
Download Trend Micro's Guide to Cyber Insurance
As ransomware and BEC cyberattacks continue to increase, organizations are acquiring cyber insurance in record numbers to reduce cyber risk. According to Zurich, 83% of organizations have cyber insurance, the highest percentage in over a decade. However, there is some debate around the clarity of cyber insurance policy requirements and what security tools CISOs and security leaders need to consider when obtaining or renewing policies.
This article will discuss 5 considerations to enhance your cybersecurity maturity in-line with cyber insurance coverage requirements.
What is cyber insurance?
Cyber insurance, or cyber liability insurance, is a contract that enterprises can purchase to reduce the risks associated with conducting online business. This covers your business’ liability for most data breaches caused by cyberattack. Cyber insurance can help offset the cost of legal fees, restoring personal identities of impacted customers, recovering compromised data, repairing any damage to compromised systems, and notifying customers about any possible breaches.
Security considerations for cyber insurance coverage
No cybersecurity vendor can guarantee their solutions will get you the best cyber insurance coverage at the lowest rate. The upside is that enhancing your security to align with cyber insurance coverage requirements will certainly improve your resiliency (if configured correctly, of course).
Here are five security considerations that are in-line with cyber insurance requirements and may help reduce cyber risk:
- Choose the right security vendor
- MFA as part of a broader zero trust strategy
- Go beyond EDR to XDR
- Prioritized patching strategy
- Stronger email security
Despite what some cybersecurity vendors may say, carriers do not have any mandated vendors that businesses must use to receive cyber insurance coverage. Ultimately, they want to see an organization has a strong partnership with vendors that deliver a baseline level of cybersecurity maturity.
There’s a myriad of cybersecurity maturity frameworks to reference; Nemertes Research simplified the well-known NIST Cybersecurity Framework into four stages: unprepared, reactive, proactive, and anticipatory.
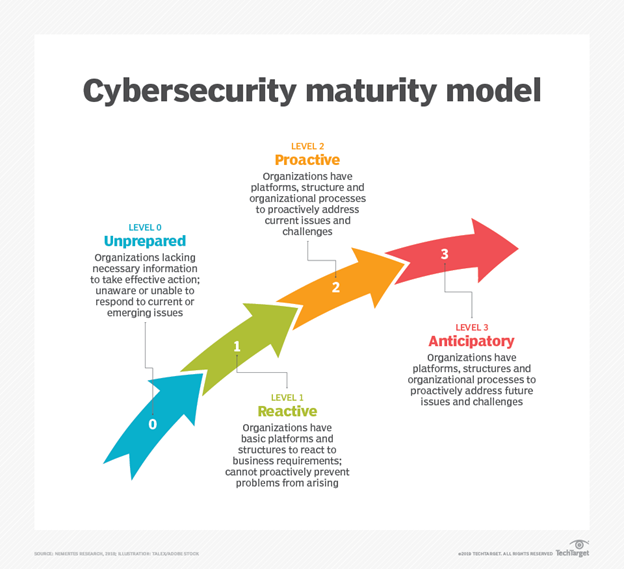
According to Nemertes, this maturity model assesses an organization’s cybersecurity initiative across several layers, including people, processes, and technology. To reach the higher stages—proactive and anticipatory—businesses need to leverage the latest threat defenses like AI, ML, behavioral analysis, and approaches like zero trust. And preferably from one platform, to help streamline processes, deliver faster and better detection and response, as well as reduce the strain of manual processes.
Therefore, consider a vendor that isn’t offering you a product suite, but a true cybersecurity platform that consolidates security capabilities and provides broad third-party integrations to further enhance visibility. This will demonstrate you’re partnered with an innovative vendor that is dedicated to enhancing cybersecurity maturity and reducing cyber risk.
Increasing ransomware demands have been a major contributor to tightening cyber insurance requirements. Underwriters across the board are looking for ransomware prevention practices, such as using MFA before they will provide a quote.
While having MFA is a great first step, the ultimate goal is to improve your security posture as much as possible to reduce cyber risk. Ideally MFA should be used in tandem with other network security capabilities under a zero-trust model like Zero Trust Network Access (ZTNA) to strengthen security maturity.
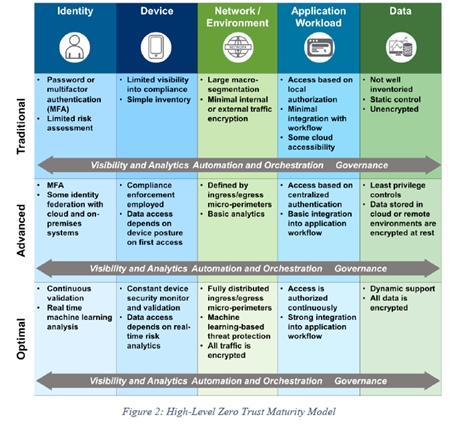
Why ZTNA? According to the Zero Trust Maturity Model by CISA, MFA lies within the identity pillar for the first two stages of maturity: traditional and advanced. The optimal stage includes continuous validation and real-time machine learning analysis, both of which—alongside MFA—are part of ZTNA.
Carriers who require EDR as a security control should accept XDR as a solution. And with the main objective being to improve security maturity, organizations should be looking to enhance detection and response capabilities beyond EDR with XDR.
XDR is simply an extension of EDR. Whereas EDR only detects at the endpoint level, XDR can collect and correlate threat activity data across endpoints plus servers, cloud, networks, and email. Done well, XDR can help to contextualize threat data, providing only critical alerts instead of bogging down security teams with false positives.
With a graphical, attack-centric timeline view, SOCs can better understand how the user got infected, the first point of entry, how the threat spread, and a host of other helpful data to limit the scope of an attack.
As previously mentioned, carriers want to see if an organization has implemented the necessary security tools to stop ransomware. When XDR is combined with ZTNA, you have a better chance at combating costly ransomware attacks.
How does this work? First, ZTNA hardens the infrastructure against malicious attacks by establishing a source of truth to authenticate, authorize, and continuously monitor access against. Additionally, segmenting the network will slow down an attack by reducing lateral movement within the organization.
Then, XDR brings together information about possible attack elements like indicators of compromise (IoCs), network traffic logs, suspicious endpoint behavior, SaaS service requests, and server events for analysis. This forms the basis for an effective response, should any risky behavior be detected from XDR analysis.
With this approach, your security posture is enhanced, and you can effectively demonstrate how to stop ransomware attacks to cyber insurers.
In the event of a zero- or n-day event, lost revenue from business downtime as well as repair, PR, and legal associated costs are usually covered under cyber insurance. Thus, underwriters want to see if an organization has an effective patch management strategy in place before providing a quote.
The days of patching everything are gone. The time to attack is shrinking as exploits to vulnerable systems occur in just minutes, not days. For example, it only took the hacking group Hafnium five minutes to start scanning for vulnerabilities after Microsoft announced a zero-day vulnerability found in Microsoft Exchange Server. And while cybercriminals are quick to strike, it can take days for the vendor to release a patch, leaving your system unprotected and your business operations at risk.
The key to a strong patch management is prioritization. To achieve this, organizations need to focus on bugs that are relevant to their specific application systems. From there, security teams can identify which of those bugs have been actively exploited and if they are part of the business’ critical infrastructure.
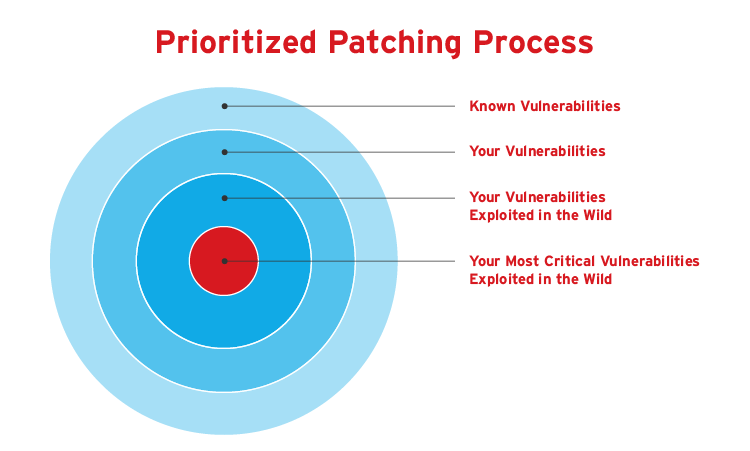
Next, use the CISA Known Exploited Vulnerability catalog as a reference point when identifying which applications or operating systems have been exploited by vulnerabilities in the wild.
Keep in mind, you’ll need full visibility of the attack surface to effectively prioritize patches; another reason why a unified cybersecurity platform is so valuable to security teams. Disparate point products can lead to visibility gaps, which in turn means your patching strategy could be leaving old applications, networks, systems, devices, and servers unprotected.
While ransomware is regularly in the news, its method of delivery is less talked about. More than 90% of cyber threats, including ransomware, come from email. Furthermore, losses from email attacks dwarf those of ransomware; in 2021, the FBI reported $2.4B in adjusted losses from BEC claims compared to $49.2M from ransomware.
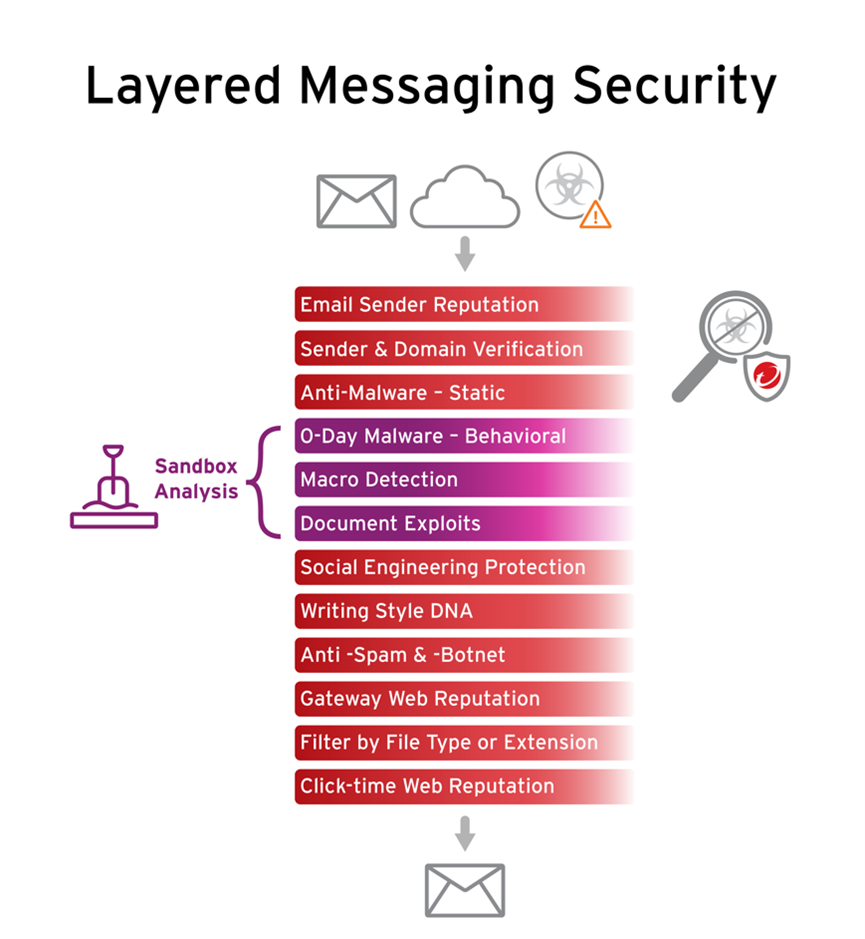
Look for cutting-edge email security capabilities such as gateways to detect external and internal malicious emails, writing style and computer graphic analysis, and integration with other security solutions. A strong email security strategy will not only improve your security maturity but can demonstrate proactive, risk-based protection to cyber insurance carriers.
Next steps
Cybersecurity maturity is not a destination, but a journey. Don’t upgrade your security stack with the intent of doing the bare minimum to meet cyber insurance coverage requirements. Look to shift from reactive to proactive security, meaning evolving beyond basic security procedures to more innovative methods like ZTNA, XDR, and virtual patching.
For more information on cyber insurance and the security capabilities discussed, check out the following resources:
- Building Business Resilience: How Cyber Insurance Fits into Your Risk Management Plan
- Cyber Insurance Market: FAQs & Updates with iBynd
- How Zero Trust and XDR Work Together
Questions about cyber insurance or Trend Micro? Reach out to Cyberinsurance@trendmicro.com

