The Cloud: What it is and what it's for

Over the past decade, the cloud has been an integral component of software development and overall business operations. It has opened various possibilities for small and medium-sized businesses as well as individual users to gain easy access to data storage and processing capabilities. From powering video streaming, web-based apps, customer relationship management (CRM) systems, mobile banking, inventory, and big data analyses, the cloud is helping empower businesses of all sizes to focus on innovation rather than infrastructure. What are the services in the cloud and what should you know about cloud security?
Cloud computing refers to storing and accessing data, software, programs, or services over the internet — the cloud — instead of in physical hard drives, servers, or mainframes.
Through cloud computing, important data can be accessed at any time with internet connectivity, regardless of where the user is located. It also allows organizations the flexibility to allocate and reallocate resources based on their dynamic needs.
Cloud providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud, provide computing resources to users and organizations all over the world.
The cloud has paved the way for organizations across industries to undergo digital transformation. And the shift has been swift — according to Forbes, by 2020, a staggering 83% of enterprise workloads will already be in the cloud.
The business advantages of cloud computing
Because organizations are freed of the burden and responsibility of maintaining and paying for their own infrastructure, the time it takes to develop and deploy applications and services is drastically reduced. Organizations can focus on application development rather than the laborious manual upkeep and maintenance of infrastructure to ensure that software and tools are on the latest versions.
Through the cloud, organizations become more streamlined — therefore, they are able to reach their customers faster, test and deploy their applications quicker, and drive innovation further.
The National Institute of Science and Technology (NIST) has provided five essential characteristics for what each cloud model should have:


A Closer Look at the Cloud
What are the different cloud computing deployment models?

Public cloud
- An infrastructure that is open for use by the general public or a large industry group
- Operates on a multitenant model; multiple users from different organizations access the service at the same time
- The cloud service provider has ownership and provides maintenance and management of the cloud service
- On-demand capability allows resources to be allocated dynamically based on users' requirements
- Exists on the premises of the cloud service provider and can be accessed via the internet
- Usually used for less-integral applications or operations
- Ideal for single users and small and medium-sized businesses

Private cloud
- A dedicated infrastructure that services a single organization and is inaccessible to those outside of the organization
- Operates on a single-tenant model; only an organization’s employees can access the private cloud for different operational needs
- The organization is responsible for paying for the acquisition, deployment, and maintenance costs
- Resources can be allocated dynamically based on users' demands
- May exist on the premises of the cloud service provider or as server configurations physically running on the organization's premises
- Usually used for sensitive data or applications, as well as operations that require a high level of control
- Ideal for healthcare organizations, government agencies, financial institutions, and telecommunication companies
Hybrid cloud
- A combination of both public and private cloud models, pairing the dependable nature of the private cloud and the on-demand capacity of the public cloud
- Ideal for businesses that provide services or offer products
What are the different cloud service models?

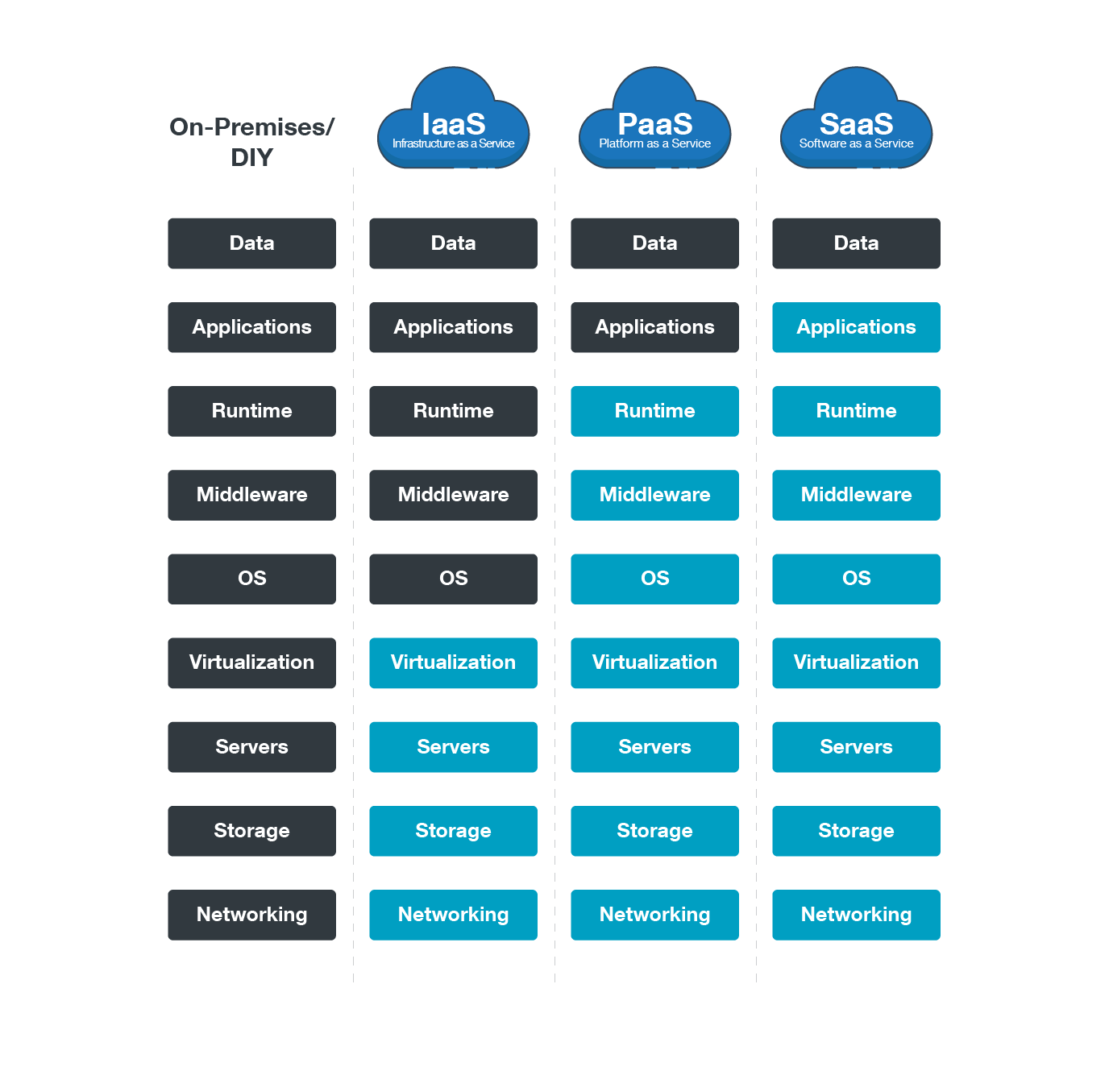
Software as a Service (SaaS)
SaaS is the most widely used type of cloud service model. Applications are hosted by a cloud-based service provider and can be accessed over a network or via the internet. Simply put, it's using an essential software that’s not saved on a computer, but instead, on a server that can be accessed via the internet.
SaaS providers manage, maintain, and have control over the cloud infrastructure (both hardware and software) as well as its security. SaaS examples include Gmail or Office 365, Google Apps, Salesforce, and Netflix. Because of its user-friendly nature, SaaS does not require technical skills to use or adopt.
Benefits:
- Easy-to-use interface
- New releases and automatic updates
- Low upfront costs
- High usage rates

Platform as a Service (PaaS)
PaaS is a cloud computing model where users or organizations can create, test, manage, and host their applications. It provides users with computing resources as well as tools and software to develop their apps, including middleware, database management, or the operating system. Like SaaS providers, PaaS providers manage, maintain, or have control over the cloud infrastructure as well as its security.
PaaS is mostly used by application developers and, hence, requires technical skills to operate.
Benefits:
- Reduced administration costs
- Increased agility
- Centralized and simplified application management
- Faster time to market

Infrastructure as a Service (IaaS)
IaaS is a cloud service model that provides users or organizations computing and processing resources, virtual machines (VMs), storage, as well as networks. Its servers may include physical as well as virtual ones. Unlike SaaS and PaaS, IaaS users have control over the cloud infrastructure as well as its security. The IaaS service provider takes care of the infrastructure while the user buys, installs, and manages the operating systems, middleware, and tools they need to develop their apps.
Highly technical professionals like infrastructure and network architects use IaaS.
Benefits:
- Reduced startup and maintenance expenses
- Increased scalability
- More rapid innovation
- Enhanced business continuity and disaster recovery
Staying Aloft in the Cloud with Trend Micro Security Solutions
The cloud, with its many business advantages, can empower organizations of all sizes to scale their business more quickly, streamline operations better, and innovate products and services faster. Businesses must ensure that everything that they move to the cloud — applications, data, and software, among others — are protected against the latest and most sophisticated threats.
Trend Micro has pioneered the use of the cloud to identify emerging threats rapidly via the Trend Micro™ Smart Protection Network™ infrastructure, which analyzes hundreds of terabytes of threat information daily. This valuable source of threat intelligence is connected to all Trend Micro security products and solutions.
Trend Micro’s Hybrid Cloud Security solution provides powerful, streamlined, and automated security within the organization’s DevOps pipeline and delivers multiple XGen™ threat defense techniques for protecting runtime physical, virtual, and cloud workloads. It also adds protection for containers via the Deep Security™ platform and Deep Security Smart Check, including the scanning of container images during predeployment and at runtime.
These solutions enable organizations to focus on security and compliance while still moving in the agile and adaptable world of DevOps. They also reduce the number of security tools needed with multiple security capabilities and a single dashboard to give full visibility into leading environments like Amazon Web Services, Docker, Microsoft Azure, and VMware. The Trend Micro Deep Security solution lowers the cost and complexity of securing workloads across multiple environments, including automated deployment, extensive API integration, and security capabilities that can virtually shield servers from the latest advanced threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks