Osama bin Laden's Death Serves as Social Engineering Lure
Data de publicação: segunda-feira, 9 de maio de 2011
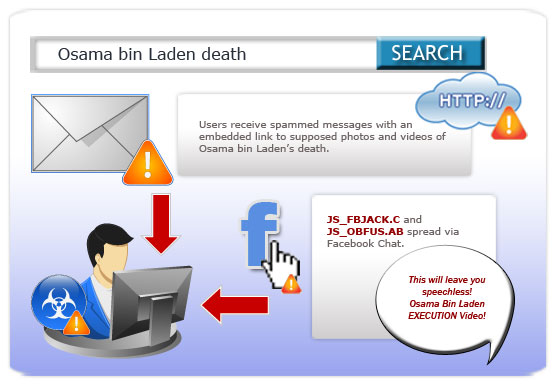
News of Osama bin Laden’s death took the worldwide Web by storm, filling blogs and social networking sites like Facebook and Twitter with details on how the al-Qaeda founder died. The attention and coverage bin Laden’s death obtained online thus spurred cybercriminals to leverage the incident to propagate their own brand of terrorism. To protect yourself and your system against malicious attacks while staying informed, you may find the information below useful.
How does this threat arrive on the user’s system?
The following attacks have been spotted by TrendlabsSM engineers from the time news of bin Laden’s death broke:

- Links poisoned via blackhat search engine optimization (SEO) techniques in relation to bin Laden’s death were spotted.
- Users looking for news and information on the event using Google, Yahoo!, and other online search engines thus landed on malicious sites or pages instead.As expected, spammed messages disproving bin Laden’s death with supposed photos as evidence also littered the Web.
- Several Facebook users were also spammed malicious links to sites or pages supposedly containing videos and/or pictures of bin Laden’s “execution.” Apart from wall posts, the malicious links also appeared in chats.
How can these threats affect users?
Users who click poisoned links that appear as popular search engine results may land on phishing or malware (e.g., FAKEAV variants) download sites or pages. Those who are tricked into opening spammed messages and clicking the link embedded in these are likely to suffer the same consequence. Users who have been tricked into copying and pasting a malicious JavaScript code detected by Trend Micro as JS_OBFUS.AB to view a “video” into their Web browsers’ address bars end up with malware-infected systems. Others who have been tricked into clicking a link embedded in certain Facebook Chat messages may also end up with JS_FBJACK.C-infected systems.
What are JS_OBFUS.AB andJS_FBJACK.C's routines?
JS_OBFUS.AB triggers the posting of wall messages enticing an affected user’s contacts to click the malicious link as well using a video as lure. The wall post also contains the instructions that the users should follow to view the video. The script also sends the same malicious link to all of the affected user’s contacts via Facebook Chat.
Like JS_OBFUS.AB, JS_FBJACK.C also triggers the sending of messages with a malicious link to an affected user’s online Facebook contacts via Chat. Clicking the link directs the user to a possibly malicious site. It also posts wall messages enticing others to click the embedded link. Finally, it automatically signs up the affected user as a fan of a particular Facebook page.
Why is this threat noteworthy?
Celebrity deaths are usually noteworthy because these are effective social engineering baits. Sites on which stories about popular people, shows, and the like attract a lot of curious readers, pushing them to the top of search results pages. Because cybercriminals know this, too, they often prey on the curious. They poison links via blackhat SEO techniques to redirect users to compromised or specially crafted malicious sites or pages, which allow them to profit from their victims’ misery.
Are Trend Micro product users protected from this threat?
Yes, Trend Micro product users are protected from this threat. Powered by the Trend Micro™ Smart Protection Network™, Trend Micro products prevent spammed messages from even reaching users’ inboxes via the Email Reputation Technology, blocks access to malicious links via the Web Reputation Technology, and stops the execution of malicious files via the File Reputation Technology.
What can users do to avoid this malware from executing in their systems?
To protect your system from the payloads of malicious scripts like JS_OBFUS.AB and JS_FBJACK.C, follow these useful tips:
- Avoid clicking links embedded in dubious-looking email messages even if these come from known senders. If possible, immediately delete spam.
- Instead of looking for news and information using search engines, visit credible news sites instead by directly typing their addresses on your browser’s address bar. Bookmarking often-visited sites and relying on these for information lessens your chance of becoming a blackhat SEO attack.
- Be wary of news and information on social networking sites. It is always safer to assume that these are false unless linked to credible news sites. Exert effort to read through previous wall posts or Tweets to know exactly where the information came from.
- Purchase and install a reliable security software and keep it updated. Constantly download and install patches for your system’s OS and for all of your applications as soon as these are released by their respective vendors.
Expert Insights
“Facebook threats or attacks succeed because its users trust their contacts. They automatically click links embedded in direct and chat messages as well as event invitations that their contacts sent, unmindful that their friends’ accounts may have been compromised. It is thus a good idea to always seek confirmation from the messages’ senders. Always think twice before you click.” -- Karla Agregado, TrendLabs Web Blocking Engineer