EMOTET Returns With New Spam Campaign
Data de publicação: 15 março 2023
After months of hiatus, the notorious malware EMOTET has resumed its spam operations with a mixture of old and new techniques.
Discovered in 2014, EMOTET began as a banking trojan that steals victims' credentials and information. Over the years, it has evolved into one of the most widely spread malware in the world gaining initial access to networks some of which led to ransomware infections.
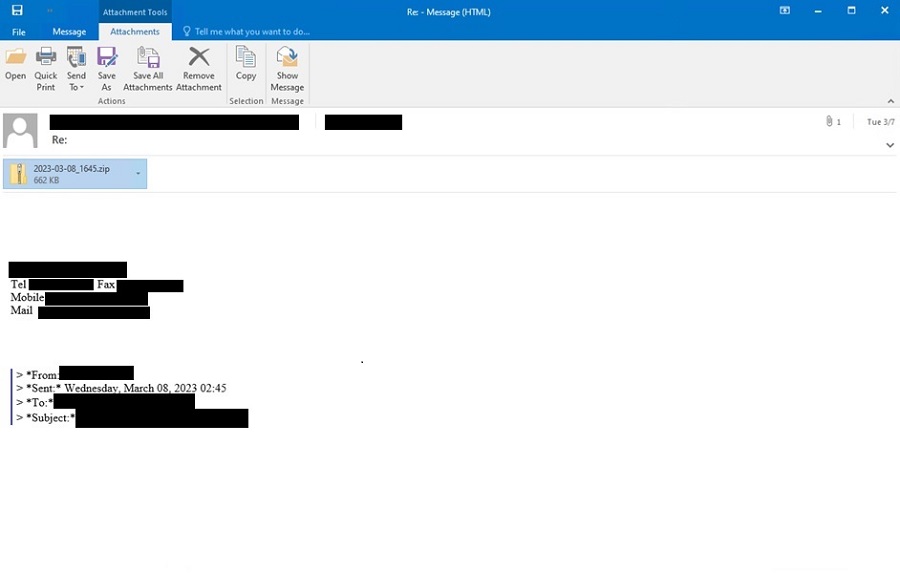
Early this March, we observed a spike of EMOTET malspam targeting recipients using ZIP files that contain Word documents with malicious macro. The email sample exhibits thread hijacking, a characteristic common to other EMOTET spam attacks since one of the capabilities of this malware is stealing email data from its infected victims.
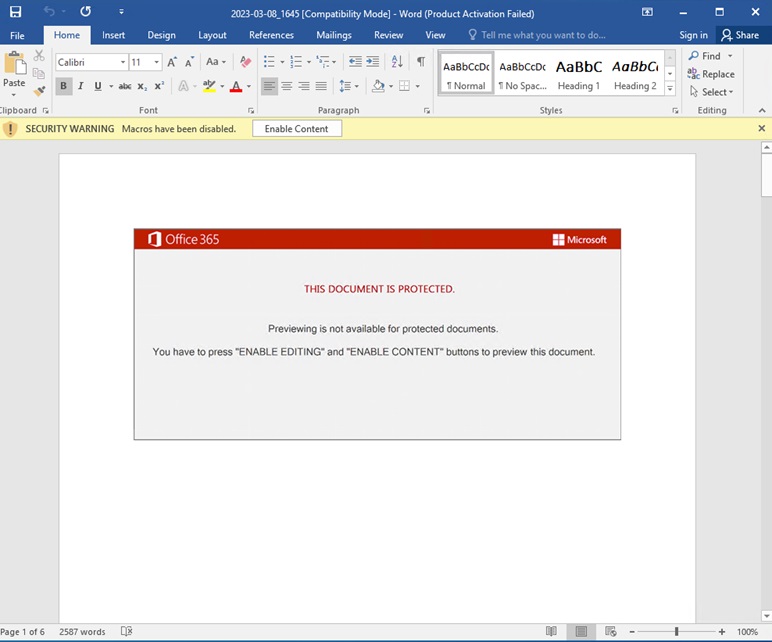
This wave of EMOTET spam is particularly notable for using padded Word documents to evade most gateway defenses. While the initial ZIP attachment is no more than 700KB in size, this contains a padded Word document that can reach more than 500MB of file size once uncompressed. When opened, the Word document uses EMOTET's old reliable Red Dawn template that tricks victims into enabling content and allowing macros to execute its malicious code. The macro will then download a DLL that Trend Micro detects as TrojanSpy.Win64.EMOTET.SMA.
Spam emails in this campaign are also detected by Trend Micro Email Security Solutions. Furthermore, we recommend users to be cautious of email messages with threads they are not familiar with, one of the ways EMOTET lures its targets, and open any attachments or click any links that come with these emails.

Data/Hora do bloqueio de spam: 15 março 2023 GMT-8
TMASE
- Versão do mecan
- Patrón TMASE: 2.7506.000