Verizon: PoS Attacks Down, Web Apps Up
SOURCE: 2014, Verizon Data Breach Investigations Report (DBIR)
We’ve all seen the string of point-of-sale (PoS) system attacks in the US after the holidays. Two retail giants got hit with widespread information theft that left about 110 million customers in one and 1.1 million credit card details exposed.
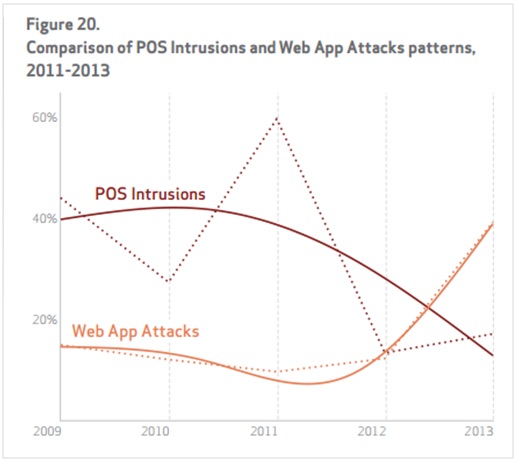
But contrary to recent media reports on the continued rise of PoS attacks, Verizon says PoS-related cases are actually on a downward trend and have been so since their peak in 2010.
Though Verizon still acknowledges that 2013 was the “year of the retailer breach,” the company’s recent Data Breach Investigations Report (DBIR) shows that web application attacks are actually responsible for the rising number of breaches.
Verizon claims that web apps remain the “proverbial punching bag of the Internet” with 3,937 total incidents in 2013—490 of which had confirmed cases of stolen information. Many of these attacks were done by targeting flaws in applications or by using stolen credentials to get in systems. Either way, a web app attack is a hotspot incident that frequently bothers the information (41%), utilities (38%), trade (30%), and finances (27%) industries the most.
Attackers Want Your Payment Cards
The Verizon report also notes how attacks have shifted from being geopolitical to large-scale payment card system attacks. A total of 198 confirmed PoS intrusions incidents with successful data breaches were noted in 2013.
Data shows that, despite recent attacks on large retail corporations, attacks using PoS intrusions remain a small-and-medium business issue. This makes restaurants, hotels, grocery stores, and the like potential targets for this type of attack.
Attackers profit from stolen customer information because of the underground demand for personally identifiable information (PII). Underground forums are full of exchanges for credit card and other information that can be tied to a real person. In Russia, for instance, U.S. credit cards can sell for up to $3 each. Recent studies have also found proof of thriving underground markets in China and Brazil.
All is not in the Clear
“Everyone is vulnerable to some type of event. Even if you think your organization is at low risk for external attacks, there remains the possibility of insider misuse and errors that harm systems and expose data,” the report states.
There are a total of 63,437 incidents in 2013 which put information in compromised situations. 1,367 of these were confirmed breaches that could have led to data being disclosed. These incidents can be in the form of PoS intrusions, web app attacks, insider misuse, physical theft or loss, miscellaneous errors, crimeware, card skimmers, DoS attacks, cyber-espionage, or others.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- Threat Attribution Framework: How TrendAI™ Applies Structure Over Speculation
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks
- The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One