
Regardless of whether a factory becomes a smart factory or not, truly effective security measures are not something that can be achieved through responses in the field or system changes alone. In order to protect a business's continuity from security threats, it is necessary for management to correctly understand its importance and relay courses of action to the field.
The first part of this series explained cyber threats to smart factories connected externally with IoT technology and open networks, as well as the necessity of establishing countermeasures.
Smart Factory Security Series Part 1: Contemplating the impact of inadequate cybersecurity on factories
This article will consider how enterprises should tackle security measures in smart factories, including those that have evolved from old structure to those we have now.
IT vs OT
Comparison of the words IT and OT is something we see time and again in the smart factory field. IT in this case signifies Information Technology, meaning technology related to conventional information systems as well as tacit knowledge developed around it. In other words, it is used as a term that includes the "knowledge" and "culture" shared among people involved in the IT field. Conversely, OT signifies Operational Technology, a term that signifies the same category for control systems in facilities such as factories.
As such, some cases exist in which even if there are risks that may impact the protection of digital information, such security risks are ignored if the stable operation of the factory can be preserved. Even if an OS vulnerability with a severely high impact were to be found in the IT world, some factories that run 24 hours a day 365 days a year are not able to make the decision to apply a security patch if it means halting the entire control system in order to undertake the maintenance.
In addition, once a system has been implemented, factories often use it for a longer period than most regular IT systems, sometimes continuing to use it even after the OS has reached its end-of-life. In comparison, in the IT world where consecutive vulnerability attacks are carried out one after another over networks, the speedy application of security patches such as that mentioned in the previous example and the use of a supported OS is often recognized as a subject handled with an extremely high priority.
In the movement to transform regular factories into smart factories with even greater efficiency and maximum profit productions, it is necessary to adequately fill such gaps through the fusion of IT and OT in order to acquire an optimal security solution.
As long as smart factories are connected through networks, the implementation of cybersecurity measures and technologies cultivated in the IT field become indispensable. Additionally, when that happens, consideration should be given to the fact that OT's highest priority is the factory's stable operation.
Three countermeasures in securing factories
Here, we introduce three courses of action that enable smart factories to be created with guaranteed security.
1. Creating organization standards agreed upon by management
Most enterprises likely already have some sort of cybersecurity standards in place, but it would be best to organize them based on a standard of measures ensuring that the business continuity of the entire company, including the factory, is not damaged. Even safer environments can be constructed if security elements that meet security standards can be incorporated into new or replacement equipment as they are installed in smart factories in the future.
Furthermore, new security threats appear on a daily basis so it is not a job that simply ends once countermeasures are implemented. It is important to go through the plan-do-check-act (PDCA) cycle and to create a rule to regularly conduct reviews even after the measures begin operation. In addition, it is necessary to decide in advance on how to respond to security incidents if, by chance, they occur. This allows for quick decision making and responses, but it is also a position that bears responsibility. Therefore, it is a subject where the management level should ideally agree upon a principle in advance. As a resource to promote understanding of cybersecurity on a management level, it would be helpful to use documents such as the one provided by the Cabinet Secretariat's National Center of Incident Readiness and Strategy for Cybersecurity (NISC) titled "Cybersecurity Philosophies for Business Administrations." Damage can also occur if a supplier's factory suffers a security incident. For example, deliveries of parts may be delayed or they may be mixed with defective goods. If your company's factory is connected to the supplier's factory through a network, the threat may infiltrate your factory as well. All these present the risk of impacting the production activities of your enterprise. With such risks in mind, it is important to request to your suppliers that they implement the appropriate security measures.
2. Applying multi-layered defense
When applying specific measures, the important thing to bear in mind is the policy that was first decided on "maintaining business continuity" and to consider implementations that match the risk level. Furthermore, combining a variety of security solutions in multiple countermeasure locations produces a multi-layered defense, which makes it possible to ultimately prevent damage even if one area is infiltrated.
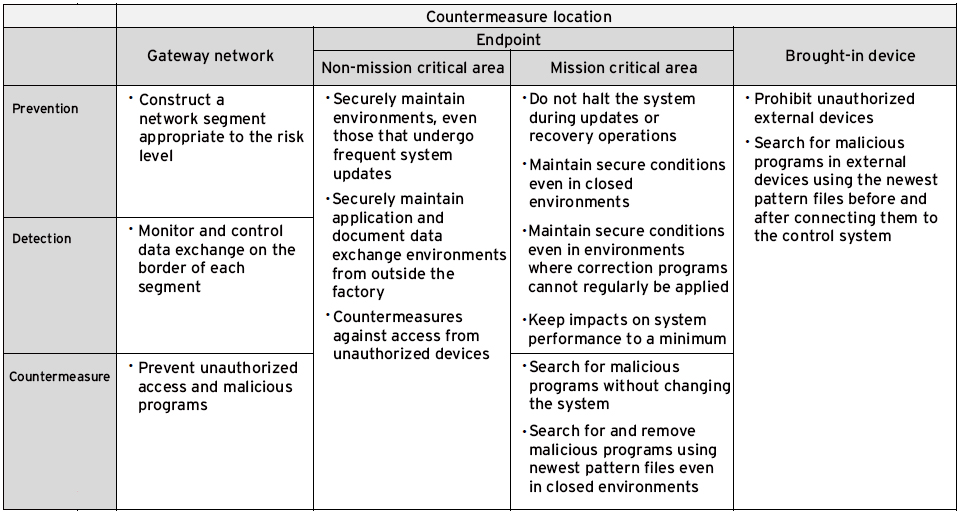
Table 1 is a summary of security measure requirements necessary at each countermeasure location and for each function. Security measures are implemented based on these requirements.
When making the implementation, it is also important to consider whether the target environment is already established or will be newly established.
In this case, it is crucial to focus on how fast abnormalities can be discovered and how quickly the system can be recovered.
For example, with regards to tests that check for infections from malicious programs and removal of infected files, management may choose to do a virus search and a removal tool on a USB drive. Because the removal tool does not need to be installed, it is able to detected and removed malicious programs without triggering compatibility issues caused by software installation.
Network intrusion detection products are effective for the early detection of abnormalities, especially internal monitoring products that trigger alarms if suspicious communications or behaviors are confirmed, even if the protocol is legitimate. The concern about products that monitor networks revolves around the impact they will have on existing networks such as misdetections or communication delays. However, by connecting to a switch mirror port and selecting the type of action, there will not be any particular impact while making it possible to detect attack packets and dangerous symptoms such as multiple login failures.
Combining these two methods allows for the early detection of abnormalities while also building a system that can quickly respond to issues. This makes it possible to reduce risks caused by large-scale damage without impacting existing network environment, while simultaneously shortening the downtime if an incident were to occur.
Furthermore, when making new installations or replacements, preventative measures at endpoints should also be considered in addition to the abovementioned points. With regards to endpoints, a general antivirus product raises compatibility issues but also its impact on machine performances. There are also cases in which the labor of updating a limited network and the burden of performing operation verifications after every update becomes an issue. Therefore, security products known as lock-down models are appropriate, as they allow only permitted applications to start.
Once you register a permitted application, there is no need to update any sort of exterior pattern file after that. It can also be used in a closed environment, and checking whether the application is permitted is only necessary at the time of start-up. This makes it possible to use the product without reducing the machine's performance. In addition, if the product provides services to support old OS versions, it can be used in existing systems that have been run for many years.
3. Nurturing organizations and human resources
The final point is about nurturing human resources and creating an environment where they can work effectively. Only by consolidating the organization and human resources can specific policies and measures be developed.
Until now, in organizational structures, the information system (IT) department was not involved in managing the factory system and the factory supervising (OT) department was not particularly involved in managing security either. There was no need for them to do so. Establishing smart factories requires the nurturing of human resources who understand both IT and OT. Additionally, it is necessary to create an environment in which personnel can work effectively by establishing an appropriate organizational structure that regards security as an issue the entire company should engage in. In order to acquire an agreement to construct such an organization, it becomes indispensable to have already obtained the consensus of management in advance.
One of the most important points for turning smart factories into a reality is to adequately understand both IT and OT situations, to recognize that security challenges are an issue that affects the company's business continuity, and to have the entire company, including management, engaged in it.

