Adware.Win32.Cydoor.AD
Win32:AdwareX-gen [Adw], Win32:Cydoor [Adw] (AVAST)
Windows

Threat Type:
Adware
Destructiveness:
No
Encrypted:
No
In the wild::
Yes
OVERVIEW
It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Este malware no tiene ninguna rutina de propagación.
Este malware no tiene ninguna rutina de puerta trasera.
Se conecta a determinados sitios Web para enviar y recibir información.
TECHNICAL DETAILS
Detalles de entrada
It arrives on a system as a file dropped by other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Instalación
Agrega las carpetas siguientes:
- %Program Files%\Babylon
- %Program Files%\Babylon\Gloss
- %Program Files%\Babylon\Help
- %Program Files%\Babylon\Updates
- %Program Files%\Babylon\Utils
- %Program Files%\Babylon\Data
- %Program Files%\Babylon\Data\BGLs
- %User Temp%\{Random Characters}
- %User Temp%\{Random Characters}\adverck
- %User Temp%\{Random Characters}.tmp
- %System%\AdCache
(Nota: %Program Files% es la carpeta Archivos de programa predeterminada, que suele estar en C:\Archivos de programa).
. %User Temp% es la carpeta Temp del usuario activo, que en el caso de Windows 2000(32-bit), XP y Server 2003(32-bit) suele estar en C:\Documents and Settings\{nombre de usuario}\Local Settings\Temp y en el case de Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) y 10(64-bit) en C:\Users\{nombre de usuario}\AppData\Local\Temp).. %System% es la carpeta del sistema de Windows, que en el caso de Windows 98 y ME suele estar en C:\Windows\System, en el caso de Windows NT y 2000 en C:\WINNT\System32 y en el caso de Windows 2000(32-bit), XP, Server 2003(32-bit), Vista, 7, 8, 8.1, 2008(64-bit), 2012(64bit) y 10(64-bit) en C:\Windows\System32).)Infiltra los archivos siguientes:
- Upon execution:
- %User Temp%\{Random Characters}.tmp\Uninstbb.exe
- %User Temp%\{Random Characters}.tmp\bab_cht.bgl
- %User Temp%\{Random Characters}.tmp\bab_dut.bgl
- %User Temp%\{Random Characters}.tmp\bab_eng.bgl
- %User Temp%\{Random Characters}.tmp\bab_fre.bgl
- %User Temp%\{Random Characters}.tmp\bab_ger.bgl
- %User Temp%\{Random Characters}.tmp\bab_heb.bgl
- %User Temp%\{Random Characters}.tmp\bab_ita.bgl
- %User Temp%\{Random Characters}.tmp\bab_jpn.bgl
- %User Temp%\{Random Characters}.tmp\bab_ptg.bgl
- %User Temp%\{Random Characters}.tmp\bab_spa.bgl
- %User Temp%\{Random Characters}.tmp\bab_swe.bgl
- %User Temp%\{Random Characters}.tmp\babylon.exe
- %User Temp%\{Random Characters}.tmp\b-update.exe
- %User Temp%\{Random Characters}.tmp\captlib.dll
- %User Temp%\{Random Characters}.tmp\convert.dat
- %User Temp%\{Random Characters}.tmp\features.dat
- %User Temp%\{Random Characters}.tmp\rates.dat
- %User Temp%\{Random Characters}.tmp\bab_chs.bgl
- %User Temp%\{Random Characters}.tmp\LICENSE.TXT
- %User Temp%\{Random Characters}.tmp\SHLHOOK.EXE
- %User Temp%\{Random Characters}.tmp\OleLoad.dll
- %User Temp%\{Random Characters}.tmp\ImageLoad.dll
- %User Temp%\{Random Characters}.tmp\babylon.chm
- %User Temp%\{Random Characters}.tmp\Setup30.exe
- %User Temp%\{Random Characters}.tmp\PSAPI.DLL
- %User Temp%\{Random Characters}.tmp\cd_install_167.exe
- %User Temp%\{Random Characters}.tmp\Cydoor.txt
- During installation:
- %Program Files%\Babylon\DeIsL1.isu
- %Program Files%\Babylon\Updates\b-update.exe
- %Program Files%\Babylon\Updates\convert.dat
- %Program Files%\Babylon\Updates\rates.dat
- %Program Files%\Babylon\Utils\Shlhook.exe
- %Program Files%\Babylon\Utils\OleLoad.dll
- %Program Files%\Babylon\Utils\ImageLoad.dll
- %Program Files%\Babylon\Utils\Psapi.dll
- %Program Files%\Babylon\Help\babylon.chm
- %Program Files%\Babylon\features.dat
- %Program Files%\Babylon\babylon.exe
- %Program Files%\Babylon\captlib.dll
- %Program Files%\Babylon\Data\BGLs\bab_eng.bgl
- %Program Files%\Babylon\Data\BGLs\bab_chs.bgl
- %Program Files%\Babylon\Data\BGLs\bab_cht.bgl
- %Program Files%\Babylon\Data\BGLs\bab_dut.bgl
- %Program Files%\Babylon\Data\BGLs\bab_fre.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ger.bgl
- %Program Files%\Babylon\Data\BGLs\bab_heb.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ita.bgl
- %Program Files%\Babylon\Data\BGLs\bab_jpn.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ptg.bgl
- %Program Files%\Babylon\Data\BGLs\bab_spa.bgl
- %Program Files%\Babylon\Data\BGLs\bab_swe.bgl
- %User Temp%\_adA304.dll
- %User Temp%\{Random Characters}\_adA304.adx
- %User Temp%\{Random Characters}\_adA304.rtp
- %User Temp%\{Random Characters}\adverck\B_{Random Numbers}.gif
- %User Temp%\{Random Characters}\adverck\cd_clint.dll
- %User Temp%\{Random Characters}\adverck\cd_load.exe
- %User Temp%\{Random Characters}\adverck\Start.cdi
- %User Temp%\{Random Characters}\B_{Random Numbers}.gif
- %User Temp%\{Random Characters}\cd_clint.dll
- %User Temp%\{Random Characters}\cd_load.exe
- %User Temp%\{Random Characters}\Start.cdi
- %System%\cd_clint.dll
- %System%\cd_load.exe
- %System%\AdCache\b_249400.GIF
- %System%\AdCache\b_202200.GIF
- %System%\AdCache\b_217000.GIF
- %System%\AdCache\b_205800.GIF
- %System%\AdCache\b_217300.GIF
- %System%\AdCache\b_217100.GIF
- %Common Programs%\Babylon.lnk
- %Windows%\uninstbb.exe
- After running the installed program:
- %Program Files%\Babylon\oc_stack.txt
- %Program Files%\Babylon\log_file.txt
- %Program Files%\Babylon\banmng.ban
- %Program Files%\Babylon\ocr_data
- %Program Files%\Babylon\Gloss\bab_eng_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_chs_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_cht_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_dut_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_fre_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ger_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_heb_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ita_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_jpn_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ptg_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_spa_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_swe_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_eng_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_chs_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_cht_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_dut_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_fre_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ger_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_heb_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ita_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_jpn_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ptg_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_spa_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_swe_{Random Numbers}.bdc
(Nota: %User Temp% es la carpeta Temp del usuario activo, que en el caso de Windows 2000(32-bit), XP y Server 2003(32-bit) suele estar en C:\Documents and Settings\{nombre de usuario}\Local Settings\Temp y en el case de Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) y 10(64-bit) en C:\Users\{nombre de usuario}\AppData\Local\Temp).
. %Windows% es la carpeta de Windows, que suele estar en C:\Windows o C:\WINNT).)Agrega los procesos siguientes:
- Upon execution:
- %User Temp%\{Random Characters}.tmp\setup30.exe
- During installation:
- "%User Temp%\{Random Characters}.tmp\cd_install_167.exe"
- "%User Temp%\{Random Characters}\cd_load.exe" i r
- After running the installed program:
- "%Program Files%\Babylon\babylon.exe"
- %System%\CD_Load.exe
(Nota: %User Temp% es la carpeta Temp del usuario activo, que en el caso de Windows 2000(32-bit), XP y Server 2003(32-bit) suele estar en C:\Documents and Settings\{nombre de usuario}\Local Settings\Temp y en el case de Windows Vista, 7, 8, 8.1, 2008(64-bit), 2012(64-bit) y 10(64-bit) en C:\Users\{nombre de usuario}\AppData\Local\Temp).
. %System% es la carpeta del sistema de Windows, que en el caso de Windows 98 y ME suele estar en C:\Windows\System, en el caso de Windows NT y 2000 en C:\WINNT\System32 y en el caso de Windows 2000(32-bit), XP, Server 2003(32-bit), Vista, 7, 8, 8.1, 2008(64-bit), 2012(64bit) y 10(64-bit) en C:\Windows\System32).)Técnica de inicio automático
Agrega las siguientes entradas de registro para permitir su ejecución automática cada vez que se inicia el sistema:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Run
Babylon Translator = %Program Files%\Babylon\Babylon.exe
Otras modificaciones del sistema
Agrega las siguientes entradas de registro:
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\Users\Default\
Options
TranslateWithShift = 2
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\Users\Default\
Settings
Interface = 0
AllowedExt = JPG BMP GIF TXT HTM HTML WAV MP3 PNG
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\Users\Default\
GlossInst
gls0 = %Program Files%\babylon\data\bgls\bab_eng.bgl,1{BLOCKED}.com
gls1 = %Program Files%\babylon\data\bgls\bab_chs.bgl,1{BLOCKED}n.com
gls2 = %Program Files%\babylon\data\bgls\bab_cht.bgl,1{BLOCKED}n.com
gls3 = %Program Files%\babylon\data\bgls\bab_dut.bgl,1{BLOCKED}n.com
gls4 = %Program Files%\babylon\data\bgls\bab_fre.bgl,1{BLOCKED}n.com
gls5 = %Program Files%\babylon\data\bgls\bab_ger.bgl,1{BLOCKED}n.com
gls6 = %Program Files%\babylon\data\bgls\bab_heb.bgl,1{BLOCKED}n.com
gls7 = %Program Files%\babylon\data\bgls\bab_ita.bgl,1{BLOCKED}n.com
gls8 = %Program Files%\babylon\data\bgls\bab_jpn.bgl,1{BLOCKED}n.com
gls9 = %Program Files%\babylon\data\bgls\bab_ptg.bgl,1{BLOCKED}n.com
gls10 = %Program Files%\babylon\data\bgls\bab_spa.bgl,1{BLOCKED}n.com
gls11 = %Program Files%\babylon\data\bgls\bab_swe.bgl,1{BLOCKED}n.com
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2022
Url = www.{BLOCKED}r.com/BestDeals
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2494
Url = http://www.{BLOCKED}.com/track/track.dll?
AID=1143761&PID=190859&URL=http%3A%2F%2Ffxnetworks%2Ecom%2Fshows%2Foriginals%2Fthesight%2Findexcj%2Ehtml
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2170
Url = http://{BLOCKED}t.com/bfast/click?bfmid=1429031&siteid=8854274&bfpage=homelinks
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2058
Url = http://www.{BLOCKED}e.com/promo/cydoor
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2173
Url = http://s{BLOCKED}.com/bfast/click?bfmid=1429031&siteid=8854274&bfpage=homelinks
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2171
Url = http://www.c{BLOCKED}n.com/track/track.dll?
AID=1143760&PID=190859&URL=http%3A%2F%2Ffxnetworks%2Ecom%2Fshows%2Foriginals%2Fthesight%2Findexcj%2Ehtml
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167
LastDate = {Installation Date}
ExistFile = %Program Files%\Babylon\babylon.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
Prod.Cap
Index = {Hex Values}
Index3 = {Hex Values}
Usage = {Hex Values}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
Babylon
UninstallString = C:\Windows\uninstbb.exe
DisplayName = Babylon
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\App Paths\
Babylon.exe
{Default} = %Program Files%\Babylon\Babylon
Path = %Program Files%\Babylon
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Explorer
GlobalAssocChangedCounter = 37
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\WebSearch
S0 = 08
S2 = http://search.excite.com/search.gw?search=+ÿExcite
S3 = http://www.lycos.com/cgi-bin/pursuit?cat=dir&query=+ÿLycos
S4 = http://infoseek.go.com/Titles?qt=+ÿInfoseek
S5 = http://www.altavista.com/cgi-bin/query?q=+ÿAlta Vista
S6 = http://www.askjeeves.com/main/askJeeves.asp?ask=+ÿAsk Jeeves
S7 = http://www.northernlight.com/nlquery.fcg?cb=0&qr=+ÿNorthern Light
S8 = http://www.google.com/search?q=+ÿGoogle
S9 = http://hotbot.lycos.com/?MT=+ÿHotBot
SA = http://www.webcrawler.com/cgi-bin/WebQuery?searchText=+ÿWebCrawler
SB = http://results.searchopolis.com/cgi-bin/britannica_results.cgi?firstResult=0&displayfirstResult=1&act.search=search&request=+ÿBritannica.com
R2 = http://search.britannica.com/bcom/search/results/1,5843,,00.html?p_query0=+ÿBritannica.com
R3 = http://www.encarta.com/find/search.asp?tr=122&search=+ÿEncarta Online
R4 = http://www.infoplease.com/search.php3?in=all&query=+ÿInfoPlease
R5 = http://www.encyclopedia.com/cgi-bin/search.cgi?search=+ÿEncyclopedia.Com
HKEY_CURRENT_USER\Software\Cydoor
PrxyEnable = 0
PrxyUrl = pµ&
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
BabyGloss
{Default} = Babylon Glossary
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
BabyGloss\DefaultIcon
{Default} = %Program Files%\Babylon\Babylon.exe,2
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
BabyGloss\shell\open\
command
{Default} = "%Program Files%\Babylon\Babylon.exe" %1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
.bgl
{Default} = BabyGloss
Content Type = application/bgl
HKEY_LOCAL_MACHINE\SOFTWARE\Cydoor
%Program Files%\Babylon\babylon.exe = 167
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
MIME\Database\Content Type\
application/bgl
Extension = .bgl
HKEY_LOCAL_MACHINE\SOFTWARE\Babylon\
Babylon Translator\b1
IndexByData = {Hex Values}
IndexByExport = {Hex Values}
Propagación
Este malware no tiene ninguna rutina de propagación.
Rutina de puerta trasera
Este malware no tiene ninguna rutina de puerta trasera.
Otros detalles
Agrega las siguientes entradas de registro como parte de la rutina de instalación:
HKEY_CURRENT_USER\Software\Babylon
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\WebSearch
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\Users
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\Users\Default
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\Users\Default\
GlossInst
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\Users\Default\
Options
HKEY_CURRENT_USER\Software\Babylon\
Babylon Translator\Users\Default\
Settings
HKEY_CURRENT_USER\Software\Cydoor
HKEY_CURRENT_USER\Software\Cydoor\
Seqn_2173
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2022
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2058
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2170
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2171
HKEY_CURRENT_USER\Software\Cydoor\
Adwr_167\Loct_0\Level_4\
Seqn_2494
HKEY_LOCAL_MACHINE\SOFTWARE\Cydoor
HKEY_LOCAL_MACHINE\SOFTWARE\Babylon
HKEY_LOCAL_MACHINE\SOFTWARE\Babylon\
Babylon Translator
HKEY_LOCAL_MACHINE\SOFTWARE\Babylon\
Babylon Translator\b1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
.bgl
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
Prod.Cap
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
BabyGloss
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
BabyGloss\DefaultIcon
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
BabyGloss\shell
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
BabyGloss\shell\open
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
BabyGloss\shell\open\
command
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
MIME\Database\Content Type\
application/bgl
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\App Paths\
Babylon.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\
Windows\CurrentVersion\Uninstall\
Babylon
Se conecta al sitio Web siguiente para enviar y recibir información:
- http://{BLOCKED}n.co.il/gloss/gloss.cgi
Hace lo siguiente:
- It displays the following installation GUI upon executing the malware:

- It identifies itself as an adware before asking the user to install the program:
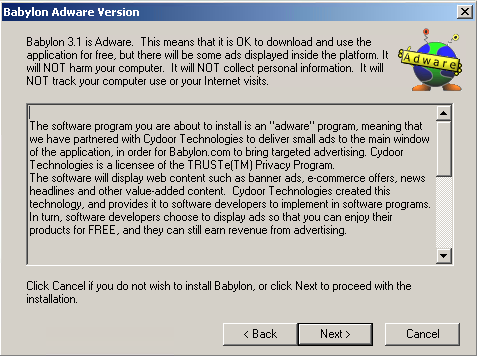
- When running the installed program, it is minimized as a system tray icon with the following context menu:
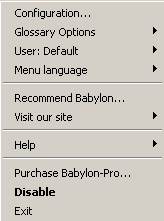
- Double clicking the system tray icon enables or disables the program.
- The system tray icon context menu does the following:
- Configuration → customize the functionality of the program:

- General → option to launch the program at startup, always use last user-defined window size, and minimize Babylon when mouse moves
- Find → setup a hotkey to activate Babylon and customize search results
- Appearance → customize font settings
- Connection → setup connection type, proxy settings, and automatic updates
- Voice → setup voice and text-to-speech features
- Glossary Options → customize how the program accesses and manages its glossary:
- Add from Babylon index → connects to the following URL: http://www.{BLOCKED}n.com/redirects/redir.cgi?type=index
- Open from Babylon builder → connects to the following URL: http://www.{BLOCKED}n.com/redirects/redir.cgi?type=builder
- Install from Disk
- User Default → Create, modify, and delete users of the program
- Menu Language → change menu language using the following languages:
- English
- Chinese
- Japanese
- Dutch
- French
- German
- Hebrew
- Italian
- Korean
- Portuguese
- Spanish
- Swedish
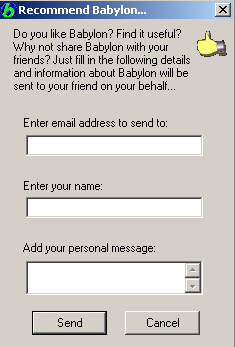
- Recommend Babylon → send email to a designated email address which includes ads or promotions along with the sender's personal message:
- Visit our site → redirects to the following sites depending on the user's choice:
- Upgrade Babylon → connects to the following URL: http://www.{BLOCKED}n.com/redirects/update.cgi?lang=-1&BabyVer=32.-1.2.50.31.32
- Send feedback → connects to the following URL: http://www.{BLOCKED}n.com/eng/contact/
- Babylon message board → connects to the following URL: http://www.{BLOCKED}n.com/redirects/redir.cgi?lang=eng&type=forum30
- What's New? → connects to the following URL: http://www.{BLOCKED}n.com/redirects/redir.cgi?lang=eng&type=whatsnew30
- Help → contains instructions on how to use the installed program:
- Contents → opens an CHM Help file by executing the following process:
- "%Windows%\hh.exe" %Program Files%\babylon\Help\Babylon.chm
- Frequently asked questions → connects to the following URL: http://www.{BLOCKED}n.com/redirects/redir.cgi?lang=eng&type=faq30
- About Babylon → displays the product version, company, and registration status
- Registration: registers a user to receive preferred contents and access more features
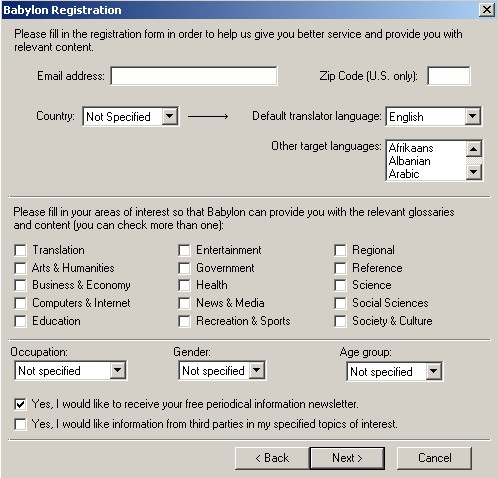
Requires to fillup the following:- Email add
- Country
- Occupation
- Gender
- Age group
- Contents → opens an CHM Help file by executing the following process:
- Purchase Babylon-Pro... → option to purchase Pro version of Babylon:

- Enable/Disable → Enable or disable Babylon program
- Exit: terminates the program
- Configuration → customize the functionality of the program:
SOLUTION
Step 1
Los usuarios de Windows ME y XP, antes de llevar a cabo cualquier exploración, deben comprobar que tienen desactivada la opción Restaurar sistema para permitir la exploración completa del equipo.
Step 2
Note that not all files, folders, and registry keys and entries are installed on your computer during this malware's/spyware's/grayware's execution. This may be due to incomplete installation or other operating system conditions. If you do not find the same files/folders/registry information, please proceed to the next step.
Step 3
Reiniciar en modo seguro
Step 4
Eliminar este valor del Registro
Importante: si modifica el Registro de Windows incorrectamente, podría hacer que el sistema funcione mal de manera irreversible. Lleve a cabo este paso solo si sabe cómo hacerlo o si puede contar con ayuda de su administrador del sistema. De lo contrario, lea este artículo de Microsoft antes de modificar el Registro del equipo.
- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Babylon Translator = %Program Files%\Babylon\Babylon.exe
- Babylon Translator = %Program Files%\Babylon\Babylon.exe
- TranslateWithShift = 2
- Interface = 0
- AllowedExt = JPG BMP GIF TXT HTM HTML WAV MP3 PNG
- gls1 = %Program Files%\babylon\data\bgls\bab_chs.bgl,1{BLOCKED}n.com
- gls2 = %Program Files%\babylon\data\bgls\bab_cht.bgl,1{BLOCKED}n.com
- gls3 = %Program Files%\babylon\data\bgls\bab_dut.bgl,1{BLOCKED}n.com
- gls4 = %Program Files%\babylon\data\bgls\bab_fre.bgl,1{BLOCKED}n.com
- gls5 = %Program Files%\babylon\data\bgls\bab_ger.bgl,1{BLOCKED}n.com
- gls6 = %Program Files%\babylon\data\bgls\bab_heb.bgl,1{BLOCKED}n.com
- gls7 = %Program Files%\babylon\data\bgls\bab_ita.bgl,1{BLOCKED}n.com
- gls8 = %Program Files%\babylon\data\bgls\bab_jpn.bgl,1{BLOCKED}n.com
- gls9 = %Program Files%\babylon\data\bgls\bab_ptg.bgl,1{BLOCKED}n.com
- gls10 = %Program Files%\babylon\data\bgls\bab_spa.bgl,1{BLOCKED}n.com
- gls11 = %Program Files%\babylon\data\bgls\bab_swe.bgl,1{BLOCKED}n.com
- Url = http://www.{BLOCKED}n.com/track/track.dll?AID=1143761&PID=190859&URL=http%3A%2F%2Ffxnetworks%2Ecom%2Fshows%2Foriginals%2Fthesight%2Findexcj%2Ehtml
- Url = http://{BLOCKED}.com/bfast/click?bfmid=1429031&siteid=8854274&bfpage=homelinks
- Url = http://www.{BLOCKED}.com/track/track.dll?AID=1143760&PID=190859&URL=http%3A%2F%2Ffxnetworks%2Ecom%2Fshows%2Foriginals%2Fthesight%2Findexcj%2Ehtml
- LastDate = {Installation Date}
- ExistFile = %Program Files%\Babylon\babylon.exe
- Index = {Hex Values}
- Index3 = {Hex Values}
- Usage = {Hex Values}
- UninstallString = C:\Windows\uninstbb.exe
- DisplayName = Babylon
- {Default} = %Program Files%\Babylon\Babylon
- Path = %Program Files%\Babylon
- GlobalAssocChangedCounter = 37
- S0 = 08
- S2 = http://search.excite.com/search.gw?search=+ÿExcite
- S3 = http://www.lycos.com/cgi-bin/pursuit?cat=dir&query=+ÿLycos
- S4 = http://infoseek.go.com/Titles?qt=+ÿInfoseek
- S5 = http://www.altavista.com/cgi-bin/query?q=+ÿAlta Vista
- S6 = http://www.askjeeves.com/main/askJeeves.asp?ask=+ÿAsk Jeeves
- S7 = http://www.northernlight.com/nlquery.fcg?cb=0&qr=+ÿNorthern Light
- S8 = http://www.google.com/search?q=+ÿGoogle
- S9 = http://hotbot.lycos.com/?MT=+ÿHotBot
- SA = http://www.webcrawler.com/cgi-bin/WebQuery?searchText=+ÿWebCrawler
- SB = http://results.searchopolis.com/cgi-bin/britannica_results.cgi?firstResult=0&displayfirstResult=1&act.search=search&request=+ÿBritannica.com
- R2 = http://search.britannica.com/bcom/search/results/1,5843,,00.html?p_query0=+ÿBritannica.com
- R3 = http://www.encarta.com/find/search.asp?tr=122&search=+ÿEncarta Online
- R4 = http://www.infoplease.com/search.php3?in=all&query=+ÿInfoPlease
- R5 = http://www.encyclopedia.com/cgi-bin/search.cgi?search=+ÿEncyclopedia.Com
- PrxyEnable = 0
- PrxyUrl = pµ&
- {Default} = Babylon Glossary
- {Default} = %Program Files%\Babylon\Babylon.exe,2
- {Default} = %Program Files%\Babylon\Babylon.exe %1
- {Default} = BabyGloss
- Content Type = application/bgl
- %Program Files%\Babylon\babylon.exe = 167
- application/bgl
- Extension = .bgl
- IndexByData = {Hex Values}
- IndexByExport = {Hex Values}
Step 5
Eliminar esta clave del Registro
Importante: si modifica el Registro de Windows incorrectamente, podría hacer que el sistema funcione mal de manera irreversible. Lleve a cabo este paso solo si sabe cómo hacerlo o si puede contar con ayuda de su administrador del sistema. De lo contrario, lea este artículo de Microsoft antes de modificar el Registro del equipo.
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\
- Babylon
- Babylon
- In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\
- Babylon.exe
- Babylon.exe
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MIME\Database\Content Type\
- application/bgl
- application/bgl
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\BabyGloss\shell\open\
- command
- command
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\BabyGloss\shell\
- open
- open
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\BabyGloss\
- shell
- shell
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\BabyGloss\
- DefaultIcon
- DefaultIcon
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
- BabyGloss
- BabyGloss
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
- Prod.Cap
- Prod.Cap
- In HKEY_LOCAL_MACHINE\SOFTWARE\Classes\
- .bgl
- .bgl
- In HKEY_LOCAL_MACHINE\SOFTWARE\Babylon\Babylon Translator\
- b1
- b1
- In HKEY_LOCAL_MACHINE\SOFTWARE\Babylon\
- Babylon Translator
- Babylon Translator
- In HKEY_LOCAL_MACHINE\SOFTWARE\
- Babylon
- Babylon
- In HKEY_LOCAL_MACHINE\SOFTWARE\
- Cydoor
- Cydoor
- In HKEY_CURRENT_USER\Software\Cydoor\Adwr_167\Loct_0\Level_4\
- Seqn_2494
- Seqn_2494
- In HKEY_CURRENT_USER\Software\Cydoor\Adwr_167\Loct_0\Level_4\
- Seqn_2171
- Seqn_2171
- In HKEY_CURRENT_USER\Software\Cydoor\Adwr_167\Loct_0\Level_4\
- Seqn_2170
- Seqn_2170
- In HKEY_CURRENT_USER\Software\Cydoor\Adwr_167\Loct_0\Level_4\
- Seqn_2058
- Seqn_2058
- In HKEY_CURRENT_USER\Software\Cydoor\Adwr_167\Loct_0\Level_4\
- Seqn_2022
- Seqn_2022
- In HKEY_CURRENT_USER\Software\Cydoor\Adwr_167\Loct_0\
- Level_4
- Level_4
- In HKEY_CURRENT_USER\Software\Cydoor\Adwr_167\
- Loct_0
- Loct_0
- In HKEY_CURRENT_USER\Software\Cydoor\
- Adwr_167
- Adwr_167
- In HKEY_CURRENT_USER\Software\Cydoor\
- Seqn_2173
- Seqn_2173
- In HKEY_CURRENT_USER\Software\
- Cydoor
- Cydoor
- In HKEY_CURRENT_USER\Software\Babylon\Babylon Translator\Users\Default\
- Settings
- Settings
- In HKEY_CURRENT_USER\Software\Babylon\Babylon Translator\Users\Default\
- Options
- Options
- In HKEY_CURRENT_USER\Software\Babylon\Babylon Translator\Users\Default\
- GlossInst
- GlossInst
- In HKEY_CURRENT_USER\Software\Babylon\Babylon Translator\Users\
- Default
- Default
- In HKEY_CURRENT_USER\Software\Babylon\Babylon Translator\
- Users
- Users
- In HKEY_CURRENT_USER\Software\Babylon\Babylon Translator\
- WebSearch
- WebSearch
- In HKEY_CURRENT_USER\Software\Babylon\
- Babylon Translator
- Babylon Translator
- In HKEY_CURRENT_USER\Software\
- Babylon
- Babylon
Step 6
Buscar y eliminar estos archivos
- %Common Programs%\Babylon.lnk
- %Program Files%\Babylon\babylon.exe
- %Program Files%\Babylon\banmng.ban
- %Program Files%\Babylon\captlib.dll
- %Program Files%\Babylon\Data\BGLs\bab_chs.bgl
- %Program Files%\Babylon\Data\BGLs\bab_cht.bgl
- %Program Files%\Babylon\Data\BGLs\bab_dut.bgl
- %Program Files%\Babylon\Data\BGLs\bab_eng.bgl
- %Program Files%\Babylon\Data\BGLs\bab_fre.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ger.bgl
- %Program Files%\Babylon\Data\BGLs\bab_heb.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ita.bgl
- %Program Files%\Babylon\Data\BGLs\bab_jpn.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ptg.bgl
- %Program Files%\Babylon\Data\BGLs\bab_spa.bgl
- %Program Files%\Babylon\Data\BGLs\bab_swe.bgl
- %Program Files%\Babylon\DeIsL1.isu
- %Program Files%\Babylon\features.dat
- %Program Files%\Babylon\Gloss\bab_chs_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_chs_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_cht_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_cht_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_dut_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_dut_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_eng_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_eng_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_fre_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_fre_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ger_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ger_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_heb_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_heb_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ita_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ita_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_jpn_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_jpn_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ptg_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ptg_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_spa_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_spa_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_swe_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_swe_{Random Numbers}.dat
- %Program Files%\Babylon\Help\babylon.chm
- %Program Files%\Babylon\log_file.txt
- %Program Files%\Babylon\oc_stack.txt
- %Program Files%\Babylon\ocr_data
- %Program Files%\Babylon\Updates\b-update.exe
- %Program Files%\Babylon\Updates\convert.dat
- %Program Files%\Babylon\Updates\rates.dat
- %Program Files%\Babylon\Utils\ImageLoad.dll
- %Program Files%\Babylon\Utils\OleLoad.dll
- %Program Files%\Babylon\Utils\Psapi.dll
- %Program Files%\Babylon\Utils\Shlhook.exe
- %System%\AdCache\b_202200.GIF
- %System%\AdCache\b_205800.GIF
- %System%\AdCache\b_217000.GIF
- %System%\AdCache\b_217100.GIF
- %System%\AdCache\b_217300.GIF
- %System%\AdCache\b_249400.GIF
- %System%\cd_clint.dll
- %System%\cd_load.exe
- %User Temp%\_adA304.dll
- %User Temp%\{Random Characters}.tmp\b-update.exe
- %User Temp%\{Random Characters}.tmp\bab_chs.bgl
- %User Temp%\{Random Characters}.tmp\bab_cht.bgl
- %User Temp%\{Random Characters}.tmp\bab_dut.bgl
- %User Temp%\{Random Characters}.tmp\bab_eng.bgl
- %User Temp%\{Random Characters}.tmp\bab_fre.bgl
- %User Temp%\{Random Characters}.tmp\bab_ger.bgl
- %User Temp%\{Random Characters}.tmp\bab_heb.bgl
- %User Temp%\{Random Characters}.tmp\bab_ita.bgl
- %User Temp%\{Random Characters}.tmp\bab_jpn.bgl
- %User Temp%\{Random Characters}.tmp\bab_ptg.bgl
- %User Temp%\{Random Characters}.tmp\bab_spa.bgl
- %User Temp%\{Random Characters}.tmp\bab_swe.bgl
- %User Temp%\{Random Characters}.tmp\babylon.chm
- %User Temp%\{Random Characters}.tmp\babylon.exe
- %User Temp%\{Random Characters}.tmp\captlib.dll
- %User Temp%\{Random Characters}.tmp\cd_install_167.exe
- %User Temp%\{Random Characters}.tmp\convert.dat
- %User Temp%\{Random Characters}.tmp\Cydoor.txt
- %User Temp%\{Random Characters}.tmp\features.dat
- %User Temp%\{Random Characters}.tmp\ImageLoad.dll
- %User Temp%\{Random Characters}.tmp\LICENSE.TXT
- %User Temp%\{Random Characters}.tmp\OleLoad.dll
- %User Temp%\{Random Characters}.tmp\PSAPI.DLL
- %User Temp%\{Random Characters}.tmp\rates.dat
- %User Temp%\{Random Characters}.tmp\Setup30.exe
- %User Temp%\{Random Characters}.tmp\SHLHOOK.EXE
- %User Temp%\{Random Characters}.tmp\Uninstbb.exe
- %User Temp%\{Random Characters}\_adA304.adx
- %User Temp%\{Random Characters}\_adA304.rtp
- %User Temp%\{Random Characters}\adverck\B_{Random Numbers}.gif
- %User Temp%\{Random Characters}\adverck\cd_clint.dll
- %User Temp%\{Random Characters}\adverck\cd_load.exe
- %User Temp%\{Random Characters}\adverck\Start.cdi
- %User Temp%\{Random Characters}\B_{Random Numbers}.gif
- %User Temp%\{Random Characters}\cd_clint.dll
- %User Temp%\{Random Characters}\cd_load.exe
- %User Temp%\{Random Characters}\Start.cdi
- %Windows%\uninstbb.exe
- %Common Programs%\Babylon.lnk
- %Program Files%\Babylon\babylon.exe
- %Program Files%\Babylon\banmng.ban
- %Program Files%\Babylon\captlib.dll
- %Program Files%\Babylon\Data\BGLs\bab_chs.bgl
- %Program Files%\Babylon\Data\BGLs\bab_cht.bgl
- %Program Files%\Babylon\Data\BGLs\bab_dut.bgl
- %Program Files%\Babylon\Data\BGLs\bab_eng.bgl
- %Program Files%\Babylon\Data\BGLs\bab_fre.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ger.bgl
- %Program Files%\Babylon\Data\BGLs\bab_heb.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ita.bgl
- %Program Files%\Babylon\Data\BGLs\bab_jpn.bgl
- %Program Files%\Babylon\Data\BGLs\bab_ptg.bgl
- %Program Files%\Babylon\Data\BGLs\bab_spa.bgl
- %Program Files%\Babylon\Data\BGLs\bab_swe.bgl
- %Program Files%\Babylon\DeIsL1.isu
- %Program Files%\Babylon\features.dat
- %Program Files%\Babylon\Gloss\bab_chs_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_chs_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_cht_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_cht_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_dut_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_dut_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_eng_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_eng_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_fre_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_fre_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ger_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ger_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_heb_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_heb_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ita_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ita_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_jpn_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_jpn_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_ptg_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_ptg_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_spa_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_spa_{Random Numbers}.dat
- %Program Files%\Babylon\Gloss\bab_swe_{Random Numbers}.bdc
- %Program Files%\Babylon\Gloss\bab_swe_{Random Numbers}.dat
- %Program Files%\Babylon\Help\babylon.chm
- %Program Files%\Babylon\log_file.txt
- %Program Files%\Babylon\oc_stack.txt
- %Program Files%\Babylon\ocr_data
- %Program Files%\Babylon\Updates\b-update.exe
- %Program Files%\Babylon\Updates\convert.dat
- %Program Files%\Babylon\Updates\rates.dat
- %Program Files%\Babylon\Utils\ImageLoad.dll
- %Program Files%\Babylon\Utils\OleLoad.dll
- %Program Files%\Babylon\Utils\Psapi.dll
- %Program Files%\Babylon\Utils\Shlhook.exe
- %System%\AdCache\b_202200.GIF
- %System%\AdCache\b_205800.GIF
- %System%\AdCache\b_217000.GIF
- %System%\AdCache\b_217100.GIF
- %System%\AdCache\b_217300.GIF
- %System%\AdCache\b_249400.GIF
- %System%\cd_clint.dll
- %System%\cd_load.exe
- %User Temp%\_adA304.dll
- %User Temp%\{Random Characters}.tmp\b-update.exe
- %User Temp%\{Random Characters}.tmp\bab_chs.bgl
- %User Temp%\{Random Characters}.tmp\bab_cht.bgl
- %User Temp%\{Random Characters}.tmp\bab_dut.bgl
- %User Temp%\{Random Characters}.tmp\bab_eng.bgl
- %User Temp%\{Random Characters}.tmp\bab_fre.bgl
- %User Temp%\{Random Characters}.tmp\bab_ger.bgl
- %User Temp%\{Random Characters}.tmp\bab_heb.bgl
- %User Temp%\{Random Characters}.tmp\bab_ita.bgl
- %User Temp%\{Random Characters}.tmp\bab_jpn.bgl
- %User Temp%\{Random Characters}.tmp\bab_ptg.bgl
- %User Temp%\{Random Characters}.tmp\bab_spa.bgl
- %User Temp%\{Random Characters}.tmp\bab_swe.bgl
- %User Temp%\{Random Characters}.tmp\babylon.chm
- %User Temp%\{Random Characters}.tmp\babylon.exe
- %User Temp%\{Random Characters}.tmp\captlib.dll
- %User Temp%\{Random Characters}.tmp\cd_install_167.exe
- %User Temp%\{Random Characters}.tmp\convert.dat
- %User Temp%\{Random Characters}.tmp\Cydoor.txt
- %User Temp%\{Random Characters}.tmp\features.dat
- %User Temp%\{Random Characters}.tmp\ImageLoad.dll
- %User Temp%\{Random Characters}.tmp\LICENSE.TXT
- %User Temp%\{Random Characters}.tmp\OleLoad.dll
- %User Temp%\{Random Characters}.tmp\PSAPI.DLL
- %User Temp%\{Random Characters}.tmp\rates.dat
- %User Temp%\{Random Characters}.tmp\Setup30.exe
- %User Temp%\{Random Characters}.tmp\SHLHOOK.EXE
- %User Temp%\{Random Characters}.tmp\Uninstbb.exe
- %User Temp%\{Random Characters}\_adA304.adx
- %User Temp%\{Random Characters}\_adA304.rtp
- %User Temp%\{Random Characters}\adverck\B_{Random Numbers}.gif
- %User Temp%\{Random Characters}\adverck\cd_clint.dll
- %User Temp%\{Random Characters}\adverck\cd_load.exe
- %User Temp%\{Random Characters}\adverck\Start.cdi
- %User Temp%\{Random Characters}\B_{Random Numbers}.gif
- %User Temp%\{Random Characters}\cd_clint.dll
- %User Temp%\{Random Characters}\cd_load.exe
- %User Temp%\{Random Characters}\Start.cdi
- %Windows%\uninstbb.exe
Step 7
Search and delete these folders
- %Program Files%\Babylon\Data\BGLs
- %Program Files%\Babylon\Data
- %Program Files%\Babylon\Gloss
- %Program Files%\Babylon\Help
- %Program Files%\Babylon\Updates
- %Program Files%\Babylon\Utils
- %Program Files%\Babylon
- %User Temp%\{Random Characters}
- %User Temp%\{Random Characters}\adverck
- %User Temp%\{Random Characters}.tmp
- %System%\AdCache
Step 8
Reinicie en modo normal y explore el equipo con su producto de Trend Micro para buscar los archivos identificados como Adware.Win32.Cydoor.AD En caso de que el producto de Trend Micro ya haya limpiado, eliminado o puesto en cuarentena los archivos detectados, no serán necesarios más pasos. Puede optar simplemente por eliminar los archivos en cuarentena. Consulte esta página de Base de conocimientos para obtener más información.
Did this description help? Tell us how we did.

