The Raspberry Pi has Its Potentials and Perils
10 de сентября de 2014
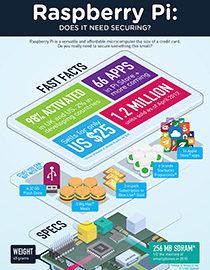 View infographic: Raspberry Pi: Does it Need Securing?
View infographic: Raspberry Pi: Does it Need Securing?
More than being a multipurpose, it sells for only US$ 25, roughly the amount of five Big Mac® meals or a three-month subscription to Xbox Live® Gold. That’s why the Pi sold like pancakes when it came to the United States.
The Pi is easily a DIY boss. It can be used as the base for powerful systems. It features an SD card slot, USB ports, an Ethernet port, an RCA socket, an HDMI port, an audio out, and a micro USB. As such, you can expand its memory, play media, and use it to connect to the Internet. If you build around it, you can use it as a portable computer, a file storage server, a home security control box, a home lighting system control box, a gaming device, a toy and novelty gadget, or an educational tool.
There is one caveat, though. One thing that makes the Raspberry Pi attractive and powerful is that it can be used to connect to the Internet, which could be risky. Threats of malware infections and data theft are lurking online. And since the Pi is just hardware where data is saved and loaded, the next logical step is to secure it.
Since the technology in this versatile microcomputer is already in use in mobile phones, there is a certain familiarity with the way security can be handled. It may not be enough to just enable all security features on the OS you use to run the Pi. As with desktop and mobile devices, make sure to also avoid downloading apps from suspicious sources onto the Pi as this can lead to data-stealing malware. Seeing as the Pi can easily connect to multiple devices and networks, all these should also be updated with the latest security solutions.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks