Fake invoice email with Html attachment spreads Locky ransomware
September 09, 2017
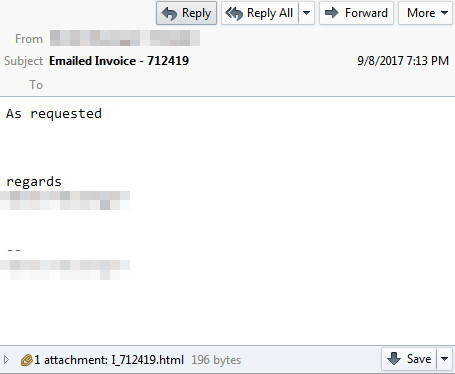
An email with the subject 'Emailed Invoice - [random_number]' using a random name claiming to be from the recipients domain is spreading Locky ransomware.
The spam campaign uses a new technique to deliver ransomware through an attached html file. When the html file is clicked, it displays a page that says 'Your file is downloading. Please wait...' and will download a malicious executable file.
Given that most ransomware is spread via spam, Trend Micro users are shielded from these kinds of attack. Spam filtering and gateway solutions prevent emails with malicious attachments from making their way into the user's inbox.
SPAM BLOCKING DATE / TIME: September 09, 2017 GMT-8
TMASE INFO
- ENGINE:
- PATTERN:3318
