Ransomware Recap: Erebus Makes a Splash
The re-emergence of an Erebus ransomware variant last week became the latest high-profile ransomware attack after WannaCry. Detected by Trend Micro as RANSOM_ELFEREBUS.A, Erebus hit South Korean web hosting company NAYANA, affecting 3,400 business websites it hosts.
NAYANA posted a notice on its website on June 12, stating that the attackers demanded a ransom of 550 Bitcoins (BTC) or US$1.62 million, in exchange for the necessary decrypt keys. In an update on June 14, NAYANA negotiated a payment of 397.6 BTC (around $1.01 million as of June 19, 2017) to be paid in installments.
Erebus infected NAYANA’s Linux servers, and uses a fake Bluetooth service as part of its persistence mechanisms to make sure that the ransomware is executed even after the system or server is rebooted. It also employs UNIX cron—a utility in Unix-like operating systems that schedules jobs via commands or shell scripts—to check hourly if the ransomware is running.
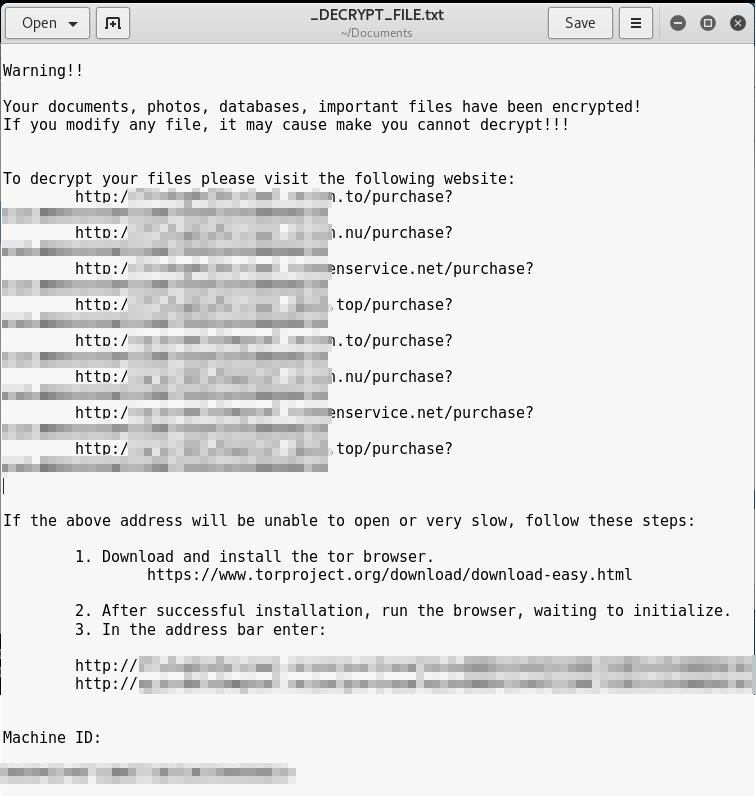
Figure 1. Erebus ransom note
CryptoSpider and WinUpdatesDisabler
Hidden Tear variants are still very much alive the past week with CryptoSpider (detected by Trend Micro as Ransom_HiddenTearCSPIDER.A) and WinUpdatesDisabler (Ransom_HiddenTearWUPDIS.A).
CryptoSpider is a ransomware variant that looks to be under development. Lacking the sophisticated elements of its predecessors, the lock screen of the Hidden Tear variant does not demand any ransom from its victims. Instead, it only informs them that they have been hacked by a certain ./Mr-Ghost-C47.

Meanwhile, WinUpdatesDisabler was discovered in the wild asking victims to pay an unspecified amount in exchange for a decrypt key. Arriving as a Win32.exe file, its ransom note uses Bosnian language to convey its demand. It encrypts a variety of file types including Microsoft Office documents, as well as various audio and video file formats.
Here are other notable ransomware stories that have surfaced:
CA$HOUT Ransomware
Still under development, the CA$HOUT Ransomware (detected by Trend Micro as Ransom_CASHOUT.A) is a new variant that was discovered in a malfunctioning state. Its ransom note demands a ransom of US$100 in exchange for a decrypt key.
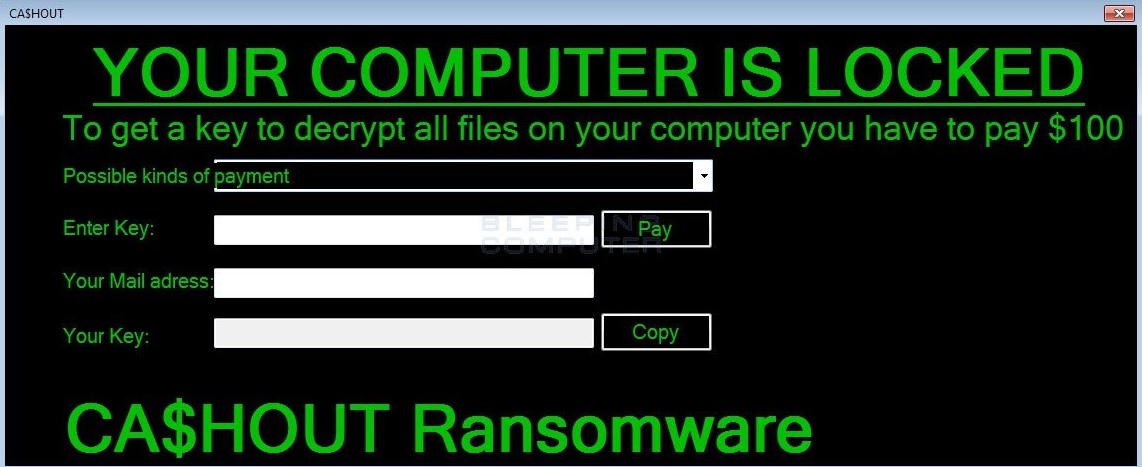
Figure 3. CA$HOUT Ransomware ransom note
MacRansom
Detected by Trend Micro as Ransom_PROTONOSX, MacRansom is believed to be the first MacOS Ransomware-as-a-Service (RaaS). Using symmetric encryption with a hardcoded key, the ransomware asks victims to pay 0.25 BTC (US$700) in exchange for a decryptor. If payment is not made within seven days, MacRansom threatens to delete the decrypt key for the encrypted files–causing the affected files to remain encrypted permanently.
MacRansom targets files larger than eight bytes found in the active account of an infected endpoint. However, the probability of future variants that use a different behavior to target files would depend on the specifications provided to the seller.
Virus Ransomware
Virus Ransomware (detected by Trend Micro as Ransom_UCRAZY.A) is a malware that does not encrypt files. What it does is it flash annoying message boxes, and uses a My Little Pony character on a note that asks for $300 BTC from users despite its inability to hostage files.
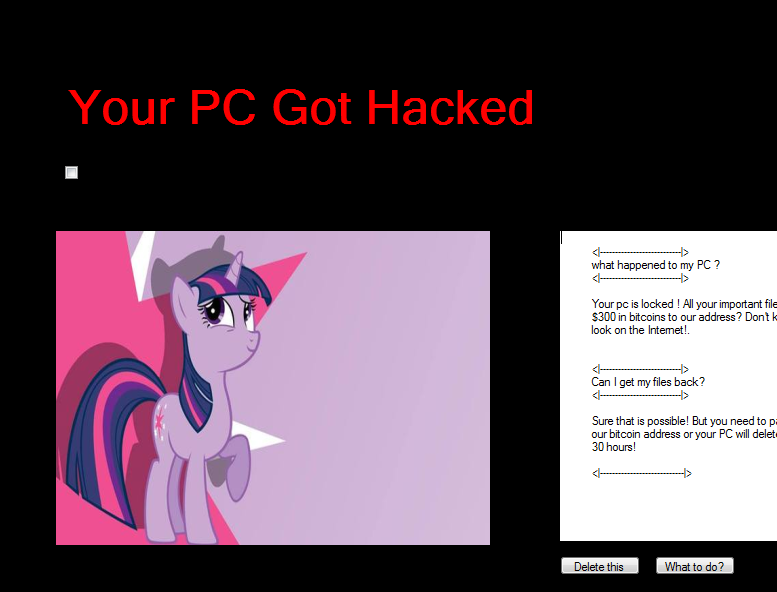
Figure 4. Virus Ransomware lock screen
Although some of the ransomware variants that emerged the past week appeared to have less damaging effects on its victims, users and organizations have to stay vigilant and make security a priority especially against more dangerous threats like Erebus. Its re-emergence should remind IT and system administrators not to overlook the importance of securing the servers and systems that power business processes. The possible damage to an enterprise’s operations, reputation, and bottom line could multiply if the security posture of servers and systems is not strengthened.
Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers—whether physical, virtual, or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Postagens recentes
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks