As vehicles become more advanced, their associated threat landscape also grows broader and more complex. In the annual cyberthreat landscape report of VicOne, the subsidiary of Trend Micro dedicated to automotive cybersecurity, a notable concern raised is vulnerabilities and how they’ve begun to affect the automotive industry.
Vulnerabilities in the automotive industry
A look at Common Vulnerabilities and Exposures (CVE) counts in the automotive industry from 2000 to the first half of 2023 shows a sharp increase in 2019, with another jump in 2020. The trend signifies a major push for discovering CVEs within the industry, which in turn points to a growing interest in automotive cybersecurity in recent years.
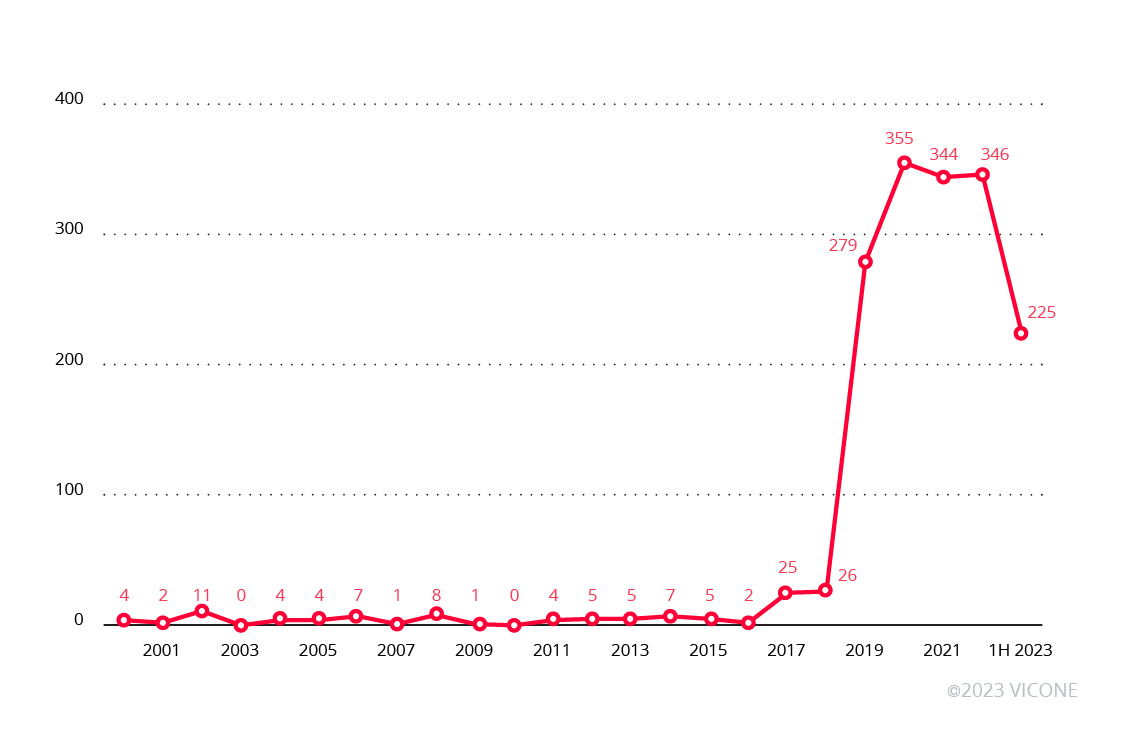
Figure 1. CVE counts from 2000 to the first half of 2023
VicOne researchers identified the Common Weakness Enumeration (CWE) vulnerabilities within the CVEs of the first half of 2023. Their collections showed different cases of SQL injection (CWE-89) vulnerabilities in website or application management. They also saw integer overflow or wraparound (CWE-120) vulnerabilities occur in different components of chipsets.
Security issues in vehicles
How do these vulnerabilities translate into issues for vehicles? VicOne looked at the distribution of security issues within the top identified CVEs to see which components were the most affected. Issues on chipsets or systems-on-chip (SoCs) had the major share of reported CVEs in the first half of 2023, reflecting a trend that has been consistent since 2021. SoC-related issues were followed by vulnerabilities in third-party management apps and in-vehicle infotainment (IVI) systems.
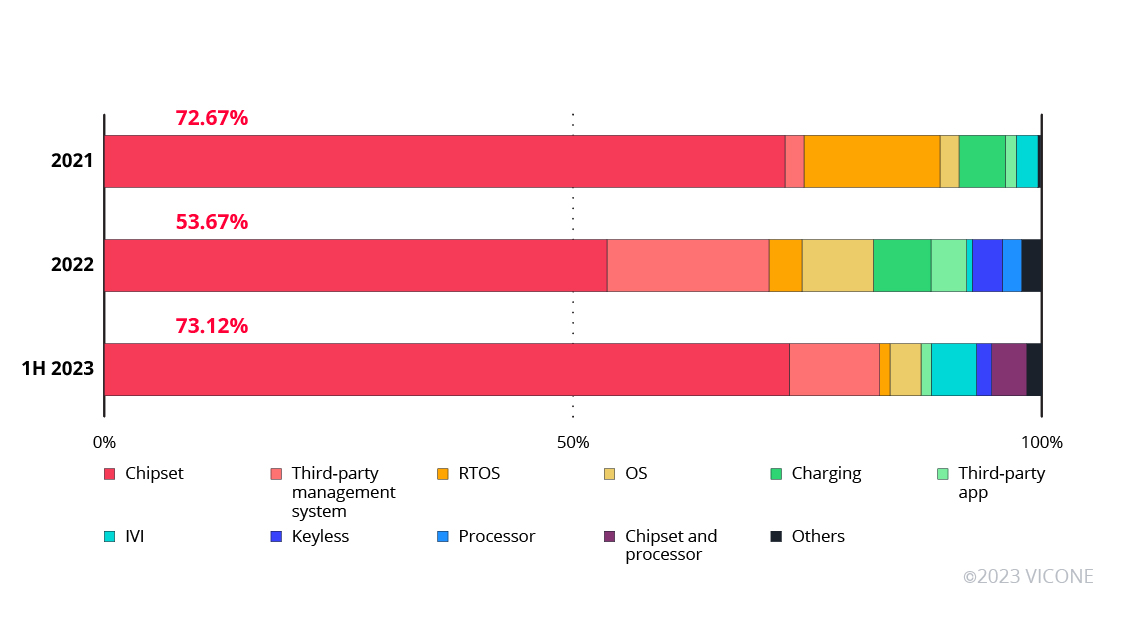
Figure 2. The distribution of security issues within the top CVEs in 2021, 2022, and the first half of 2023
Case studies
In 2023, notable research and tests demonstrated how the industry could be affected by vulnerabilities. Thankfully, these studies were made under controlled conditions, with no known exploits in the wild. They show that vulnerabilities could have a grave impact on vehicles if left unaddressed and highlight security gaps in how technologies, such as the cloud, are being adopted.
Zenbleed
The discovery of Zenbleed was relatively alarming, given that it’s a critical vulnerability in AMD’s Zen 2 microarchitecture. The vulnerability was discovered by Tavis Ormandy, a Google security researcher, who found that it could lead to the leakage of sensitive data at a remarkably fast rate of 30 kbps per core.
Zenbleed demonstrates how more advanced components necessary for new vehicle functionalities can introduce new vulnerabilities and expand the vehicle attack surface.
Cloud service compromise
Sam Curry, a web application security researcher, demonstrated how he and his team were able to access the back-end cloud infrastructure of different automotive manufacturers (OEMs) by exploiting vulnerabilities in their telematics systems and APIs. They were able to gain limited access to the employee applications, which they then leveraged to gain further access to sensitive internal applications.
This discovery exemplifies how the automotive industry is susceptible to the same issues that plague cloud services in the IT industry. However, the automotive industry is not as adequately prepared to address the same problems.
Conclusion
Only a few years ago, vulnerabilities in vehicles were not yet a major concern in cybersecurity. But rapid advancements in automotive technologies and the transformation of vehicles have left cybersecurity much to contend with. As VicOne’s report shows, even well-known vulnerabilities in the IT industry have started to affect not just the manufacturers and suppliers themselves but also real vehicles now on the road.
It’s important to acknowledge that the automotive industry has been making marked improvements in implementing automotive cybersecurity. Standards and regulations like ISO/SAE 21434 and UN Regulation No. 155 (UN R155) drive the way forward. However, with the shift toward software-defined vehicles (SDVs), more vulnerabilities are on the horizon.
OEMs and suppliers can look to the processes and best practices implemented in the IT industry in combination with automotive threat intelligence expertise to meet the unique cybersecurity demands of the road that they are on.
To learn more about the state of automotive cybersecurity, read “VicOne Automotive Cyberthreat Landscape Report 2023,” which details the security measures the industry is currently implementing and the risks it needs to prepare for. This report is part of the VicOne Automotive Cybersecurity Report 2023.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- LLM as a Judge: Evaluating Accuracy in LLM Security Scans
- The Silent Leap: OpenAI’s New ChatGPT Agent Capabilities and Security Risks
- Trend Micro State of AI Security Report 1H 2025
- The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
- Exploiting Trust in Open-Source AI: The Hidden Supply Chain Risk No One Is Watching
 Trend Micro State of AI Security Report 1H 2025
Trend Micro State of AI Security Report 1H 2025 AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Navigating Architecture, Threats, and Solutions
The Road to Agentic AI: Navigating Architecture, Threats, and Solutions