Deceptive Content Ahead: Google Now Warns Against Social Engineering Content
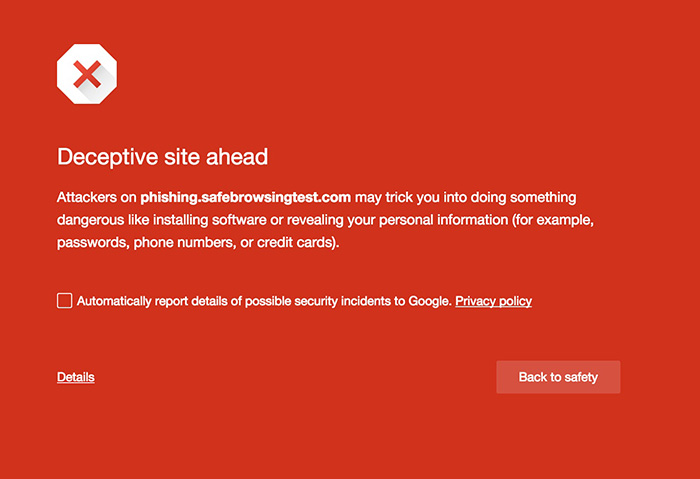
Following Google’s step towards promoting a safer web browsing experience in November of 2015, the reach of its advocacy now extends to defending against deceptive embedded content, the company shared in a security bulletin posted on Wednesday.
For over eight years, Safe Browsing has been in place as a defensive wall against bad actors, commonly against traditional phishing schemes or those that make users unknowingly download faulty software or expose sensitive data like phone numbers, passwords, and even credit card credentials. Before 2015 ended, Google reinforced web protection by policing social engineering ploys that has since succeeded in luring users into becoming unwitting victims to cybercrime. Such tactics have been a common route used by cybercriminals to victimize the web-using public.
Google’s recent announcement strengthens Safe Browsing protection by putting an extra layer of defense against dangerous embedded content masquerading as legitimate content. In the past, there’s a high chance that a user would be tricked to click on a deceptive download button, an infected image ad or a fake reminder that warns of an outdated system. Normally, as it is appears to originate from a trusted source, a user would be prompted to click “update”.
As Google expands its protection, such deceptive content will be flagged as social engineering when they attempt to pose as a legitimate entity—by imitating a site's look and feel—to trick users into doing something a trusted entity would ask like keying in a password or contacting customer support.
According to Google, “Our fight against unwanted software and social engineering is still just beginning. We'll continue to improve Google's Safe Browsing protection to help more people stay safe online.”
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Postagens recentes
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks