Mass Compromise Leads to FAKEAV and WORID Infections
Data de publicação: sexta-feira, 1 de abril de 2011
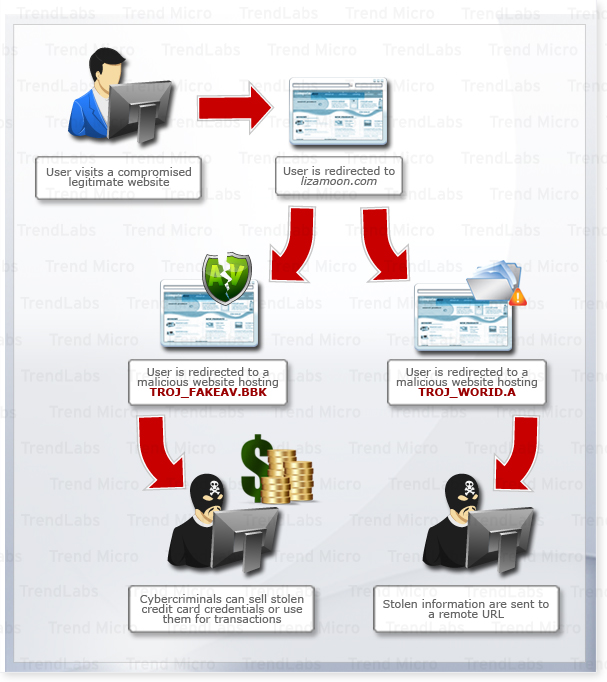
A recent SQL injection attack affecting hundreds of thousands of sites, however, proves that the days of mass compromise attacks are far from over. On the contrary, cybercriminals behind the attack succeeded in accessing databases of ASP and ASP.net websites and in proliferating malicious URLs that point to FAKEAV and WORID malware variants.
How does this attack arrive on users’ systems?
Users who visit compromised websites injected with the script will be redirected to a URL under the domain lizamoon.com. After this, they will be redirected to one of several malicious URLs used in this attack. Depending on the final landing page, the machines can be infected with a FAKEAV or WORID variant. It is also possible for users to land on a page that displays a 404 warning, which in reality, is a canned reply that will be displayed if users have previously visited the page.
Based on recent findings, however, sites previously injected with malicious code hosted in the lizamoon.com domain were later to be injected with the same script but with a new domain. This shows that the attack is ongoing and the attackers are not yet done updating their routines. It also shows that the attackers know that this threat is in the process of being mitigated, and thus they are on a race to infect other websites with the malicious scripts.
This attack itself is not only confined to lizamoon.com. Other websites, one example of which being t6ryt56.info, have been discovered to display the same exact behavior as lizamoon—redirecting a visitor into either a TROJ_FAKEAV.BBK or a TROJ_WORID.A-hosting website. Further investigation into the redirecting websites yield that they each resolve into the same IP address as that of lizamoon, pointing to one single group behind all these attacks.
How is the user affected by this attack?
Unwitting users who end up on compromised sites could download any of two known malicious files on their systems—TROJ_FAKEAV.BBK or TROJ_WORID.A.
On systems infected with the FAKEAV variant, users will be able to see the usual fake scanning results used in scareware. The final window prompts victims to purchase the full version of the so-called antivirus software. As such, users could end up handing over their credit card information to the cybercriminals behind the attack.
Other users with machines infected with TROJ_WORID.A could also suffer information theft, because the Trojan sends encrypted data to URLs following specific parameters. It sends system information such as data on the operating system used, debug information and user privilege.
What makes this attack noteworthy?
Mass compromises may not be new but their recurrence is an important reminder that many websites are still not immune to SQL injection attacks. In the case of the LizaMoon attack, the attackers succeeded in injecting the script into hundreds of thousands of websites with no specific common denominator.
Affected sites were related to a variety of subjects—astronomy, sports and even funeral. In addition to the significant number of affected sites, the fact that they covered a range of interests further increases the possibility of user infection.
Are Trend Micro customers protected from this threat?
Yes, the Trend Micro™ Smart Protection Network™ Web reputation technology blocks access to compromised sites and the known malicious URLs that host malware. File reputation technology likewise prevents the execution of and deletes all known malicious files from users’ systems.
What can users do to prevent this threat from entering computers?
Considering the nature of website compromises, there is no clear cut way of avoiding such attacks. Users have no way of predicting which legitimate websites will be compromised by cybercriminals. In such cases, proactive security solutions that are able to detect and block suspicious websites such as lizamoon.com prior to an attack can help prevent infections. In this particular incident, Trend Micro detected and blocked the domain on the same day it was created using bogus registration details.
Expert Insights
"Once again we saw the significant number of vulnerable—misconfigured, unsecured, etc.—websites that are out there in the Internet. Too bad that a LizaMoon attack had to happen to prove this fact, and at the same time, be used as a launch pad for malware attack—particularly FAKEAV. The overwhelming number of compromised sites certainly increases the success rate of such attacks."—Joseph Cepe, Trend Micro Threat Analyst
How does this attack arrive on users’ systems?
Users who visit compromised websites injected with the script will be redirected to a URL under the domain lizamoon.com. After this, they will be redirected to one of several malicious URLs used in this attack. Depending on the final landing page, the machines can be infected with a FAKEAV or WORID variant. It is also possible for users to land on a page that displays a 404 warning, which in reality, is a canned reply that will be displayed if users have previously visited the page.
Based on recent findings, however, sites previously injected with malicious code hosted in the lizamoon.com domain were later to be injected with the same script but with a new domain. This shows that the attack is ongoing and the attackers are not yet done updating their routines. It also shows that the attackers know that this threat is in the process of being mitigated, and thus they are on a race to infect other websites with the malicious scripts.
This attack itself is not only confined to lizamoon.com. Other websites, one example of which being t6ryt56.info, have been discovered to display the same exact behavior as lizamoon—redirecting a visitor into either a TROJ_FAKEAV.BBK or a TROJ_WORID.A-hosting website. Further investigation into the redirecting websites yield that they each resolve into the same IP address as that of lizamoon, pointing to one single group behind all these attacks.
How is the user affected by this attack?
Unwitting users who end up on compromised sites could download any of two known malicious files on their systems—TROJ_FAKEAV.BBK or TROJ_WORID.A.
On systems infected with the FAKEAV variant, users will be able to see the usual fake scanning results used in scareware. The final window prompts victims to purchase the full version of the so-called antivirus software. As such, users could end up handing over their credit card information to the cybercriminals behind the attack.
Other users with machines infected with TROJ_WORID.A could also suffer information theft, because the Trojan sends encrypted data to URLs following specific parameters. It sends system information such as data on the operating system used, debug information and user privilege.
What makes this attack noteworthy?
Mass compromises may not be new but their recurrence is an important reminder that many websites are still not immune to SQL injection attacks. In the case of the LizaMoon attack, the attackers succeeded in injecting the script into hundreds of thousands of websites with no specific common denominator.
Affected sites were related to a variety of subjects—astronomy, sports and even funeral. In addition to the significant number of affected sites, the fact that they covered a range of interests further increases the possibility of user infection.
Are Trend Micro customers protected from this threat?
Yes, the Trend Micro™ Smart Protection Network™ Web reputation technology blocks access to compromised sites and the known malicious URLs that host malware. File reputation technology likewise prevents the execution of and deletes all known malicious files from users’ systems.
What can users do to prevent this threat from entering computers?
Considering the nature of website compromises, there is no clear cut way of avoiding such attacks. Users have no way of predicting which legitimate websites will be compromised by cybercriminals. In such cases, proactive security solutions that are able to detect and block suspicious websites such as lizamoon.com prior to an attack can help prevent infections. In this particular incident, Trend Micro detected and blocked the domain on the same day it was created using bogus registration details.
Expert Insights
"Once again we saw the significant number of vulnerable—misconfigured, unsecured, etc.—websites that are out there in the Internet. Too bad that a LizaMoon attack had to happen to prove this fact, and at the same time, be used as a launch pad for malware attack—particularly FAKEAV. The overwhelming number of compromised sites certainly increases the success rate of such attacks."—Joseph Cepe, Trend Micro Threat Analyst