Spam, BEC, Ransomware: The Continuing Abuse of Email by Old and New Threats
Opening an email didn’t seem as harmful as it sounds like before the advent of email threats. The current reality, however, couldn’t be more different. Many businesses across the globe have suffered through hefty payouts, paralyzed systems, and damaged reputations after simply opening an email with malicious content. The scope of attacks and the rampant rate with which the abuse of email managed to inflict on businesses and users points to the effectiveness of email-borne threats.
Email remains a major infection vector for malware threats, with attackers continuing to employ schemes such as the bogus invoice or supplier swindle and employ keylogger malware or HTML pages in phishing emails to trick employees and executives. Similarly, ransomware operators continue to utilize email to spread their malware. Just last week, a sizeable spam campaign was detected distributing the latest Locky variant alongside another ransomware called FakeGlobe, launching millions of attacks in a single day.
Email’s favorite poison, spam, is evidently the common denominator of major attacks the past few years. The latest Locky outbreak is a testament to how far spam has come since its first incarnation as annoying text strings, when email was utilized to advertise products and services for phishing purposes or to drive recipients to compromised or malicious sites. While in the beginning, spam was relatively less harmful to its recipients, it has now evolved to deliver more serious threats.
Figure 1. Spam in the past couple of years
Spam Continues to Distribute Ransomware and other Malware
Cerber ransomware, which was also sent in spam emails, continues to thrive this year with its new defense mechanisms and refashioned encryption routines. Spammers have also reportedly capitalized on the WannaCry outbreak by sending emails claiming to protect and recover systems, but they just steal recipients’ data. Other new and old email-borne threats with fresh routines have also come out in 2017, and it may be a cause for concern. Historically, these threats were mostly distributed via spam emails.
Lukitus (detected as Ransom_LOCKY.DLDTATN, Ransom_LOCKY.TH817, Ransom_LOCKY.DLDTATT, and Ransom_LOCKY.AJA), a new Locky ransomware variant, was discovered sporting a new arrival vector. The variant arrives as an email with a ZIP compressed attachment that contains a Visual Basic Script (VBS) or JavaScript file, which initiates a downloader that reaches out to its C&C servers to download the ransomware. Another ransomware variant, Reyptson (detected by Trend Micro as Ransom_REYPTSON.B), is a threat that manipulates a popular email application to send malicious email directly to its potential victims. It was discovered abusing the free email program Mozilla Thunderbird to infect email recipients. The variant scans Mozilla Thunderbird for Simple Mail Transfer Protocol (SMTP) credentials, collects any it finds, and sends them to its remote servers.
Meanwhile, a revamped version of the banking Trojan Emotet (TSPY_EMOTET.L) can log into email services using a stolen account name and password to distribute spam. This renders traditional anti-spam techniques useless because the email is sent from a legitimate email address. TrickBot, another banking Trojan which is an iteration of older malware DYRE/Dyreza, is equipped with new capabilities designed to steal data saved by Microsoft Outlook by opening relevant registry keys.
Old tricks also get a makeover via a typical phishing tactic that uses template injection attack instead of a macro. Discovered two months ago, this new threat targeted energy facilities in the U.S. with emails containing fake resumes or environmental reports in Word documents that can silently harvest the user's credentials if opened.
Data from the Trend Micro Smart Protection Network™ reveals a notable increase in the number of blocked spam emails since 2011, which means that spam threats can be expected to be even more prevalent. Last year’s number almost doubled from 2015 with 75 billion spam emails blocked, and this year, Smart Protection Network already recorded 34.4 billion blocked spam threats for the first half of 2017.

Figure 2. Blocked spam threats in the first half of 2016 and 2017
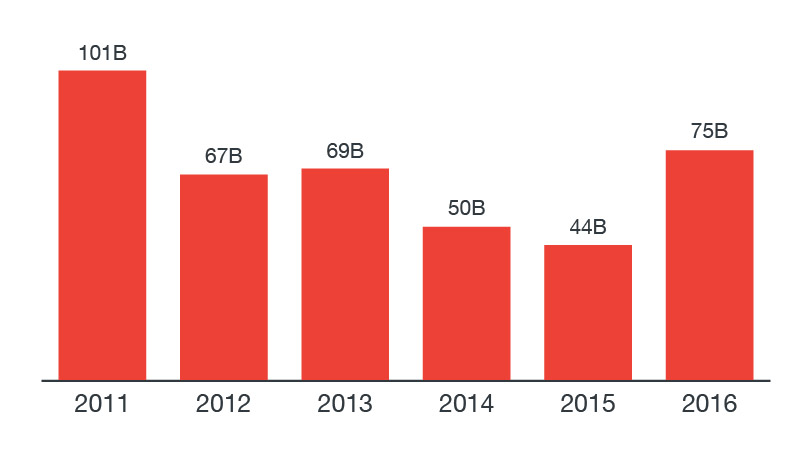
Figure 3. Number of email reputation queries blocked as spam from 2011 to 2016
In comparison to 2016’s 25.6 billion, there is a strong indication that distribution of spam threats is going to be more widespread in the second half of 2017. If the numbers for the second half of the year are on track to surpass last year’s 49.1 billion, it will overtake 2016’s numbers. It’s also possible that it could equal, or even exceed, the spam record of 2011.
The Cost of Business Email Compromise (BEC)
Business email compromise (BEC), while not new, continues its upward trajectory, causing an increasing number of victims and business losses. In 2016, BEC attacks cost businesses worldwide an average of US$140,000 per attack, while the Federal Bureau of Investigation (FBI) said that the global losses due to BEC have currently reached $5.3 billion.
There's a new emerging trend involving the use of HTML pages instead of executable files. In this scheme, the page asks the recipient to enter their username and password to view the document file.
Email-based threats, whether it is BEC, spam, or the many other new and forthcoming threats, should be seen for what it is: a security issue that is as alarming as the malware that uses it to profit or steal from its victims.
Mitigations and Solutions
It is highly recommended to build a culture of security to combat email threats as it is an important communication tool for business organizations. Cybercriminals will use different kinds of social engineering tactics to coerce potential victims into downloading files or giving out sensitive information, so it is important to educate employees on how to avoid phishing attacks. Network administrators should also ensure that antispam filters, including policy management and threat detection level thresholds, are properly configured. In addition, IT professionals should adopt security measures such as Sender Policy Framework (SPF), Sender ID, DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting & Conformance (DMARC) to prevent the spoofing the company domain.
[Related: How to mitigate email threats]
The rise of spam levels along with new e-mail-borne threats also calls for a multilayered and proactive approach to security—from the gateway, endpoints, networks, and servers. Trend Micro endpoint solutions such as Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security can protect users and businesses from these threats by detecting malicious files, and spammed messages as well as blocking all related malicious URLs. Trend Micro Deep Discovery™ has an email inspection layer that can protect enterprises by detecting malicious attachment and URLs.
Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, spear phishing, ransomware, and advanced targeted attacks before they reach the network. It protects Microsoft Exchange, Microsoft Office 365, Google Apps, and other hosted and on-premises email solutions.
Trend Micro™ OfficeScan™ with XGen™ endpoint security infuses high-fidelity machine learning with other detection technologies and global threat intelligence for comprehensive protection against advanced malware.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks