
While transitioning from regular factories to smart factories, the gap in awareness between information technology (IT) and operational technology (OT) security measures is one of the most crucial challenges to overcome. In this blog, we will take a look at the threat of ransomware. It will be used as an example to look at the current state of cyberattacks that significantly impact the stability of connected factory operations, as well as effective security measures that can be practiced.
Smart Factory Security Series Part 1: Contemplating the impact of inadequate cybersecurity on factories
Smart Factory Security Series Part 2: Three courses of action for future factory security that management should know
Ransomware that inflicts severe damage on corporate IT systems
Ransomware is indiscriminate on its targets. It is a type of that infects smartphones, tablets, computers, and servers to render the device inaccessible by locking the screen or encrypting its files. In order to regain access, the user must pay up.
Ransomware began to appear in earnest in Japan around 2013 and the first Japanese language ransomware was confirmed in 2014.
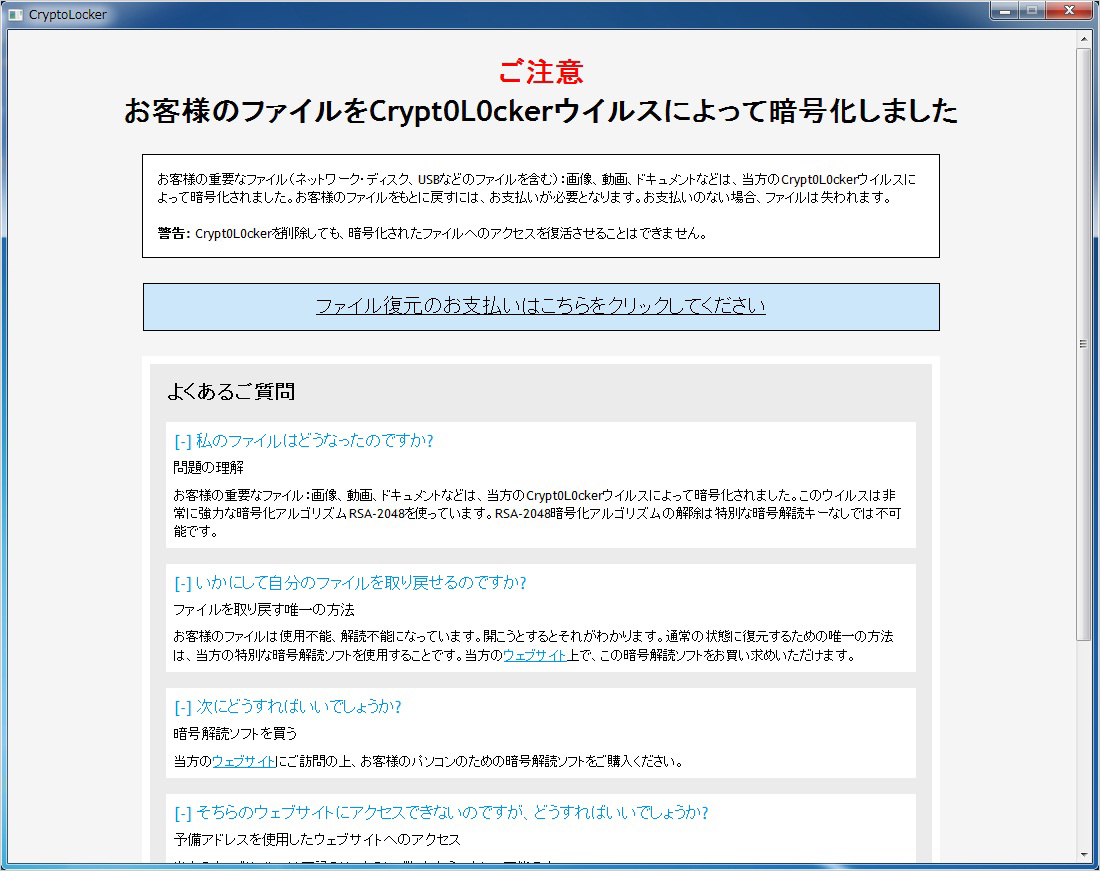
Once infected by ransomware, the device may become inoperable or important business files, such as text documents, spreadsheets, images, and databases may be encrypted. In many cases, victims are forced to recover through backups or reset the device to the default settings. Even if the user gives in and pays the ransom, there is no guarantee that the files will be recovered. The user may even become target for further attacks, or the information the user provided to make the payment could be used for malicious purposes. As a result, such actions may inflict significant damage to system operations and adversely impact businesses.
In 2016, a record-breaking increase of ransomware was confirmed worldwide. Damage from ransomware?the number of devices from which they were detected on, as well as the number of reported cases were the highest ever in Japan . Cybercriminals are increasingly and actively using ransomware in their moneymaking schemes.
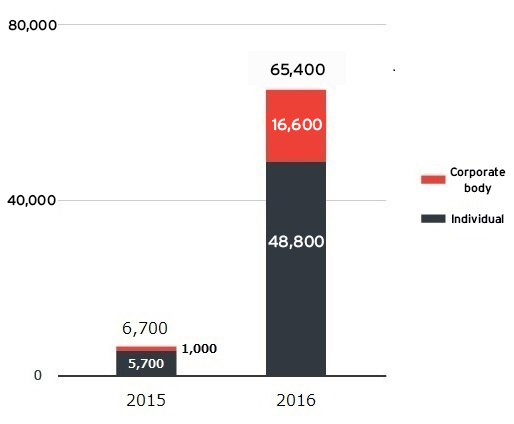
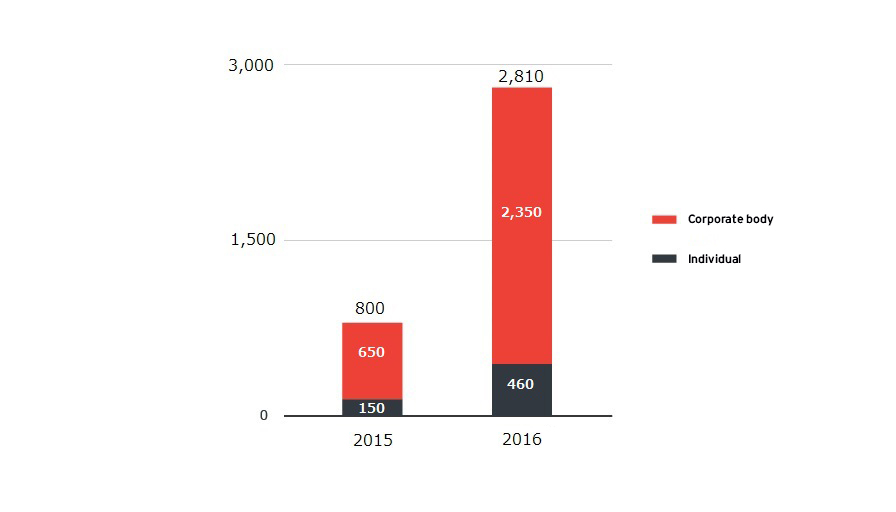
As indicated in Figure 3, which illustrates the reported cases of ransomware, the threat is especially severe for enterprises.
An investigation was conducted by Trend Micro involving 534 people who make IT-related decisions in enterprises and organizations, as well as those who are involved in the process. The results showed that 25.1% (134 people) of them have experienced ransomware attacks at their workplace, and it was confirmed that approximately one out of every four companies was attacked by ransomware.
Ransomware seen to affect enterprise systems have been around since 2015. Ransomware that target enterprises not only encrypt infected devices but also all the drives mounted on the device. It can also search for shared folders on the network and encrypt those files as well. There has also been a ransomware that destroys backups on servers and infiltrates the organization's network similar to a typical targeted attack.
It is also necessary to understand the ransomware's infection vectors. Ransomware mainly uses emails and URLs to attempt infection. According to the Trend Micro roundup, among all the ransomware detected in 2016, nearly 80% was accounted to emails. Most of these were random attacks to unspecified targets, however, no matter how limited, several cases of attacks in the country were specialized; in other words, they were targeted toward specific enterprise entities.
The confirmed targeted email attacks shared several common traits, such as using an email written in Japanese that targeted only a limited number of enterprise users, not directly attaching the malware to the email but tricking the receivers into downloading them from cloud storage, and the fact that the ransomware being used were ones still unidentified in Japan. This raises concerns that targeted ransomware attacks will be more common from now on.
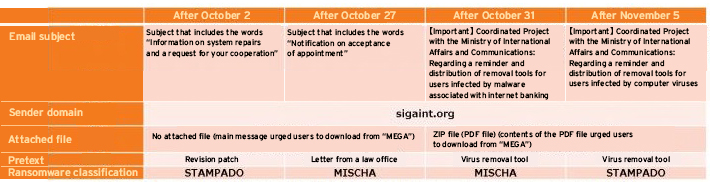

On the other hand, web-related ransomware infection happens when cybercriminals lure users to tampered-with legitimate websites run by enterprises and organizations, or they abuse web advertisements to display malicious advertisements. If the user's device is not appropriately patched if this happens, such attacks can exploit vulnerabilities and infect the device with ransomware even if the user was only browsing through the website.
How ransomware infection occurs through malicious advertisements. Trend Micro Official YouTube Channel.
Ransomware's threat to factories
What happens if a factory's control system gets infected with ransomware? If, for example, production data were to be encrypted at a pharmaceutical factory or a food plant, production will be forced to halt. In a parts manufacturing factory, the instant a control panel were to be locked, monitoring productions lines would be impossible; as a result, the lines will have to be stopped. Furthermore, if backups were not made or recovery methods were not established, recovery would take a long time and would result in a long-term production downtime.
Unfortunately, these ransomware threats to factories are already a reality. There have been reports, such as the case of a Brazilian furniture factory, where ransomware infected the human machine interface (HMI) installed in the factory and forced all operations to cease for 15 days until being restored. Another case occurred at a Brazilian electrical company where ransomware infected the HMI via a USB drive, which then continued to spread and infect multiple monitoring servers on the network.
The gap between IT and OT cybersecurity in factories that we discussed in the previous blog also raises the risk of ransomware threats. Are emails, which are a major infection vector, also plausible to make their way on the factory's network as well? Are work networks and factory networks even clearly separated in the first place? Even if the networks are isolated, there is a chance to input and collect information from the control network. Additionally, ransomware that spread via USB drives also exist
Once a system has been implemented, factories often use it for a longer period than most regular IT systems, sometimes continuing to use it even after the operating system (OS) has reached its end-of-life. Vulnerability attack tools (exploit kits) used to spread ransomware utilize attack codes aimed at vulnerabilities in the OS, browser, and software. If the OS has been updated to its latest version, damage inflicted from exploited vulnerability will be significantly reduced. However, if an OS which support has already reached its end-of-life is continued to be used, the risk of being infected with ransomware through vulnerability exploitation is further increased.
Additionally, it is necessary to be aware of new risks that come with making a factory IoT-compatible. According to the Trend Micro 2016 roundup, vulnerabilities involving Supervisory Control And Data Acquisition (SCADA), such as Advantech's WebAccess, increased by 421%. As network connections further develop in factories, there are concerns that cyberattacks targeting vulnerabilities in control systems will occur more in the future.
Security measures for smart factories
Here are three security measures necessary to counter cyberattacks, including ransomware, in factories.
1. Prior preparation
In order to minimize downtime caused by system changes due to attacks from ransomware and other malware, it is best to acquire a secure system backup. Consider multiple backups and recovery methods for the whole system, different data, and so on. Additionally, create a procedure for restoration and conduct actual tests so that the labor required to restore systems can be minimized depending on the situation.
Setting up a structure that separates IT networks from the factory's control network is also an effective way to prevent malware from entering the control network. That being said, the development of IoT factories depends on establishing a connection between the control network and external networks. For this, it is crucial to make sure the structure is not set up where individual systems have different connection ports. Instead, make sure that the one connection point where all the systems are gathered is set up with appropriate security in place. In addition, even if networks are separated in the original plan, conduct regular checks to make sure the structure has not been changed without being noticed due to onsite operational changes.
2. Countermeasures
As seen in targeted cyberattack methods, recent malware use sophisticated and complex attacks that are split into stages. In order to prevent these attacks, it is crucial to set up multiple layers of defense. Specifically, consider applying multi-layered defenses for all points of a control system. Even if malware were to slip past the entry point defense, it is possible to prevent it from spreading within the system or establishing external communications and conducting final malicious activities.
Defense at the entry points
- Detect and block malware on the file exchange server in the demilitarized zone (DMZ), which serves as a connector to external networks.
- Detect and block malware in USB drives and brought-in PCs that will be used in the control network.
Internal defense
- Take measures to counter device vulnerabilities by updating programs, or as an alternative method, utilize virtual patching.
- In the case of newly established facilities and the like, implement lockdown-type measures to control devices that hinder programs, except for those intended in advance to execute. This will prevent unauthorized files, including malware, from running.
- Conduct regular inspections on devices using malware detection tools that do not require installation.
- Detect and block the behavior of a malware trying to spread to other devices or servers on the network by visualizing internal communications.
Defense at the exit points
- Detect and block a malware's external communication as it attempts to download other malware from external sources, or tries to acquire further information (e.g. encryption keys from malicious web servers so the ransomware can encrypt files) in order to perform malicious activities.
3. Information-sharing with the IT department
It is also important to receive support from the IT department, which handles Internet threats. In particular, acquiring information on the latest IT threat trends, and promoting employee IT security education will particularly help prevent damage caused by trickery that exploits human vulnerabilities. This includes phishing attacks and the distribution of ransomware disguised as updates for specific control software.

