By Trend Micro Research
Despite the decreasing number of detected incidents since 2019, ransomware attacks continue to be one of the biggest menaces in the threat landscape.
From 491,600 incidents reported in 2019, the number of ransomware attacks decreased every year until 2022, as seen in Figure 1. But due to the uncompromising and all-or-nothing nature of their assaults on enterprises to force them pay a large ransom, they continue to be one of the most impactful threats today.
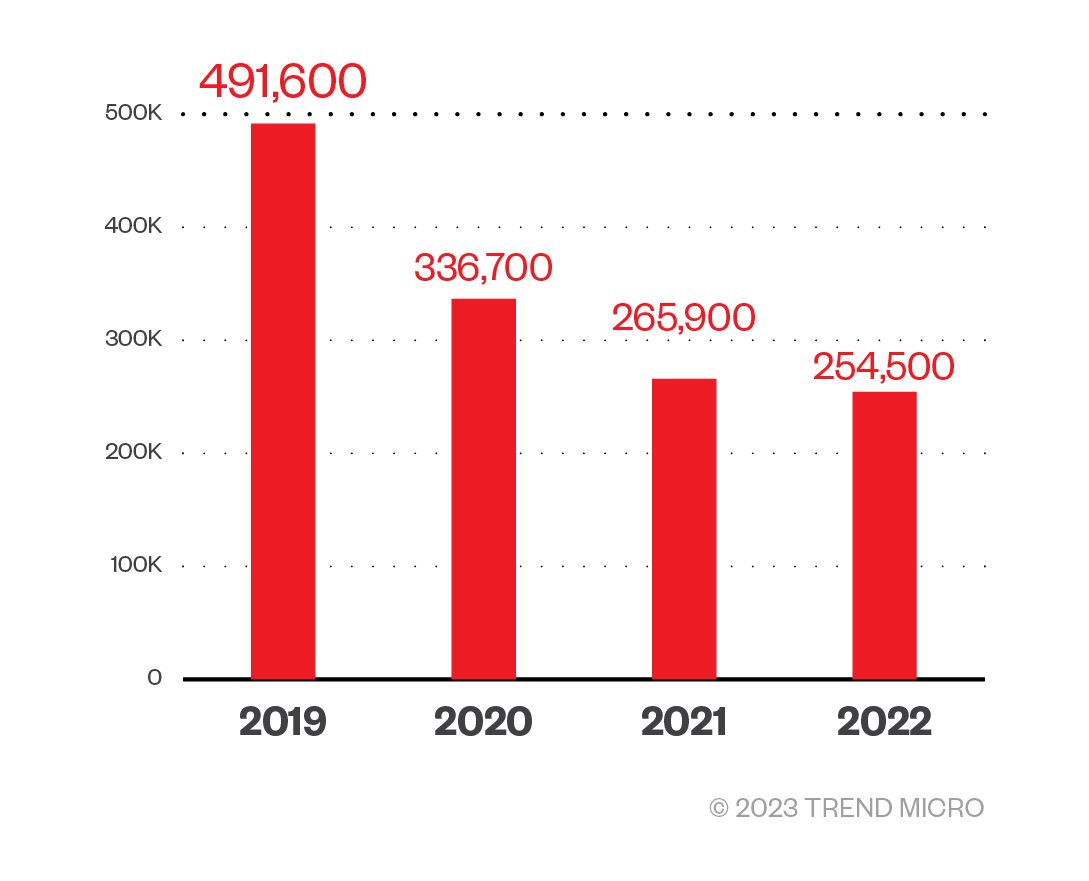
Figure 1. The number of reported ransomware attack incidents based on Trend Micro File Reputation Service data from 2019 to 2022.
Our data showed that threat actors behind ransomware groups continue making high stakes claims, targeting the government, healthcare, and manufacturing organizations, as well as the banking sector and fast-moving consumer goods sector.
This article details an incident response by Trend Micro that successfully stopped what would have been a ransomware attack on an enterprise. Time is of the essence in ransomware attacks such as this, and our services were tapped about a week after the first reported suspicious activity.
 View infographic of Imminent Ransomware Attack
View infographic of Imminent Ransomware Attack
In targeted ransomware attack incidents where we were involved in its response support, statistics show that the average number of days from the threat actor’s initial access to their execution of the fatal attack (encryption of the target system's files), is 6.3 days.
This cautionary tale begins after a security operations officer, who we will name Ashton Lownes for the purpose of this case study, received an email from the company they outsourced to operate part of their security system. The email alerted him to an unauthorized communication within their company’s system.









Over the following days, Lownes and the entire security team continued their investigation of the company’s system and consulted with members of the management to consider response policies.
Several days passed without conclusive results on the initial alert’s full impact. It is important to note that the outsourced company that provided the initial alert did not offer incident response services. Fearing that their own response policies and measures might be inadequate, Lownes made the decision to consult with Trend Micro, their security vendor for the other tools that their enterprise uses.
Compromised assets
The organization conducted a joint investigation with the Trend Micro incident response team and discovered that cybercriminals performed the following unauthorized and malicious activities within the company’s network:
- Cybercriminals stole top-level administrator privileges and used these privileges to conduct unauthorized activities.
- After the intrusion, malicious actors also viewed the organization’s files and removed traces of them doing so.
- Cybercriminals also attempted to steal passwords, based on traces found during the investigation.
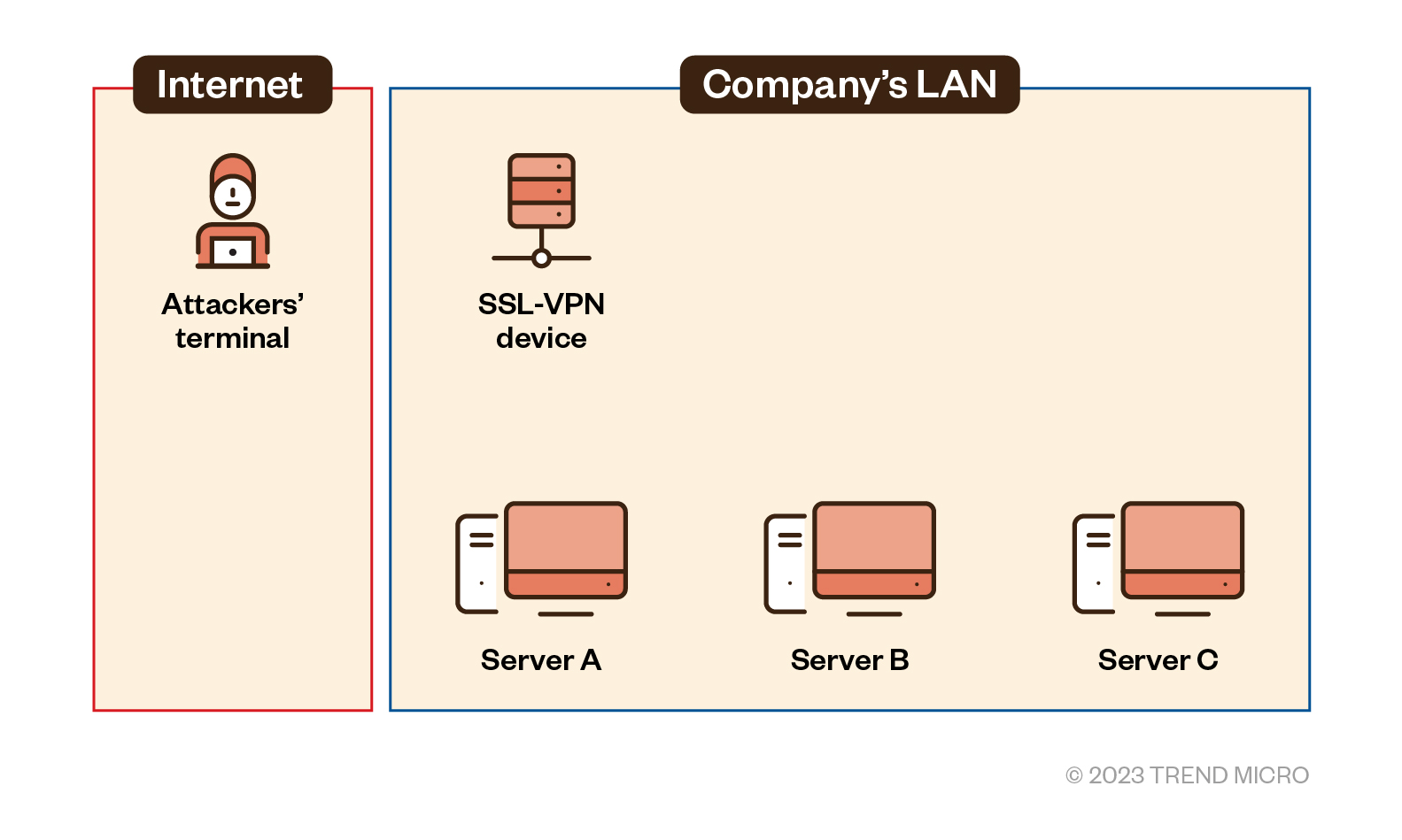
Figure 2. The four devices within the enterprise’s LAN network compromised by the attack
The four devices in Figure 2 were confirmed to have been significantly compromised. In addition to these four, Trend Micro also confirmed that remote command execution requests have been sent to multiple other servers, which means that threat actors succeeded in logging in to the organization’s RDP. We will primarily discuss these four devices that are most relevant to the case in the following sections.
The range indicated by the red frame in Figure 2 is the organization’s internal LAN, which ideally contains an environment that malicious actors typically cannot access via the internet. In this case, it is assumed that threat actors intruded into the organization’s system via SSL-VPN equipment.
It is highly likely that the enterprise would have been substantially affected by the attack had intervention been sought later, especially since the threat actors had already succeeded in gaining initial access to domain administrator privileges.
In the following sections, we discuss the details of this case: how threat actors made the initial access, which vulnerabilities were exploited, what kind of attacks were carried out, how countermeasures were implemented, and the lessons that can be drawn from this event.
Attack vector
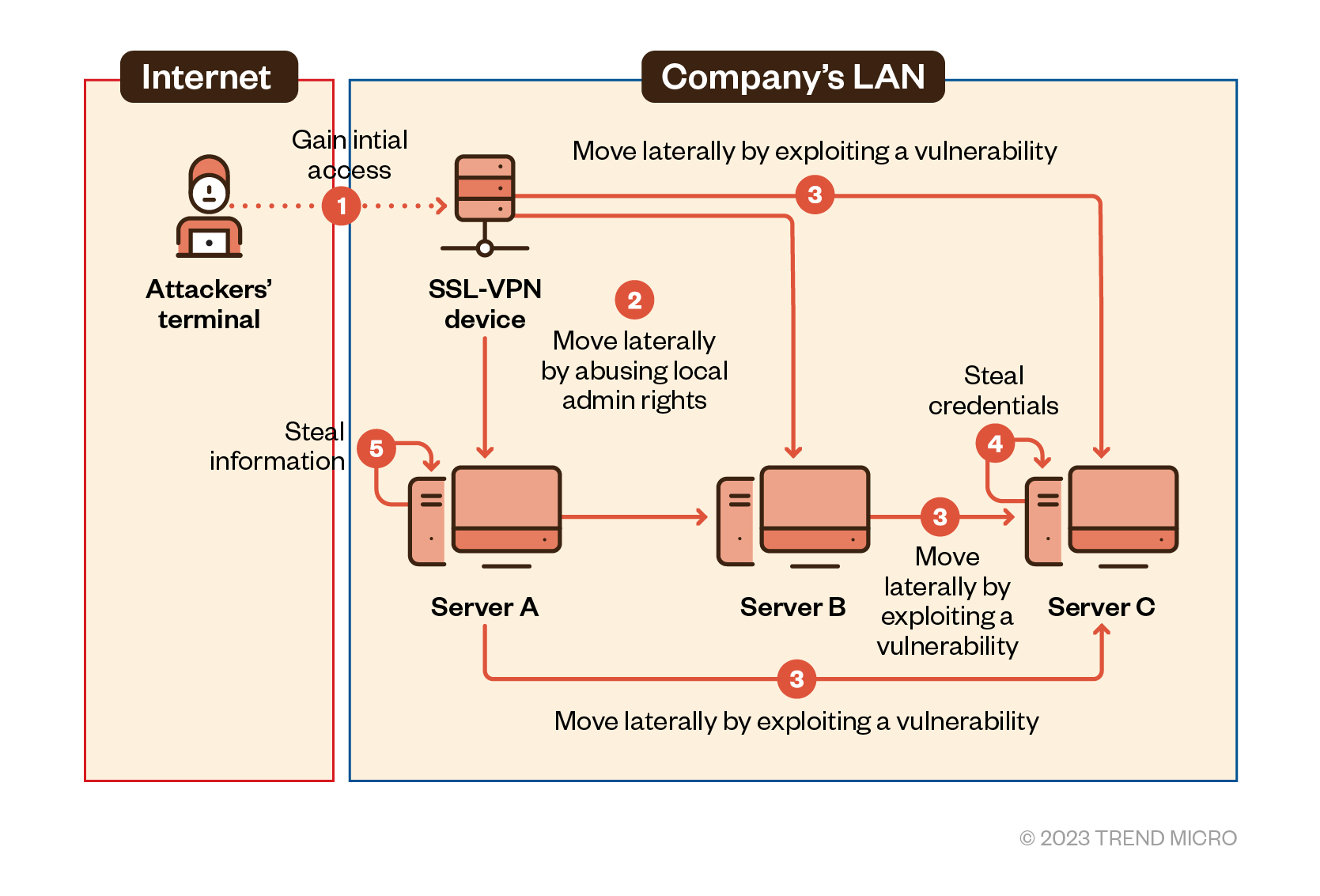
Figure 3. Threat actors gained initial access through the enterprise’s SSL-VPN and moved laterally onto other machines
The threat actors behind the attack first acquired an employee VPN account belonging to the local administrator’s group and compromised the SSL-VPN equipment. It is assumed that they first accessed the LAN through this route. However, this is not fully confirmed in our investigation because of the lack of any definitive trace or evidence, another security gap that we will get into later.
After the intrusion, the attackers used RDP to move laterally to multiple terminals within the organization. It was also confirmed that the attackers viewed some files and searched for or stole information from Server A.
Our investigations also confirmed that the malicious actors attacked Server C by exploiting the Zerologon vulnerability and acquired additional domain administrator privileges.
The team also saw execution traces of the credential dumping tool Mimikatz on Server C and discovered that the malicious actors deleted relevant log files in an attempt to evade detection.
A ransomware attack stopped in its tracks
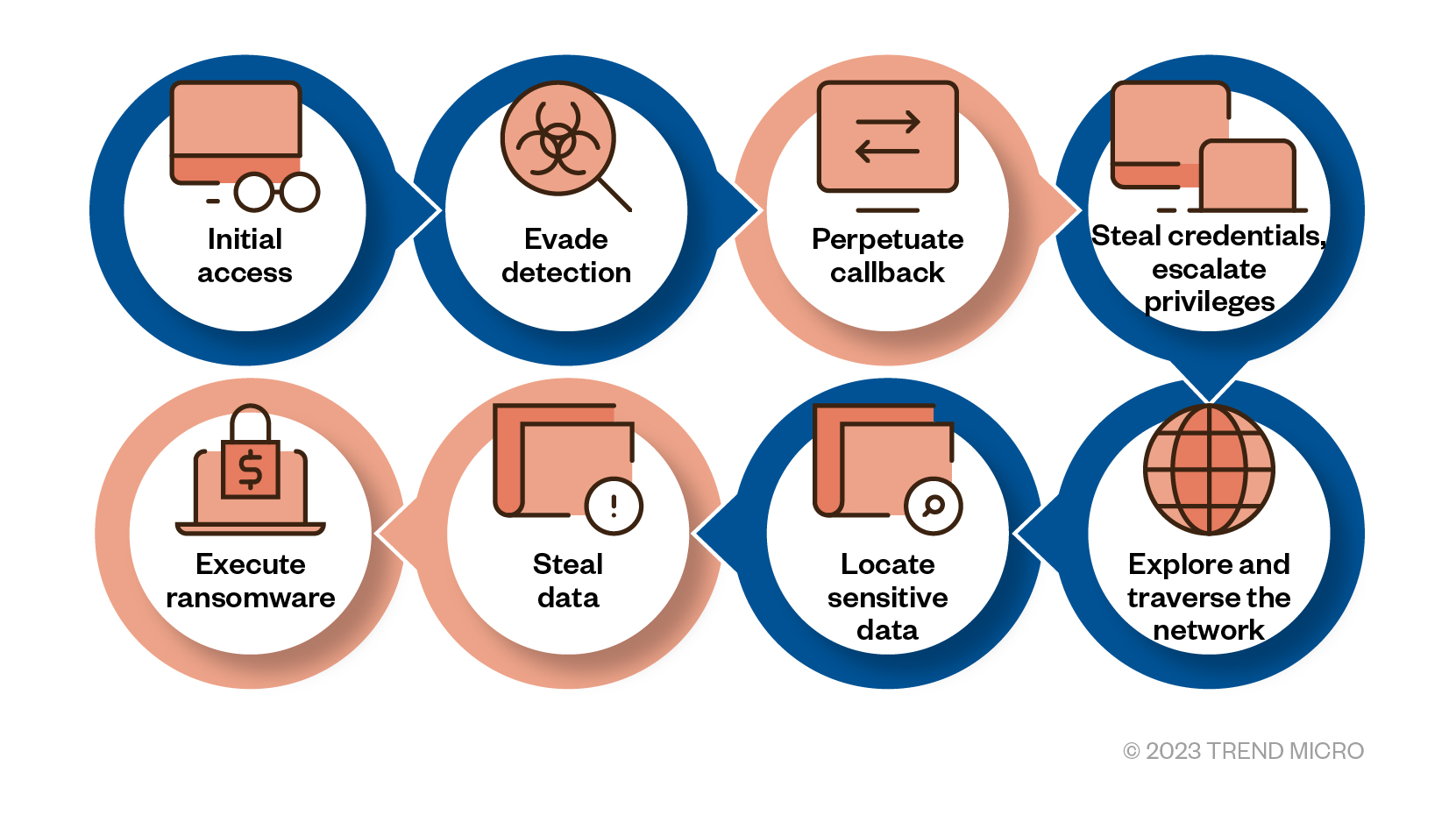
Figure 4. Methods commonly used by ransomware attackers, as confirmed by the Trend Micro response support team. The ones highlighted in blue were observed in the case discussed.
The behaviors observed in our investigation are similar to the attack methods often seen in ransomware cases for which Trend Micro provides response support. Of the eight common methods threat actors often use to orchestrate and carry out a ransomware attack, five were executed in the case discussed in this feature.
We asked the victim organization to promptly implement the appropriate defense measures.
Defense vulnerabilities
We investigated the gaps, or defense vulnerabilities, that allowed the security breach by closing in on each stage of the attack. In this section, we compare the ideal defense system with that of the victim organization at the time of the attack.
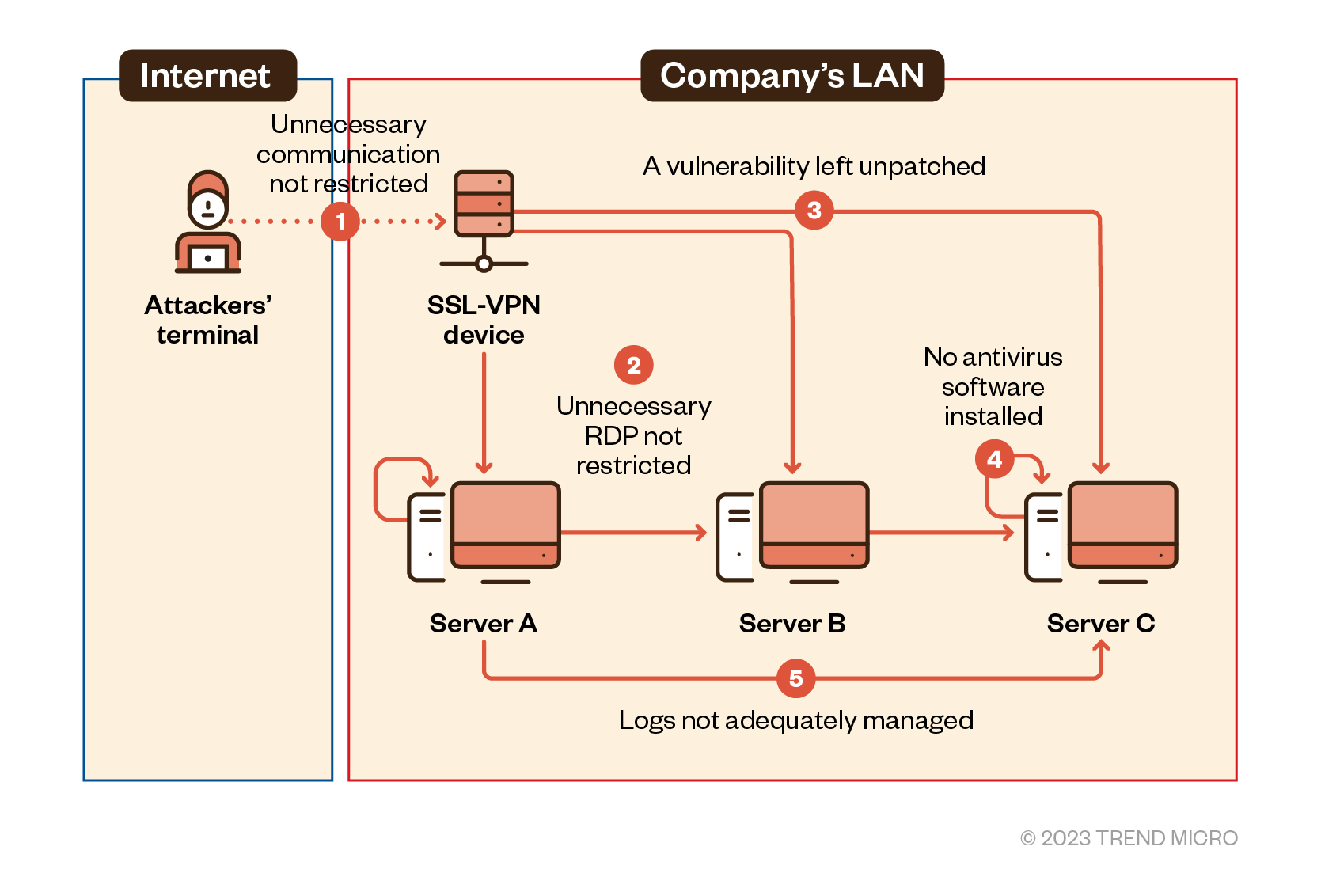
Figure 5. Defense vulnerabilities found in the victim organization’s system
Table 1 lists the five defense vulnerabilities that were exploited in this breach and shows the security measures that should be implemented to reduce the risk of such attacks.
| Defense vulnerabilities | Preventable attacks | Countermeasures |
|---|---|---|
| Communications that do not occur in normal operations were not restricted. | An unattended VPN account was stolen by exploiting a known vulnerability. |
|
| Unnecessary ports (RDP) not used in normal operations were not restricted. | An RDP service not used in normal operations was exploited. |
|
| There were inadequate measures to patch and secure technical vulnerabilities. | There were credentials stolen by exploiting the Zerologon vulnerability. |
|
| There was a server terminal that did not have security software installed. | Mimikatz was executed on a server terminal that did not have security software installed. |
|
| There was inadequate log management. | Server logs were deleted to make tracking difficult. |
|
Table 1. Defense vulnerabilities and countermeasures
Ransomware actors do whatever it takes to profit from their victims. This means that they exhaustively search for gaps in a system, look for vulnerabilities to exploit, and expand their scope of attack without being noticed to then steal information and encrypt important files.
Implementing any of the previously mentioned measures does not necessarily mean that the security of the organization is guaranteed. Rather, reducing the number of vulnerabilities will eventually contribute to the reduction of the total risk that an organization inevitably has to contend with.
Organizations can implement extended detection and response (XDR) to mitigate the risks associated with vulnerabilities and increase an enterprise’s overall security level. XDR supports the protection of the entire organization’s system by continuously monitoring it using sensors placed in various layers, including endpoints, servers, and networks.
XDR helps detect any suspicious behavior at an early stage, such as the ones we reviewed in this case. It also helps determine the extent of an attack’s impact and acquires the information necessary for quick countermeasures and recovery.
Moreover, the following measures can be useful in reducing the risk of being on the receiving end of a similar attack in the future:
- Review your organization’s password management rules, such as those pertaining to expiration periods or password complexity requirements.
- Enforce the principle of least privilege. Delete unnecessary local administrator privileges and disable domain administrator privileges for normal operations.
Conclusion and recommendations
Based on these results, Trend Micro's incident response team presented immediate countermeasures as well as medium- and long-term security procedures for implementation.
Because the organization’s SOC team quickly applied the recommended measures, the organization did not encounter system or operational disruptions.
We recommend that organizations implement the following security measures to protect them against similar attacks:
- Define "normal" network traffic for normal operations. Defining “normal” network traffic will help identify “abnormal” network traffic, such as unauthorized access.
- Ensure that behavior and communication logs are in a safe location. Logs are an integral part of an investigation that can help determine the root cause of an incident. Not having logs available could affect the initial speed in which incident response is carried out.
- Conduct incident response drills and training sessions. Run your team through the process so that members can better understand your policies and gain confidence in the entire incident response process. These training sessions can help them react quickly in real-life incident response situations.
Attackers, in recent years, have become increasingly adept at exploiting vulnerabilities that victims themselves are unaware of and are employing behaviors that are not anticipated. In addition to a continuous effort to prevent any unauthorized access, early detection and response within the organization’s network is critical. Immediacy in remediation is also essential, as delays in reaction time might lead to serious damage.
By understanding attack scenarios in detail (as we have done here), organizations can not only identify vulnerabilities that could lead to compromise and critical damage but can also take necessary measures to prevent them.
With contributions by: Japan Incident Response Team, Japan Marketing Strategy
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering






















 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks