Gateways to Infection: Exploiting Software Vulnerabilities
Data de publicação: segunda-feira, 3 de setembro de 2012
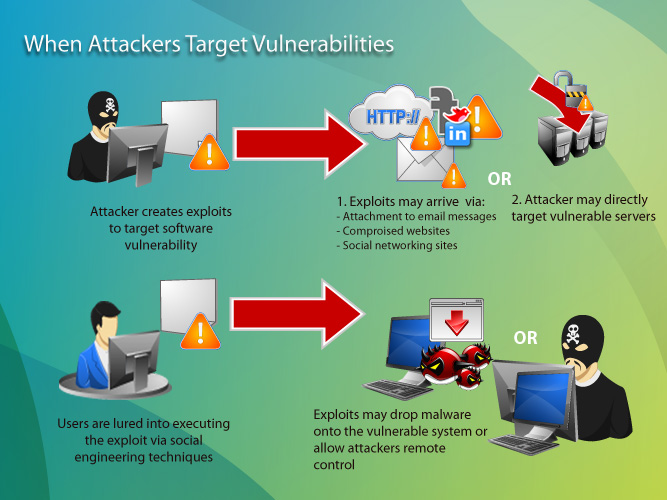
Software vulnerabilities, like the malware, have serious security implications. We recently reported about a Chinese high school Web page that exploited a vulnerability in Microsoft XML Core Services. Users who visited the Web page were at risk of downloading malware.
This incident, along with the slew of Blackhole exploit kit spam runs, an exploit in certain Adobe Flash Player versions and the zero-day exploit in Java 7, were just a few of the noteworthy threats that leveraged software vulnerabilities. Attackers continue to effectively exploit software vulnerabilities as most users do not regularly update their systems. It is important for users to know what vulnerabilities are, why these are being exploited, and how they affect a user's computing experience.
What is a software vulnerability?
A software vulnerability is a security flaw, glitch, or weakness found in software or in an operating system (OS) that can lead to security concerns. An example of a software flaw is a buffer overflow. This is when software becomes unresponsive or crashes when users open a file that may be "too heavy" for the program to read.
However, this commonly encountered error becomes a security concern when attackers uncover the vulnerability, conduct research about it, and create a malicious code or exploit that targets this glitch to launch their schemes. Some schemes may include gaining administrator privileges which gives attackers control over the vulnerable system or infecting it with malware.
Vulnerabilities are found in all software and OSs and are not limited to a particular software vendor. For 1Q 2012, Apple posted the highest number of reported vulnerabilities and also issued their largest number of patches during the same time period.
Users tend to not notice software vulnerabilities. An attacker may target one without the software showing any sign of an attack.
Attackers can also target vulnerabilities without user having to visit a malicious site or download an exploit such as attacks that target CVE-2012-2526 and CVE-2012-1852.
What is an exploit?
An exploit is a code purposely created by attackers to abuse or target a software vulnerability. This code is typically incorporated into malware. Once the exploit code is successfully executed, the malware drops a copy of itself into the vulnerable system.
In some cases, an exploit can be used as part of a multi-component attack. Instead using a malicious file, the exploit may instead drop another malware, which can include backdoor Trojans and spyware that can steal user information from the infected systems.
How did exploits evolve?
Exploits that target vulnerabilities have evolved through the years. Cybercriminals began to incorporate vulnerabilities in their attacks since the success of Blaster worm in 2003. Below are the highlights of exploits and vulnerabilities in the threat landscape:
| Time Period | Highlights |
| 2006 and earlier |
|
| 2007 |
|
| 2008 |
|
| 2009 onwards |
|
What are security updates?
Software vendors are aware of these security vulnerabilities and regularly release security updates to address these flaws. Software vendors such as Microsoft, Adobe, Oracle, Firefox, and Apple are just some software vendors with regular releases security updates. In particular, Microsoft regularly releases updates with a security bulletin every second Tuesday of the month, known as “Patch Tuesday”. Once the Patch Tuesday bulletin goes live, users are expected to update their systems.
Why should I patch?
Updating systems with the latest security patches protects against attacks that exploit vulnerabilities.
Systems with outdated security patches face the risk of malware attacks that use software exploit. A successful exploit may lead to immediate malware infection or remote users gaining control over infected systems. These malware may include Trojans that perform malicious routines into the system. Such malware also includes backdoors that can communicate with a remote user, and spyware that can steal online banking credentials and personally identifiable information (PII) from the infected system.
Applying security updates also addresses technical glitches to improve the software’s performance.Until systems are updated, computers remain open to threats that abuse vulnerabilities. Unfortunately, not all users are keen on applying these updates.
Other vendors, such as Google Chrome and Flash are also known to release updates automatically and invisible to users.
Why don’t users patch?
Despite its benefits, not all users regularly update their systems with the latest security releases. Last year, a CSIS study reveals that 37% of users still browse the web with unsecure Java versions. Users are also not likely to patch third-party applications as 66% of users do not regularly update these apps.
A Skype survey revealed that 40% American, German, and British users don’t immediately apply security updates when prompted. The report also reveals the following reasons why users do not readily update their software:
- “I’m worried about computer security, so I don’t download everything I’m prompted to.”
- “There is no real benefit to me.”
- “Updates take too long.”
- “I don’t understand what these updates will do.”
Which threats take advantage of vulnerabilities?
Here are some examples of threats that typically target software vulnerabilities to successfully infect systems:
Blackhole exploit kit. These attacks typically arrive via email and usually mimic well-known organizations. The message contains a link to a compromised website that redirects users to a malicious website or landing page. This page then attempts to exploit vulnerabilities in the system. If successfully exploited, it downloads data-stealing malware variants like ZeuS or Cridex. The high amount of legitimate-looking email related to the Blackhole exploit kit is a reason why this poses a noteworthy threat.
Attacks using old, but reliable vulnerabilities. Instead of exploring new security flaws to target, potential attackers may also rely on previously reported vulnerabilities to successfully infect their targets.We already wrote about attacks that continue to use MS-2010-3333, a vulnerability reported and patched two years ago. This shows that such vulnerabilities still work and users do not regularly updating their systems.
Old but reliable vulnerabilities were also targeted by Flame, an attack that has drawn comparison to STUXNET. Flame was even dubbed the “most sophisticated malware” by some security researchers. This attack particularly targeted MS10-061 via rule and MS10-046, which Trend Micro already covered in 2010.
Vulnerabilities in mobile apps. With everyone going mobile, it was only a matter of time before attackers hit the mobile platform by exploiting the OS and apps. One of the earliest threats we saw that targeted iOS was the jailbreaking tool JailbreakMe, which uses a malicious .PDF file or TROJ_PIDIEF.HLA to exploit a vulnerability in Safari. Apple has already provided a patch to the said software flaw.
Android-based mobile devices were not spared. Last year, the Chinese telecom company ZTE acknowledged a vulnerability in their M Score mobile devices. If exploited, it allows a remote attacker to gain root privileges which grants remote attackers complete control over the vulnerable devices.
Android apps were also fair game. A spam run made the rounds through a compromised Android-based device. This may have been caused by attackers taking advantage of a vulnerability in the Yahoo! Mail Android app. The real cause of the spam run was undetermined; however, we were able to reveal a vulnerability in the app that can possibly lead to spamming users with an Android-based device.
What are zero-day exploits?
Zero-day exploits are known to target unpatched software flaws.
In this scenario, attackers are able to identify a flaw that is not yet known or covered by vendors. An example of this was the DUQU threat in the Middle East, which was dubbed as the next STUXNET. Based on analysis, the attackers behind DUQU used a .DOC file that exploits a previously unpatched vulnerability in Microsoft Word to drop either RTKT_DUQU.B or TROJ_DUQU.B onto the affected system.
Its effect to users can be serious. Given that security updates are not yet available, even updated systems are exposed to such attacks. To combat these, vendors may release a solution before scheduled release or offer a workaround solution.
How can I stay protected from attacks that use exploits?
The first step to staying protected is to apply the latest security patches provided by the software vendor. This provides protection against exploits and web threats that abuse the software vulnerability as an infection vector.
Users may sometimes be hesitant in downloading these security updates as these may take up a large amount of time. However, applying patches guarantees protection against exploits. Users are also recommended to turn on automatic software updates.
For zero-day attacks, users are advised to refer to the software vendor for security bulletins. Typically, software vendors provide workaround solutions or tools to address these flaws until they are able to release an official update.
Users should avoid visiting untrusted sites or opening links in spammed messages. When browsing websites, users should instead bookmark reputable websites and refrain from opening email from unknown sources.
How does Trend Micro protect users from such attacks?
Trend Micro Smart Protection Network™ protects users from exploits and malware that take advantage of these software vulnerabilities. Trend Micro users need not worry as they are protected from this threat. An NSS Labs study shows that Trend Micro successfully blocks threats delivered via HTTP and HTTPS. Trend Micro™ Titanium™ Security effectively detects fresh exploits, including zero-day exploits.
FROM THE FIELD: Experts' Insight
"Attackers would rather use old reliable exploits such as CVE-2010-3333 that are proven to work instead of experimenting with new, but unreliable exploits." - Ryan Flores, senior threat researcher
"Attacks were successful because a high percentage of users still used unpatched versions of vulnerable software." - Pawan Kinger, vulnerability research manager