 Download A Security Analysis of the Data Distribution Service (DDS) Protocol
Download A Security Analysis of the Data Distribution Service (DDS) Protocol
The Data Distribution Service (DDS) drives thousands of systems every day as a middleware for machine-to-machine communication. This technology ensures interoperability and fault-tolerance of public and private devices such as healthcare, railways, and automation systems, to robotics, spacecraft, and military machines, with growing usage as it responds to embedded systems’ and applications’ real-time requirements.
In a collaborative study, our research “A Security Analysis of the Data Distribution Service (DDS) Protocol” looked at the security posture of DDS as a critical software component of industries’ supply chains. We identified 13 new vulnerabilities from the six most commonly used implementations and one security gap in the standard’s specifications. This is in addition to other deployment issues in the DDS ecosystem that malicious actors could use for other illicit activities such as data theft and cyberespionage.
Our research identified some of the critical industries that can potentially be affected in a compromise of the DDS protocol and their respective use cases. We also provide a summary of our research findings, as well as some short- and long-term mitigation procedures.
DDS applications and affected sectors
DDS and real-time publish-subscribe (RTPS) packets are used for mission-critical applications, connecting embedded systems as a reliable communication layer between sensors, controllers, and actuators. Situated at the beginning of the supply chain, developers and teams responsible for maintaining DDS can easily lose track of it, making this critical library an attractive target for attackers.
Telecommunications and networks
This sector uses DDS to function and optimize communication between network equipment such as optical transponders, which are components that provide the foundation for 5G mobile transport. The system for configuring settings, monitoring the equipment, and deploying updates are also built and distributed using DDS. The service is also being tested for software-defined networking (SDN) technologies for integration in next-generation networking control planes.
Virtualization and cloud
DDS in data centers and virtualization span from high-level use of software to low-level enhancements. From managing virtual and machine units for efficient data exchange to improving how virtual machines (VMs) and computing cores communicate with each other, DDS is seen as the ideal choice for its built-in or add-on integration capabilities. Counting on its capability to multicast for discovery, DDS can be used across distributed networks to create the appearance of a uniform DDS-based network.
Healthcare
DDS is used by companies and healthcare stakeholders to enable interoperable data connectivity for medical devices and clinical systems. Examples of these DDS use cases include healthcare institutions in different countries with a command center software to process real-time needs, and facilitation of medical devices for hospital patients’ safety and integration of clinical decision systems such as computers and medical tablets.
Energy
Climate change and the challenges it poses are driving significant innovation and changes in the sector due to emerging industrial internet of things (IIoT) solutions. Problem areas are being solved with the use of available technologies, and DDS is being adopted by both states and companies for research and implementation in applications and programs for power generation, storage and management, and distribution and control.
Defense
DDS’ typical usage in the defense sector include navigation systems, weaponry and management, command and control (C&C) systems, and radar. Some agencies such as the National Aeronautics and Space Administration’s (NASA) launch control system uses DDS in its supervisory control and data acquisition (SCADA) systems.
Summary of findings
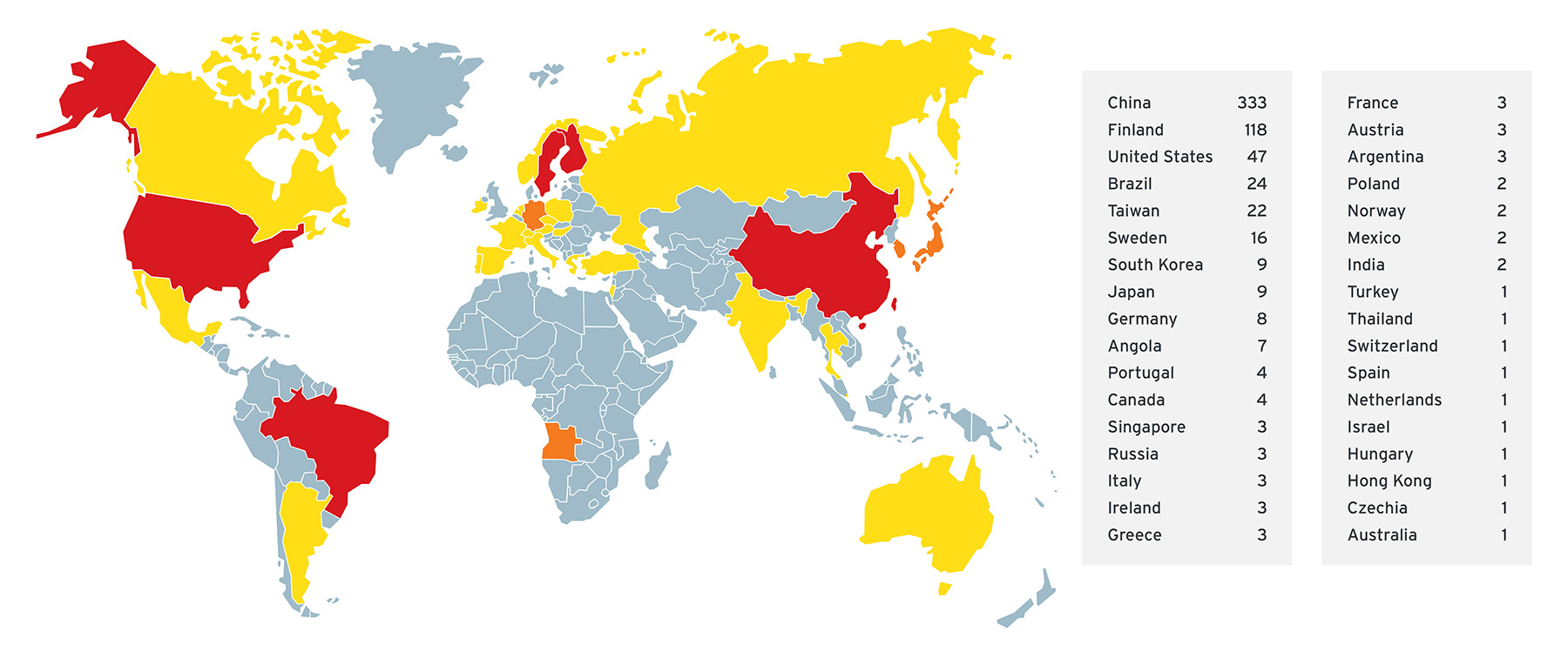
Despite its versatility and several studies in the past documenting its security and infrastructure, a significant percentage of practitioners in the industries in which it is used are unaware of DDS functions and uses. It is also because of its ubiquity that we analyzed this technology and found more than 600 identifiable public-facing DDS services in 34 countries. These exposed services affect 100 organizations via 89 different internet service providers (ISPs). During the course of studying distinct DDS vendors, 202 were leaking private IP addresses and seven secret URLs. Some of the IP addresses exposed unpatched or old versions of DDS implementation, which are affected by some of the vulnerabilities we discovered and disclosed in November 2021.
Figure 1. We found exposed DDS systems in 34 countries, including vulnerable ones, identified via distinct IPs leaking data
A Security Analysis of the Data Distribution Service Protocol
Mitigation and best practices
A look at the some of the industries involved and the usage of DDS in the supply chain of these critical sectors shows that patching will not always be as easy, available, or even possible. In the short term, companies and teams are advised to never expose a DDS endpoint unless necessary and equipped with DDS Security in every instance of exposure. Ensure protection solutions that can deploy updates and rules to spot malicious packets, as well as endpoint solutions that can be configured to detect anomalous files. In the long term, we recommend supply-chain management processes implementation to ensure critical components such as DDS libraries are constantly tracked, monitored, and automated for continuous security testing.
Download and read our full report to get the details of our research, “A Security Analysis of the Data Distribution Service (DDS) Protocol.”
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks