Threat Actors Abuse Evernote, Other Shared Platforms for Credential Phishing
Insights and analysis by Marshall Chen and Yorkbing Yap
 Trend Micro researchers encountered campaigns that abuse the note-taking platform Evernote to host credential-phishing pages. These campaigns also exploit other shared platforms for editing images, making infographics and charts, and creating brand templates for the same purpose.
Trend Micro researchers encountered campaigns that abuse the note-taking platform Evernote to host credential-phishing pages. These campaigns also exploit other shared platforms for editing images, making infographics and charts, and creating brand templates for the same purpose.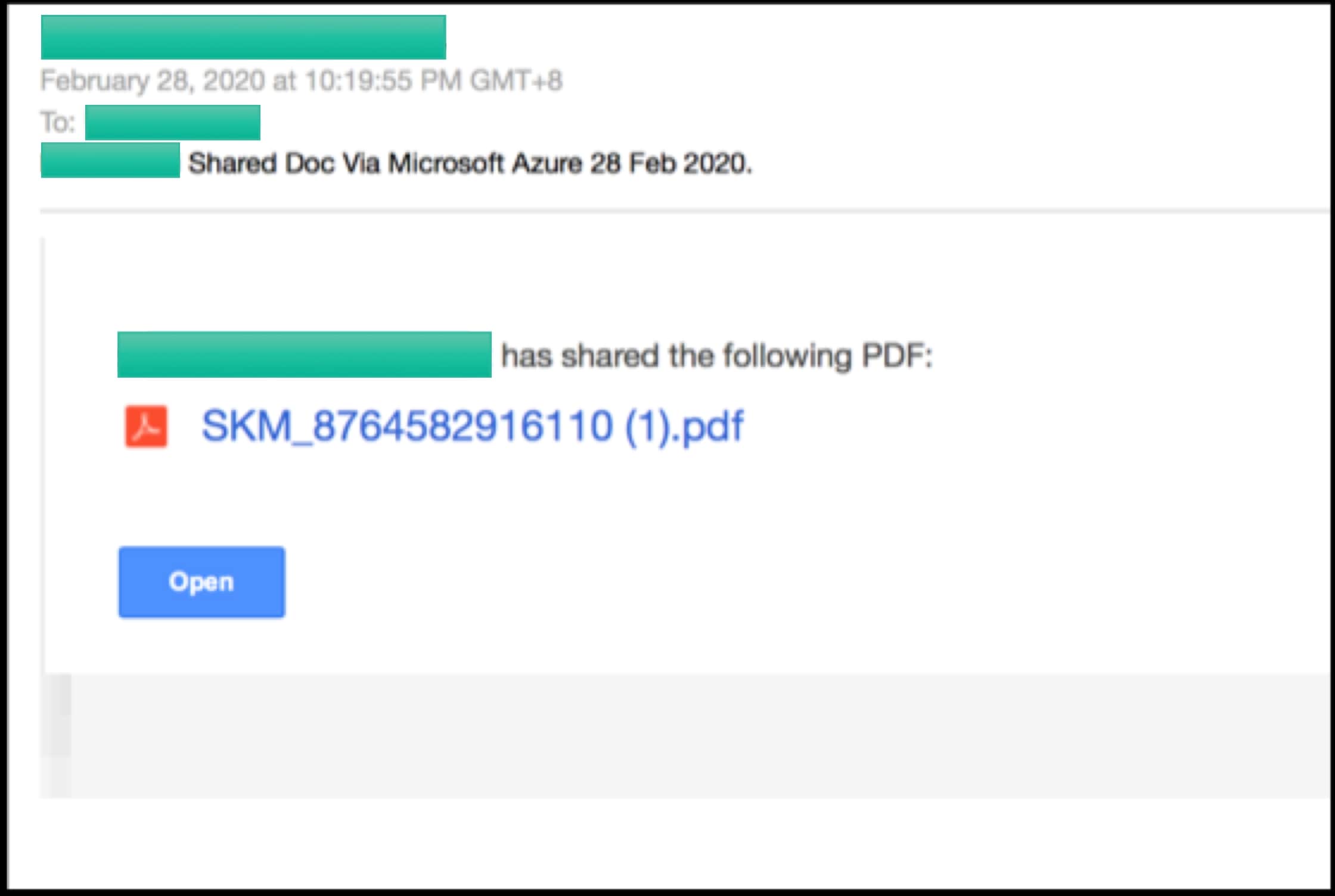
Figure 1. A sample phishing email abusing Evernote
The phishing emails contain a link that leads to a page on Evernote. On that page, users are prompted to click the link to download or preview a document that has apparently been shared using “Secured Microsoft Azure for OneDrive Cloud.”
Figure 2. The prompt to download or preview the document
After clicking the “Download or Preview Here” link, users are led to a phishing page that masquerades as a Microsoft account login page.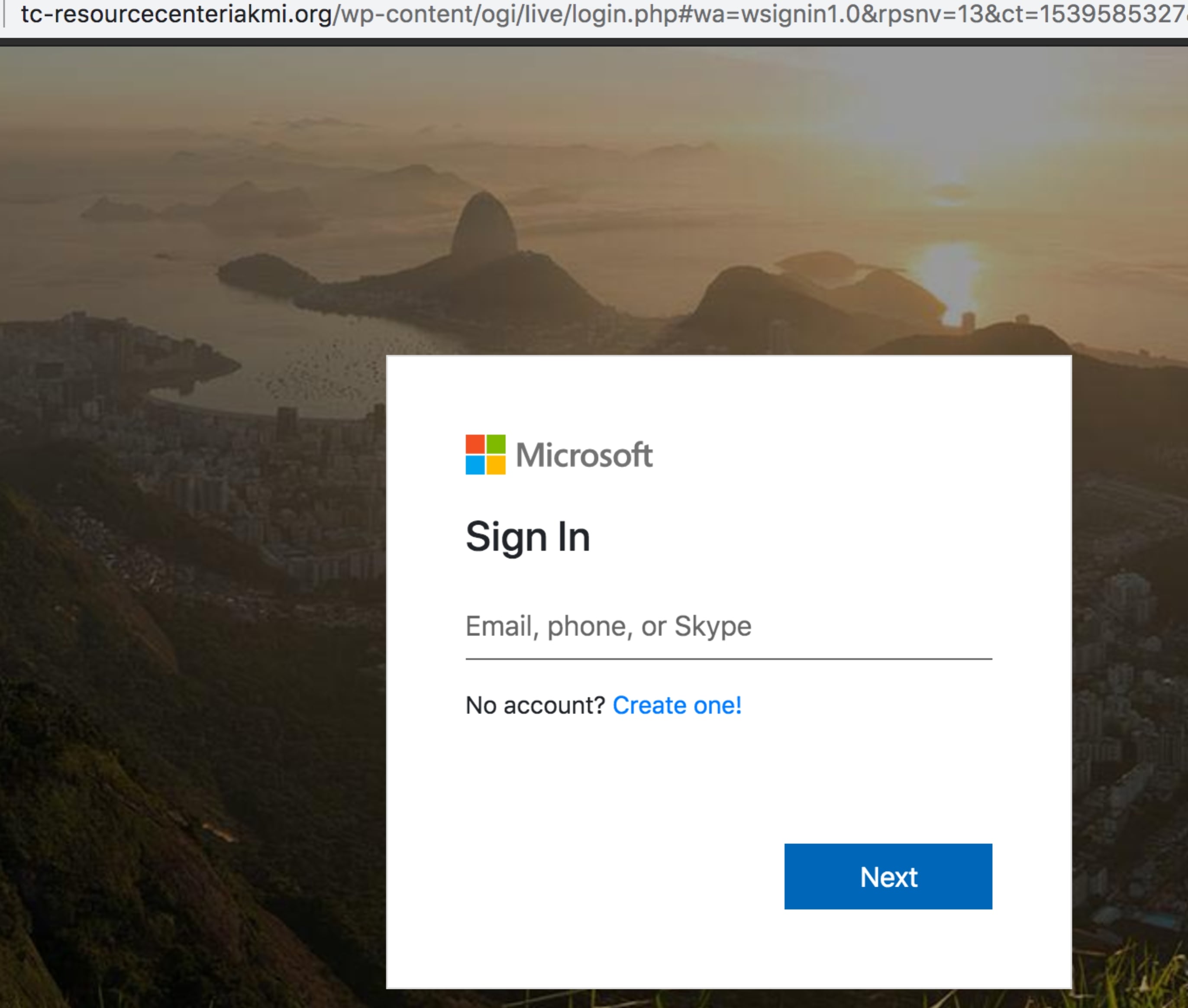
Figure 3. The fake Microsoft login page
After entering their account credentials, users will be informed that an incorrect account or password was entered, prompting them to reenter their credentials.
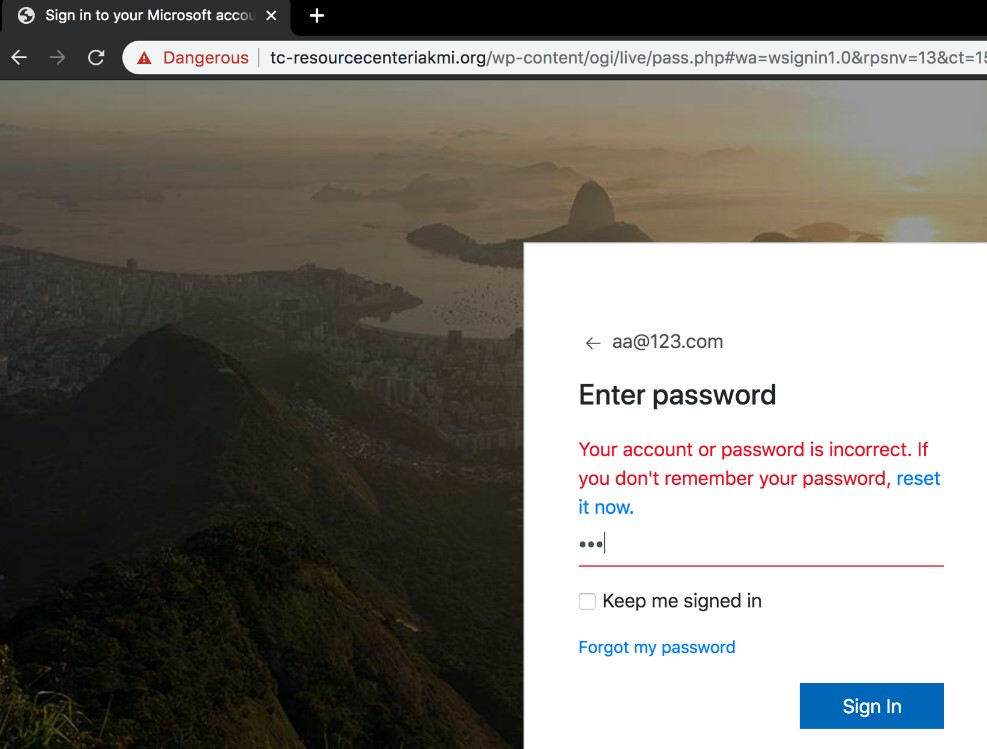
Figure 4. The prompt to reenter credentials
Email header analysis
Based on their email headers, the emails pass Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting and Conformance (DMARC) verifications. The email sender is possibly hacked, and the compromised account is used to send phishing emails.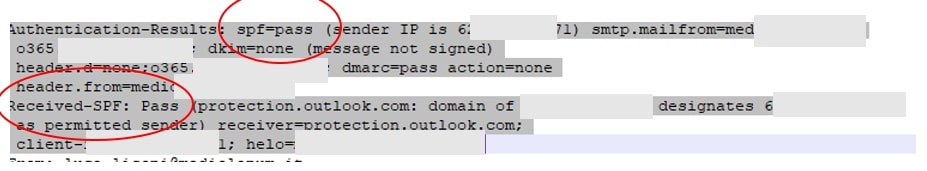
Figure 5. Email header analysis indicating SPF and DMARC verifications
Researchers identified the sender’s IP address, which they discovered to be an open Remote Desktop Protocol (RDP) port. It uses Windows on a hosting provider and is linked to other senders of the phishing emails. The email subjects also follow a pattern, as seen in these sample subjects:
- < Email account > Shared Doc Via Microsoft Azure 14 Feb 2020.
- < Personal name> Shared Doc Via Microsoft Azure 12 Feb 2020.
Other shared platforms
Researchers also found phishing campaigns exploiting the image editing site Canva, the infographic and chart maker Infogram, and the brand template platform Lucidpress. The emails in these campaigns involve the team collaboration software Microsoft SharePoint.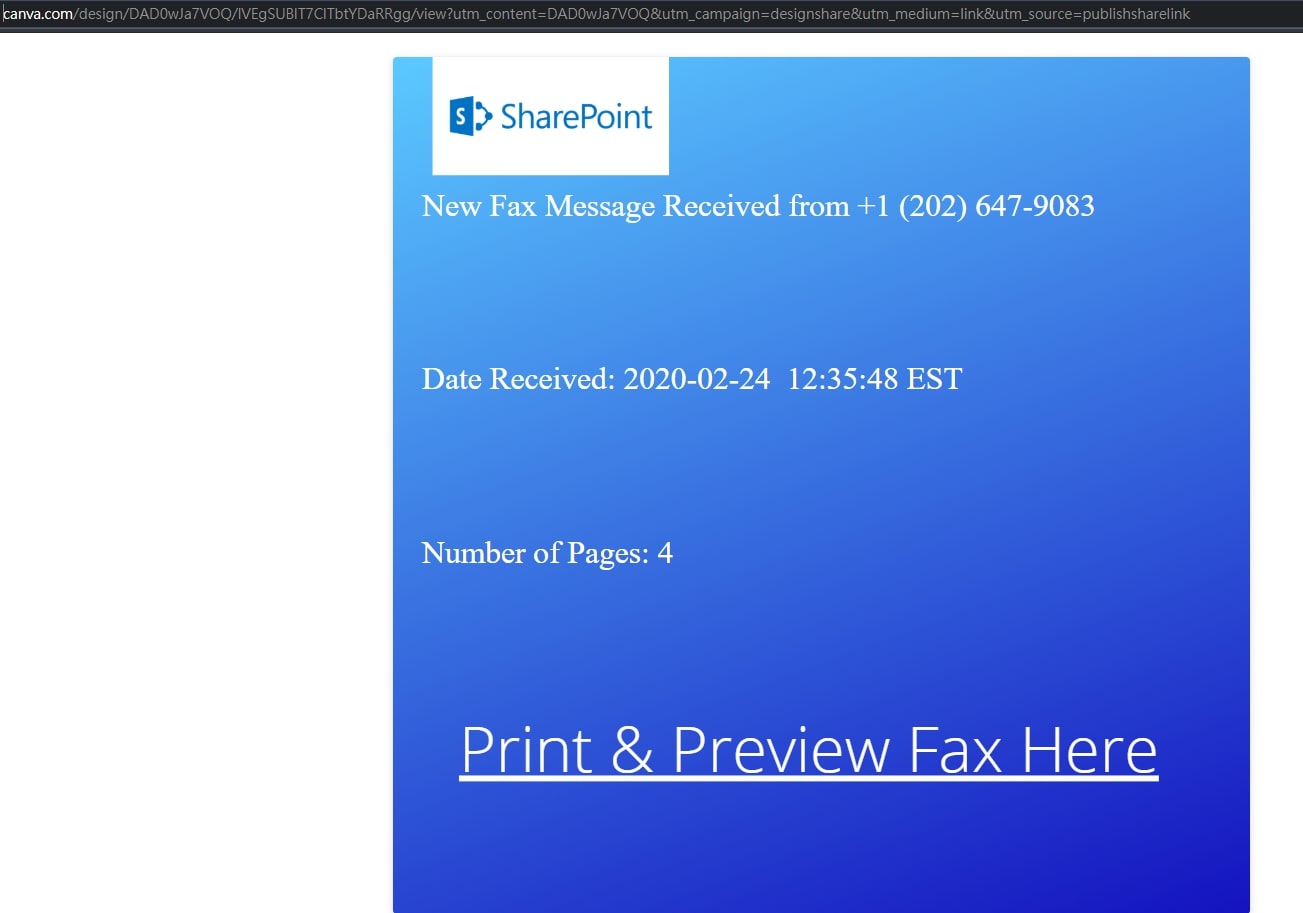
Figure 6. A phishing campaign related to Canva
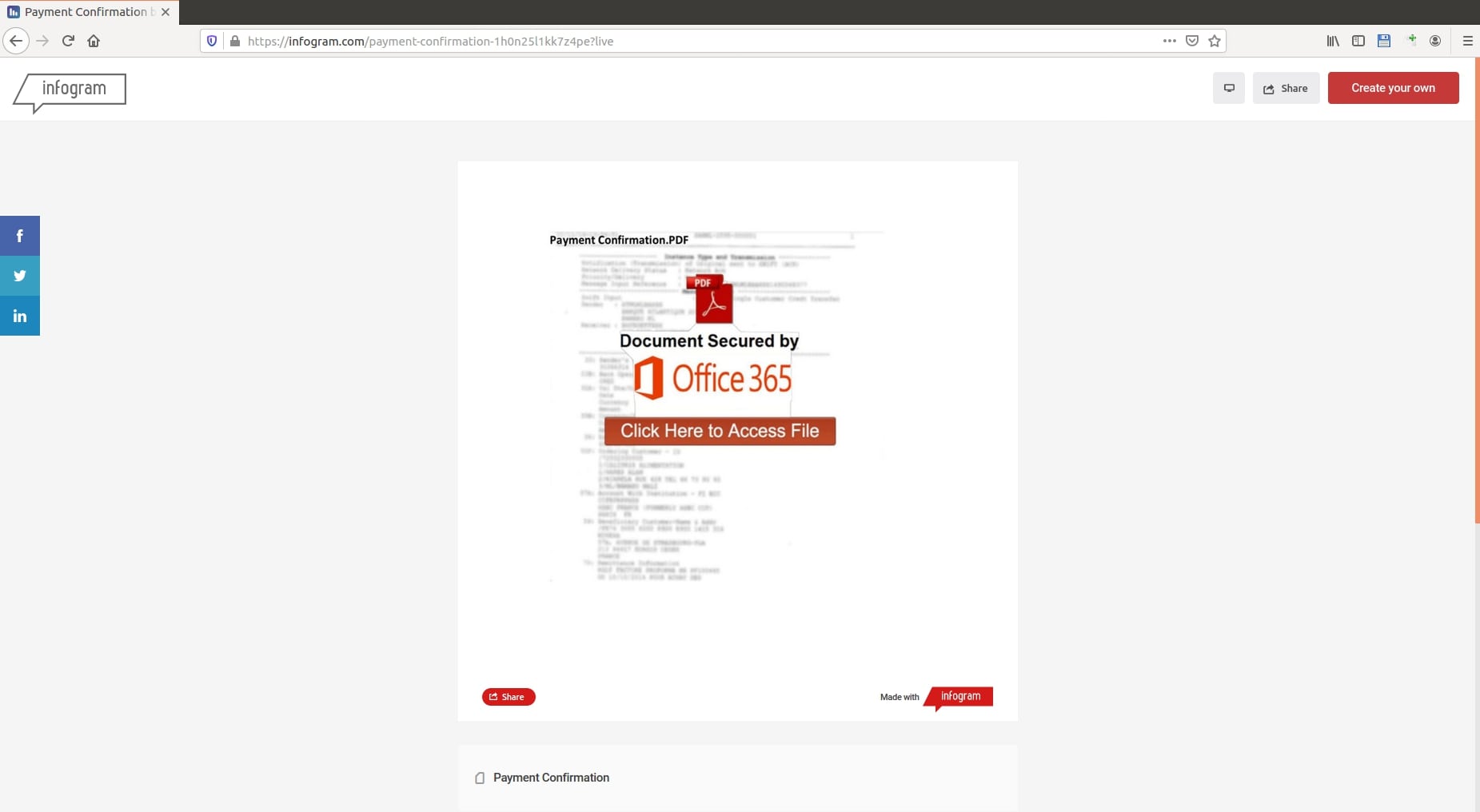
Figure 7. A phishing campaign related to Infogram
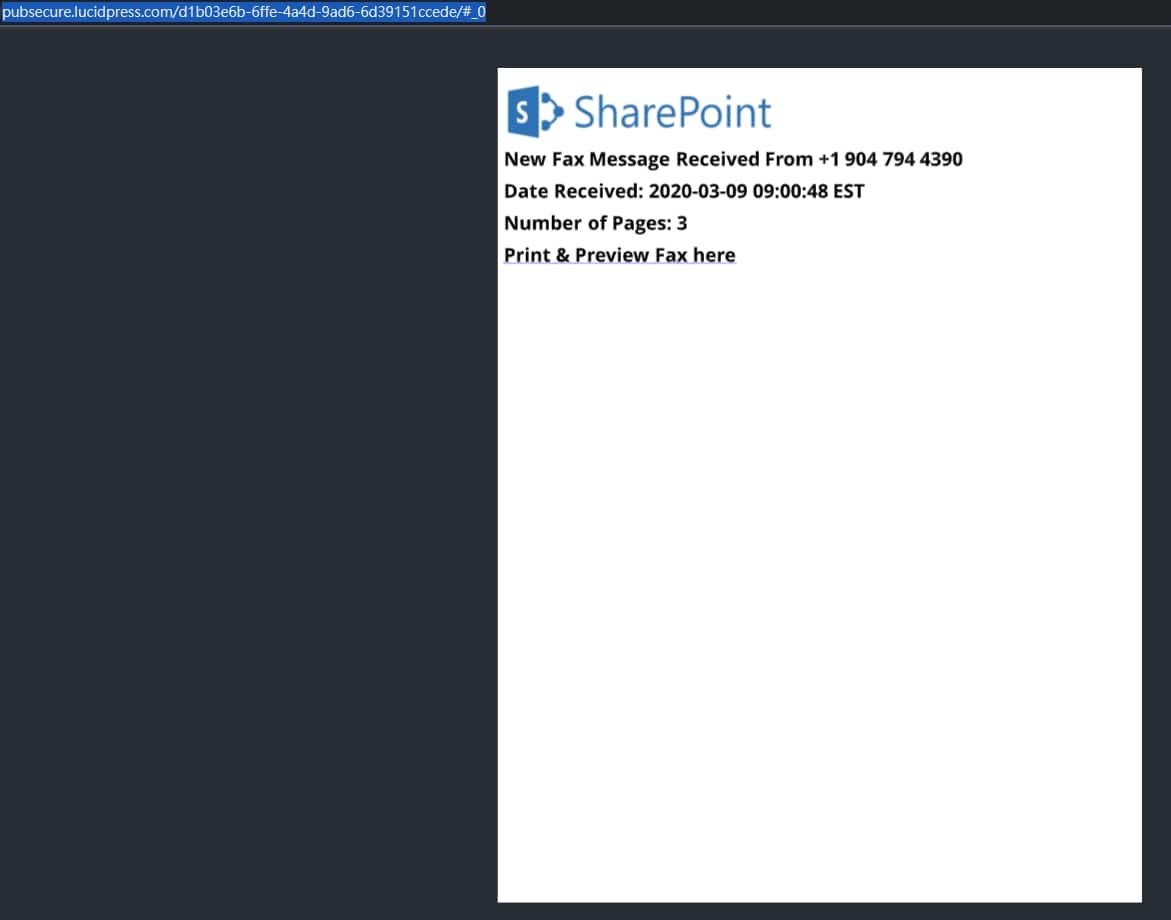
Figure 8. A phishing campaign related to Lucidpress
Third-party sources earlier reported similar attacks that abused Microsoft SharePoint and Microsoft Sway.
Guarding shared platforms
More and more threat actors are abusing legitimate sharing services to conduct credential-phishing campaigns. Enterprises should arm themselves with the best practices in mitigating such attacks. Below are some of the ways employees can avoid being victimized by phishing attacks:
- Avoid clicking links or downloading files from unfamiliar sources.
- Closely examine URLs before clicking them. Hovering the cursor over the link may reveal that it may lead to a page other than what is expected.
- Watch out for grammatical errors and spelling mistakes.
- Be cautious of emails that request sensitive information.
Security solutions for email and collaboration can also boost protection against phishing.
Indicators of compromise
Evernote
URL
- hxxps[:]//www[.]evernote[.]com/shard/s430/sh/2246e4e7[-]382f-490d[-]8b97[-]12a790d84228/aa481828b45cc2c307ea90c720cad84b
Phishing Site:
- hxxps[:]//tc-resourcecenteriakmi[.]org/wp-content/ogi/Iive/
IP Address
- 107[.]173[.]141[.]117
Canva
URL
- hxxps[:]//www[.]canva.com/design/DAD0wJa7VOQ/lVEgSUBlT7ClTbtYDaRRgg/view?utm_content[=]DAD0wJa7VOQ&utm_campaign[=]designshare&utm_medium[=]link&utm_source=publishsharelink
Phishing Site
- hxxps[:]//dickenscircles[.]icu/al/One-Drive-Arab/oneddrive/office.php
Infogram
URL
- hxxps[:]//infogram[.]com/payment[-]confirmation[-]1h0n25l1kk7z4pe?live
Phishing site
- hxxps[:]//laspalmasmotel[.]com/000secure00/Office365/
Lucidpress
URL
- hxxps[:]//pubsecure[.]lucidpress.com/d1b03e6b[-]6ffe[-]4a4d-9ad6-6d39151ccede/#_0
Phishing Site
- hxxps[:]//mysports11[.]com/msth-admin/office/index.php
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks