Traditional security threats arrive via email, file, or websites to allow attackers to install malware on a target’s machine. Fileless threats, on the other hand, differ from conventional malware in that they do not rely on malicious software or executables to infect a system. Instead, fileless threats take advantage of a machine's built-in tools and applications for attacks, essentially turning the system against itself.
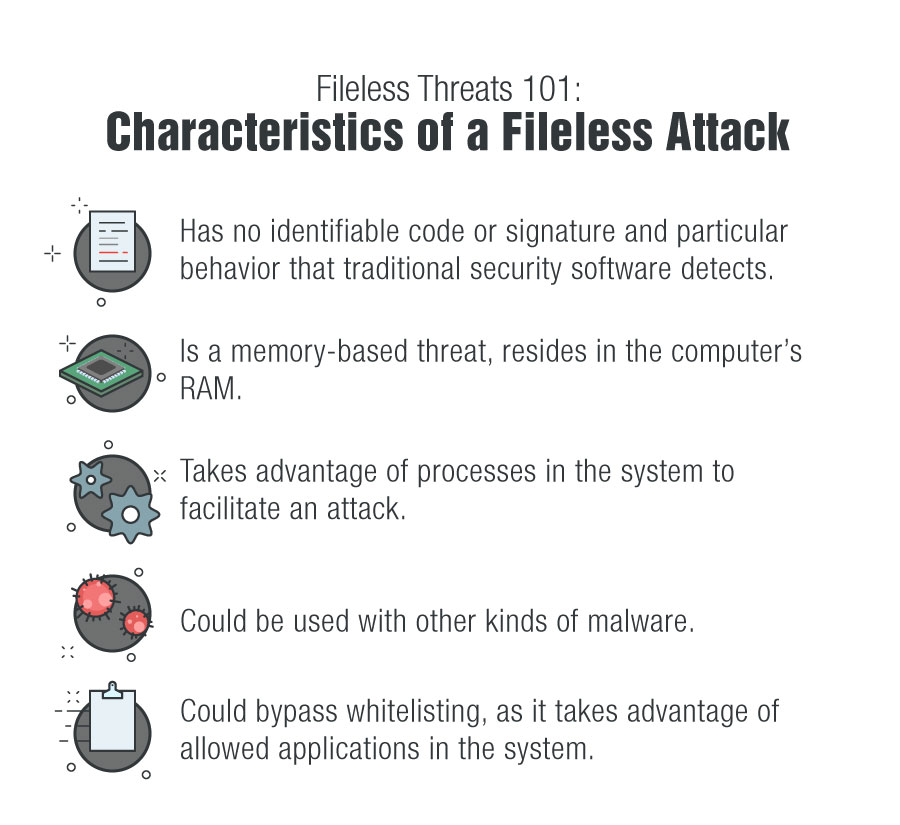
Fileless threats leave no identifiable signature that could trigger traditional security software detection, allowing them to bypass standard security mechanisms and potentially undermine the purpose of affected legitimate programs.

What are fileless attacks?
A fileless attack is a type of malicious activity wherein a hacker takes advantage of applications already installed on a machine. Unlike other attacks where malicious software is installed onto a device without a user knowing, fileless attacks use trusted applications, existing software, and authorized protocols. Essentially, fileless attacks do not need malware to execute an attack.
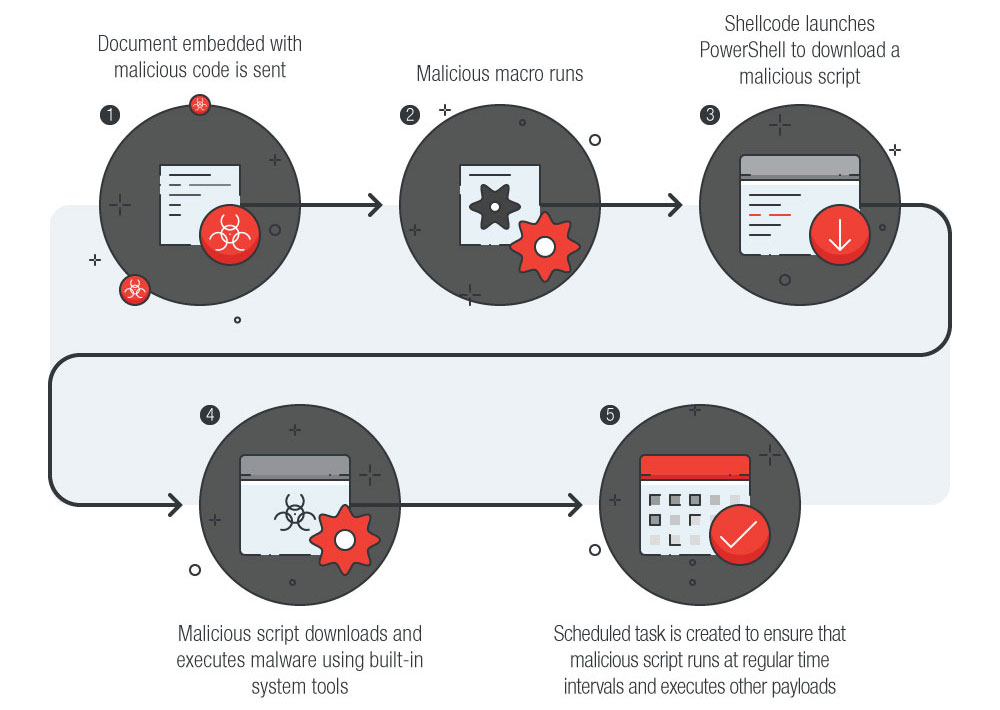
A typical infection chain of a fileless threat that launches via document exploit, installs payload, and maintains persistence
An attack can be initiated by a user action, such as clicking on an attached document embedded with abused code, which then makes use of other applications installed on the machine. Fileless attacks occur in a machine’s random access memory (RAM) and usually utilize built-in Windows tools such as PowerShell and Windows Management Instrumentation (WMI) to execute malicious commands. These known applications carry out system tasks for endpoints, which makes them ideal for facilitating the attacks. Fileless threats can also be coupled with other attack vectors such as ransomware in an attack.
Since fileless threats do not require downloaded files, detecting and preventing them can be tricky. However, because RAM only keeps its data when the machine is on, the infection should no longer be live when the computer has been rebooted. However, this doesn't mean hackers cannot take advantage of other weaknesses in the computer or even perform other techniques to give it persistence. For instance, a hacker can continue an attack by setting up scripts that run when the system restarts.
How do fileless threats enter systems and how are they detected?
Malware attacks typically involve malicious files written to disk or require interaction to carry out their malicious intent. These characteristics would leave traces, in one form or another, for post-infection forensics. However, since fileless threats are intended to be memory resident, more often than not, they don't leave a footprint after execution. The malicious payload occurs in the RAM, which means it doesn't write anything to the disk. This makes memory-based attacks trickier and harder to detect than file-based malware. However, fileless threat activities can be detected by tracking nonfile-based indicators such as particular execution events or behaviors.
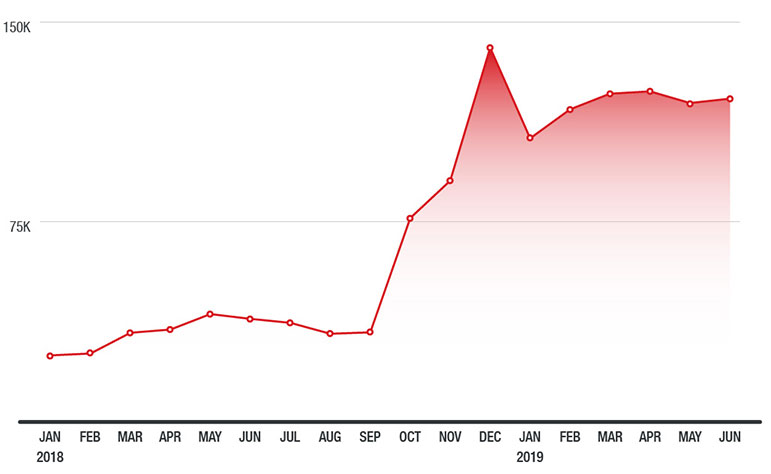
396%
in fileless threats
Jan 2018 - Jun 2019
Fileless attacks thrive in stealth and subtlety, and the month-over-month numbers show that the threat is appealing to cybercriminals. Tracking fileless threat detections from 2018 to the first half of 2019 show a noticeable increase. The upsurge can be attributed to the continued use of different fileless techniques to evade conventional blacklisting detection and solutions.
Monthly comparison of fileless events blocked, based on data from the Trend Micro™ Smart Protection Network™ infrastructure (January 2018 to June 2019)
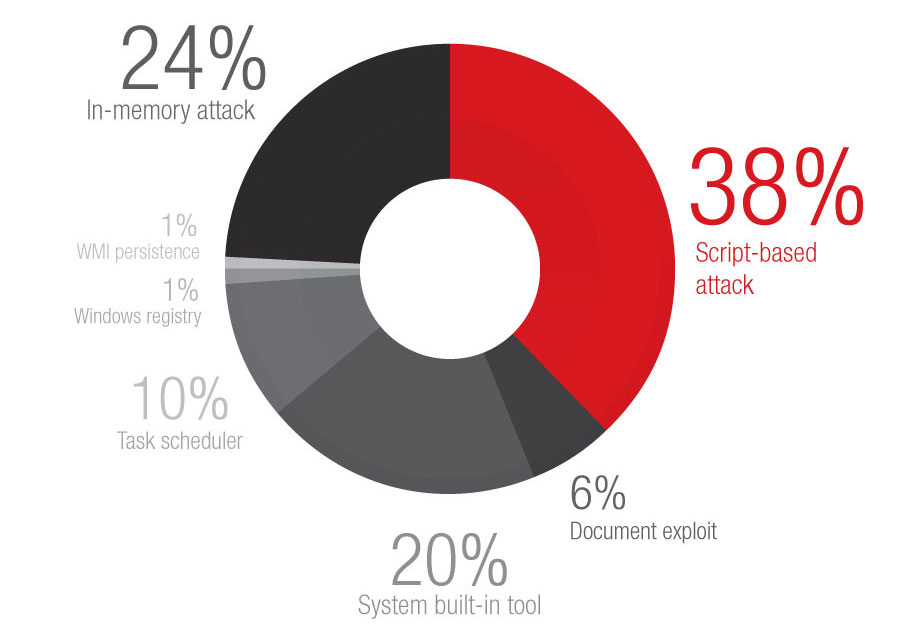
Percentage of fileless events detected (January to June 2019)

Here’s how fileless threats work and what techniques to look out for:
Launching attacks via document or in-memory exploits
Read more
A fileless attack can start “traditionally” via malicious macro code (e.g. JavaScript or VBScript) embedded in archives, other seemingly normal files, and approved applications such as Office documents (e.g. Microsoft Word and Excel) and PDFs. Attackers take advantage of these, enabling them to run code with the same privileges as the running application. The macros can run scripts and abuse legitimate tools like PowerShell to launch, download, or execute code, scripts, and payloads. These scripts can also be obfuscated, which makes detecting keywords that trigger execution a challenge for organizations. A fileless attack can also make its way to systems through a spam or phishing message that entices a receiver to click on a malicious link, which then starts the infection process.
Fileless threats can also employ different ways to execute from memory. A recent example of this is the in-memory exploit EternalBlue, which takes advantage of a vulnerability in the Server Message Block 1 (SMB 1) protocol. An attack can also take advantage of legitimate processes through DLL injection, which forces the loading of a dynamic-link library (DLL) into a host process, thus eliminating the need to write the DLL to the disk. A technique like process hollowing, which replaces some code with a malicious function, can also be employed. This involves code execution directly in memory and can even be kept running in the background even after the software has been closed.
Installing malware via built-in system tools or scripts
Attackers can abuse system administration tools and utilities for fileless infections. Instead of using executables, attackers can misuse the tools that are already on the target system to conduct their attacks. Some of these tools are command-line interfaces such as BITSAdmin (Background Intelligence Transfer Service), used for creating and downloading jobs and monitoring progress; CertUtil, used for certificate services/management; and msiexec, used for installing, modifying, and performing Windows Installer applications.
Script-based attacks are the most common fileless threat, based on our data (at 38% for 2019 1H). Many script-based attacks use interpreted scripts, as they run directly on the command line (via PowerShell, JavaScript, VBScript, WScript, mshta, etc.), and can lead to arbitrary code execution. PowerShell, for instance, can execute a hidden command in the system that can be set depending on the length of time planned for the attack. Many malware types have since been delivered filelessly through code execution in memory to bypass endpoint-based security.
Many fileless threats abuse PowerShell, in particular, as it is a built-in feature on many Windows operating systems. The Microsoft framework is also capable of accessing application programming interfaces (APIs) that execute crucial system and application functions. It is also appealing for attackers because it has no executable on the disk, thus allowing them to deliver payloads and executive malicious commands filelessly. IT administrators can best detect the misuse of PowerShell through behavioral detection, i.e., discerning a PowerShell session executed via an encoded command in command line.
Maintaining persistence via Task Scheduler, Registry, or WMI
Often, breaches caused by fileless threats can be halted as soon as the user restarts the computer since the malicious code only resides in memory. However, malicious actors have already been using techniques to ensure that fileless infections do not rely on endpoints to sustain an attack. Hackers can make subtle changes to the system registry by planting entries and setting up scripts to run even after a system restart. What makes this particularly noteworthy is that by having a system’s own commands execute an attack, it might not be considered in some monitoring efforts. For one thing, the Windows Registry can also be compromised by storing malicious codes in the registry with auto-run capabilities, so that attacks refresh in the background even after a computer reboot. An example is the fileless version of the evolving malware KOVTER, which was previously seen creating registry entries that load malicious codes into memory whenever an infected machine has been restarted or batch files have been triggered.
Read more
Windows Task Scheduler, which is used to enable programs scripted to be launched at a predetermined time, can also be abused to maintain persistence. For fileless threats, this means that tasks can be scheduled for execution. Attackers can even set the tasks to recur and create registry entries to automatically reinfect systems.
Interpreted codes such as those in PowerShell or a Windows component such as Windows Management Instrumentation (WMI) that are typically used by enterprise networks for system administration task automation, can be abused to allow malicious scripts to run, which could then affect the endpoint without writing to disk. Attackers abuse this for code execution, lateral movement, and persistence. They can use WMI repositories to store malicious scripts that are periodically invoked using WMI bindings. Notably, iterations of cryptocurrency-mining malware were also seen abusing WMI for persistence.

What are some of the known fileless attacks?
Two high-profile hacks, against Equifax and the Democratic National Committee (DNC), were reported to be fileless attacks. The latter hack used a command injection vulnerability in the Apache Struts application, while the former took advantage of PowerShell and WMI to gain a foothold in systems.
In 2017, a fileless attack infected financial institutions, telecommunication companies, and government organizations in 40 countries. One bank’s security team discovered the attack through of copy of Meterpreter, an in-memory component of Metasploit, in the physical memory of a Microsoft domain controller. This was likely done via PowerShell, so that it would be loaded into memory rather than writing it to the disk and eventually compromise computers that control automated teller machines (ATMs). In another incident, hackers were able to successfully infect machines and steal $800,000. While they couldn’t find any trace of malware on the ATMs or the backend network, they found two files containing malware logs on the ATM’s hard drive, possibly installed and executed via remote administration modules.
Read more
Other forms of cybercrime were also seen employing fileless techniques. Trend Micro has reported on a ransomware that bears some similarities to WannaCry, as it exploits the same vulnerabilities. However, the malware variant, called UIWIX, is fileless — it gets executed in memory after exploiting EternalBlue. The ransomware terminates itself if it detects a virtual machine or sandbox, allowing it to evade detection.
Another campaign used fileless infection in exploit kits, like in the case of the cybercriminal group Lurk, which stole more than $45 million from financial institutions. Attackers also used fileless threats in campaigns involving cryptocurrency miners targeting corporate servers and workstations and backdoors that arrive via autostart registry procedure. The most recent one, at the time of writing, involves the trojan Astaroth, which was dropped into the memory of infected computers and abused the Windows Management Instrumentation Command-line (WMIC) tool to spread.

How can users and enterprises defend against fileless threats?
Tackling the ever-changing landscape and protecting against emerging and sophisticated threats like fileless attacks may be daunting to organizations that are not aware of the techniques involved. However, fileless threats can be defended against, despite the lack of a discrete binary or executable. Aside from keeping systems updated and software patched, organizations can implement the principle of least privilege and employing a custom sandbox.
Best Practices
Organizations should adopt these best practices to best prepare for the aforementioned risks:
Read more
- Secure the use of PowerShell. Use its own logging capability, which can help scrutinize suspicious behavior in a system. IT administrators should also consider listing triggers for detection that can be based on commands in malicious PowerShell scripts.
- Harden systems via PowerShell commands. Windows PowerShell use can be further secured from malicious codes by employing commands that involve execution policies (i.e., setting conditions under which a script is permitted to run) and usage of ConstrainedLanguageMode (i.e., restricting scripts that can be used to invoke arbitrary functions).
- Employ behavior monitoring mechanisms. Having behavior monitoring on the endpoint can help prevent and limit data leakage and malware infection by monitoring anomalies in the process chain and blocking malicious behaviors and routines associated with malware. It also monitors unusual modifications to software and applications like PowerShell.
- Reboot endpoint device and change passwords. Restarting the machine should stop any fileless attacks since it will only keep data in RAM when the device is on — if the fileless threat did not employ any persistence techniques. Users should also change their passwords.
- Install security software that provides multilayered protection. Consider security products that can detect and prevent fileless threats in memory and other techniques that may expose systems to fileless infections.
- Disable unnecessary components. Disabling underutilized and outdated components can prevent an attacker from breaching a system or network from an unsecure component.
- Secure possible entry points. Fileless threats' attack vectors can include malicious sites and URLs, spam, and vulnerable third-party components like browser plug-ins.
- Be wary of macros. The safe route is to disable macros in Microsoft Office documents to prevent unsecure code from running. If it can't be avoided, change the settings to only allow digitally signed macros.
- Avoid opening files from untrusted locations. Malicious files can still take part in a fileless infection through embedded or downloaded payloads.
Trend Micro solutions
Trend Micro's Smart Protection Suites deliver several capabilities like high-fidelity machine learning and web reputation services that minimize the impact of persistent, fileless threats. Trend Micro Apex One™ protection employs a variety of threat detection capabilities, notably behavioral analysis that protects against malicious scripts, injection, ransomware, memory and browser attacks related to fileless threats. Additionally, the Apex One Endpoint Sensor provides context-aware endpoint investigation and response (EDR) that monitors events and quickly examines what processes or events are triggering malicious activity. The Trend Micro Deep Discovery™ solution has a layer for email inspection that can protect enterprises by detecting malicious attachments and URLs. Deep Discovery can detect the remote scripts even if it is not being downloaded in the physical endpoint.
It is also important to proactively monitor the endpoints and networks. Fileless threats may not be as visible as other malware, but they can also leave telltale signs that IT and security teams could watch out for, such as suspicious network traffic (for C&C communication and data exfiltration). For example, Trend Micro's custom sandbox integrated in Deep Discovery™ via Deep Discovery Analyzer, Deep Security™, and OfficeScan™ can intercept APIs and check for code strings meant to execute a malware’s evasion technique or routines.
Implementing behavior monitoring also helps by monitoring and blocking anomalous behaviors and routines associated with malware, like how a hijacked process would invoke Command Prompt to execute a PowerShell script. Trend Micro endpoint solutions such as Trend Micro™ Security, OfficeScan, and Worry-Free Business Security all include behavior monitoring to detect script-based, fileless threats. This helps organizations look out for malicious behavior and block the malware before the behavior is executed or performed. OfficeScan can also include a device control feature that can prevent removable media such as USB and optical drives from being accessed, preventing them to be vectors to fileless threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks