The Anatomy of RTKT_ZACCESS
Publish Date: 2011年11月17日
What is RTKT_ZACCESS?
RTKT_ZACCESS is a rootkit component bundled with other malware such as FAKEAV. RTKT_ZACCESS, or ZACCESS monitors I/O request packets (IRPs) and prevents applications from detecting malware such as forensic tools and prevents security software from executing. It also modifies the file’s Access Control List (ACL).
Rootkits are notorious for being able to take complete control of an affected system, able to perform routines that can only be performed through administrator-level access. This may result in the malware able to hide itself or its components, making it difficult to detect or remove.
Why is RTKT_ZACCESS noteworthy?
It is the first rootkit malware that uses a new method in disabling AV products in the system it infects. Not only does it terminate the AV’s process, but it also modifies the ACL of the affected system.
In an operating system, ACL refers to a system-wide list of per file permissions or restrictions granted to users. An ACL specifies which user or system processes are granted access to specific files. It also specifies which operations are allowed on these files.
RTKT_ZACCESS modifies the affected system’s ACL, resulting in the AV product being stricken from the ACL itself. This disables said AV product from being accessed or run.
How does it arrive onto systems?
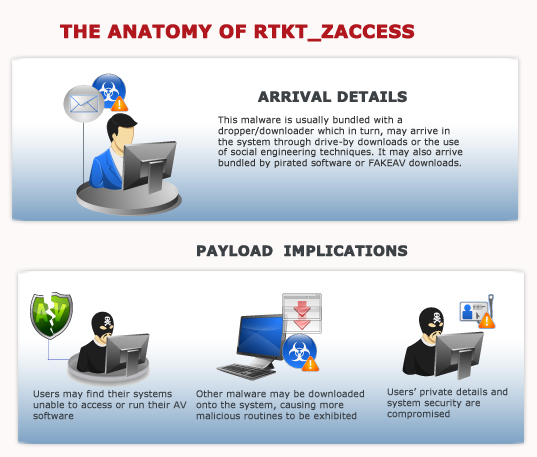
RTKT_ZACCESS arrives bundled with a dropper and/or downloader. This downloader may also arrive in the system through drive-by downloads or through the use of social engineering techniques. Based on our observation of the samples we received, the droppers/downloaders were bundled with FAKEAV variants. They may also arrive and pose as key generators or program crackers.
How do these malware affect users?
RTKT_ZACCESS is a rootkit malware designed to bring in fraudulent applications and other information-stealing malware into the system while staying hidden from detection. RTKT_ZACCESS does not collect user information; however, it may download other malware that may perform the said routine.
Are networks at risk if a single computer is infected with RTKT_ZACCESS?
Possibly. Since RTKT_ZACCESS can download other malicious files onto the system, it may also execute worms, file infectors and the like. However, RTKT_ZACCESS alone does not pose a threat to the entire network.
How do users know they are infected with this threat?
Users who suspect their systems to be infected can easily confirm their infection by attempting to run their antivirus applications. Due to RTKT_ZACCESS’ ability to modify processes’ ACL, it can render the system unable to run applications that attempt to detect it.
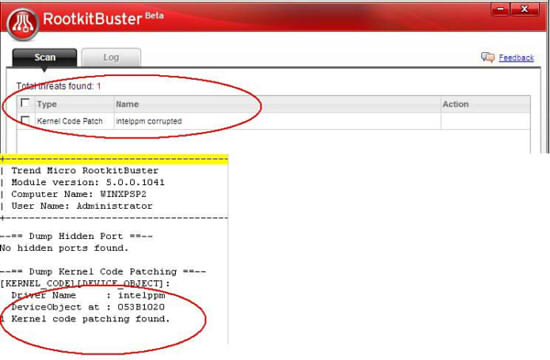
Users can also use the Trend Micro tool, RootkitBuster to confirm infection by following the steps below:
1. Download the latest version of RootkitBuster here.
2. Run the program and select all the options except for the following:
- Services
- Files or Master Boot Record (MBR)
3. The infected system will return with a result like below:

The user may perform any of the following:
1. ATTK Fixtool (for RTKT_ZACESS.SM1) - This tool removes infection and restores the ACL of coreServiceShell.exe, a component of Trend Micro Titanium™ 2011, whose security access may have been modified by the malware such that the program will not be accessible for execution thus, disabling the product.
OS: Windows XP, Windows Vista, and Windows 7.
Limitation: This fixtool only supports RTKT_ZACCESS.SM1 and RTKT_ZACCESS.SM3 infections.
2. Rescue Disk - This tool will automatically remove ZACCESS (for Windows XP Windows SP3, Windows 2003, Windows Vista, and Windows 7). Here’s how to use the tool:
- Download the tool from this link.
- While the installer downloads, prepare an empty USB drive (128 MB or larger).
- Once the download finishes, double-click the Trend Micro Rescue Disk icon to start the installer.
- Once done with the setup, download the latest OTH pattern from this link.
- Update/replace the OTH signature inside the TM Rescue Disk->Pattern folder.
- Set up the Boot Order in BIOS.
- In Rescue Disk boot menu, choose “Remove Threats”.
Users may also refer to the guide uploaded here for more information on the usage of this tool.
Are Trend Micro users protected from this threat?
Yes. Trend Micro provides a multi-layered protection from ZACCESS through the Trend Micro Smart Protection Network™. The file reputation technology detects and deletes RTKT_ZACCESS variants found on the affected system.
Trend Micro’s Threat Discovery Appliance (TDA) also protects users' networks by blocking malicious packets, such as C&C communication and uploading stolen information.
Home users can use Trend Micro’s free tool, HouseCall to scan and clean systems infected with malware components related to this attack. Similarly, Trend Micro’s GeneriClean cleans and rids the system of malware-related modifications.
Users are advised to be wary of divulging any personal information online. It is always advisable to access online bank accounts using a secure network. For businesses, we recommend the use of various security layers such as firewall, gateway, messaging, network, server, endpoint, and mobile security for optimal protection against attacks like this.