Revealing the Hidden Routines of ZACCESS
In the past, cybercriminals have crafted malicious files that exhibit explicit behavior such as in the case of FAKEAV, ransomware, and adware which display noticeable message prompts and pop-ups. However, there are also malware that prefer to keep their routines under wraps. ZACCESS is the type of malware that does just that. It performs its routines hidden from plain sight, and due to its rootkit technology, it can download other malware and steal important information right under victims’ noses. With more than 140,000 worldwide infections as of our 2Q 2012 Security Roundup, we may be seeing more of this threat.
What is ZACCESS?
ZACCESS (ZEROACCESS) aka SIREFEF is a rootkit malware crafted to push fake applications and other malware into infected systems while staying hidden from detection.
ZACCESS variants generally do not collect user data e.g. user names and passwords. However, ZACCESS may also download other malware that may perform the said routines. ZACCESS is capable of running on both 32-bit and 64-bit Windows Operation System.
ZACCESS is known to open random ports in order to connect to its command and control (C&C) server. This communication allows remote attackers to connect to the infected machine. Once the connection is established, remote attackers can perform their commands. To remain hidden, ZACCESS prevents detection by disabling or terminating Windows security-related services.
How do users encounter this threat?
ZACCESS is bundled with pirated copies of popular movie titles. Some examples of movie files seen with ZACCESS variants were The Dark Knight Rises, Amazing Spiderman, and Hunger Games. Users may also encounter this malware via drive-by-downloads while visiting specific malicious websites. Some ZACCESS versions were also found bundled with other malware variants like FAKEAV.
What are rootkits?
ZACCESS variants are known for its use of rootkit technology. A rootkit is a program that specifically created to hide files, processes or registry entries on the system. This method is being abused by malware to hide their presence on the system and in order to gain administrator-level access to the system without being detected by the user.
Typically, a remote attacker may need to exploit a vulnerability or crack a password in order to install the rootkit onto the target machine. Successful installation of the rootkit enables a possible remote attacker to gain administrator-level access to a machine or network.
This type of malware is known to hide its routines or activities from affected systems. Such stealth routines allow attackers to use infected machines for their malicious schemes which include launching denial-of-service (DoS) attacks against other computers or servers, monitoring traffic and keystrokes, or escaping detection from antivirus software.
What are the noteworthy behavior of ZACCESS?
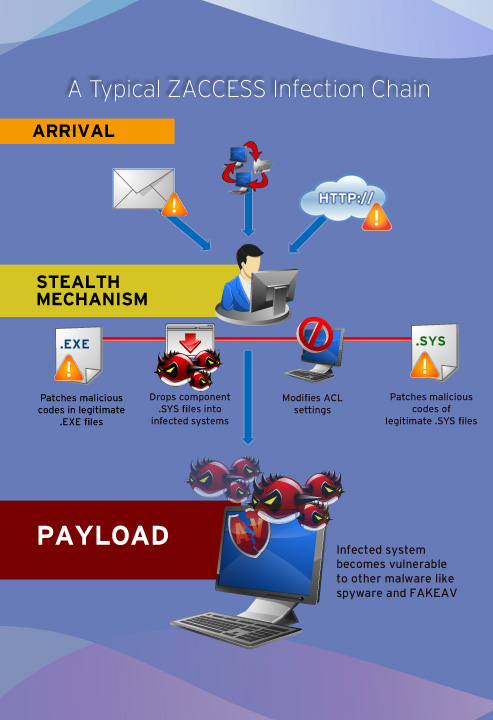
We have uncovered several ZACCESS variants with different stealth routines, but with the same motive to remain hidden. Below are some of these routines:
- Access control list (ACL) modifications. Certain SIREFEF variants like BKDR_ZACCESS.M change the ACL setting of terminated processes related to security software and forensic tools. This routine effectively prevents these programs to run, which enables the malware to remain undetected.
- .SYS file patcher/infection or overwrite. ZACCESS infects/modifies a random driver file (system) with ZACCESS code or overwrite a random driver with ZACCESS code in order to load its code into the system at every system startup.
- .SYS file dropper. The main ZACCESS variant drops a .SYS file in the system, which is the actual rootkit component of the malware.
- .EXE file patcher. For its rootkit routines, some ZACCESS variants modify legitimate .EXE files by adding its malicious code as part of its auto start mechanism.
What is different with newer ZACCESS variants?
We were able to detect ZACCESS variants that mainly patch legitimate executable files. We uncovered several services.exe files (Mal_Siref32 for 32-bit and Mal_Siref64 for 64 bit versions) that were patched by the malware BKDR_ZACCESS.SMQQ.
This backdoor is downloaded by BKDR_ZACCESS.KP, which is typically bundled with product keygen generators (keygen) applications or required codec for movie files downloaded from peer-to-peer (P2P) networks.
BKDR_ZACCESS.KP then drops BKDR_ZACCESS.SMQQ, which causes a user account control (UAC) notification to appear. This notification may discourage users to execute the file, which in turn foils the ZACCESS installation. To circumvent this, ZACCESS executes a binary planting technique. Specifically, it drops a non-malicious Adobe Flash installer (InstallerFlashPlayer.exe) and msimg32.dll in the user temporary folder. When InstallerFlashPlayer.exe is executed, Windows looks for the msimg32.dll in the temp folder before searching the Windows system folder. In this scenario, the dropped malicious msimg32.dll is executed instead of the original, clean one.
How does ZACCESS affect users?
Users with systems infected with ZACCESS and other malware that have rootkit components will have a difficult time removing the malware. To completely remove the malware from an infected machine, users need to determine and delete all of its component files. Failure to do so may result in continuous execution of the malware and its components.
Because it keeps itself under the radar, there is also a chance that the malware may have already performed its malicious routines prior to its discovery.
ZACCESS downloads other malware such as ZeuS/ZBOT, Spyeye and other malware that may perform more menacing routines like personal data theft. These typically include stealing login credentials and other personally identifiable information (PII) stored on the vulnerable system.
How can I protect myself from this threat?
There are various ways to protect against ZACCESS variants:
- Refrain from downloading pirated from P2P networks. Be cautious when downloading files from P2P networks and other sharing sites. Aside from being a potentially illegal activity, chances are the next movie you download may be bundled with a ZACCESS variant.
- Visit only trusted sites. Bookmark trusted and credible websites instead of typing in website URLs. Keep an eye on suspicious links especially those found in spammed messages, spim (spammed links in instant messages), or links in social networking sites.
- Keep admin privileges to a minimum. Ensure that programs use the lowest level of privileges necessary to complete a task. This minimizes the risk of letting malware take over the vulnerable system.
- Keep system up-to-date. Attackers typically exploit system vulnerabilities in order to install a rootkit malware. Thus, users must always keep their systems updated with the latest security patches released by software vendors like Microsoft, Adobe, Google, Apple and more.
Does Trend Micro protect users from this threat?
Trend Micro protects users from this threat via the Smart Protection Network™. In particular, the File Reputation Service detects and deletes ZACCESS variants. Web Reputation Services also effectively blocks access to websites hosting ZACCESS and its C&C servers.
Trend Micro Deep Discovery also protects users' networks by blocking malicious packets, such as C&C communication and uploading stolen information.