Mobile Ad Fraud Schemes: How They Work, and How to Defend Against Them

Mobile devices have strongly competed against media staples like television and desktop computers as a platform for delivering information to consumers. More people go straight to mobile devices to consume online content compared to other platforms, and enterprises are quick to adapt to this user behavior trend. It's causing a shift across different industries; online advertising is projected to lean more towards the mobile market, taking a considerable chunk of the market share from other media every year. Unfortunately, threat actors also readily adapt to these shifting trends. These realities all intersect in mobile ad fraud.
Mobile ad fraud works by exploiting the system used to deliver or measure the effectivity of ads. Since most ads usually have a payment scheme tied to these systems, tricking it allows the threat actors to effectively steal from advertising funds of enterprises.
What are common mobile ad frauds?
The expanding capabilities of mobile devices allow advertisers to deploy their ads in different formats. This provides fraudsters with a number of ways to trick potential victims, from fake installs to attribution manipulation, among others.
Here's a list of the most common ad fraud methods in today's mobile landscape:
Ad Stacking
In ad stacking, fraudsters “stack” multiple ads so that users only see the ad at the top of the stack. However, the fraudsters will still get credit for each ad under the top one—unfairly billing the advertisers.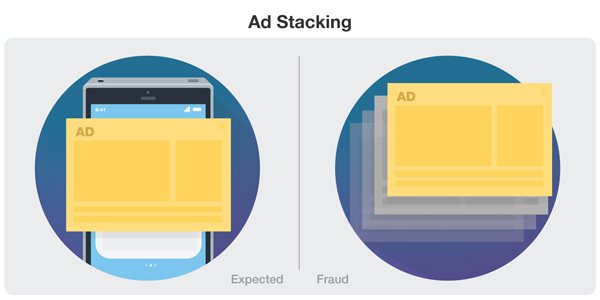
Click Fraud
The main goal of click fraud is to mimic real user behavior, to trick the system into counting their fake clicks as legitimate. Click injection is a type of click fraud where fraudsters use their own downloadable app to monitor a device for installs. Once an install is detected it generates clicks with this app, before it is actually even opened by the user.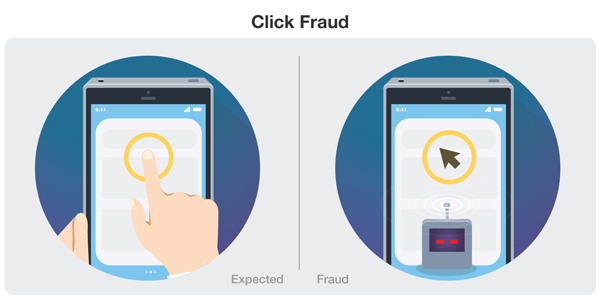
Click Flooding
In this method, fraudsters try to catch the last click or engagement prior to an actual install of the advertised product. They do this by sending a large number of fraudulent clicks, which increases the chances of having one of their clicks getting credit for the download. Each click also uses a unique ID that is aimed to match that of a real user who actually downloaded the advertised app.
Methods like this are not as invasive on mobile devices, which makes them effective for both Android and iOS devices. In fact, click flood rate was higher for iOS than for Android devices in the first quarter of 2018.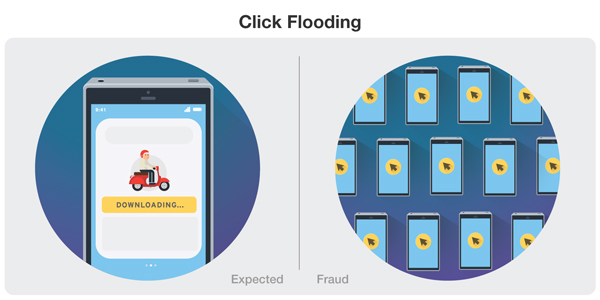
Device ID Reset Fraud
This fraud involves a cycle of downloads and resets, with each cycle counting as an install of an advertised app. The cycle begins with a fraudster clicking on an ad, downloading the corresponding app, generating the needed engagement then resetting the device ID. The fraudster then uninstalls and then reinstalls the app. According to AppsFlyer, device ID reset fraud accounts for 26% of mobile install fraud in 2018, amounting to losses of up to US$1 billion.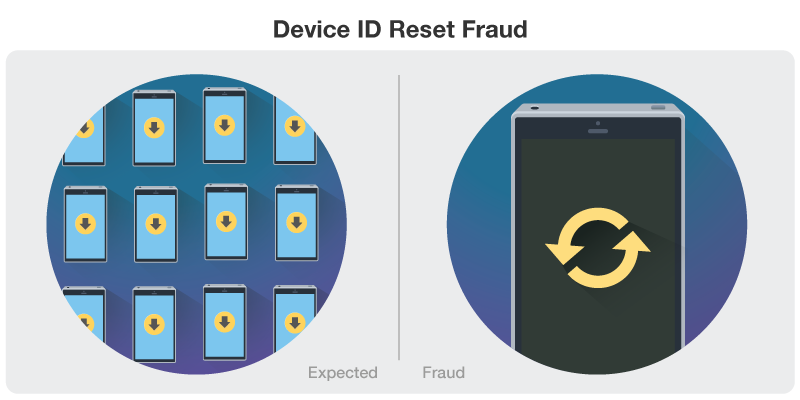
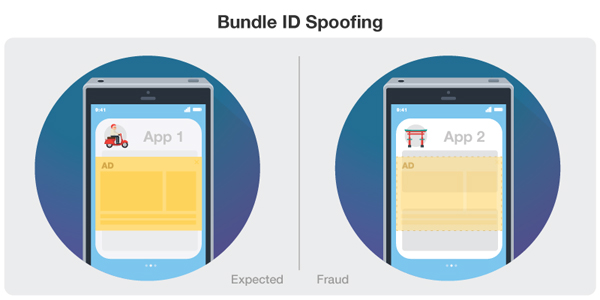
Bundle ID Spoofing
In this method, fraudsters trick advertisers into believing that their ads are being run in one app, when it's actually being run on another app. They do this by changing the parameters of the second app and giving it fake or illegitimate identifiers, thus the name bundle ID. Pixelate first uncovered this method in June 2018 after finding that these ads could appear on a black screen or in a background process, making them invisible to a user.
SDK Spoofing
SDK spoofing is a bot-driven strategy, that also uses a downloadable albeit malicious app. Malware laced into an otherwise legitimate app will generate clicks, and other engagements for a different app, without the latter having been installed in the first place. This method is considered one of the hardest schemes to detect. Any app that uses SDK (software development kit) is susceptible to it.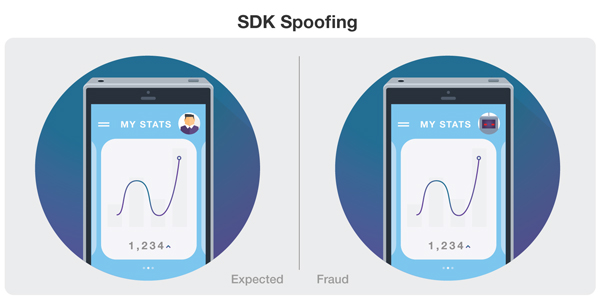
Impact of mobile ad fraud
Many mobile ad fraud techniques are familiar because they have already banked on the capabilities of traditional computers. On one hand, it can be seen as a testament to the mobile platform's evolution, with devices that possess the power and capabilities of desktop computers from previous generations. On the other, it also highlights how cyber fraud has evolved along with it.
Mobile ad fraud was particularly active in 2018. One of the major fraud cases involved an ad scheme that cost Google and its partners around US$10 million in losses, while the fraudsters earned up to US$75 million per year in fake ad revenue. It is possible to assume that the total damage from ad fraud could have reached billions. Trend Micro MARS had also reported 1,088 apps that contained SDKs for fraud. The ones that were identified on Google Play had already been taken down, but they've already done significant damage — these apps were found to have been installed 120,293,130 times.
Monetary loss is only a part of the numbers enterprises need to look out for. A side- (but still significant) effect of any ad fraud for enterprises, is how it corrupts data. The digital data gathered from ads is what advertisers and all those related to the field use to make strategic decisions. As mobile ad fraud techniques become more sophisticated, it will become more difficult to determine legitimate traffic from fraud.
Defending against mobile ad fraud
Taking measures against ad fraud should be a priority for enterprises, especially since some attacks also infringe on user privacy.
Users can also do their part to help prevent the rampant perpetuation of apps used by fraudsters. Here are some ways to do so:
- Be aware of mobile ad fraud schemes. Knowing and understanding the different techniques mobile ad fraudsters use can help users avoid them.
- Practice caution in choosing and installing apps on your device. Fraudsters commonly use malicious applications for their schemes. Sticking to apps from verified, legitimate sources can prevent fraudsters from using your device for ad fraud.
- Install mobile security solutions. Users should consider installing a multilayer mobile security solution that can protect the device against adware, potentially unwanted applications (PUAs), and other online threats.
- Report incidents that could be related to fraud. Improving the general awareness of all stakeholders affected by mobile ad fraud can mitigate and prevent future cases. Users can contact websites and apps used in mobile ad fraud directly to alert them of possible fraud.
Enterprises take the brunt of the losses caused by ad fraud. It would be in their best interest to defend against these schemes. Here are some ways to do so:
- Prioritize security from the planning phase. With the growing impact of mobile ad fraud, defense and security measures against it should be one of the primary considerations during the planning phase of any digital ad.
- Choose the right platforms and third-party vendors. Enterprises should be careful in choosing third-party vendors and platforms for ad publishing and distribution.
- Be more attuned to data patterns. The large amount of data advertisers and enterprises have access to can be used along with technologies like machine learning to distinguish patterns and identify fraudulent activity.
Ultimately,when it comes to any kind of fraud, it is important for all stakeholders to work together to maintain a safer digital environment. Sharing information and working towards a solution against new forms of ad fraud is crucial in the fight against it.
The overall effect of any kind of cyber fraud is that it decreases digital trust, from enterprises down to the users. Taking measures therefore to defend against mobile ad fraud can maintain trust in the larger digital community.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks