ZeuS, Still a Threat; Now Also Spreading Through LICAT
Data de publicação: quinta-feira, 21 de outubro de 2010
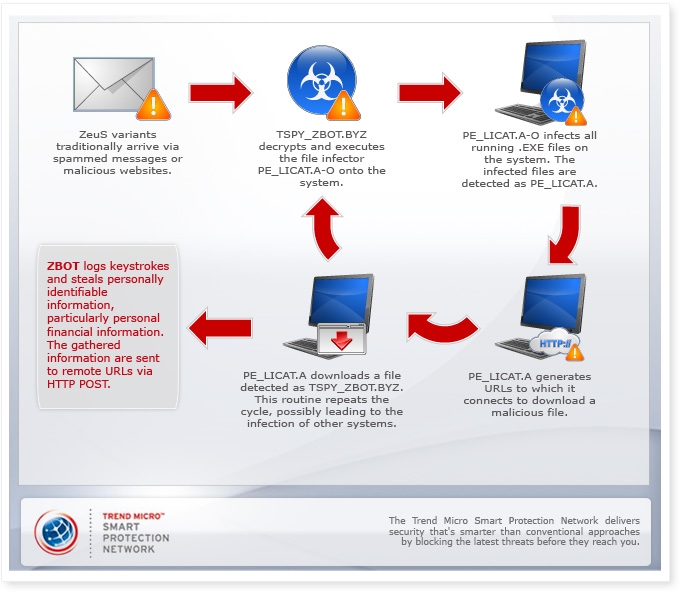
In October, TrendLabsSM reported on PE_LICAT.A-O, a new malware that inserts its code into .EXE files, turning them into the downloader PE_LICAT.A, which generates and accesses URLs to download TSPY_ZBOT.BYZ.
What is ZeuS and what does it do?
ZeuS is the name of a toolkit sold in underground forums that is responsible for creating a breed of information-stealing Trojans detected by Trend Micro as the TSPY_ZBOT family of threats. Trend Micro has been monitoring the ZBOT family as early as 2007.
ZeuS' creators have been continuously updating it throughout the years. This has given its cybercriminal patrons more options in terms of additional functions. ZeuS Trojans are key to carrying out sophisticated cybercrimes wherein unsuspecting users’ banking credentials are stolen and are used to channel funds to the criminals' accounts.
For more information about TSPY_ZBOT and how it steals data, read "ZeuS and Its Continuing Drive Towards Stealing Online Data."
For more technical readers, our researchers wrote a comprehensive treatment of the ZeuS threat (March 2010) in "ZeuS: A Persistent Cybercriminal Enterprise"�and "File-Patching ZBOT Variants: ZeuS 2.0 Level Up."
What is LICAT and what does it do?
PE_LICAT.A-O specifically targets executable aka .EXE files, the typical file format for software installer packages. PE_LICAT.A-O inserts its code into executable programs such as .COM and .EXE files. This turns the .EXE files PE_LICAT.A-O patches into PE_LICAT.A, which does not infect other files.
Many of the malware today access a hard-coded URL once executed. However, since antivirus products can easily identify the URLs, these are blocked, disabling the malware from performing its intended download routine.
PE_LICAT.A attempts to prevent its URLs from being blocked by generating new sets of domains every time it is executed. This makes it hard for antivirus products to block all of the URLs. In this attack, every time PE_LICAT.A successfully accesses a live URL, it downloads TSPY_ZBOT.BYZ, a ZeuS variant, onto the affected system.
A more detailed description can be found in "File Infector Uses Domain Generation Technique Like DOWNAD/Conficker."
Recently, we received a new LICAT sample that communicates with its command-and-control (C&C) server using a pseudorandomly generated domain not found among those generated by the original algorithm. This new sample, however, still had the original routines�found in the original LICAT sample but with a different XOR key and uses multiple keys. This variant is detected as PE_LICAT.B-O, while patched files�are detected as PE_LICAT.B. More details can be found in "Updated ZeuS-LICAT Variant Spotted."
Is LICAT widespread? Can I become a target?
LICAT affects users from several regions, including EMEA and NABU. Trend Micro Researcher Rik Ferguson discussed this on his CounterMeasures blog.
How will I know if my system has been infected?
Unfortunately, this malware does not show any visible clue of its existence in a system.
More tech-savvy users, however, may be able to detect the existence of a suspicious, randomly named file in the Startup folder (for LICAT) or of randomly named folders in the Application Data folder (for ZBOT). Modified files, on the other hand, will have a different hash.
To confirm a possible infection, update your security software and completely scan your system.
My computer at work got infected and I used my thumb drive to save my files. Should I be worried that my thumb drive has been infected too?
Unlike STUXNET, this malware does not spread through removable drives like external hard drives or thumb drives. However, accessing a removable drive that contains an .EXE file via an already-infected system may infect the .EXE file as well. For more information on how PE_LICAT.A-O and PE_LICAT.A behave, check out the following reports:
People are saying it is related to Conficker, should I be alarmed?
LICAT's association with Conficker/DOWNAD is due to its use of the same domain generation technique aka domain generation algorithm (DGA). This technique, which can help the malware evade malicious URL blocking, was last seen in Conficker in 2009. Besides that, however, there are no other links between Conficker and LICAT.
What should I do to avoid system infection?
We strongly advise that you update your system's antivirus patterns as soon as possible to stay protected. Non-Trend Micro product users may use HouseCall to check their systems for infections.
How did I get this threat?
Based on the available information, this threat seems to arrive via drive-by downloads. Drive-by downloads occur when a file is downloaded onto a system without its user's knowledge.
After checking against several trigger conditions, TSPY_ZBOT.BYZ may also decrypt and execute PE_LICAT.A-O in memory.
How can this threat affect me?
ZeuS variants are known for stealing users' banking credentials, which are necessary for conducting online transactions. Users with LICAT-infected systems are at risk of losing their online financial assets to cybercriminals.
What is the driving force behind this threat?
ZeuS variants are primarily created for profit.
What makes this attack different?
This is the first time a LICAT variant was used to spread ZeuS. The DGA PE_LICAT.A used was also last seen in DOWNAD/Conficker variants.
Are Trend Micro product users protected from this threat?
Yes. Solutions supported by the Trend Micro™ Smart Protection Network™ can detect and prevent the execution of the malicious files via the file reputation technology. It also blocks access to malicious sites and phone-home attempts wherein an infected system tries to upload stolen data to or to download additional malware from C&C servers via the Web reputation technology.
What can I/my organization do to prevent this and similar threats from entering my computer/network?
- Use a firewall to monitor incoming connections from the Internet.
- Ensure that programs and users of the computer use the lowest level of privileges necessary to complete a task.
- Always keep your software patch levels up-to-date.
- Always keep your pattern files up-to-date.
- Avoid visiting untrustworthy sites that may redirect or download malware onto your system.
- Configure your email server to block or remove email messages that contain file attachments such as .VBS, .BAT, .EXE, .PIF and .SCR files.
- Avoid opening email attachments unless expected.
Note: When a computer has already been compromised, isolate it immediately from the network. Update/reset access information such as user names/passwords for all sites/applications.