New Zeus Gameover Employs DGA and Fast Flux Techniques
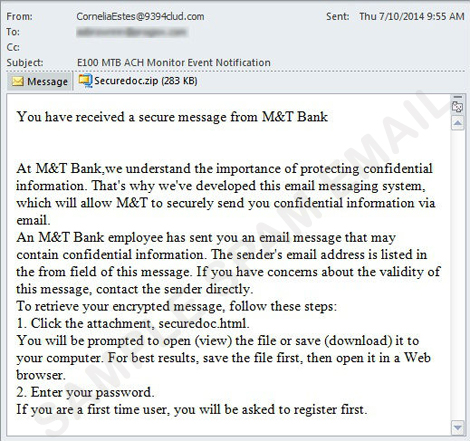
After the reported takedown last month, Gameover ZeuS resurfaced once again as seen in spam campaigns that seem to be bank-related emails. These spam mails purport to come from legitimate companies like M&T bank and Natwest. In one of the spam samples we spotted, the message informs users that they’re sending their personal information via email to maintain confidentiality. It then urges them to open the attached .ZIP file supposedly containing their data. However, once users open the attachment, they will download a GoZ malware detected as TSPY_ZBOT.YUYAQ.

Gameover ZeuS is known for employing peer-to-peer functionality for its command-and-control. However, this specific variant (TSPY_ZBOT.YUYAQ) uses both Domain Generation Algorithm (DGA) and a 'fast flux' tactic to mask its C&C servers.
Trend Micro advises users to verify first if the email message they received is really legitimate or not even though it came from seemingly known sources. It is also best to exercise caution to avoid system infection and data theft.
- Versão do mecan
- Patrón TMASE: 0810