CARBANAK Targeted Attack Campaign Hits Banks and Financial Institutions
Data de publicação: terça-feira, 17 de fevereiro de 2015

Imagine a targeted attack that aims for financial profit rather than the typical stealing of enterprise’s “crown jewels” or confidential data—then you have CARBANAK. According to news reports, a backdoor hit more than 100 banks and financial organizations. The attack, which began late 2013, affected banks across the globe.
What is CARBANAK?
CARBANAK is the detection name related to the targeted attack campaign that hit banks and financial organizations. Based on reports, it employed methods and techniques such as spear phishing email and exploits, commonly seen in targeted attacks. Accordingly, attackers did intelligence gathering about their target networks in order to infiltrate it. Similar to other targeted attacks, they also used spear phishing emails as their point of entry to their attack. Trend Micro detects this as BKDR_CARBANAK.A.
Who are the targets?
The attackers behind CARBANAK malware targets banks and financial institutions located from various countries such as Russia, US, Ukraine, and others countries in Asia Pacific region.
How does the malware enter a network?
Attackers behind CARBANAK send spear phishing emails to their target banks’ employees. The said email message has attachments containing known or old exploits such as CVE- 2012-0158, CVE-2013-3906, and CVE- 2014-1761. When successfully exploited, it executes a shellcode, which in turn, executes the CARBANAK malware. In another infection chain, users get a .CPL file attachment which when executed also leads to CARBANAK malware.
Attackers normally leverage old and known exploits given that some users do not immediately patch their systems with new software or system updates.
What happens after the threat actors successfully infiltrate a network?
Once recipients of the spear phishing emails open the said malicious email with attached exploits, CARBANAK malware is executed. One of the notable behavior of this malware is it allows remote users to execute commands such as capturing screenshots when accessing certain websites, stealing cookies, injecting codes to sites so as to monitor it, and deleting cookies from browsers among others. In addition, it also gathers system information.
To move laterally across the network, attackers also used remote administration tools thus reaching their target systems related to processing bank accounts. When they reached their target systems, attackers then recorded videos of the activities and operations of the affected user, probably to familiarize with banking procedures and workflow via their stolen information. Information is used to manipulate bank records and transfer funds into their accounts without being detected.
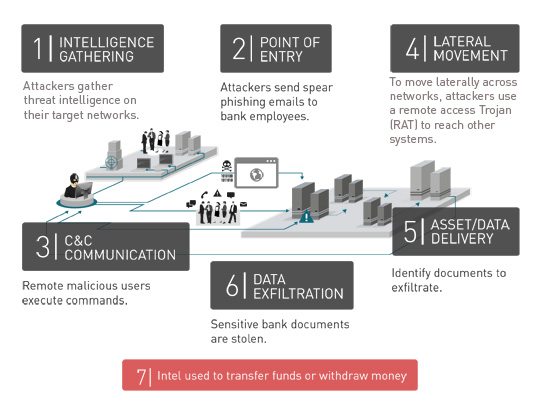
Infection diagram
During our investigation, we found other malware being used in the attack. Trend Micro detects these as:
How were the threat actors able to siphon money?
Once attackers are able to infiltrate the target network, the next step is to transfer the stolen money to their accounts. To do this, they used the Society for Worldwide Interbank Financial Telecommunication (SWIFT) network. In other cases, they employed e-payment systems just to send money from fake accounts and even assigning ATMs.
I am a customer using Trend Micro products. Am I protected from this threat?
Yes. Trend Micro product users are protected from this targeted attack via the following solutions:
Custom Defense
Trend Micro Deep Discovery provides the network-wide visibility and intelligence that is the cornerstone of the Custom Defense solution against so-called APTs (advanced persistent threats) and targeted attacks such as this one.
For the Carbanak attack scenario, Deep Discovery could detect the attack at several different points in the sequence of events:
- Trend Micro Deep Discovery Email Inspector is able to detect the spear-phishing emails sent by attackers to the banks’ employees as the initial step to breach traditional security defenses, establish a foothold, and commence a targeted attack. Deep Discovery Email Inspector has email inspection capabilities that discover malicious content, attachments, and URL links that pass unnoticed through standard email security.
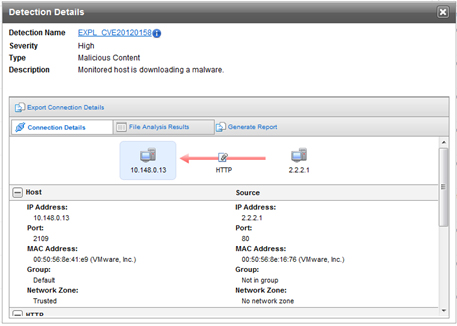
Deep Discovery detecting exploit attached to spear phishing email
- Trend Micro Deep Discovery Analyzer is able to detect even previously unknown threats by analyzing a broad range of file types, sizes, and sources using customizable sandbox environments that attackers design and build to match organization’s desktop and device platforms. It enhances the malware detection capabilities of all existing security investments by giving the ability to share detected and analyzed threat insight, enabling security infrastructure to prevent malicious communication, websites, applications, malware and attacker behavior from spreading.
- Trend Micro Deep Discovery Inspector is able to identify suspicious activities anywhere on network, such as those executed by Carbanak in moving laterally through the network and connecting to its command and control. Deep Discovery Inspector is also able to proactively detect the traffic triggered by the remote administration tool used by attackers.
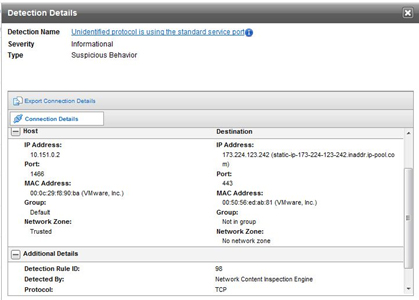
Deep Discovery Inspector heuristically detecting traffic from Ammy Remote Admin Tool
Deep Discovery Inspector is capable of monitoring traffic across all ports and more than 80 protocols and applications to detect threats that are purposely built to evade traditional security defenses. It also features Trend Micro Advanced Threat Scan Engine that is able to detect the malicious email attachments with embedded exploit code through its forward-looking heuristic rules.
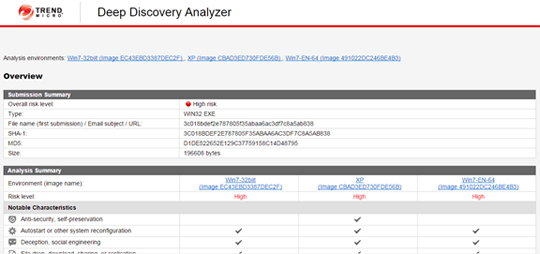
Sandbox analysis result for a sample Carbanak variant
Once detected, Deep Discovery can provide the organization with both local intelligence and global threat intelligence from the Trend Micro Smart Protection Network to identify and assess the risk of the malware, communications or activities found.
Finally, Deep Discovery provides automated security signature updates and alert notifications to the organizations’s other security products to enable a full Custom Defense that stops the attack from progressing further. Examples include:
- Providing IOC (Indicators of Compromise) information including C&C blacklists to both Trend Micro and third party security products
- SIEM alerting and full IOC sharing
- Optionally invoking Trend Micro Network VirusWall Enforcer to isolate endpoints known to be infected
Endpoint Protection
Properly-configured endpoint solutions can ensure the prevention of Carbanak from coming into the machine or network.
- Components of OfficeScan Corporate Edition (OSCE) such as SmartScan, Web Reputation Service, Behavior Monitoring, and Smart Feedback offer the best protection against CARBANAK by detecting the malicious files.
- Worry-Free Business Security/Services (WFBS/WFBS-SVC) is also equipped with technologies to detect and remove Carbanak in the machine or network
Mail Scanning Solution
Email played a big part in the delivery of Carbanak, making it an important vector to protect from attackers.
- Trend Micro Hosted Email Security offers technologies such as the connection-level and content-based reputation filtering, designed best to block threats that arrive via email.
- Trend Micro InterScan Messaging Security Virtual Appliance leverages the Trend Micro Advanced Threat Scan Engine in order to detect document exploits such as the ones used in this attack.