Protecting Physical Security Systems against Network Attacks
 View infographic: Protecting Physical Security Systems Against Network Attacks
View infographic: Protecting Physical Security Systems Against Network Attacks
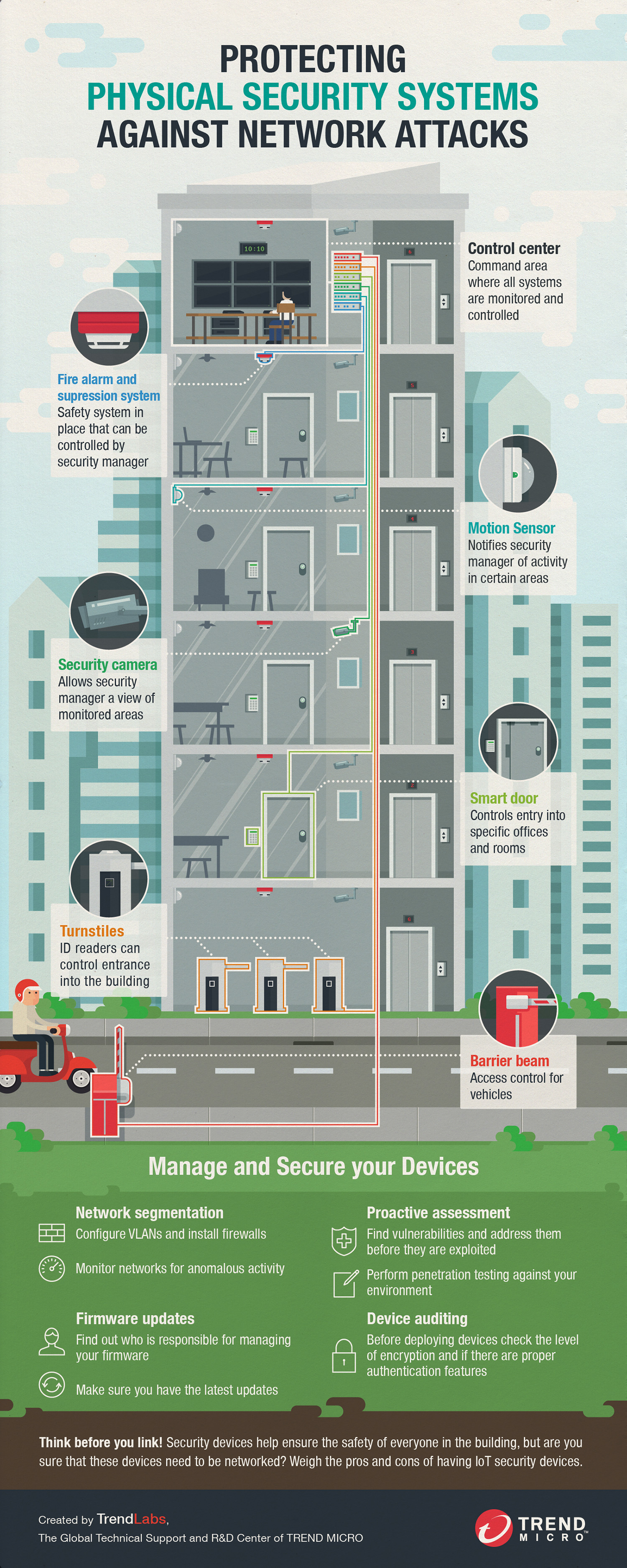
Every building—regardless of whether it accommodates enterprises or private owners—has security systems in place to protect valuable assets. These physical security systems range from simple access control, meaning doors and locks, to widespread surveillance systems and multiple alarms. And as these different systems grow more sophisticated, building administrators are finding ways to make managing them more convenient.
Piece by piece, security systems are going online to allow quicker access and easier control. Smart buildings are being built with centralized security management and monitoring. Appointed administrators can screen fire alarms, see which motion sensors are triggered, or view the security footage on each floor from a control center. Access permissions to entryways can be changed remotely as well. The physical is becoming digital.
These security system devices are also becoming more complex. Access into a room can be controlled with an ID reader, Request to Exit (REX) systems, door controllers, and management software for the whole system. Surveillance systems need cameras, digital video recorders and viewing software. Buildings are installing multiple alarms such as tamper sensors, fire alarms with suppression systems, and motion sensors as well.
Increased convenience and centralized control are perks of having all these devices accessible through the network, but there are also risks involved. They become susceptible to different kinds of network attacks, and the recent incident with HID door controllers proves that there is a real possibility that vulnerabilities in these devices can be exploited.
This infographic shows the different ways that you can address these concerns before they become a problem. We provide simple guidelines that building administrators can follow to manage physical security systems and also properly secure devices.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks