Cyberbedrohungen
Factory security 1: Impact of poor cybersecurity
Through internet of things (IoT), traditional factories are transforming into smart factories. Part one of the 3-part series explains cybersecurity threats in factories and the necessity of establishing suitable countermeasures.

Through internet of things (IoT), traditional factories are becoming smart factories. Cybersecurity threats in factories and the necessity of establishing countermeasures will be explained in two parts. This first part explains cybersecurity threats in factories and the necessity of establishing suitable countermeasures.
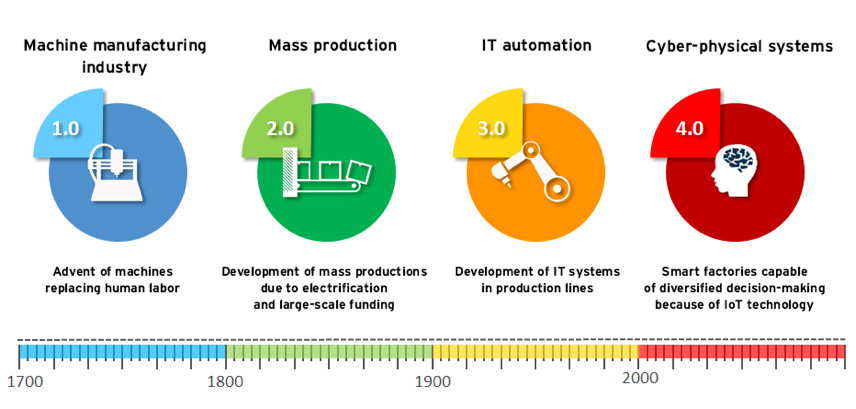
Smart factories brought by the Fourth Industrial Revolution
The term "Industry 4.0" that originated from Germany is not a new concept. This movement, also called the Fourth Industrial Revolution, began as a German national policy. However, in the US, the same line of thinking has been producing smart factories under the name of Industrial Internet.
Until the end of the 20th century, production was automated as a result of the Third Industrial Revolution. Now, the Fourth Industrial Revolution utilizes IT and IoT technologies across a broad range, striving to realize a connected factory, the smart factory.
By handling the machineries that were not managed in the past by IoT technology, smart factories enable the conditions of machines in the factory to be uniformly monitored in real-time. This enables the factory as a whole to run efficiently, which in turn creates an environment that produces maximum profits.
One of the challenges for smart factories is cybersecurity
In smart factories, the system (which was previously in a closed network environment) is connected to other systems, machineries, and networks. Additionally, as standardization continues, the use of open networks is expected to increase. This shift poses a significant challenge to security.
Factories were previously run using a closed network with no external connections. The consensus was that they were sufficiently secure. As such, security measures, particularly within factories, remained mostly underdeveloped. In addition, when it comes to actually rolling out countermeasures, the financial and operational aspects are far from trivial matters, and are believed to be one of the reasons for creating a high hurdle.
Security incidents in factories
So were there no security problems in factories until now?
ICS-CERT in the United States releases security incident reports in the Industrial Control System (ICS) field and they show that the number of reported incidents on critical infrastructures is increasing annually.

Source: ICS-CERT https://ics-cert.us-cert.gov/Other-Reports
Do note that the data presented here only comes from reported security incidents. Considering those that have yet to be reported, it is believed that the actual number of victims is even higher.
Source: ICS-CERT https://ics-cert.us-cert.gov/sites/default/files/Annual_Reports/Year_in_Review_FY2015_Final_S508C.pdf
Source: ICS-CERT https://ics-cert.us-cert.gov/sites/default/files/Annual_Reports/Year_in_Review_FY2015_Final_S508C.pdf
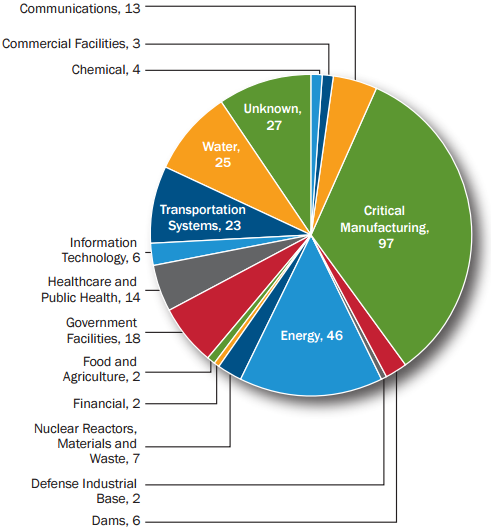
Figure 3 illustrates the number of reported incidents by sector. A large percentage of security incidents are in the manufacturing- and energy-related sectors; however, it is clear that incidents have occurred across a wide range of sectors.
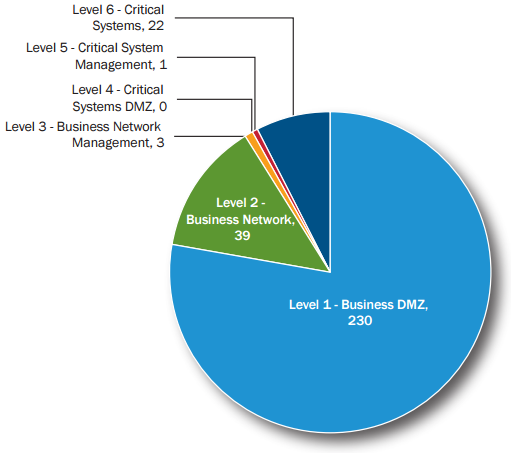
Figure 4 illustrates the systems attacked, divided into levels. In most cases, the attacks were discovered in demilitarized zones (DMZ) or office networks, where the damages had low impact and were deemed level 1. However, it is worth noting that 22% of security incidents (level 6) occurred in the most critical internal system.
These damages include cases in which malware infiltrated the factory by accident. But there have also been a number of reported cases that systems within a factory were intentionally targeted. For example, the media has reported on significant damages caused by STUXNET in 2014, and attacks on a German iron mill in the same year.
As these reports show, it is necessary to regard security threats to factories as something that is currently happening. According to a Trend Micro research, 23.1% of manufacturers reported that they had experienced a security incident in their manufacturing and production environments between January 2015 and June 2016.
How should the need for security measures be approached?
In the cases Trend Micro studied, it was revealed that many of the computers involved were using old operating systems, since they were still functional and would only be changed unless necessary. It was also revealed that in many cases, information system departments were not involved with machinery in factories. As a result, it was confirmed that vulnerable systems were being used without the requisite security measures.
If measures were not applied and a security incident similar to the examples mentioned above were to occur, a factory's entire operations could come to a halt and result to serious damages to the business. It is important to recognize that if no security measures are taken, it will take a significant amount of time to recover from such incidents. In addition to recovery costs, the losses suffered during the downtime may also increase.
Predictive maintenance will be further developed in smart factories with the implementation of the IoT. However, just as the conditions of machinery equipment must be monitored and problems be prevented in advance, security measures must also be prepared ahead to prevent security incidents.
The necessity of security measures from a business continuity plan (BCP) perspective
As a traditional factory transitions into a smart one, many of its machines will get connected to different networks. This makes the factory network more open to hacking, information gathering campaigns, and other types of malicious attacks. For that reason, security measures for smart factories should be approached from a business continuity plan (BCP) perspective. Doing so will no longer make attacks unforeseeable. As a first step, factories must take stock of their current security measures and consider if they are satisfactory or not.

