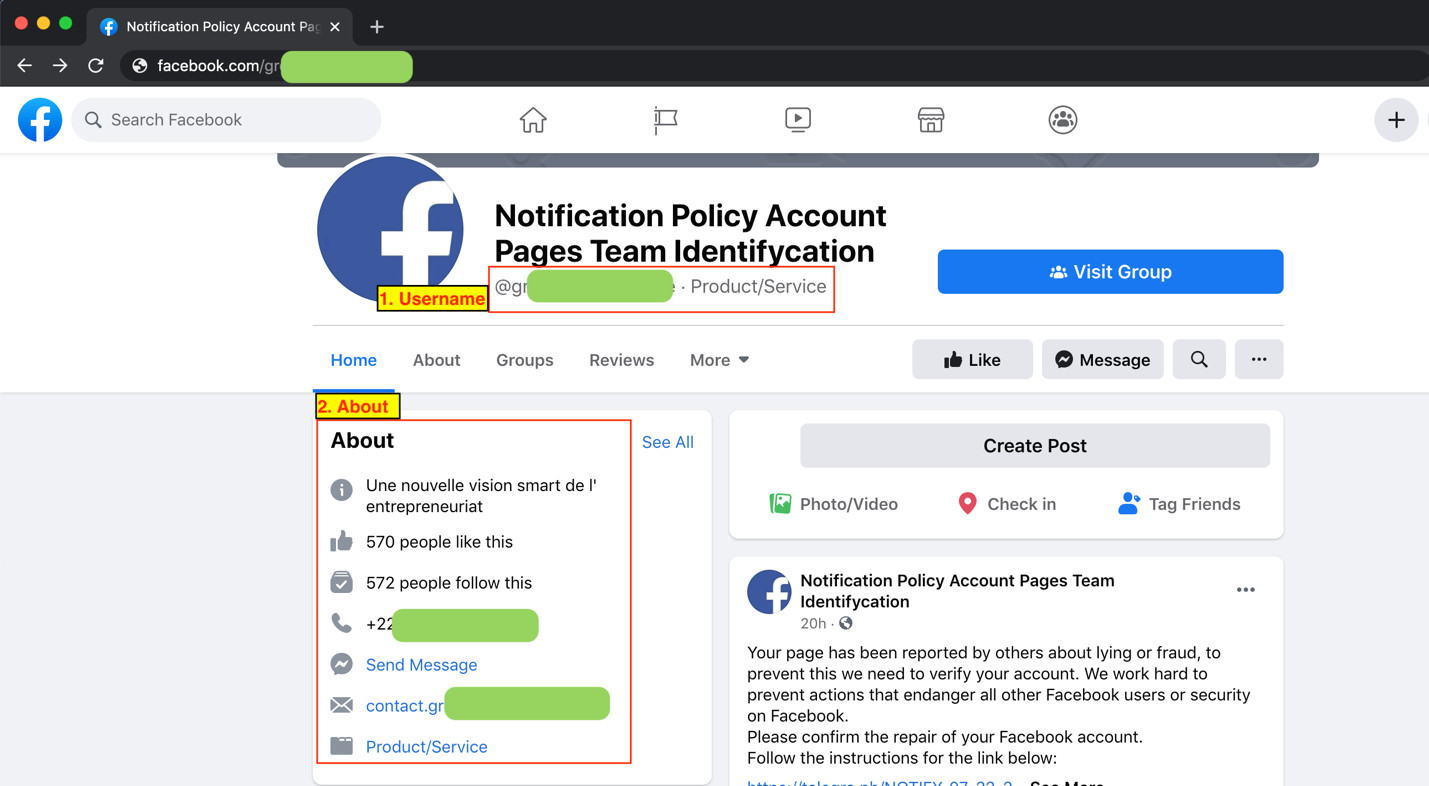
- Username: Legitimate usernames are almost the same as the account names. Fake accounts may have usernames and account names that have little to no relation to each other.
- About: This section might offer basic information on the owner of the account. A compromised account, however, might have dubious entries that can be easily compared to publicly available information online.
- Page transparency: This section shows the edits made in the page history, such as the date when the page was created and the original name registered.
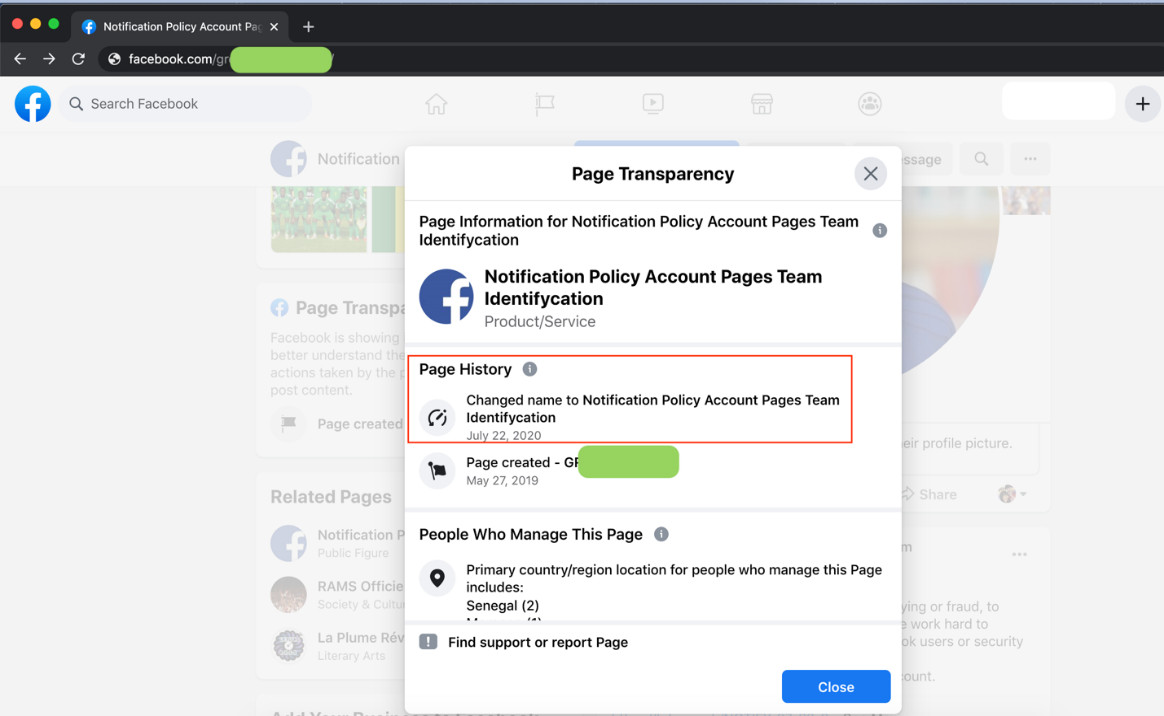
Figure 11. A sample page history via the Page Transparency feature
- Account photos: The photos found in the account can also reflect activity history. Compromised accounts will usually only have one Facebook icon photo uploaded in order for the hackers to change the profile picture.
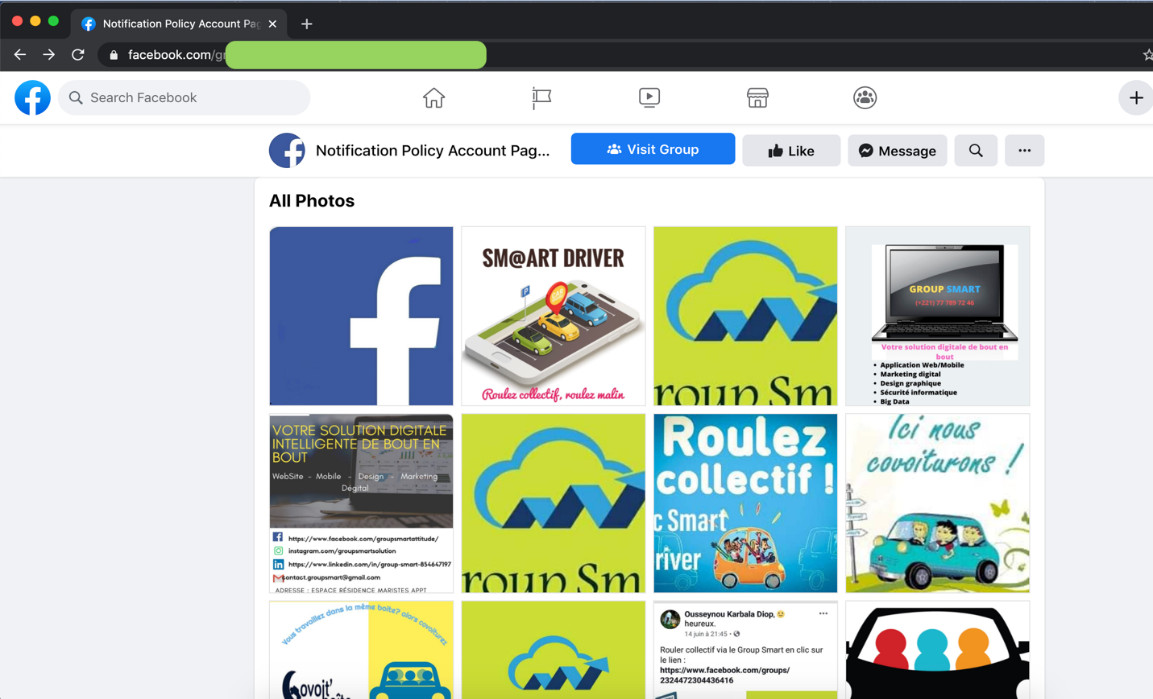
Figure 12. An account’s profile and album photos
Moreover, legitimate Facebook pages have a verification badge beside their respective names to signify the account as legitimately belonging to Facebook.

Figure 13. Legitimate Facebook pages that have a verification badge
Conclusion and security recommendations
Active Facebook users and their respective administrators will immediately notice the differences in their respective accounts once these are compromised, such as the name change and the fake content posted on their timelines. Hence, the malicious actors behind these activities would have to act fast in changing the account names and posting content before they can be discovered within a day.
Moreover, given the current situation wherein people are physically distant from each other, users and commercial brands are likely to be more reliant on social media platforms to maintain connection. It is understandable that affected victims are initially overcome with panic upon receiving a Facebook notification before they can check for red flags in the said warnings. Aside from possibly going through personal information, the hackers behind these attacks can also go through the users’ personal messages for sensitive information. For brands who subscribe to the platform’s advertisements, the use of their credit card information, potential for misinformation, and easy access to the brand’s data and followers can be detrimental to the business.
To add, given these social engineering techniques, the cybercriminals behind these threats can easily apply the same routines to other social media platforms. New accounts are compromised daily; as a result, it can become more challenging to track where these come from and who their specific targets are. Changing the names of influential pages’ accounts immediately enables the cybercriminals access to a significant number of followers, which means a large audience to spread content for. The follower counts alone could be used for a number of malicious purposes such as the dissemination of fake news. We continue to follow these incidents to ensure that these are not used as threat vectors for other possible routines.
For Facebook users who suspect their accounts have been compromised, they can visit this link to get a step-by-step process and resources on how to fix it.
Users can keep these best practices and reminders in mind to protect themselves from these threats:
- If your page is reported, platform reviewers will review the post/content/page for any violation of the Community Standards. Should they decide to reach out to the person, this is done confidentially via private means and hence the interaction is not posted on the timeline.
- Social media platforms respond faster to commercial pages’ inquiries and requests due to the potential sensitive financial information on these pages. Should your business page be affected by these threats, report and request for feedback from the platform immediately.
- Platforms will not use external domain links for internal processes and notifications. Once an external link is included in the message or post, report the page immediately.
- Enable two-factor authentication (2FA) in your social media accounts whenever it is available.
- Install and enable a multilayered protection system capable of detecting and blocking malicious websites.
Trend Micro solutions
Trend Micro™ Web Security™ Advanced, powered by XGen™, provides you with forward-looking threat protection on web threats, URL filtering, and application control, plus enterprise-grade features. Trend Micro endpoint solutions such as the Smart Protection Suites and Trend Micro™ Worry-Free™ Business Security detect and block the malware and the malicious domains they connect to.
Indicators of Compromise (IoCs)
- *hxxps[:]//www.facebook.com/awetaiwan/
- *hxxps[:]//www.facebook.com/WK.Carbon.Exhaust/
- hxxps[:]//telegra.ph/notify-07-22
* Compromised accounts abandoned by their owners due to failure to revert their account names.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks