NECURS: The Malware That Breaks Your Security
Data de publicação: sexta-feira, 28 de março de 2014
Recently, we’ve detected a surge of NECURS infections, each one of them tracked and noted thanks to our own Trend Micro™ Smart Protection Network™. We detected the surge to start around late February 2014, with the amount of infections peaking around early March.
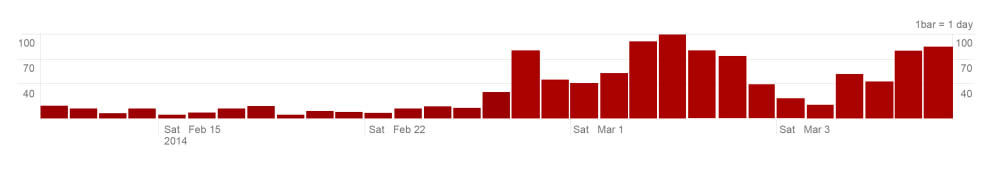
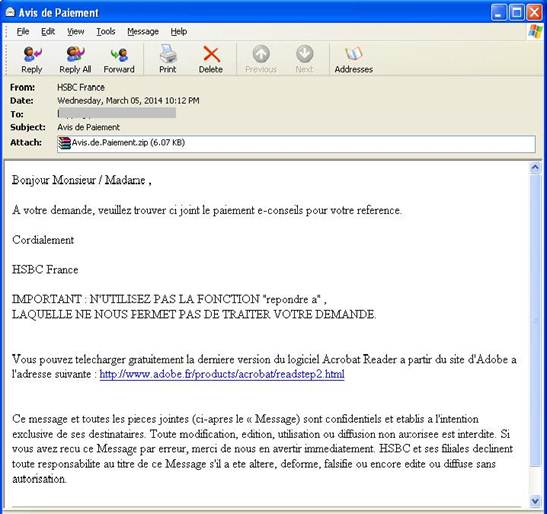

Fig 1. NECURS infection count (February - March 2014)
How does NECURS arrive into users’ systems?
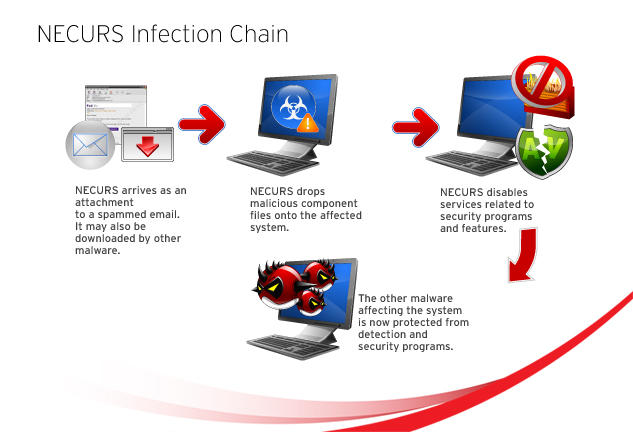
NECURS and its variants arrive into users’ systems by being download by other malware, such as UPATRE. It may also infiltrate systems by being an email attachment to a malicious spammed mail, as shown below:

Fig 2. Spam with malicious NECURS attachment
NECURS may also find its way onto systems through malicious ads.
What happens when users execute this threat on their systems?
Once downloaded and installed on the affected system, NECURS variants disable security services and elements as their main routine. This is combined with information theft as well as performing certain routines to avoid detection and make their presence persist (ensuring their automatic execution upon system startup). They may also drop component files and/or malware.
How does this threat affect users?
Users affected by NECURS variants will find the security of their systems compromised, as they effectively shut down services and/or elements that relate to system security. One particular variant, BKDR_NECURS.BGSH deactivates the system firewall and disables users from being able to turn it back on again. Their system may fall prey to other information-stealing malware, or malware that can give a cybercriminal remote access to the infected system itself.
Another variant, RTKT_NECURS.BGSF, disables security programs by disabling services they’re associated with, along with their drivers. This leaves the user’s system vulnerable for any other malware to attack it.
Why is this threat notable?
NECURS and its variants are notable because it is a prime example of cybercriminals using ‘supplemental’ malware as a payload in order to protect the main malicious routines of their original creations. With NECURS being a downloaded payload of certain malware, such as UPATRE variants, NECURS variants serve as a shield to stop other malware (as well as itself) from being detected and/or stopped.�
As a payload all on its own, it gives cybercriminals a hidden ‘entryway’ into infected systems, allowing them to slip in and install malware without being detected or blocked by the firewall.
Are Trend Micro users protected from this threat?
Web Reputation Services™�in Trend Micro™�security offerings detects the malware that has NECURS variants as a payload and blocks them. Additionally, Email Reputation Services™�blocks the spammed mail that delivers the malware in question as a malicious attachment.
What can users do to prevent these threats from affecting their computers?
Users are always advised to be constantly vigilant of all the mail they receive, most especially ones that come from unexpected or suspicious senders. Should the mail received come from an official entity, first verify from an outside source if the mail is indeed legitimate.�
Installing a security solution that blocks malicious, malware-carrying spam even before they can reach your inbox is also essential in protecting yourself from becoming a victim.