Form Strategies Based on these Targeted Attack Stages
24 de мая de 2012
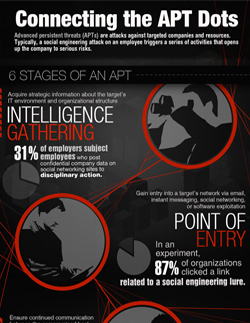 Download the infographic: Connecting the APT Dots
Download the infographic: Connecting the APT Dots
We often hear about the stuff popular targeted attacks are made of—which new large company was breached this time, how problematic it is to change passwords after a major attack on a favorite mobile app, or who are axing their executives after a breach led to major trading lows. But really, what happens when companies are targeted? How do those attackers stick their foot inside the door and stay inside without anyone noticing? Are there invisibility cloaks against security staff?
There’s really no magic or mystery to it. Attackers follow six well-planned stages in going about stealing from a company.
It can start with a simple Facebook post with too much information in it, an email that supposedly came from a colleague, or a storage device an employee luckily found lying around on the way to the office. It all starts with a trigger, and from there, things can only go bad.
Ultimately, attackers will steal what information they can grab and leave companies with major headaches on how to deal with the consequences. However, that doesn’t mean that only targeted attacks cause data breaches or that money is the only reason for stealing company data.
Check which attack information you think you know is accurate and which ones are just myths.
HIDE

Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks